In this video tutorial, learn how to make a wireless Internet hotspot with the following: a Mac computer, an ethernet cable (connected to your modem), and an airport. This video will releave you of the need to deal with a router. Once completed, you will have you're very own wifi hotspot that will work on your iPod Touch (1st & 2nd generation), your Sony PSP (PSP 1000, 2000, & 3000 series), and anything else that has wifi compatibility.

In this video, Tim Carter, of Ask the Builder, will show you a quick tip for how to remove drywall so you can demo a wall without damaging the walls around it. All you need is a razor knife. If you just take a minute to trim the seam along the wall, you can save yourself from having to repair a whole of expensive damage later.

Want to learn how to broadcast live & record from your game console while viewing game-play in HD - using the BlitzBox B1-HD (for under $100). THis is an easy way to record your PS3, PS2, XBOX 360 or Wii games.

HIP2B2 TV Show presents how to build a parachute! This is a perfect rocket parachute that you can build on your own. You need to cut six strings to connect the chute to your model. They test it out with a rock.
This is a video demonstration on how to tether your iPhone 3G to a Mac laptop to use the 3G network for surfing the web on the laptop. This is against AT&T's policy so try at your own risk. This is in place of the NetShare app that keeps getting removed by Apple or ATT. This let's you connect your computer to the 3G wireless network by using a proxy on your jailbroken iPhone.

You can paint the Mona Lisa with Microsoft Paint. You start by drawing dots that you need to connect to make the face. Everything needs to be colored in by the end.

A lot of customers thought that one can place the Micro Mosquito on the base (which looks like a Helicopter Landing Pad) and it will be charged. No, there is a charging cord underneath the charging base that is used. All you need to do is to unlatch the cover and connect to the Mirco Mosquito. When connected properly, the green LED light will flash and once charged, the green LED will stop flashing. This video walks you through the process.

A DeAuth hack attack against a wireless network, as shown in this how-to video, will disconnect any and all users on a given WiFi network. The attacker does not need to know the WEP or WPA key or be connected to the network. For step-by-step instructions on running a DeAuth hack yourself, watch this simple how-to guide.

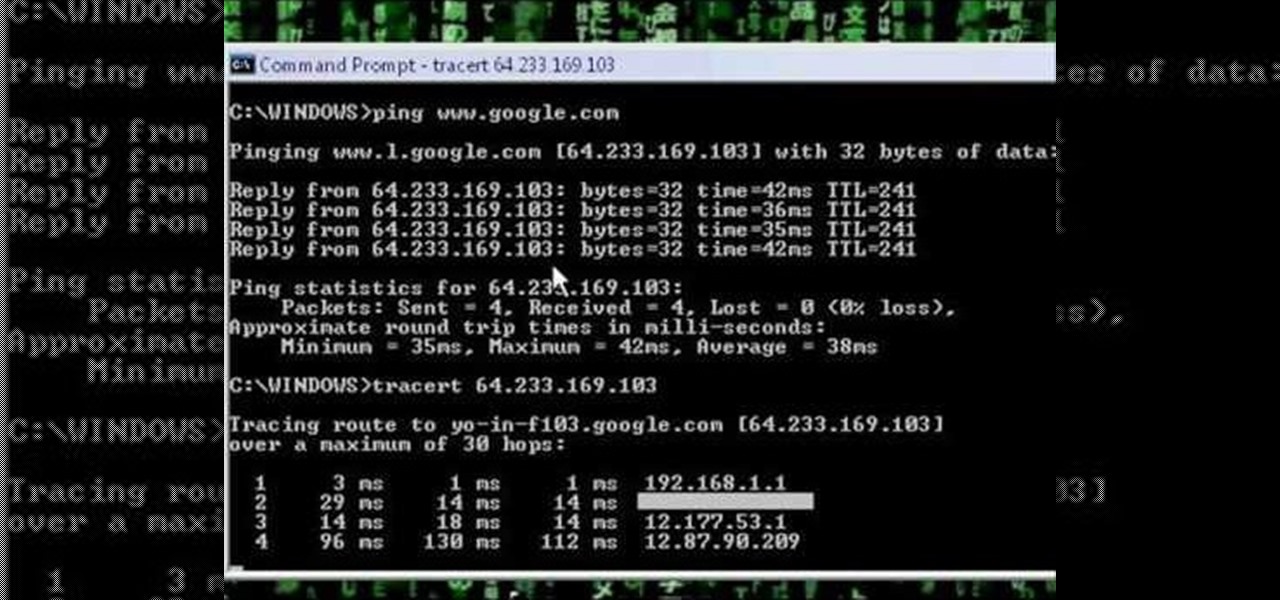
A network security tutorial on using ping and tracert to show th IP of a webserver, your own IP, your ISP's IP, who they connect to, and what computers your request goes through before reaching a destination.

This knot is common in the climbing world. We use it to secure two ropes together. Often used to form a loop on a prussik (cordalette) to construct an anchor. Can also be used to connect two ropes to rappel. This knot has many applications in the real world not just climbing.

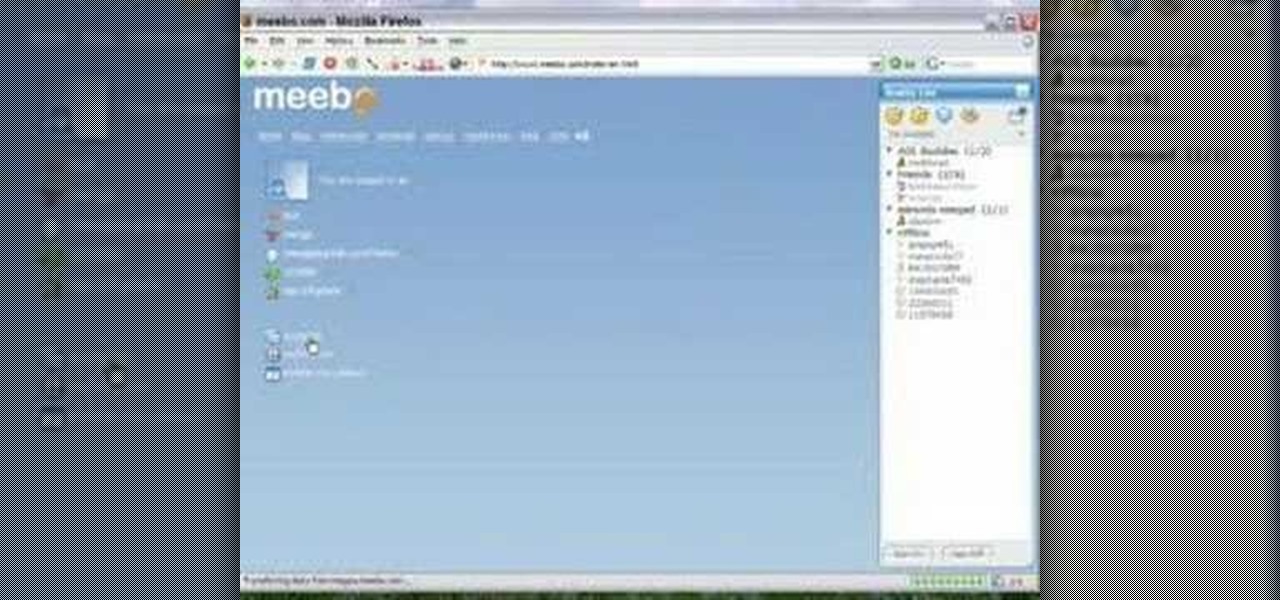
How to use Meebo as your instant messenger and connect to multiple instant messager services all via the Internet without installing any software.

Kipkay explains how to make a rocket powered matchbox by combining two matchbox toy cars. You need A10-PT model rockets and 32 gauge wire to connect the model rockets to the two cars.

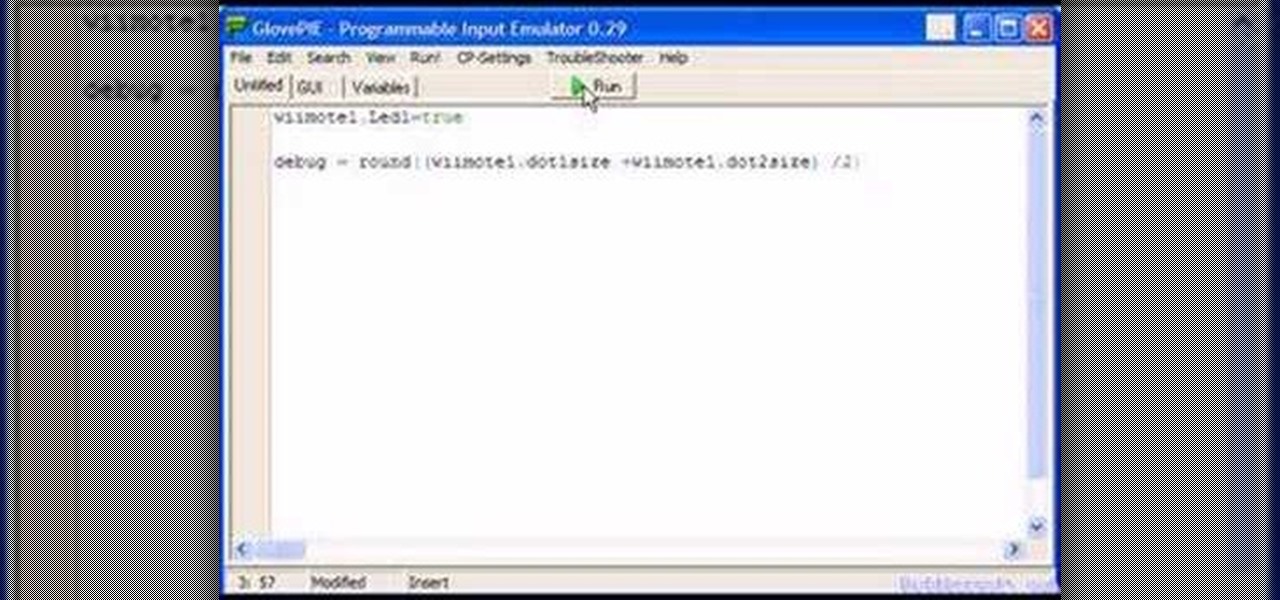
You can connect your Nintendo Wii Wiimote to your PC using GlovePie input emulation software and a bluetooth connection. Learn how to program your PC to calculate distance using the Wiimote's infra-red (IR) sensor.

You're out and about, and nothing on your iPhone will load. A glance at the settings shows a saved Wi-Fi network with full bars that your iPhone had connected to automatically, but you're not getting any internet. If you've experienced this, you're not alone, and there's something you can do about it. You'll even increase privacy and security on your iPhone in the process.

Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.

With EA chief executive Andrew Wilson stating the official mobile version of Apex Legends won't arrive until the 2021 fiscal year, fans have to wait at least another year to enjoy their favorite battle royale game on the go. But for those who can't wait, there are ways to play the game on iPhone and Android right now.

Smartphone hardware surpassed the most popular portable game devices long ago in all but one category — control. Your iPhone is more than capable of running impressive, fully-realized games, but touch controls only go so far. That's why it's so exciting that Apple has added support for PS4 and Xbox controllers with iOS 13.

Spotify integration in Bumble has been around for a few years now, allowing prospective matches to view the artists you listen to the most on the popular music streaming service. It definitely helps people connect, but sadly, it doesn't work as well as it should because it rarely updates to show what you're listening to now.

Having a dropped call can be incredibly frustrating, especially when you look down and see that your iPhone has full reception. While there's any number of issues that can cause this, one common and often overlooked issue is your iPhone failing to switch cell towers as appropriately needed.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

While HBO Now does not support offline viewing yet, your smartphone is the perfect way to watch your favorite shows and movies on-the-go. Whether you're in a hotel running off Wi-Fi or you have an unlimited plan and are on the bus, if you want to binge some Game of Thrones, the HBO Now app is there for you.

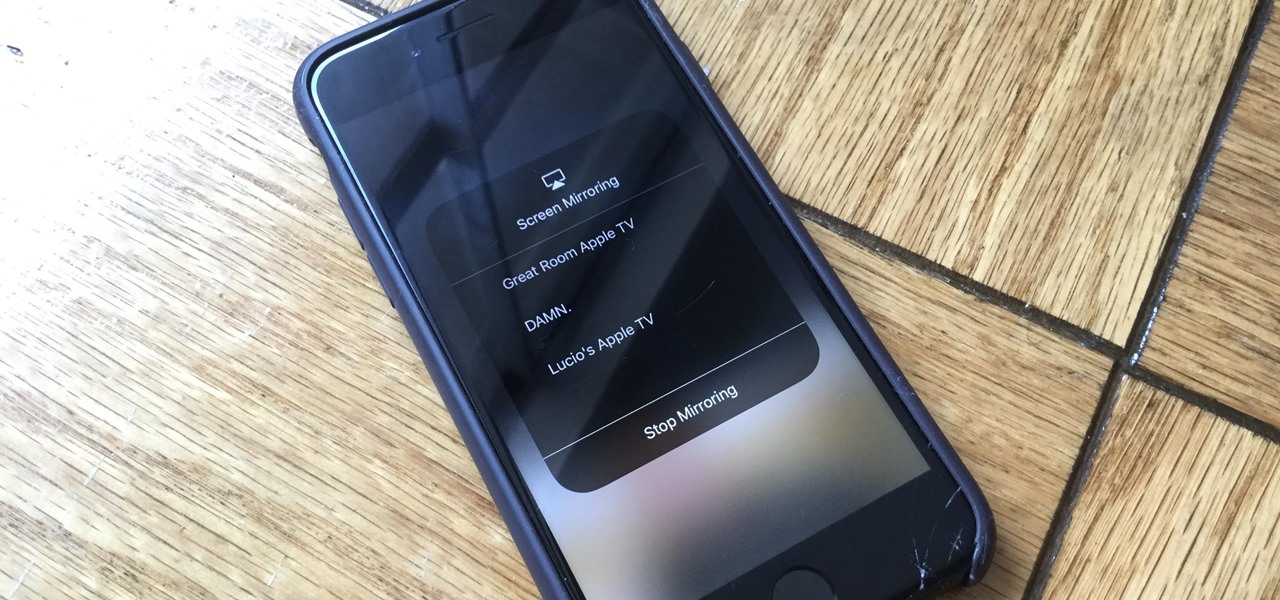
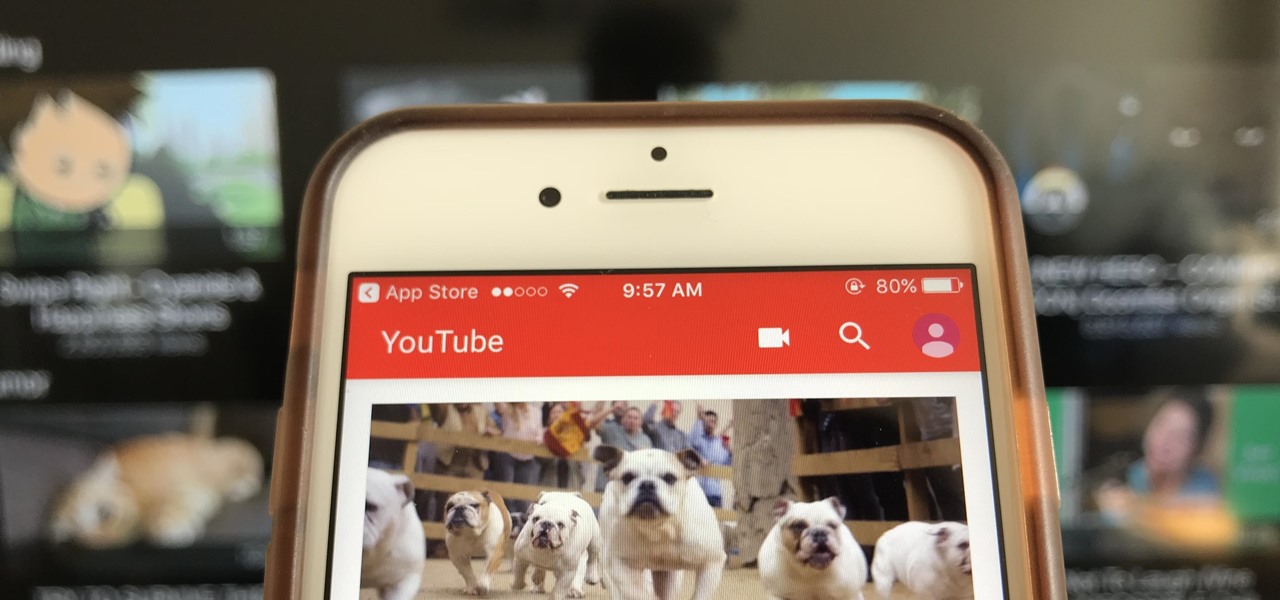
Watching YouTube on your phone has never been a better experience than it is today — our smartphones have super-sharp displays that make watching the newest HD, QHD, and even 4K content look fantastic. But there are plenty of circumstances where we want to watch our content on a larger screen.

Let's say you gave your Wi-Fi password to your neighbor a while back, under the assumption that they'd only use it while they were at your house sharing stuff via Chromecast. But now, your connection is slower than it normally should be, and you have this sneaking suspicion that the dude in apartment 3C is flat-out piggybacking off of your home network.

Wi-Fi signals have limited range, so if you live in a two-story house or work in a larger office, you may have set up multiple routers or repeaters to ensure full wireless coverage. Sadly, Android handles the transition between networks pretty poorly.

There's no doubt you've heard the old saying, "When life gives you lemons, make lemonade." The phrase was penned in an obituary to a dwarf actor in 1915 by an anarchist named Elbert Hubbard, who lost his life five months later aboard the RMS Lusitania when it was torpedoed by a German submarine.

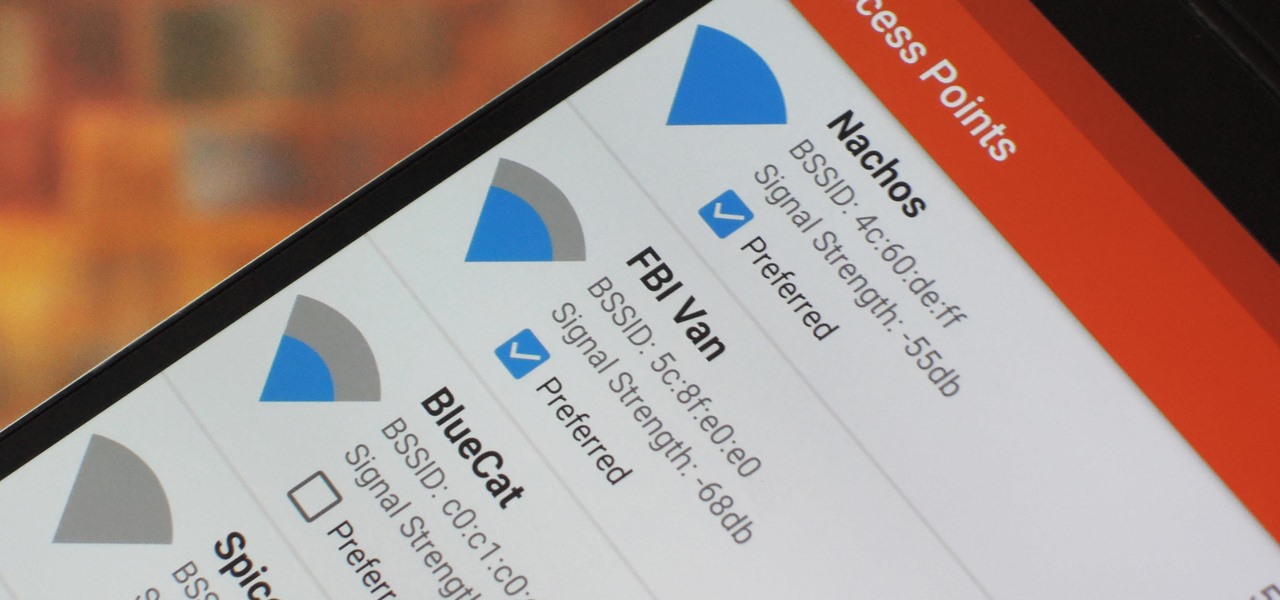
Hi Elite Hackers! Welcome! to my 4th post. This tutorial will explain, how to extend a (hacked) AP's range with a wireless adapter. I made this guide because after hacking an AP it was difficult to connect to it (poor connection) and further exploit it. You can also use this:

AllCast, from renowned developer Koushik Dutta (better known as Koush), allows users to stream personal media, such as movies, photos, and music from mobile devices to Chromecast and other streaming devices.

With all of the personal data that's stored on our smartphones, it's of vital importance that we have some sort of lock screen security enabled. One of the Galaxy S5's killer features is obviously the fingerprint scanner. It makes the process of dealing with a secure lock screen a bit easier than typing in a password or PIN.

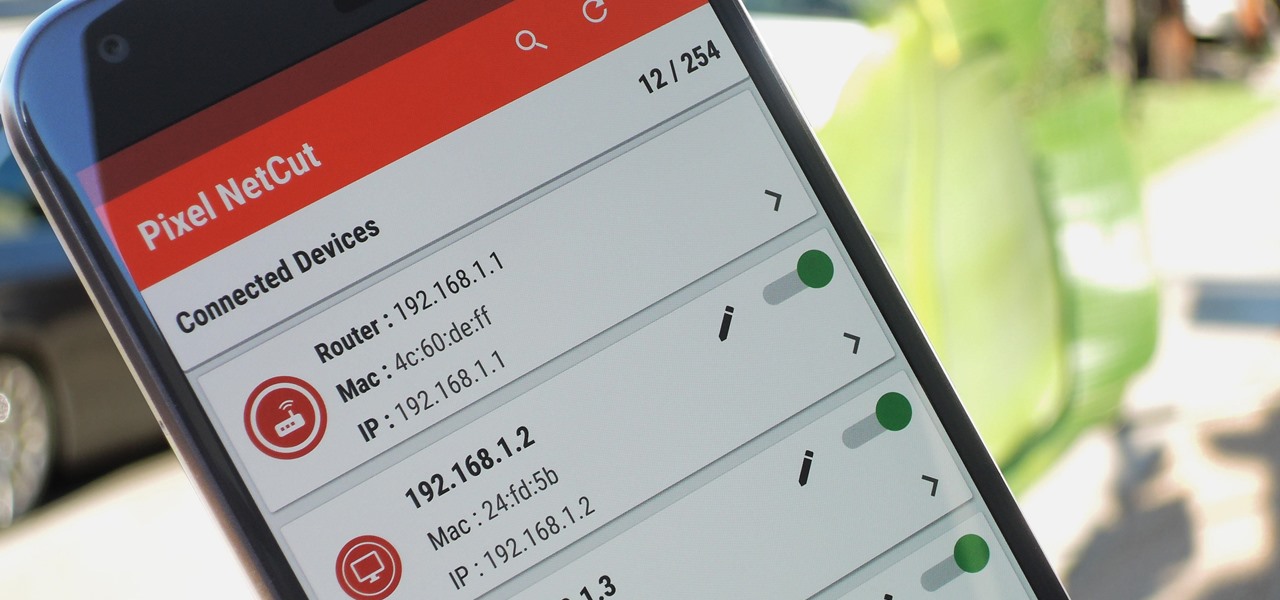
Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, netcat, which enables us to create a connection between any two machines and transfer files or spawn a command shell for "owning" the system. Despite the beauty and elegance of this little tool, it has one major drawback—the transfers between the computers can be detected by security devices such as firewalls and an intrusion detection system (IDS).

Want to use that great gel eyeliner. Don't Know how? Don't worry it is super easy. First pick a color of gel eyeliner that you like best. Then make sure you have and angled brush.

Welcome back, my hacker apprentices! My recent posts here in Null Byte have been very technical in nature, so I thought that I'd have a little fun with this one.

MAC addresses (not to be confused with Macs) are unique identifiers assigned to network devices in order to access the internet. Hotels use these Mac addresses in order to check if a registered patron has agreed to their terms and conditions, how much bandwidth is being consumed, and of course, whether they've paid or not.

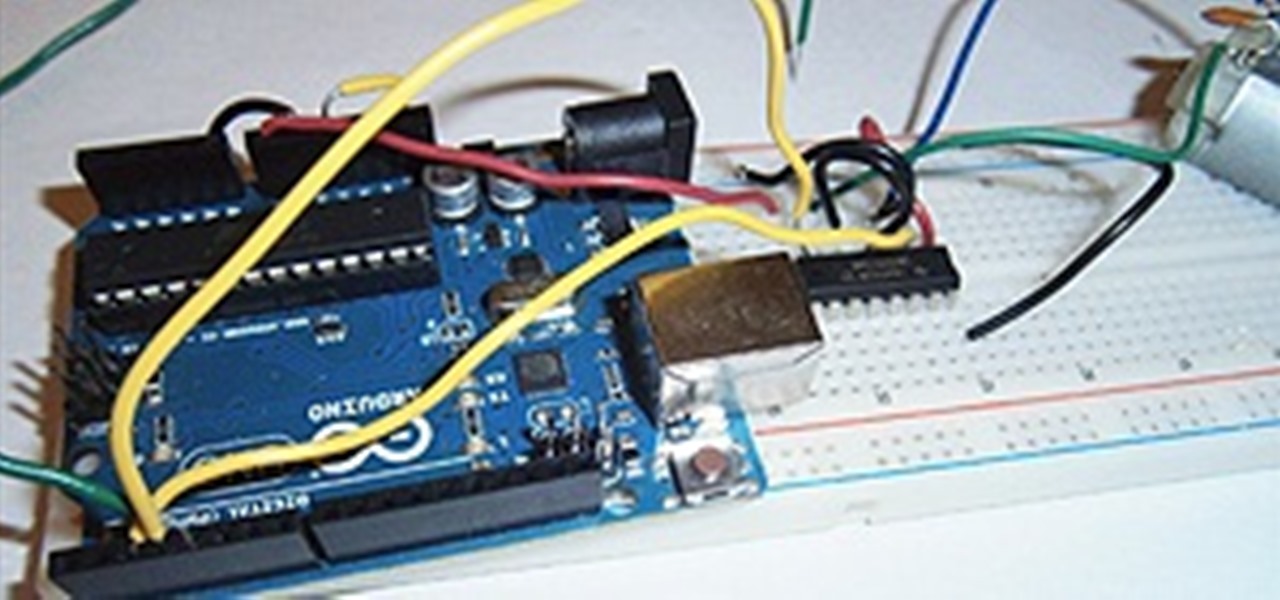
I love robots. They have the potential to evolve into Asimovian destroyers of the human species, but have only just mastered the art of cleaning my rug. They have an ever increasing cool factor and a growing number of cheap and simple components that let the hobby roboticist reach for the burning miasmas of plasma. But to get to the stars, we need to start with the basics.

Rust protection doesn't have to cost a fortune. With a little zinc and some electricity, you can protect your precious metals from rust by galvanization. When you galvanize something, you're giving it a protective coating, and in this case, it's a zinc coating.

Right out of the box, iPhone is incredibly easy to use. If you want to get the most out of every feature, you’ve come to the right place. This video tutorial straight from Apple will teach you how to browse the web with Safari on the Apple iPhone 3G. The iPhone redefines what a mobile phone can do.

This video tutorial is for beginner puzzlers who are getting more advanced in their speedsolving of the Rubik's Cube. When solving the Rubiks Cube, there are these mathematical equations called algorithms, which I'm sure you already know. With an endless supply of them out there for this puzzle, how can you possibly remember them all? By watching videos, that's how. This one will help teach you how to use the ZBF2L algorithms to solve the Rubik's Cube. What is the ZBF2L? It's the ZB Method of...

There are several safety precautions and steps that you must take before you attempt to start or use a portable generator. Take a look at this guide to learn how to check the oil levels, connect the battery to the generator, and start the generator.

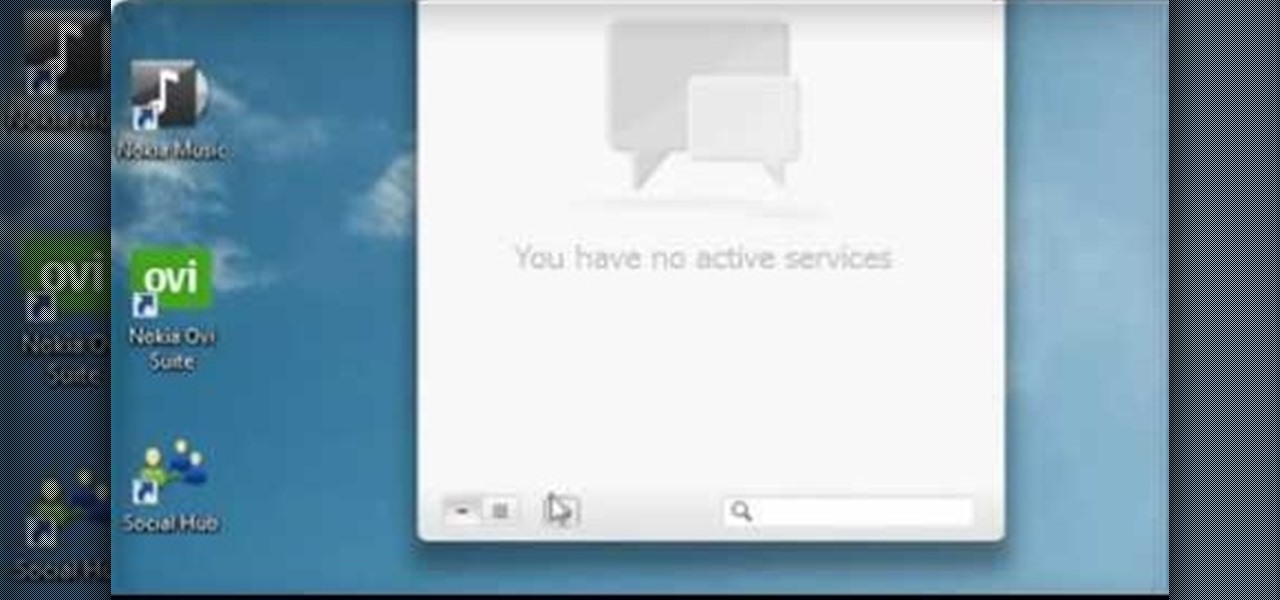
The Nokia Social hub is a fairly useful piece of software available to owners of the Nokia Booklet 3G netbook. From the Social hub, you can connect to facebook and access several of the social network's functions, including posting an update. If you have a SIM card inserted with an active 3G connection, you can even send a text message from the netbook.

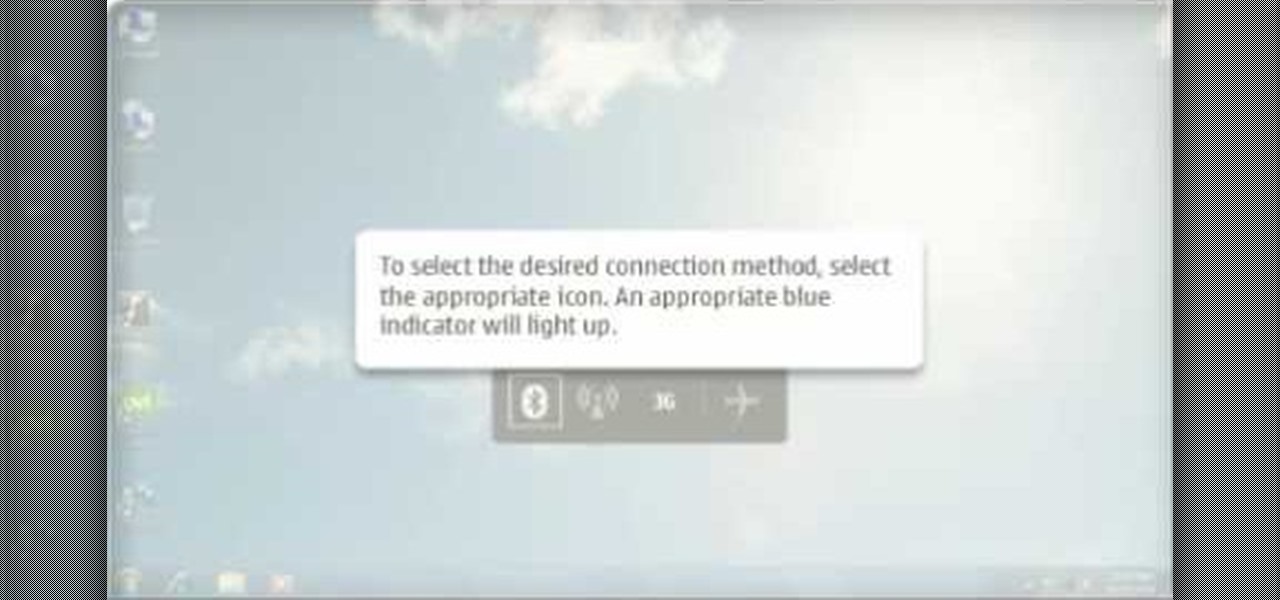
If you hit the FN + F10 keys on your Nokia Booklet 3G, you'll see the available internet connections methods for your netbook including Bluetooth, wifi, and 3G.

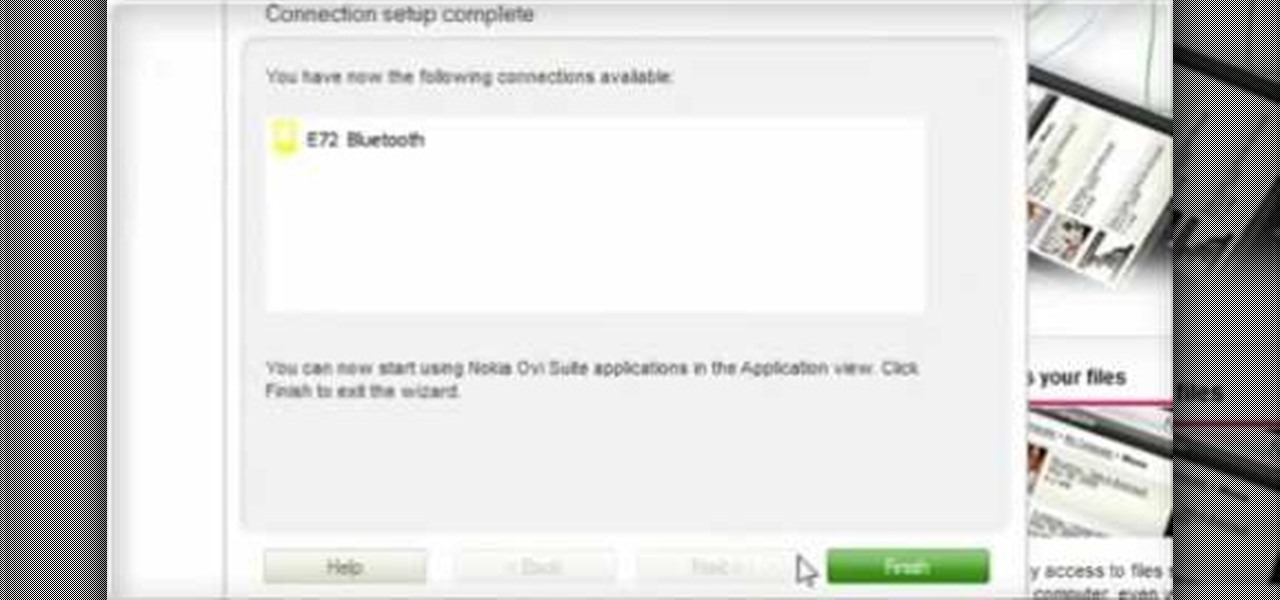
Calendar data, images, sounds, videos, and messages can be easily synchronized between your Nokia Booklet 3G netbook and supported mobile devices and phones when the two are connected using Bluetooth. To find out how to use Nokia's Ovi Suite software to synchronize your data, take a look at this tech support video from the company.