Ah, subscriptions. Whether you love or hate them, they are now a fundamental part of our increasingly digital lives. If you have some essential subs on your iPad, iPhone, or Mac, like Apple Arcade, Apple Music, Apple News+, Bumble, Pandora, Tinder, or YouTube Premium, there are three key issues you need to know about that could unexpectedly stop your membership from renewing.

It's pretty much a given at this point that Facebook has a lot of data on us. While you might be conscious of the data you share with Facebook when you post, upload photos, or chat with friends on Messenger, you might not be thinking about all the data it receives from websites and apps you use outside the social media giant. Now, you can actually do something about it.

It feels strange to be walking through an open field in a small village in the English countryside. There's no one else around — just the four of us: me, my husband, my 12-year-old son, and my adult niece. The day is spectacular, particularly for England. The sun is shining, and the temperature is in the low '70s.

Web applications are becoming more and more popular, replacing traditional desktop programs at an accelerated rate. With all these new apps out on the web comes various security implications associated with being connected to the internet where anyone can poke and prod at them. One of the simplest, yet the most prevalent types of security flaws found in modern web apps are SQL injections.

It always looks different when it's not about you. The Internet is our world's Alterego. Those many bits don't really make sense unless we want them to be valuable, to mean something.

Emoji have taken over the world, so there's a good chance you regularly use (or overuse) emoji on your iPhone's keyboard just like everyone else. But before emoji were popular, there were emoticons, short for "emotion icons" — and iOS has a secret emoticon keyboard just waiting for you to unlock.

Apple's iOS 16 for iPhone includes even more ways to customize your Memoji characters, and it even removes some barriers that were in place in iOS 15.

As the U.S. inches closer to herd immunity and reopening after the pandemic, it may become necessary to keep your COVID-19 vaccination cards on you at all times to gain access to places and events that are prone to spreading the coronavirus. You probably won't want to lose your card, so it may be wise to load a copy onto your smartphone for easy access.

Most of the images in your iPhone's Photos app contain exchangeable image file format data known as Exif or EXIF data, which has several helpful uses. You can use countless apps capable of reading Exif data, many of which are paid or limited. But you already have an app on your iPhone that can give you important details about each image — and I'm not talking about the Photos app.

If you'd rather be gently relaxed out of bed instead of stressed out at loud alarm sounds, there are a few things you can do on your iPhone. One of your best options is to use carefully selected songs that start out calm and soothing and gradually increase in intensity and volume. But you could also use a more intense track you know will wake you up, only set to ascend in volume to ease you out of slumber.

Penetration testing, or pentesting, is the process of probing a network or system by simulating an attack, which is used to find vulnerabilities that could be exploited by a malicious actor. The main goal of a pentest is to identify security holes and weaknesses so that the organization being tested can fix any potential issues. In a professional penetration test, there are six phases you should know.

Google TV gives the new Chromecast a home screen full of curated content from your various streaming subscriptions, but it's just that — a home screen app. Underneath, Google's new dongle is running Android TV, meaning its home screen is just a launcher that can be installed on countless other TVs and set-top boxes.

There are countless tutorials online that show how to use Netstat and Tasklist to find an intruder on your computer. But with a few PowerShell functions, it's possible for a hacker to evade detection from the almighty command line.

Overall, iOS is more impressive than ever with its stability enhancements, security tools, suite of apps and services, and intuitive user interface. With each passing update, things just get better and better for iPhone users. But don't think for a second that this is all because of Apple's genius — many of these features were at least partly inspired by tweaks made by the jailbreak community.

Rooting. As an Android user, I'm sure you've heard the word once or twice. According to Kaspersky, 7.6% of all Android users root — but for the 92.4% who don't, we wanted to talk to you.

Welcome to the first annual Next Reality 30, our list of people who've made the biggest impact on the augmented reality space in the last 12 months — and what a 12-month roller-coaster ride it's been. Apple introduced ARKit-powered apps last fall, Google launched ARCore for Android soon after, Snapchat began monetizing AR, and the Magic Leap One headset finally came out. These are historic times.

Ports allow network and internet-connected devices to interact using specified channels. While servers with dedicated IP addresses can connect directly to the internet and make ports publicly available, a system behind a router on a local network may not be open to the rest of the web. To overcome the issue, port forwarding can be used to make these devices publicly accessible.

To name just a few companies, VK, µTorrent, and ClixSense all suffered significant data breaches at some point in the past. The leaked password databases from those and other online sites can be used to understand better how human-passwords are created and increase a hacker's success when performing brute-force attacks.

THC-Hydra is a remote dictionary attack tool from The Hacker?s Choice group. It?s a well made tool that supports a lot of protocols and options. The following protocols are supported: TELNET, FTP, HTTP, HTTPS, HTTP-PROXY, SMB, SMBNT, MS-SQL, MYSQL, REXEC, RSH, RLOGIN, CVS, SNMP, SMTP-AUTH, SOCKS5, VNC, POP3, IMAP, NNTP, PCNFS, ICQ, SAP/R3, LDAP2, LDAP3, Postgres, Teamspeak, Cisco auth, Cisco enable, LDAP2, Cisco AAA. Audit remote password using THC-Hydra.

Leaving your wireless router at its default settings is a bad idea. The sad thing is, most people still do it. Once they've penetrated your network, hackers will change your router settings so they'll have an easy way back in. This allows them to change your network into a shell or proxy so they can forward their traffic anonymously through you when committing other dirty deeds.

Minecraft is the ultimate creative tool. Countless worlds filled with fantastic projects have been built to extraordinary scale in single player and SMP. This Saturday, we will be recreating some epic builds and going over things like scaling, design, detail and organization.

For some, adrenaline beats out every time. Though I've seen countless videos of base jumping, the sport never ceases to amaze. The video below, Last Walk Around Mirror Lake – Boom Bip (Boards of Canada Remix), is no exception to the rule. Shot in Norway, FroschYankee's footage is nothing short of stunning. *For more info, check out Adrenaline Rush (The Science of Risk), the film which this clip was featured in.

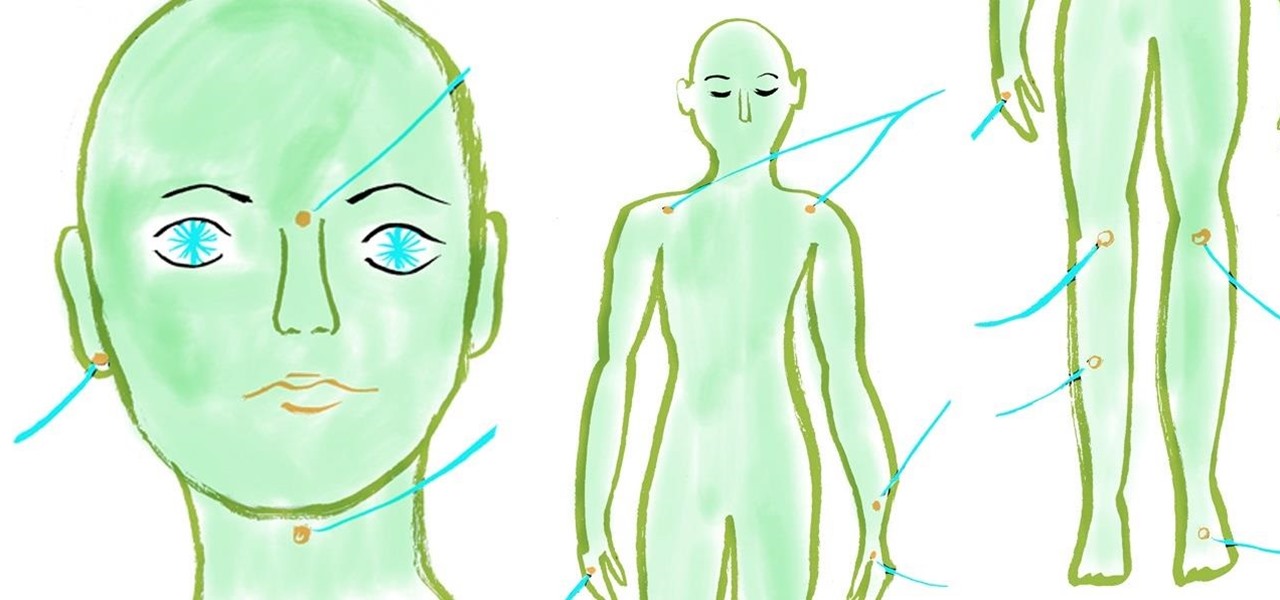
The next time you're feeling tired and stressed out, pull down on your earlobes firmly for a few seconds, or apply firm pressure to the indentation on your nose bridge between your eyebrows using your thumb for several minutes while breathing deeply. Sometimes a little acupressure is all you need to give an extra lift to your mental and physical health.

Are you one of countless Facebook users who find the classic Thumbs Up symbol tiresomely sycophantic? You're not alone. Back in August of 2010, the widespread addition of an "official" Thumbs Down symbol to Facebook pages quickly revealed itself to be a scam, but only after countless users opted in.

For the hefty price of $200 and up, you can be the proud owner of the world's first 3D printed bikini. And not just the first bikini, but reportedly the first functional and affordable item of ready-to-wear 3D printed clothing on the market. Created by Continuum Fashion, the N12 3D printed bikini is revolutionary because it addresses the technical challenge of creating flexible "textiles" with 3D printed material. The bikini is made of a material called Nylon 12, which is entirely waterproof.
to be honest with everyone, this is probably the first thing ive written about magic the gathering, but i figured i might as well start somewhere. in the game of magic the gathering there are countless different keywords, some being common, like trample, or rarely used or seen, like splice. what i wanted to do was take a closer look at some of the different keywords out there, and see just how they change the average game.

Martha Stewart and kids editorial director Jodi Levine shares ideas for decorating Easter eggs with crepe paper. Crepe paper is one of my favorite materials. It's actually tissue paper that has been reinforced with sizing and "creped," a crinkling method that yields a medium that is incredibly pliable yet sturdy enough to iron and sew. Beautiful and durable, it lends itself to countless applications. In fact, I walked down the aisle with a bouquet of crepe paper blooms! I recently realized ho...

Your iPhone's name matters more than you might think. It shows up when AirDropping files to other Apple devices, when keeping tabs on your devices' locations via Find My, and when syncing with your computer. While "Jake Peterson's iPhone" gets the job done, I'd rather give the phone I spend all my time with a proper name.

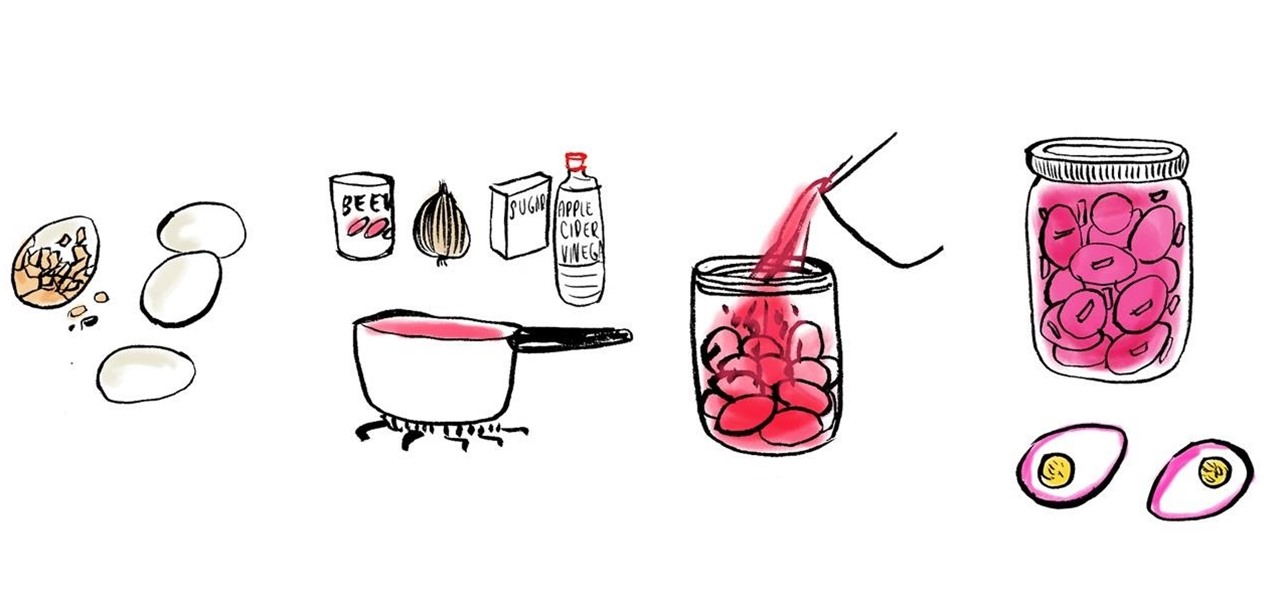
If you ever end up with an excess of raw eggs in your refrigerator, but don't know how to use them all up before their expiration date, the solution is simple. Hard-boil and peel them, place them in a sterilized jar, add pickling brine solution, and store in the refrigerator for up to one month—even more.

Lifehacker posts an article on the art of cracking weak passwords, courtesy of Internet standards expert, CEO of web company iFusion Labs, and blogger John Pozadzides. Pozadzides certainly knows a thing or two about password logic. (Note: this information is not intended to hack into accounts, but rather to protect you from using weak passwords).

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

Minecraft is not just a game. It is a creative tool. Over the past year and a half countless epic builds, servers, and community projects have been undertaken. I'm sure some of you have seen the one-to-one scale recreation of the Starship Enterprise from Star Trek or the epic server Godcraft. Countless projects such as these are being worked on as we speak, and they serve to inspire us all.

Japanese game shows are legendary for being more extreme (and absurd) than their American counterparts. Chris Farley immortalized the concept in a classic SNL sketch, and MXC and Ninja Warrior have both achieved great success dubbed and subtitled on American television. A big part of their appeal is how demanding they are compared to U.S. game shows. Only a few people have actually won Ninja Warrior in its 23 seasons on the air, and MXC is a constant comedy of failure and pain.

Sticking with our theme of XBLA games with uninspiring names, we have Outland. This game shares its name with an unrelated sci-fi cult film from 1981, unrelated comic strip from the '90s, and unrelated region in World of Warcraft. Didn't exactly try hard to build name recognition. Other than that, Finnish developer Housemarque has created the best 2D platformer I've seen in years.

There are countless tap dance moves and combinations. Learn how to do a stomp hop time step tap dance move from our expert dancer in this free video clip on beginning tap dancing. Do a stomp hop time step dance move - Part 1 of 15.

There are countless tap dance moves and combinations like the Cincinnati. Learn how to do a Cincinnati tap dance move from our expert dancer in this free video clip on beginning tap dancing. Do the Cincinnati tap dance move - Part 1 of 15.

Yesterday, Mojang announced their next video game project 0x10c, and the response has been tremendous. Discussions have covered everything from the math mystery over the game's name, to creating projects that interpret the assembly instruction code the in-game computers use (more on that later), to the debate over why a monthly fee would be required to play online in the "multiverse". To answer that last one, Mojang wants to run everyone's virtual computers in their cloud, even if the user is...

In the first part we differentiated the two types of control, mental and physical. In part 2 we will dig deeper into Physical crowd control and analyze examples that are present today.
Does this video prove that otherworldly intelligent life has visited Earth? No. It does not prove anything other than there are designs ‘etched’ onto the surface of a field. Does the video immediately above prove that otherworldly intelligent life hasn’t visited Earth? Yeah, you saw it coming; no, it proves nothing more than humans are able to ‘etch’ designs in a field of grain.

The Xbox 360 is America's video game system. It was designed in America, it has better market share in America than anywhere else, and it has the most overtly macho game catalog of any console. For many Xbox fanboys, gaming heaven is shooting hordes of really well-animated things in the most intuitive way possible. Trouble Witches NEO - Episode 1: Daughters of Amalgam, released last week on Xbox Live Arcade (XBLA) for $10 by Japanese developer Adventure Planning Service, is a typical Xbox 360...