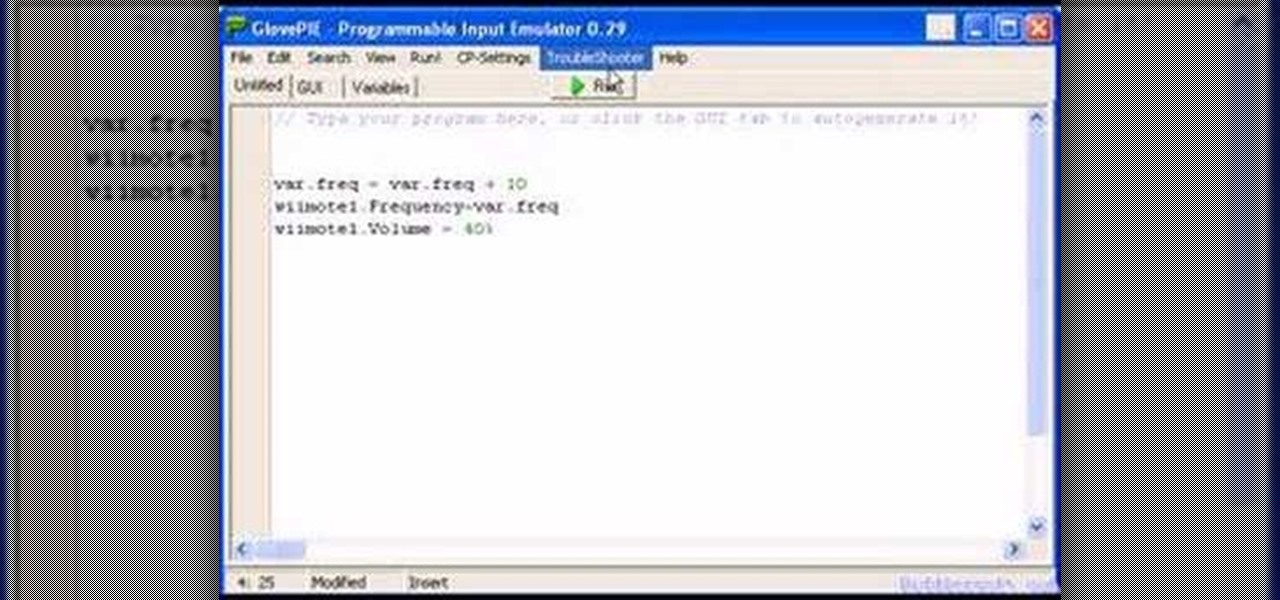
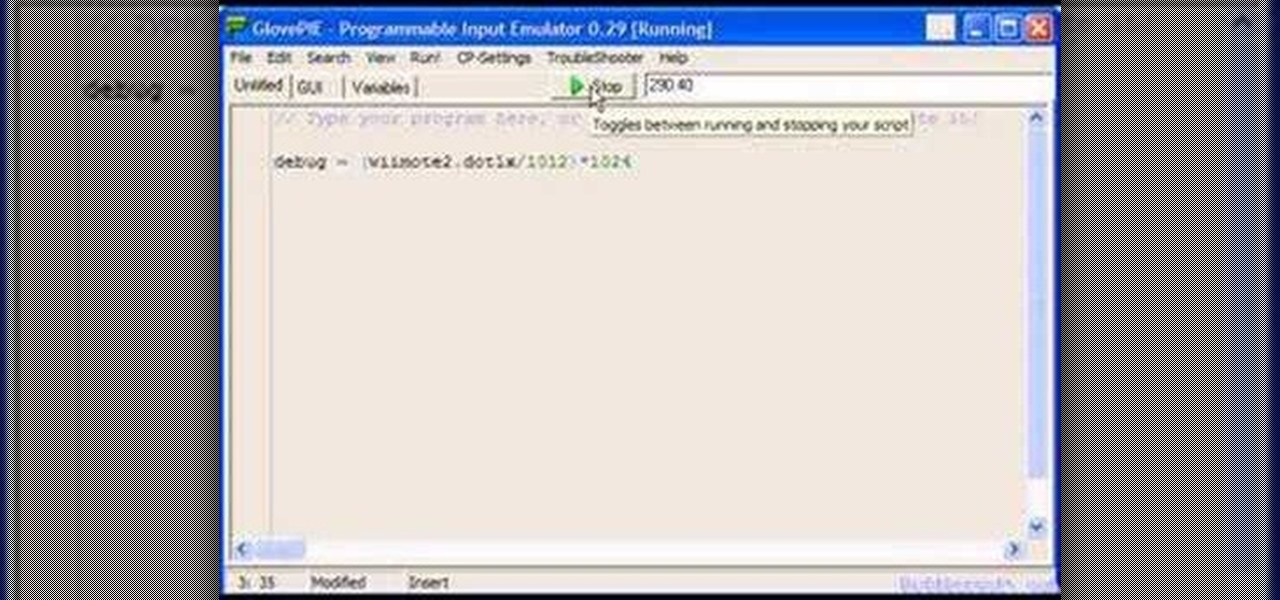
You can connect your Nintendo Wii Wiimote to your PC using GlovePie input emulation software and a bluetooth connection. Learn how you can program GlovePie scripts that will emit sounds from the Wiimote's built in speaker.

You can connect your Nintendo Wii Wiimote to your PC using GlovePie input emulation software and a bluetooth connection. Learn how to program conditionals - if, if/then, and if/else statements - in GlovePie.
You can connect your Nintendo Wii Wiimote to your PC using GlovePie input emulation software and a bluetooth connection. See how to program scripts in Glovepie to use the infra-red sensor on the Wiimote to move the mouse cursor.
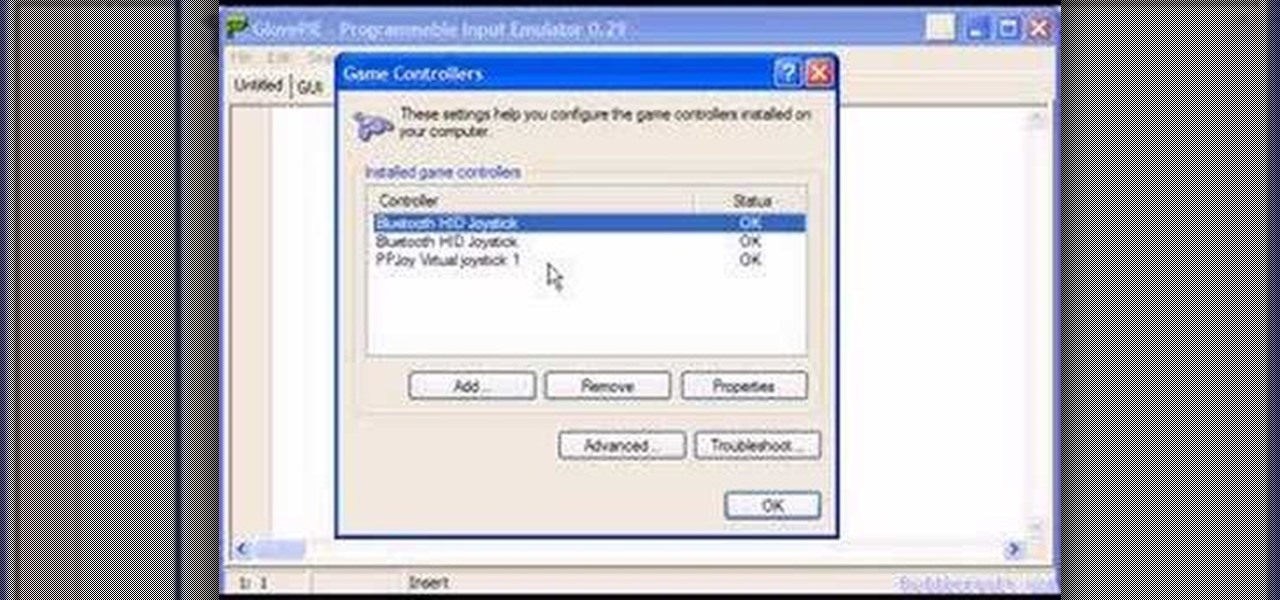
You can connect your Nintendo Wii Wiimote to your PC using GlovePie input emulation software and a bluetooth connection. Learn how to program your PC to recognize analog input or joystick/joypad input from a Wiimote using GlovePie and another piece of software called PPJOY

If you're trying to get your Nintendo Wii Wiimote to connect to your PC via a bluetooth connection, you'll need to sycronize it before you can start using it as an input device. Learn some basic scripting and programming in GlovePie, input emulation software, to get your Wiimote up and running.

Learn how to program basic script in GlovePie to allow your Nintendo Wii Wiimote to function as an input device on your PC. Using GlovePie input emulation software and a bluetooth connection you can connect your Wiimote to your PC.

It is argued that sun exposure and warm weather helps people cope with and fight multiple sclerosis. Sun is important to produce vitamin D. There are arguments that vitamin D deficiency is connected with cases of multiple sclerosis. Get a blood test to make sure your vitamin levels are optimum and you are suffering from no mineral or vitamin toxicity.

The perfection loop is used for attaching lures or sinkers to a heavy monofilament leader. The Perfection Loop knot is designed to easily create a loop at the end of the fishing line. The perfection loop is also often used by fly fisher men use the perfection loop to connect the fly fishing line and leader in a loop to loop connection.

Learn this exciting swing dance from the 30s. Sosh and Gina will start at the very beginning, no experience necessary. Learn how to dance from our instructional dance video clips (it's like a virtual dance lesson). Each? week we will post a new video clip here on our video podcast. If you're interested in more check out our site www.iDance.net.

Want to watch movies from your computer on a TV? What about just using your television as another monitor? Find out how to connect you TV to your computer and convert it into a monitor.

You can learn how to make a magical magnetic toilet roll. To do this, you need a paper roll, a piece of paper, glue, and scissors. You cut the roll into two pieces, connect the roll to the piece of paper, and mark the middle gap to make inserting the third stripe more accurate.

The docking accessories available to owners of the Motorola Droid Bionic unlock several different functions dormant in the Android smartphones. The Vehicle Navigation Dock allows you to easily access Verizon's GPS system on the go, or give vocal commands so that you stay safe and handsfree with the Droid Bionic. The HD Station Dock allows you to connect your smartphone to a TV and view photos or use applications on the big screen. This guide by Motorola shows you how to access the different f...

In this video we learn how to make a purse or handbag out of duct tape. Start out with your duct tape and a flat surface. each piece needs to be 8 inches long and laid out in front of you. Then, stick these on top of each other. Once you do this with two, take your other pieces and overlap them, then connect them together. After you have the four strips together, use a different color around the edge of this, making it with the same process. Now you will have a pouch, which will be your purse...

In this video, we learn how to build a computer. First, you will need to make sure you have all the appropriate parts for your computer. You will need to have the hard drive, cables, ram, video card, motherboard, sound card, CD burner, etc. When you start to build your computer, you will need to pay attention to where you are connecting everything. Soldering will be needed for a lot of different things and you will need to make sure you are connecting everything in the right spot. When you ar...

First of all you have to check the breast collar which is attached and hanged to the saddle. You have to maintain safety by not ducking under the horse neck. It is better for you to go around and do your job. Keep your head away from the horse head while attaching a collar. Ask your handler to hold the horse for you. Now pick your breast collar up and reach around the horse. Don’t duck under the horse head, but bring the collar belt to your side and then attach it to the ring on the saddle. N...

Need an electric outlet and don't have one? No batteries on hand, either? Well, then you should use the next best thing - potatoes! In this tutorial, learn how to make that old science fair staple - the potato powered calculator! Check it out, it really works!

If you just got some banging new subs for the trunk of your car, then you're just about ready for the ultimate car stereo. But what kind of amp are you going to get to power those subwoofer speakers? Learn about the basics of car amplifiers in this video from Sonic Electronix, where they discusses the purpose of a car amplifier, as well as the parts of the amplifier. This includes the terminals, adjustments, types of amplifiers, and amplifier channels. Before putting together your first after...

Design your own clothes by making sewing patterns, but pay attention to the details. You Will Need

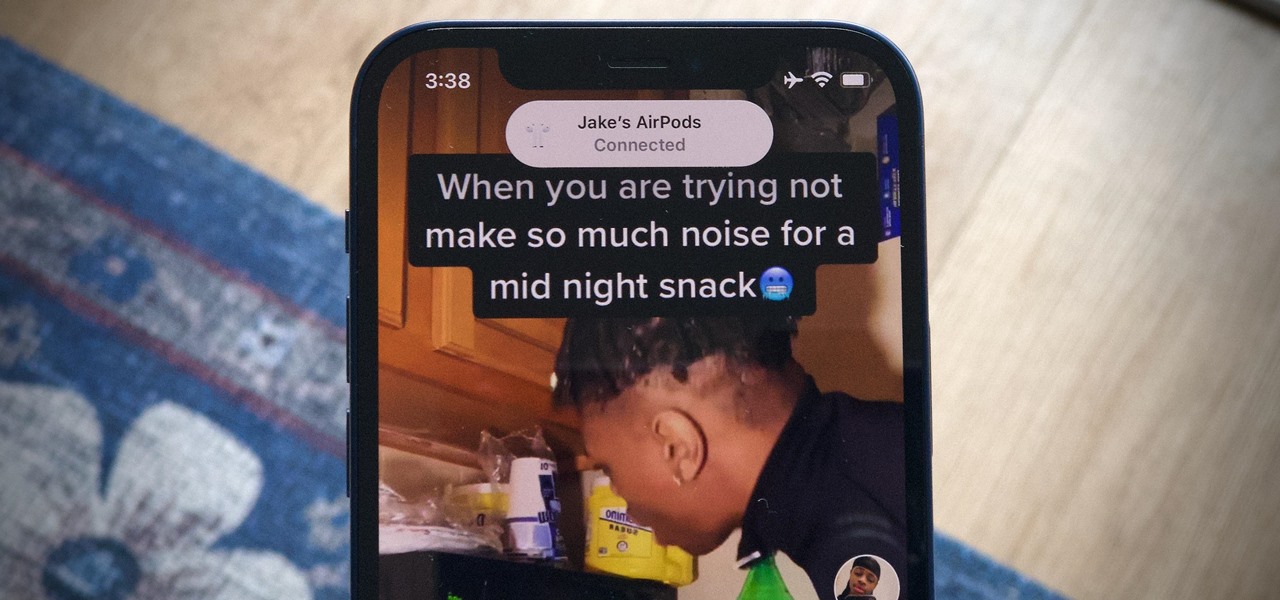
You're watching a YouTube video on your Mac, then go to check something on your iPhone. Of course, because you had a video queued on iOS, your AirPods automatically switch from your Mac to your iPhone. Now, your Mac's YouTube video is playing out loud, and you have to reroute your AirPods back over to macOS. Luckily, there's a hidden setting you can change that fixes this whole issue.

These days, you can FaceTime with family and friends whether you're at home connected to Wi-Fi or on-the-go with mobile data. You may have noticed, however, that your iPhone will sometimes drop Wi-Fi and rely on cellular instead — whether you're placing or receiving a FaceTime call. While that's not an expected result, there is a workaround to get your FaceTime calls back on track.

A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us to see where the computer has been.

There's definitely some malware-ridden apps on the Play Store. When it comes to the third-party apps you've connected to your Google Fit account, some have a crazy amount of permissions they have no business accessing. For example, you probably don't want a heart monitor app having access to your personal location data.

True home automation doesn't require interaction from the user. But let's be real, no system is going to be 100% autonomous. You'll always need a manual override for situations programming can't account for. So what's the best manual override system? I'll tell you right now, it doesn't involve yelling at Alexa or Google.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

Fireworks are the best part about the Fourth of July and other celebrations, but they can easily cause accidental injuries. It's both safer and more fun to set them off remotely, so we'll hack some standard fireworks with nichrome wire, a relay, and an Arduino to ignite remotely over Wi-Fi using any smartphone or computer.

Let me paint a picture for you. You're on a long flight home, and while listening to music on your Samsung Galaxy S10, a great song comes on. You want your friend to hear it too, who's also listening to music using a pair of Bluetooth headphones. Thanks to Dual Audio, you can easily share your experience.

With the growing list of products Apple offers, the number of devices connected to your Apple ID can get quite extensive. Having all those devices connected to your Apple ID helps you keep track of them, but when it comes time to part ways with an Apple TV or Apple Watch, those devices can still be attached to your Apple ID. In some cases, this could affect the overall security of your account.

Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

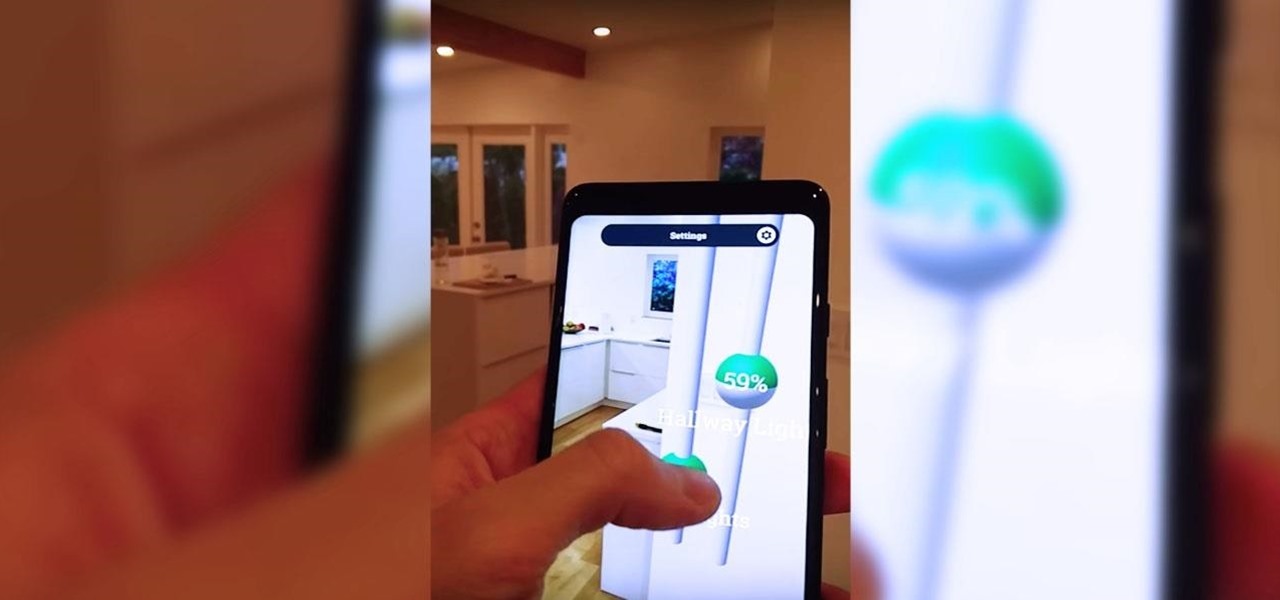
Voice-activated digital assistants from Amazon, Apple, and Google currently have the upper hand for home automation integrations, but a new augmented reality mobile app promises to give homeowners and renters visual control over their connected appliances.

If you're on iOS 11.4.1 or iOS 12 and go more than an hour without unlocking your iPhone, an "Unlock iPhone to Use Accessories" message will appear whenever you connect your iPhone to a computer or other device that tries to use the Lightning cable's data lines. This is to protect you, but it can be annoying if you have no reason to believe that law enforcement or criminals will have access to your iPhone.

Since the San Bernardino shooting in 2014, Apple's been engaged in a game of cat and mouse with law enforcement. Authorities want access to evidence on criminals' iPhones, but Apple wants to protect all of its customers' personal data equally. The latest installment in this saga has Apple outright disabling the Lightning port.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

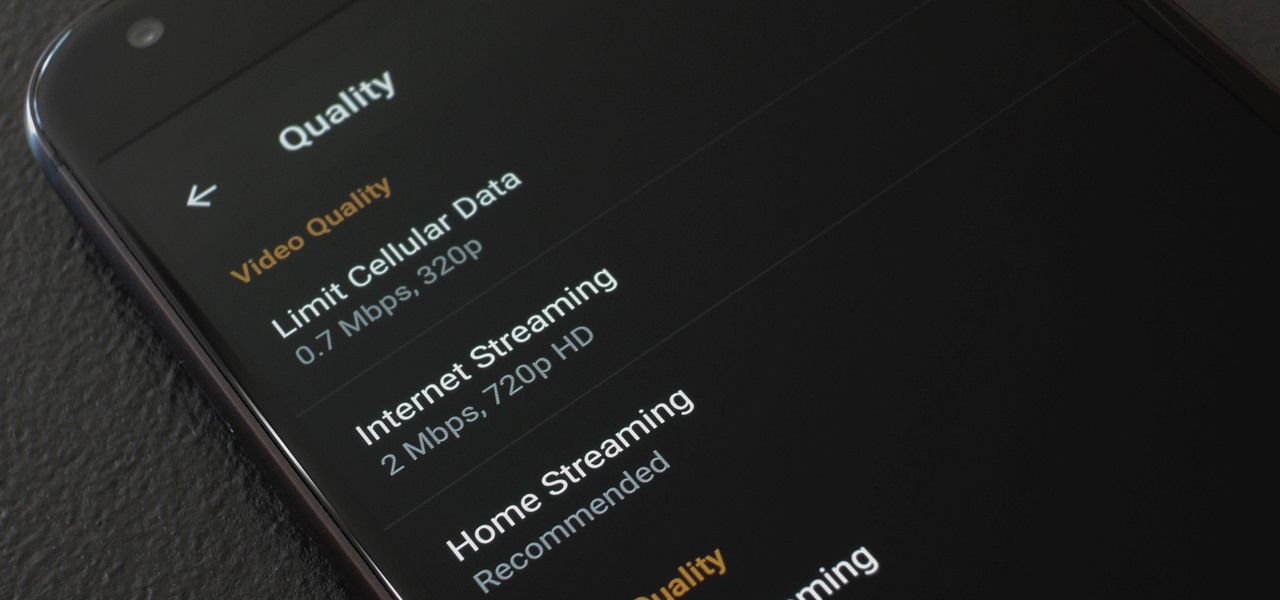
When you're on the go, Plex makes sure your media always stays with you. Just install the server app for Mac or PC and enable remote access, then you can stream movies and TV shows from your computer to your phone over the internet.

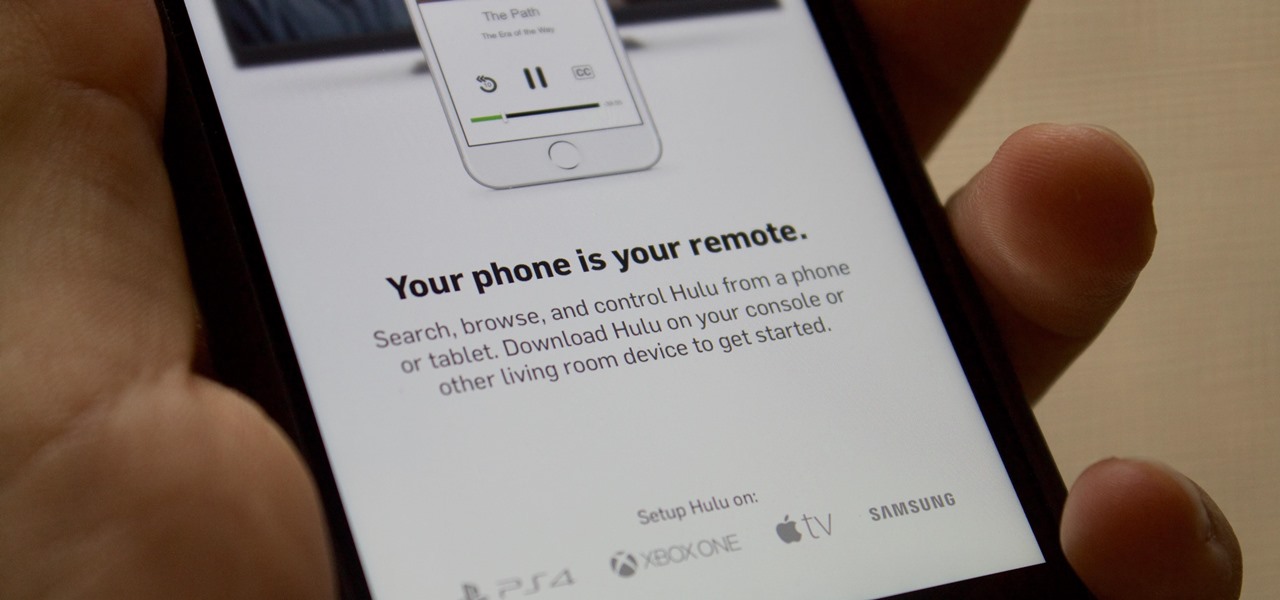
Your smartphone is the perfect place to watch Hulu on the go. Whether you're looking to catch up on your shows in a hotel, or your phone is the only screen available, mobile streaming can be a lifesaver. But what about when you have access to a TV? Wouldn't you rather watch your favorite Hulu Original on the big screen than on your comparatively tiny smartphone?

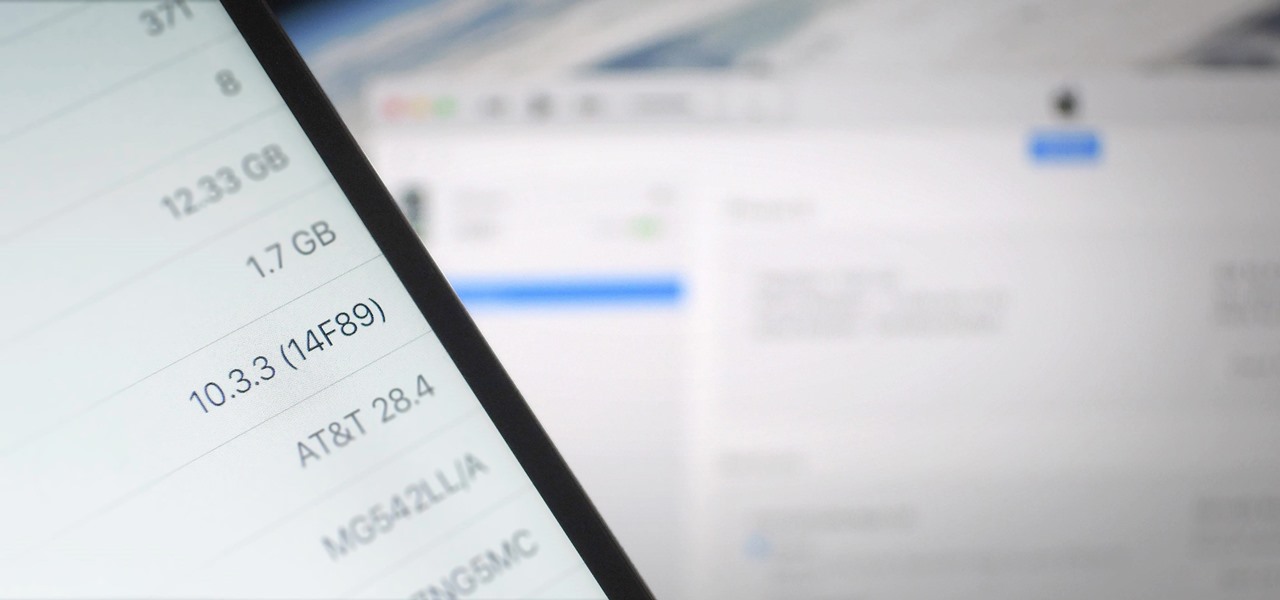
There's lots of new stuff in iOS 11, but just because things have changed doesn't mean they're better. So if you've updated to Apple's latest OS and decided it wasn't for you, you'll be happy to know that you can still go back to iOS 10.3.3.

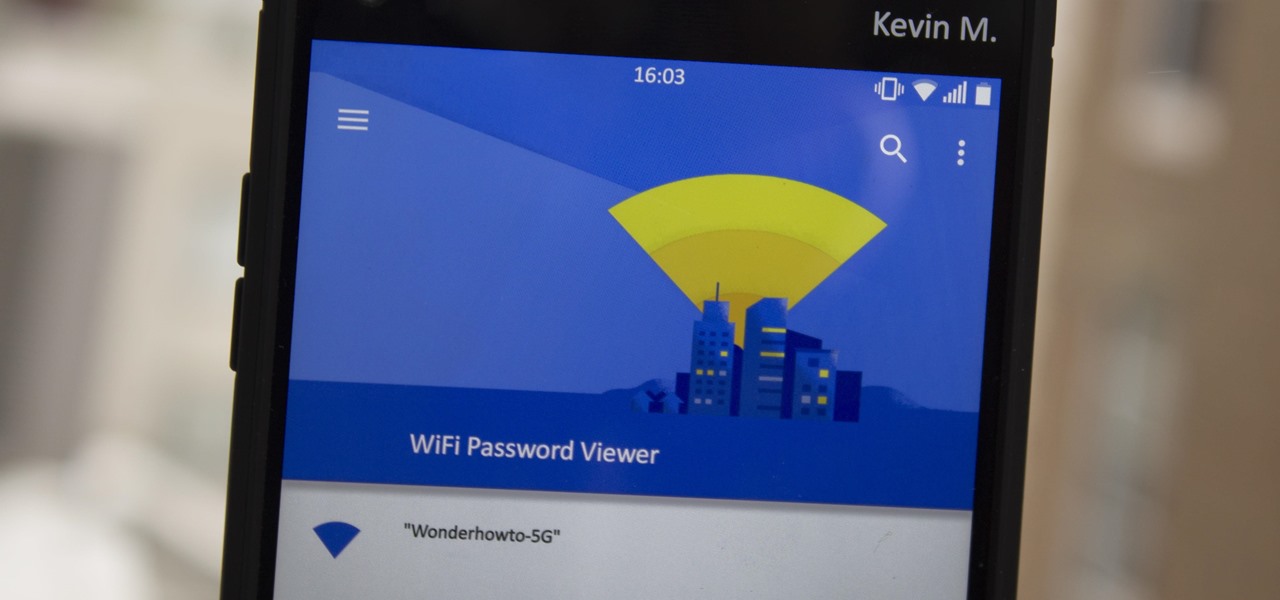
Have you ever gone to a friend's house and not asked for the Wi-Fi password? Probably not, and the same can likely be said of any friends that come over to your place. But the actual act of sharing Wi-Fi passwords is still incredibly clunky, and it's particularly hard if you have a nice and secure password with uppercase and lowercase letters, numbers, and symbols.

If you need to do some hardcore multitasking on your Windows PC, a second monitor can go a long way towards getting things done. If you opt to "extend" your Windows desktop across a dual monitor setup, it's as if you have two computers side by side, with each display getting its own set of windows and programs that can be open simultaneously.

Google's new Project Fi cellular carrier has been making waves across the mobile industry, so we decided to put it to the test against T-Mobile, one of the more established networks. For the actual testing, we slapped a SIM card from each carrier into two identical Pixel XL phones, which offer full compatibility with both networks.

The Pixel and Pixel XL come with an awesome data-saving feature called Wi-Fi Assistant that automatically connects to open internet hotspots, then creates a secure VPN on your device to keep your data safe.

The skinned versions of Android that come with Samsung, LG, and HTC phones usually have a feature that displays a small icon in your status bar when you connect a pair of headphones. It lets you know that your earbuds are plugged in or connected properly, and offers assurance that your music won't be blaring out of the loudspeaker—but mostly, it's just a nice little touch.