Are you getting that nasty "Application access set to not allowed" error on your Nokia 5300 cell phone? Unfortunately, it's a problem for most Nokia 5300 owners, ones who wish to use 3rd party applications on certain carriers, like T-Mobile, who restricts the uses for branding.
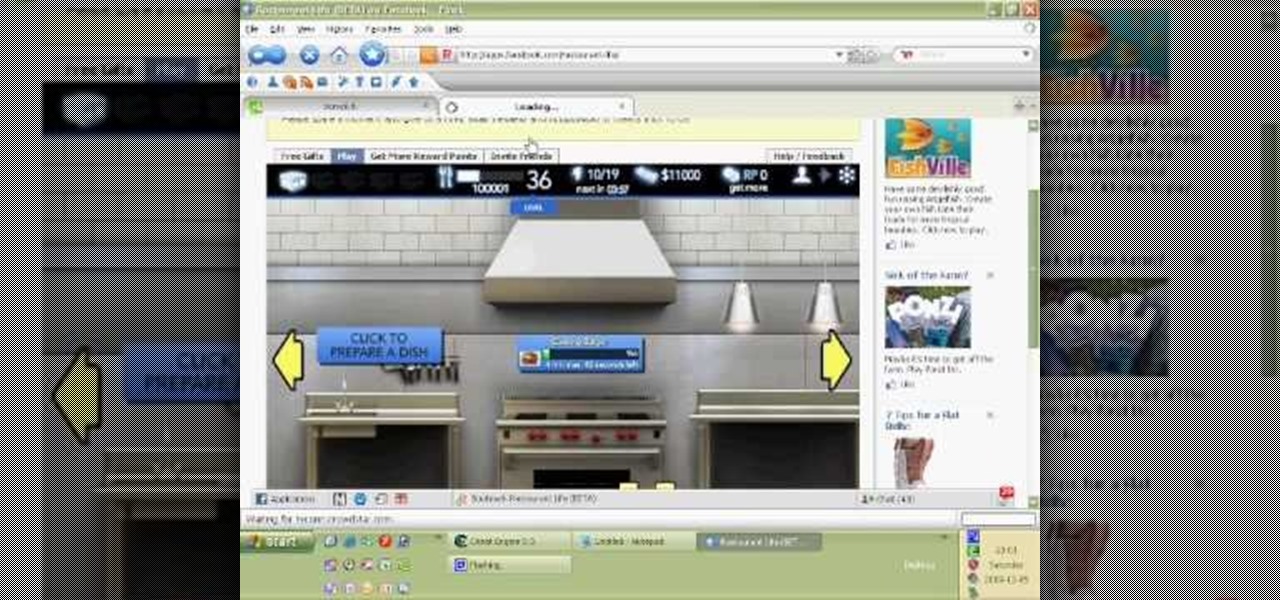
Watch this video tutorial to learn how to level hack Restaurant Life (12/05/09). 1. Open RL and Cheat Engine 5.5, then point CE 5.5 to the process of your browser.

Have an old bike combination lock that you can't remember the code for? If it's a simply four-digit cable lock, you can easily figure out the combination with a quick peck-and-go method. Best of all, this technique doesn't require any tools or special know-how, and let's you reuse the cable lock again versus just damaging it with bolt cutters. All you need is a bit of patience and you'll have your figure out your combo in no time.

In this video series, our expert Nazir Kutub will teach you how to do cheat codes for the Wii on an assortment of games. Nazir will teach you the cheat codes for tiger woods, including how to unlock all the clubs, and EA items.

Got video files on your computer? Watch them on your big-screen TV – using your Xbox! You Will Need

In many urban areas, GPS doesn't work well. Buildings reflect GPS signals on themselves to create a confusing mess for phones to sort out. As a result, most modern devices determine their location using a blend of techniques, including nearby Wi-Fi networks. By using SkyLift to create fake networks known to be in other areas, we can manipulate where a device thinks it is with an ESP8266 microcontroller.

When it comes to cybersecurity, one layer isn't enough. A complex password (or one created with a password manager) does a good job of protecting your data, but it can still be cracked. Two-factor authentication strengthens this by adding a second layer of security, giving you even more protection against online threats.

When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular phone has connected to before, giving us insight into the identity of the owner.

In 2019, the Raspberry Pi 4 was released with specs including either 1 GB, 2 GB, or 4 GB of memory, a Broadcom BCM2711B0 quad-core A72 SoC, a USB Type-C power supply, and dual Micro-HDMI outputs. Performance and hardware changes aside, the Pi 4 Model B runs Kali Linux just as well, if not better, than its predecessors. It also includes support for Wi-Fi hacking on its internal wireless card.

It is a great time to be a mobile gamer. Not only are there millions of mobile games on the Play Store and App Store, but thanks to some recent developments, we can also even play PC games. AMD recently released an app, which, among other things, lets you play your favorite PC games on your phone.

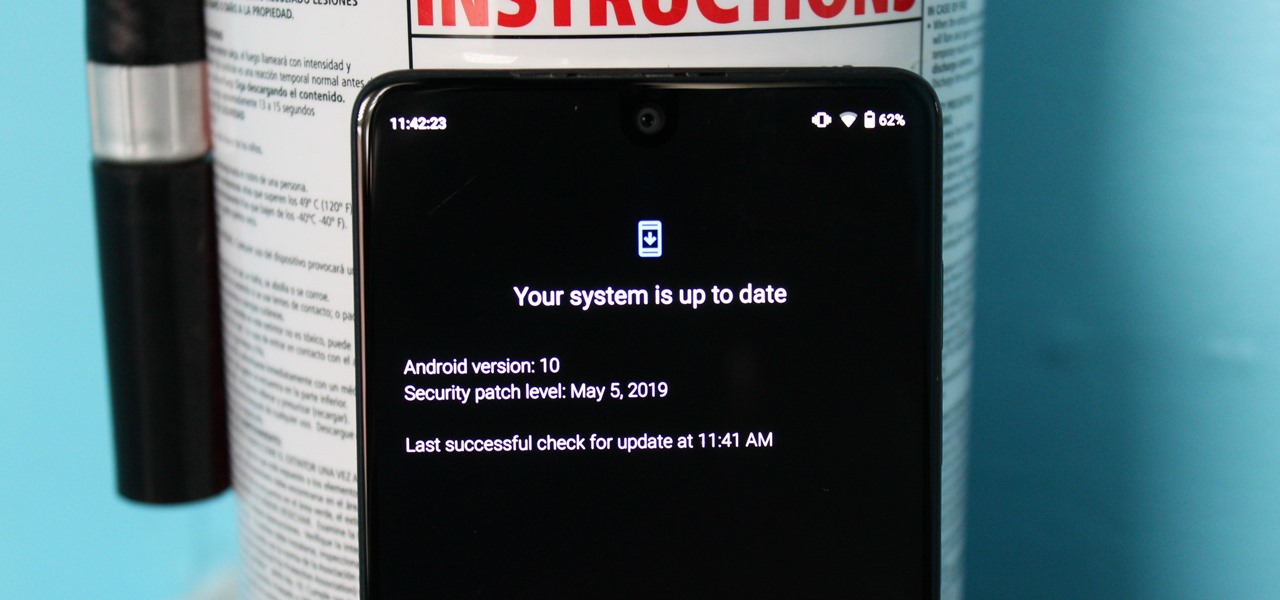
Like last year's beta release of Android Pie, Google has allowed the Android Q Developer Previews to support some non-Pixel devices. Announced at Google I/O 2019, there are 15 non-Pixel smartphones eligible for the Android 10 Beta, including 2017's Essential PH-1.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password with a security key or even a passcode with some form of biometrics, like a fingerprint or face scan.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

If you want to get started sniffing Wi-Fi networks, you usually need to start with a wireless network adapter. But thanks to a Wi-Fi sniffing library written in Arduino and the ultra-cheap ESP8266 chip, you might not need one. For less than $10 in electronics, you can build a tiny Arduino Wi-Fi sniffer that saves Wireshark-compatible PCAP files and fits anywhere.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

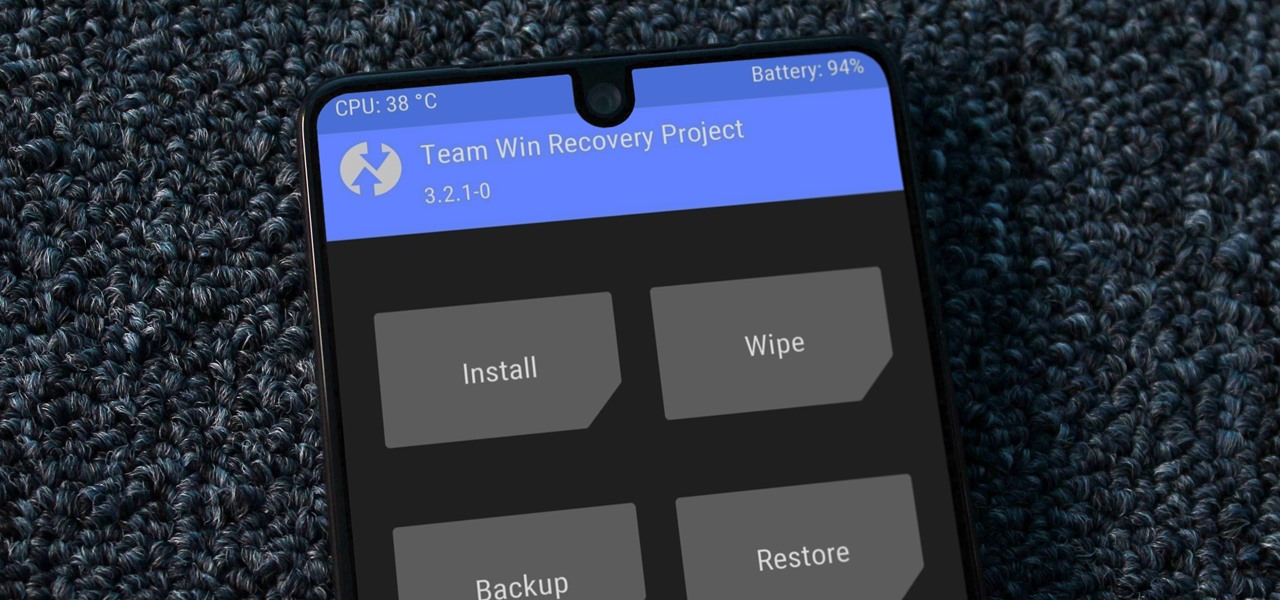
For modders, there are few tools more important than TWRP. TeamWin's custom recovery makes flashing mods like Magisk, Xposed, and custom ROMs incredibly easy, and it lets you root your phone at the press of a button. On top of that, it can make complete backups of your phone in case you mess up. That's why, for Essential users, this should be the first mod you add.

As you're surely aware, your phone can be used against you. Thanks to our cameras and microphones, a clever hacker can obtain access to your device and invade your privacy. But spying isn't limited to just these two sensors — gyroscopes, proximity sensors, QR codes, and even ads can be used to paint a very clear picture about who you are and what you're currently doing.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

Signal Private Messenger is famous for its end-to-end encryption, but you can't even use the messaging app without having a real phone number attached to it. Luckily, there is a way around this limitation, so you can use Signal even if you don't have a valid SIM card in your smartphone.

This is a lengthy, detailed series on iPhone development, for which you'll need an Intel-based Mac computer, running Mac OS X 10.5 (Leopard) or higher. Then, before you actually get started developing for the iPhone, you'll need to register as a developer with Apple. Then, you'll need to download Xcode and the iPhone SDK. Once you have all this, you can start developing iPhone applications!

In this tutorial, we learn how to make your home safe and secure with tips from Lowe's. You should do a safety check on your house at least once a year. Start with the entryway, making sure you have an insulated wood door in the doorway. Make sure there is a lock and a deadbolt lock on the door as well. Once inside, make sure you have timers to control your lighting, so it can come on even when you're not at home to detract any robbers. In the garage, make sure you have an electronic door ope...

In this video tutorial, viewers learn how to enable hidden God Mode in Windows Vista 32 bit and 7. This option does not work on Windows Vista 64 bit. Begin by right-clicking on the desktop. Then go to New and select Folder. Now name the folder to a desired name and paste this code behind it: .{ED7BA470-8E54-465E-825C-99712043E01C}. Users will now have a full list of control options for their computer system. This video will benefit those viewers who use Windows 7 and Vista, and would like to ...

In this tutorial, we learn how to eject devices from the use of the terminal for Mac. First, go to the terminal of your computer where you will see a notepad sort of page. Next, type in "df" and then press return. You will now see a list displaying processes on your computer. On the bottom will be your public zoning device, which is your USB device. Next, type in "hdiutil eject -force (the code under "mounted on)- volumes-publiczone". This is not case sensitive, but don't forget or add in any...

Ubuntu and Windows may have trouble syncing time because when they are dual booted, they both assume that your hardware clock is set to a different time setting. Ubuntu assumes that your clock is set to UTC and Windows assumes that your clock is set to local time. Answers Launchpad has solutions to fix the syncing issues. To correct the issue, configure Ubuntu to be set to local time. Launch your terminal window and click on the description box. In the code string change the UTC default value...

JamesKesn teaches you how to hack a vending machine. You must use a very specific machine and an exact combination of button presses. For this it is: far left Pepsi, near right Mountain Dew, near left Pepsi, far right Mountain Dew. Then far left Pepsi, near right Mountain Dew. Again, far left Pepsi, near left Pepsi, near right Mountain Dew and far right Mountain Dew. This hack will allow you to see the stats, set the price and see error logs.

Learn how to delete your old Yahoo or Yahoo mail account in simple steps. First open your web browser and enter the web address for Yahoo to open it. Now log into your account using your Yahoo username and password. Go the account termination page, confirm your account termination and enter code give. Finally press 'Yes' and enter your password . Now your Yahoo or Yahoo mail account will be deleted.

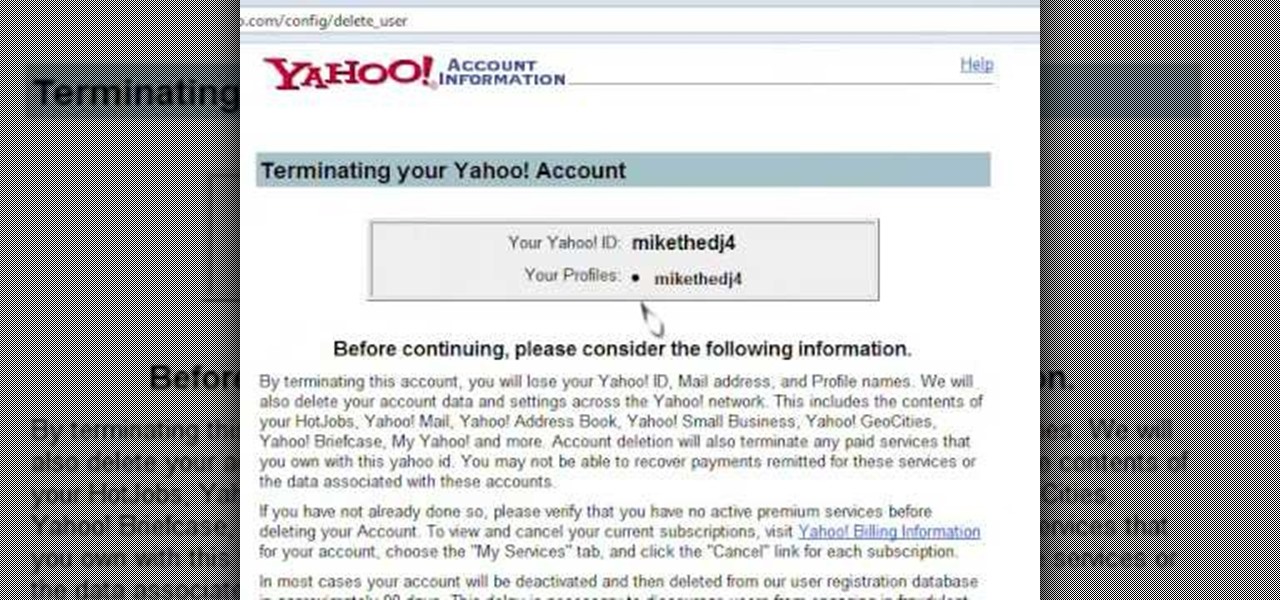
Learn how to delete your old Yahoo account from this video in simple steps. First open your web browser on your computer and go to the Yahoo home page. Now sign into your account using your username and password. Now copy and paste this link "http://edit.yahoo.com/config/ delete_user" in your address bar. Enter your password to confirm the deletion of your account. Finally enter the code to confirm and delete your account.

Learn how to change your HTML font and size with this video. First go to edit menu> preferences and then select fonts. Here there are many fonts that have their own categories-proportional font, fixed font and code view. On the right hand side, one can even change the size. Once the settings are changed, click on "OK". That's it, the font as well as its size are changed. It will help while working on the software for better viewing in case of small screens.

This video shows how to download songs from MySpace using the software Gopher. First the software should be downloaded from the site indicated. After the download is completed install the program and head over to the MySpace page where the song can be streamed. Next the MySpace friend ID should be found as indicated and the code should be entered into Gopher. Select the song to be downloaded from the list and save it to your hard drive following the steps of the video closely. Happy downloading!

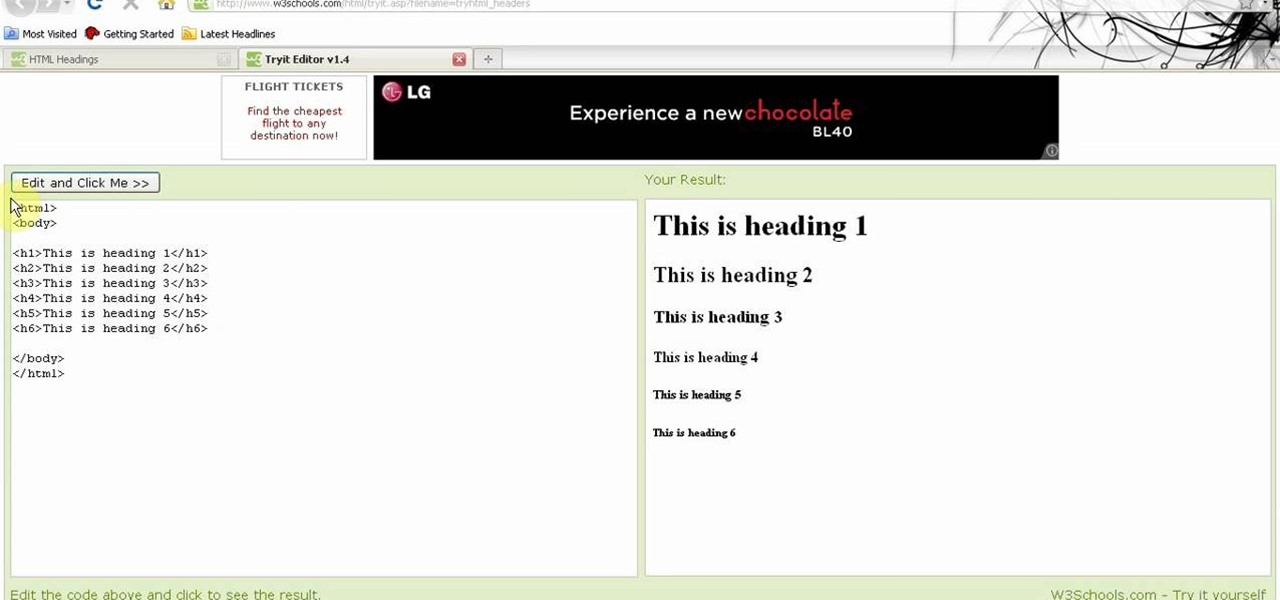
1. Visit 3schools for free and fantastic web building tutorials. 2. Find the subject you are interested in researching and simply click on it and it takes you to a video.

This video will show you how to enable MMS on your iPhone 3G and 3GS on 3.1 firmware. First, copy and paste the terminal code. Hit enter. Go back to the description and click the link to the file. Connect your iPhone and go into iTunes. Hit options, check for updates. Go to where you have downloaded the program.

Get all of the info on Thesis themes for you WordPress blog. Watch this video tutorial from 4Blogger to learn how to add a background box and color in a Thesis sidebar.

Take a look at this video if you've ever been curious on how people send video messages via the iPhone.

This video tutorial program is designed to promote ground crew safety when working under and around helicopters during external load operations. This is not a safety-training and is only intended to be used with the participation of a ground crew safety officer, trainer or other qualified personnel. All training and refresher courses must be done in accordance with federal and provincial regulations and the Canada Labour Code.

A three-part lesson in how to count and play your way through 12-bar blues changes on your harmonica. Required: a copy of "Harp Attack," a 1990 Alligator Records release.

"What's your Wi-Fi password?" That's usually the first thing guests ask for when you have them over. You tell them the network name, then try to explain your complicated hacker-resistant password, which becomes a whole ordeal. But there's a better way to do it, which doesn't rely on using the same mobile OS as your guests.

The biggest hurdle to rooting is that it usually requires a computer. Things get complicated when you're trying to use a desktop operating system to exploit a mobile OS, and the connection isn't always reliable. But with the help of Magisk, you can now use one Android phone to root another.

Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensive coding experience under your belt. On that note, we recommend Python for anyone who hasn't mastered it yet.