A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

There are a ton of new features in iOS 11, but some of the best ones, in my opinion, are in the Camera app. They're not huge features, but they're much appreciated to anyone who's ever taken a Live Photo or portrait, or even to those who've needed to scan a QR code quickly.

Facebook really wants us to use Messenger. For the most part, they've succeeded; theirs is one of the most popular messaging apps right now. And with yesterday's announcement of new features, Facebook is only going to make their flagship chat application better.

Cyanogen, Inc., the for-profit company that spun off from its CyanogenMod roots several years ago, has announced that they're shutting down all of their services. The company's impending demise shouldn't directly impact many Android users, but the announcement does have one major repercussion: The servers that used to host the popular CyanogenMod custom ROM have now been shut down.

How is it goin', fellow 1337 haXX0rZ! dtm here with another article, this time, we'll be looking at infecting PE files, executables in particular for this write-up. Obviously some prerequisite knowledge will be needed since this isn't really newbie-friendly. If you are still a beginner, fear not, it might still be interesting to read! Hopefully!
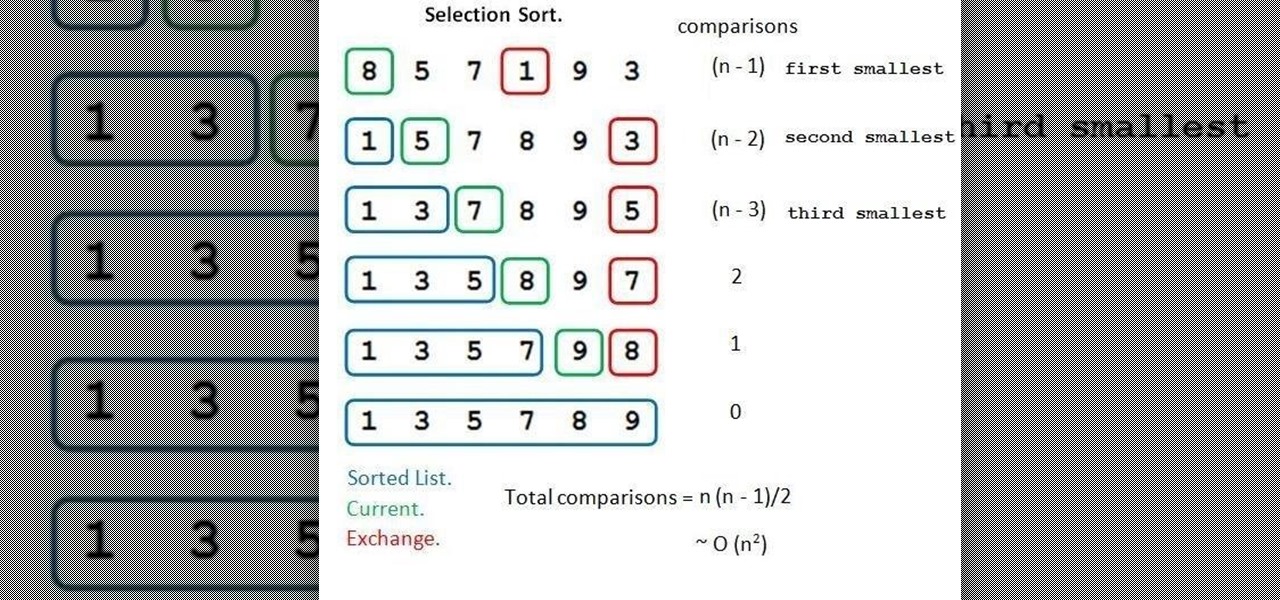
First and foremost, let me once again apologize for that bug, which I failed to notice in time. Alright, alright... Enough sulking, oaktree. Get to it!

Greetings my fellow aspiring hackers, It's still Christmas and we have a lot of things and hugs and kisses and ... to share ( you know the things that you do ). I have never done this before but I just felt to encourage you on the quest for knowledge, security and defence, skills and a whole lot more that comes out as a result of pursuing hacking. What we mean by hacking on this forum is White hat Hacking and OTW has great articles on it and I don't need to explain myself on that one.

Hello there, reader! If you've clicked on this How-to then it means you are interested in learning some C programming or just generally curious about what this page has to offer. And so I welcome you warmly to the first of many C tutorials!

Samy Kamkar, the security researcher known for the MySpace Worm and his combination lock cracking skills (using an online calculator), is back—and this time, he's after your credit cards!

Welcome back! In the last iteration of how to train your python, we covered loops, today we'll be covering something that I wish I had learned about much earlier in my scripting career, errors. We all run into them, and they can be frustrating, but there is also a silver lining to them. Today, we'll be discussing why some errors are unavoidable, and what we can do when we run into them. Also, this article will be more of a concept and less of writing actual code, but the information is equall...

I'm sure that many of us have heard of that nasty Shellshock vulnerability, but not very many people know how to exploit it. Try these few tricks on vulnerable websites!

The bread at your local supermarket will most likely always be fresh, but how do you know which loaf is the freshest out of the bunch? You can squeeze and inspect them like an annoying TSA agent, but there's actually a much simpler way to do it.

WhatsApp is one of the most well-known and most utilized cross-platform chat applications available today. It's free for one year, and only $0.99 a year after, which is chump change when you realize there are no hidden costs like international charges. Basically, it creates an easy to use forum for you and your friends to chat, regardless if they're an Android or iPhone user.

With the Android 4.4 KitKat update slated for release sometime in October (according to Nestle), I'm sure you're excited to get your hands on and test out all of the new features of Google's latest mobile operating system.

In my last article, I explained why text adventure games are some of the most Steampunk computer games out there. I even shared a free Steampunk text adventure game that I'd made myself!

Throwing a block party is a great way to meet your neighbours! Block parties are perfect for hot summer nights when no one wants to be stuck indoors. These parties are fun and easy to throw, even on a budget. Check out this video for information on how to throw a rockin' party for your neighborhood without spending much money.

The SATs are a very valuable college entrance test and could determine if you're accepted or denied to your favorite university. So, once you've learned to ace the SATs and have already taken your test, get your scores as soon as they're out! Don't sit in dreaded anticipation— go to College Board and get your SAT test results now!

This video shows you how to fix a Windows "Blue Screen of Death". You should know what to look for when you get the BSOD. You should look for the error code first and then the stock code. You should hit the F8 button upon start up to go to the last known good configuration and it will boot your computer to the last time it booted correctly. You can also start in safe mode. You will need to do a system restore. If that doesn't work do a Google search for the file name that is causing the probl...

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

Game design is among the fastest-growing industries in tech. What once was a passing hobby or niche job has become a thriving industry with a huge variety of work. If you are interested in learning game design, either as a hobby or a profession, then The 2021 Complete Learn to Code by Making Games in Unity Bundle will hold some interest for you — and it's on sale for $39.99.

The global gaming market is expected to generate $160 billion in 2020. With emerging markets in the Middle East and Africa, the planet's 2.5 billion gamers are always looking for the next great adventure.

How much screen time is too much for a child? Should you let your children have a smartphone or tablet? What age is appropriate to introduce them to technology?

We've shared a capture-the-flag game for grabbing handshakes and cracking passwords for Wi-Fi, and there are some upcoming CTF games we plan on sharing for other Wi-Fi hacks and even a dead-drop game. While security-minded activities and war games are excellent ways to improve your hacking skills, coding a real video game is also an excellent exercise for improving your programming abilities.

Apple's first AR wearable might not arrive until 2022, but we may have an early preview of what it will be like to wear a pair of its smartglasses via iOS 14.

Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.

Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.

Search engines index websites on the web so you can find them more efficiently, and the same is true for internet-connected devices. Shodan indexes devices like webcams, printers, and even industrial controls into one easy-to-search database, giving hackers access to vulnerable devices online across the globe. And you can search its database via its website or command-line library.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

Because of the way Android is laid out, you automatically lose a portion of the top and bottom of your screen thanks to the status and navigation bars. The thing is, you don't always need the navigation buttons. By hiding them, you can enjoy more of your Galaxy S10's big, beautiful display.

You may not know it, but the IPv4 address of your computer contains tons of useful information about whatever Wi-Fi network you're on. By knowing what your IPv4 address and subnet mask are telling you, you can easily scan the whole network range, locate the router, and discover other devices on the same network.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

If you're looking into buying shoes from DSW on Black Friday, then you can save an extra 20% — but only if you smile more.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

While most kids his age are busy playing Fortnite, 11-year-old Yumo Soerianto is developing augmented reality games. Kids like Soerianto are the future of the augmented reality field — they'll likely be coming into their own as professional developers right as AR technologies become lightweight and powerful enough to be contained in a pair of sunglasses.