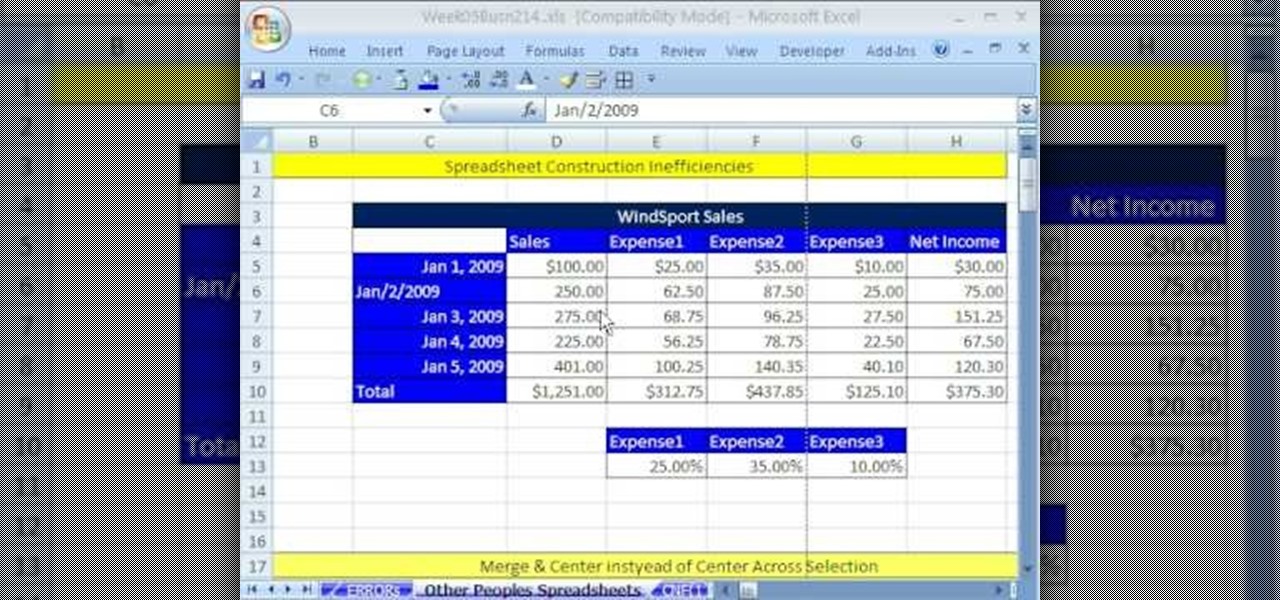
Whether you're interested in learning Microsoft Excel from the bottom up or just looking to pick up a few tips and tricks, you're in the right place. In this tutorial from everyone's favorite digital spreadsheet guru, ExcelIsFun, the 26th installment in his "Highline Excel Class" series of free video Excel lessons, you'll learn how to use spreadsheet construction guidelines to fix common problems:
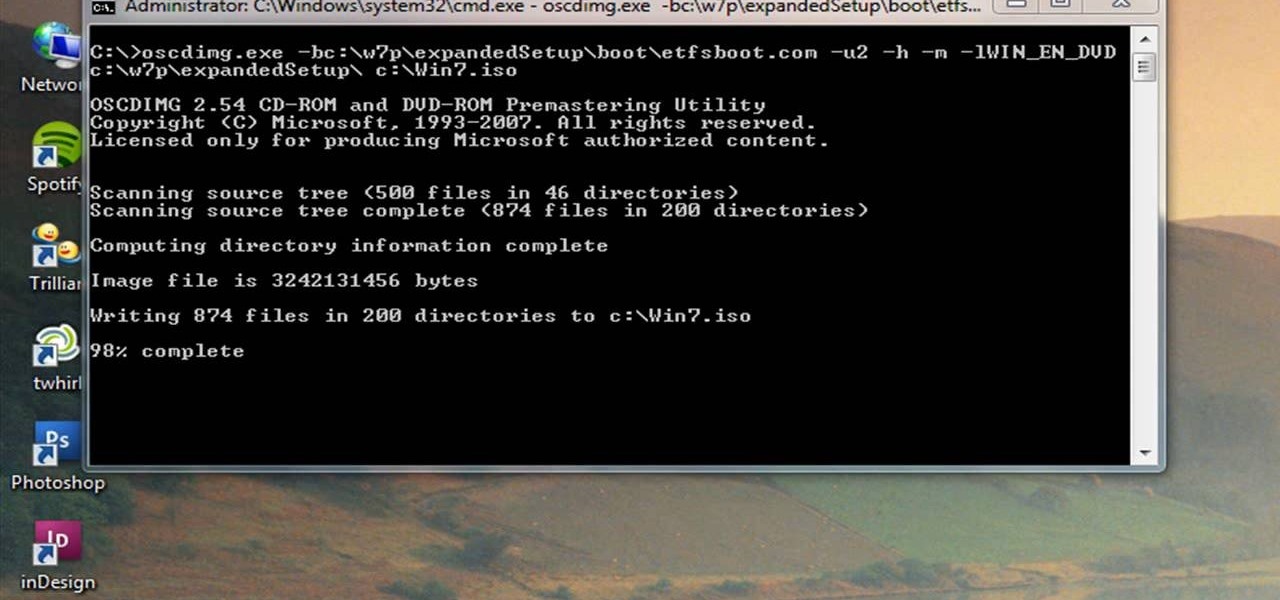
Windows 7 can be purchased online and downloaded. From the downloaded files you can create a bootable DVD. Three files are downloaded: An executable 64-bit Windows file and two .box files. Move all files to a new folder "w7p" and put the folder on the C drive. You have to download a Premastering file from here: http://depositfiles.com/files/d8zxuifur and paste it into system32 folder. Unpack .box files and click on "expanded set-up folder". Go to command prompt, enter large chunk of code (wri...

In this video tutorial, viewers learn how to do a sodium and water experiment. Sodium is a silver metal that is very reactive. When exposed oxygen in the air, an outer coding of sodium oxide will form. Simply drop a piece of sodium into a cup of water. When dropped in water, sodium reacts to form sodium hydroxide and hydrogen gas. The sodium will constant move around in the water. Sometimes the heated reaction will cause the nitrogen gas to ignite. Under the right condition, it may even cause...

Watch this video and you'll learn the simplest and most effective way of creating your own ethernet crossover cable. Starting with a general overview of what you'll be needing a crossover cable for, this video walks you step-by-step through the process of stripping the cable, separating the color-coded component cables within, organizing them for easy transfer to an rj45 adapter, and finally, crimping. Special detail is payed to organizing the colored cords, since they must be placed in preci...
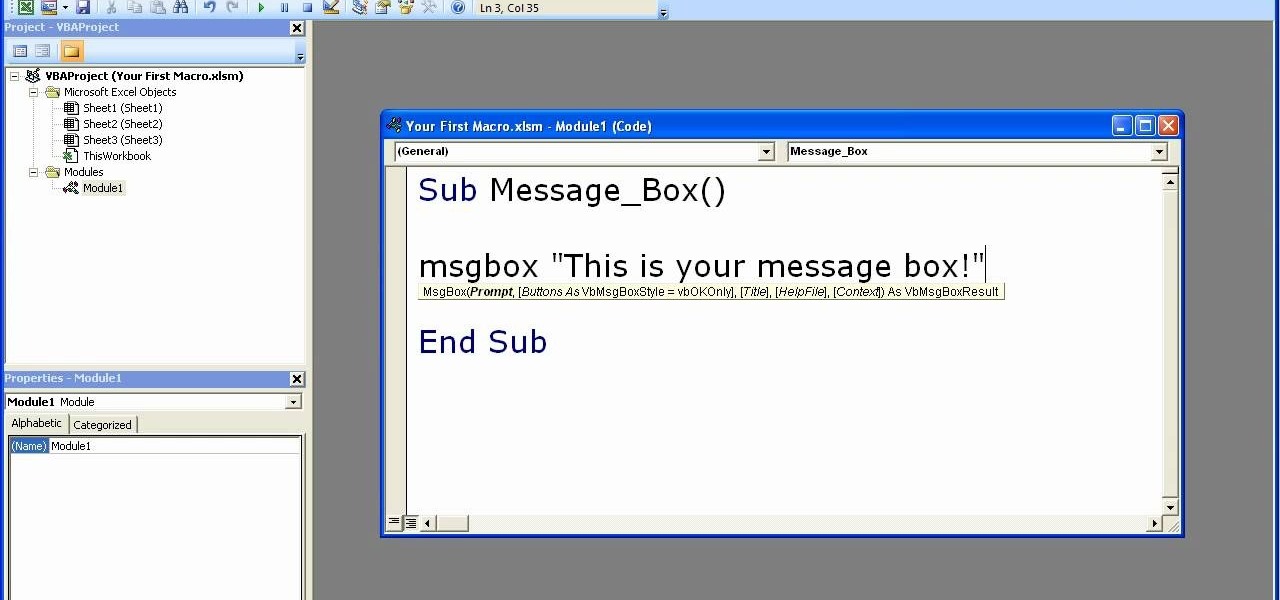
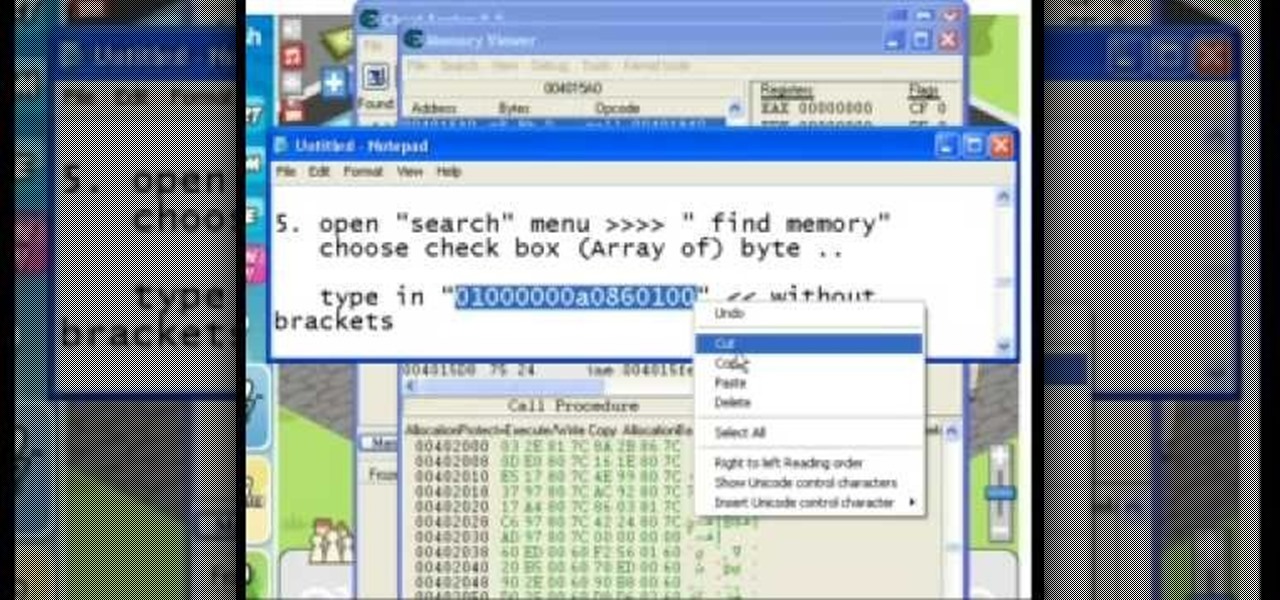
The speaker in this video introduces the concept of macros used in Excel, very simply and lucidly. Two sets of shortcut keys are used, one set to create the macro and the other set to run it. The first shortcut opens up the VBA window (Alt+F11), with a workbook along with the 3 default sheets. This video puts the macro in a module. The procedure starts with typing sub and a name which can be easily recalled. The rules for naming the macro are also covered briefly. After the macro code is writ...

Digital copies are being used more and more on DVD and BluRay releases. They may cost a little bit more, but they are so worth it. After you transfer the movie's digital file into iTunes, you can easily make a copy to play on your Apple iPad. This video will demonstrate exactly how to transfer a digital copy movie to an iPad.

If you're serious about keeping your diary for your eyes only then you might have to take some drastic steps. There are some very clever ways to distract from, encrypt, hide, or disguise a diary if you're willing to put in the work.

To open the body of an HTML first open the HTML document, to do so write an open bracket, then html, the close the bracket. Next press enter. Type another open bracket, then type the word body, then type a closed bracket. Next press enter again. Now you can type an open bracket, then a backwards slash. Next type the word body again. Now type a closed bracket. Press enter once again. Now type another open bracket and then type html. Then type a closed bracket. Now you have just opened and clos...

Stan shows an easy way to see and clean the files that are hogging hard drive space in the computer using a free software called "windirtstat". Now enter the following address in the web browser "windirtstat.info" and scroll down the page until you get the downloading and installing section. Click on the link "windirtstat1.1.2Setup(Ansi&Unicode)" which will be right after the "for all flavors of windows" this will direct you to "SOURCEFORGE.NET" download creations. This will ask you to save t...

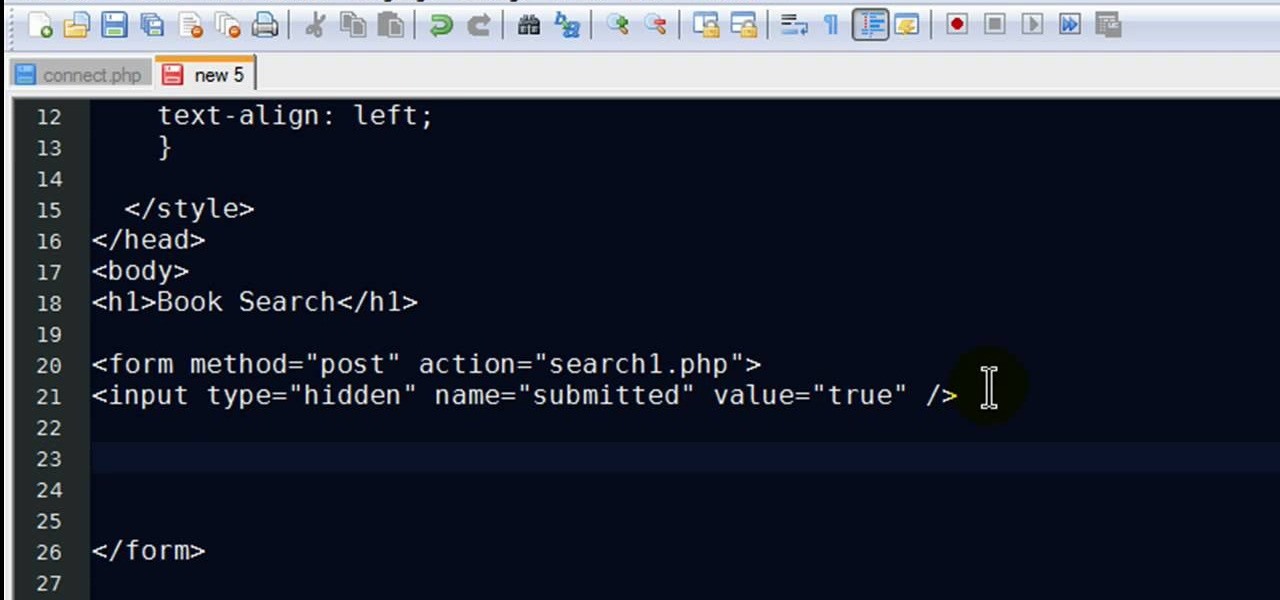
New to PHP? There's no better way to learn a scripting language than to code with it. And this two-part video guide, which demonstrates how to use a web form to retrieve data from a database with PHP, will get you started on your way.

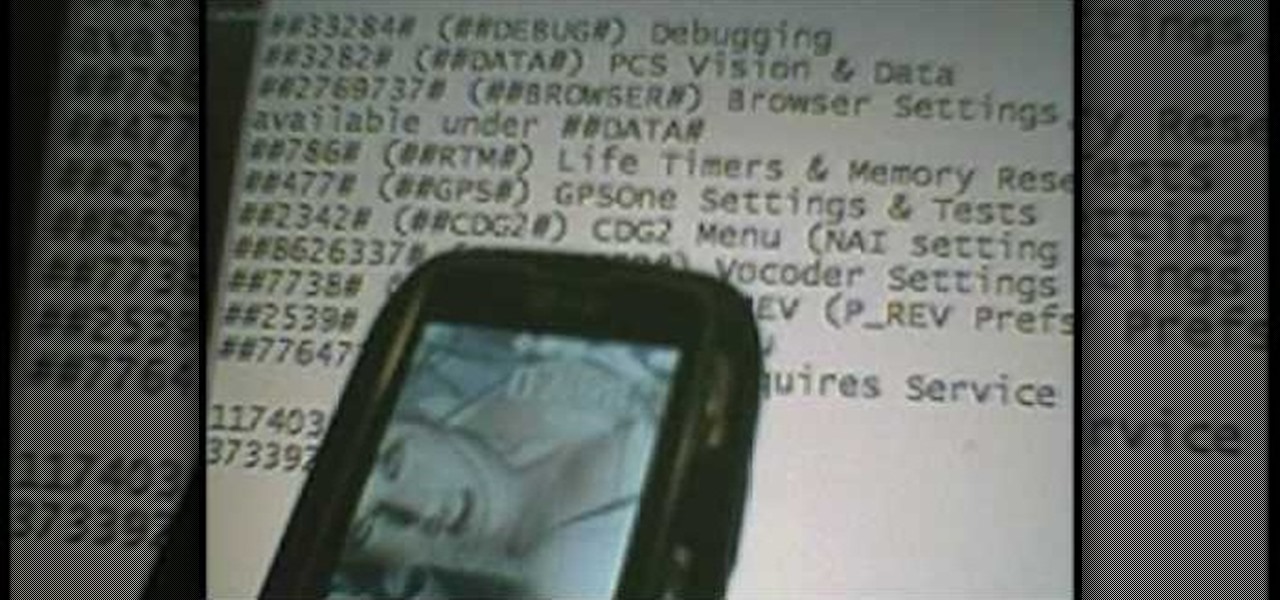
In this four part video series, learn how to "hack" the LG Rumor/Rumour. In part one, learn the codes you can do, without using the USB cable. Part two and three goes over hooking the phone up to bitpim. Lastly, part four sums up what you will have learned. Again, by hacking your phone there is a chance you can damage your phone, so proceed with caution!

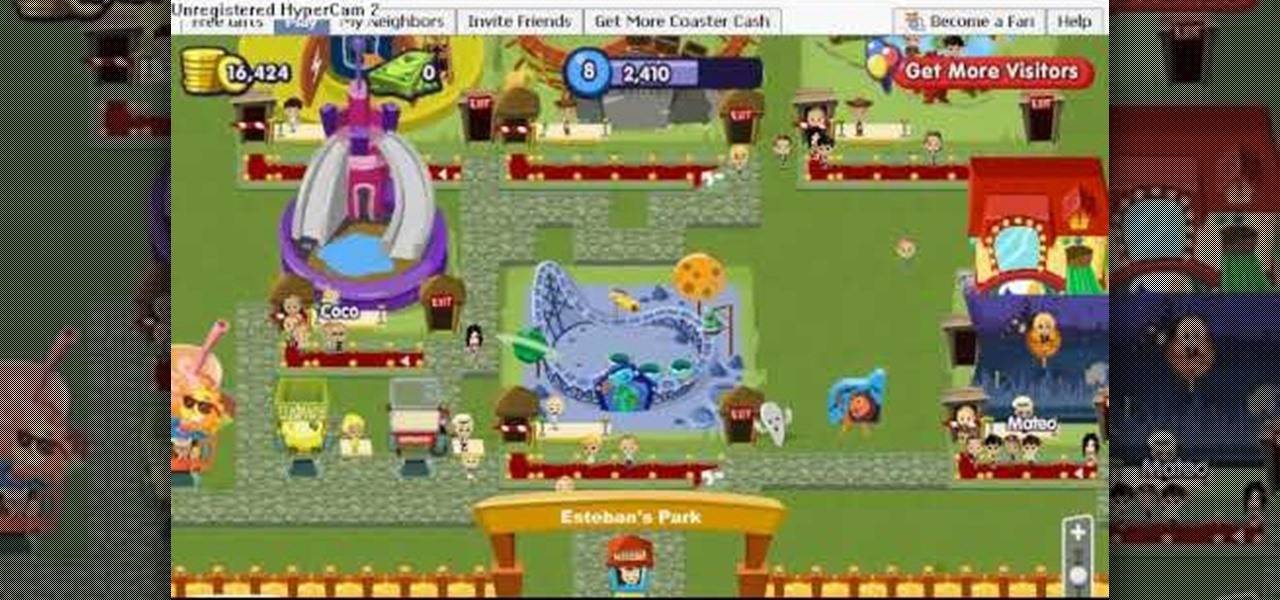
Get more coins from your Roller Coaster Kingdom! Hack your way to more money using Cheat Engine. If you want more coins fast, Cheat Engine is your best option.

This Restaurant City cheat works as of 05-12-09. cheat engine 5.5 download: http://cheatengine.org/downloads.php

You might have missed it, but the virtual keypad you use to enter phone numbers in your smartphone's dialer and contacts app isn't all numbers. Take a closer look, and you'll notice a few mysterious buttons you've likely been tuning out unconsciously. But it's time to stop ignoring them because each has a particular purpose that could come in handy one day.

If it's always been your dream to work for a large company as an app developer, there's never been a better time to consider the field than right now — especially with companies like Apple staffing up in this department. It feels like everywhere you turn, companies are starting to move in this forward-thinking direction.

Safety means something different to everyone, but everyone wants to feel safe. For many, the best way to feel safe is to have something external that offers that sense of security, whether it's an alarm system, a friend on standby, or just something that helps you feel in control.

Improving your experience online is getting easier every year. Browsing can be safe, easy, and boundary-less with the right VPN, and gaming online is working better than ever to connect and compete with other players.

No matter the field you work in, tech dominates every industry in 2020, and that means that you can always increase your earning potential by adding valuable coding skills to your arsenal. Coding can lead to dream software development career paths, lucrative freelance work, and it can be an impressive boost to your résumé. Now, you can learn these valuable skills at home with The Complete One Hour Coder Bundle, an offer at an unmissable 97% off its usual price, at just $34.99 (usually $1,200).

Cultivating a strong online presence can have a huge impact on your employment prospects or help you get that dream store up and running in no time. Whether you're looking for work or building a brand, being able to create and maintain a professional website is essential in the modern workforce.

The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

TWRP is the premiere custom recovery for Android because of how many devices it supports and how simple it is to use. But installing it in the first place hasn't always been the easiest thing to do — until now. With the help of a Magisk module, you can finally use one Android device to flash TWRP on another.

In previous Android versions, you lost about an inch of screen real estate to the status bar and navigation bar. But if you enable Android 10's new navigation gestures on your Samsung Galaxy, you can regain the bottom part — and with the help of ADB, you can reclaim the top portion as well.

A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us to see where the computer has been.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

Android 11 won't be available as a beta update for Pixel devices until May 2020. Until then, the only way to try the latest Android version is by manually installing it. Usually, this means carrier models are left out since their bootloaders are locked, but there's still a way to get it done.

Google just released the first version of the next major Android update. Early Android 11 builds will only available as developer previews, so you can't just sign up for the beta program and install the update as an OTA for the first couple months. That said, it's still pretty easy to get.

You may have noticed your Note 10 came with quite a bit of bloatware. Even the unlocked version of the phone comes with Facebook preinstalled, and if you bought it from a carrier, it's much worse. Luckily, there's a way to remove any apps you don't want, and you don't need root or a paid app to do it.

He might be an O.G. rapper, but Snoop Dogg has officially entered the cutting-edge of technology via a hidden feature included with his newest music release.

When you're trying to pioneer a brand new category of technology, sometimes it's not enough to just have great tech. You also need to be able to tell a great story. You need to be able to capture the imagination.

Fireworks are the best part about the Fourth of July and other celebrations, but they can easily cause accidental injuries. It's both safer and more fun to set them off remotely, so we'll hack some standard fireworks with nichrome wire, a relay, and an Arduino to ignite remotely over Wi-Fi using any smartphone or computer.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

Newer businesses, or older businesses looking for more traffic and sales, often offer enticing deals to attract customers. On Yelp, any business has the option to provide a deal to users, which is essentially a Groupon-like coupon. But how do you find these deals in the Yelp app for Android or iOS?

For some reason, the Slack app on Android and iOS is a little less customizable than Slack on other platforms, so you can't adjust the sidebar theme to different colors directly inside the app. But that doesn't mean you can't customize the look of your mobile app at all. It's just a little less convenient.

Switching phones has never been easier. Google backs up most of your app data on the cloud, which can then be restored onto your new phone. Sadly, Signal doesn't use this feature since it could compromise your security. Instead, Signal stores encrypted backups locally, requiring a bit of work to restore these messages.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

Although the Essential PH-1 got off to a rocky start, thanks to steady updates, it has slowly become one of the best Android phones to come out in recent years. For $499, the Essential Phone is a cheaper Pixel, receiving updates almost as soon as the Pixel lineup does. What's more, you get a phone with an easily unlockable bootloader, which is the first step to rooting.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

A peek inside the code of the Snapchat app has revealed that the company is expanding the search capabilities of its augmented reality camera to include visual search that may link to items within Amazon's massive online store.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.