During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

Speakers today are a marvel for their portability and sound quality. No longer do we need giant boxes to bring down the house — a speaker that can fit in your hand can fill a room with your favorite music. This is even more important when you pair it with your smartphone, and there are lots of smartphone-friendly speakers on sale this Black Friday.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the victim portion of the shell. Today, we'll be building the attacker portion. This script will initialize interaction with the victim portion of the shell, send commands, and receive the output.

Welcome back! In our last training session, we covered some advanced list topics. We'll be going deeper into the advanced list rabbit hole today with lambda and lambda operators! (And I'm not talking about Gordan Freeman)

Hello fellow training hackers. I do not know if many of you are familiar with ruby, but since it is a useful scripting language, that hasn't been covered too much here on Null Byte, I thought why not do some How-tos about it now and then.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Why can't I see who is stalking my Facebook profile?

Apple is widely known for keeping a tight grip on iOS, disallowing open-source and third-party downloads. While there are many reasons for this, the three most frequently referenced are quality control, malware prevention, and of course—money.

If you've never heard of geocaching, it's kind of a grown-up treasure hunt you play everywhere in the world. GPS coordinates are given as clues and the players must find the cache box. There is usually a log book to write your name and a small toy or present to collect.

In this tutorial, we learn how to bypass Captcha codes on Facebook. First, go to Facebook and log into your account. Next, go into your settings, then your accounts settings. In this section, click where it says "mobile". Next, it will take you to a section where you can activate a phone. You can use your cell phone for this, because Facebook is going to send you a verification text message next. So, enter your cell phone number and when you get the text message click "activate". Now, Faceboo...

Get the inside scoop on Wizard101 hacks, cheats, tricks, tips, and walkthroughs! Watch this video tutorial to learn how to find cheat codes in Wizard101.

IPython provides a far more powerful alternative to the standard Python interpreter, incorporating features such as string-completion, code-line macros and a rich history. This is free software that Ian Ozsvald has found to enhance the Python coding experience.

Whether you're in an airport, restaurant or waiting room, the insidious grip of televisions on human life is omnipresent. Sometimes it's nice to talk to other human beings while looking at them directly—actually hearing what they have to say.

For years, you could only make purchases with your Apple Cash balance on your iPhone using Apple Pay, but a new update gives you the power to set up a virtual card number you can use just like a debit or credit card.

Your iPhone has hidden apps that work behind the scenes to filter SMS messages, trust computers, deal with payments, test ads, and perform other actions. You won't find any of them in your App Library, but there are tricks you can employ to unlock and use some of these secret apps.

If you're trying to get your start in the web development and IT field, then one of the best places to begin is by building confidence with your coding by practicing Python and sharing your work on Git & Github. The Learn Python & Django Developer Bundle can help get you up to speed in Python, Django, Git & Github, and more, and right now it's on sale for $29.99.

The draw of wireless earbuds is convenience, and many still offer the same sound performance as their wired counterparts. The difficult part is finding a pair that will stay in your ear reliably, work when you need them, and give you the best audio quality.

Drones give you the joy of experiencing the sky without any of the downsides of gravity. Copernicus was the astronomer who put the sun at the center of the solar system. This little drone is aptly named after him because it similarly gives you a true look at the sky through a crystal clear camera and agile, intuitive controls.

Creating high-quality marketing content for your brand is labor-intensive to the point that it could be a job of its own.

There are tons of tools out there that do all kinds of recon, but it can be hard to narrow down what to use. A great way to be more efficient is by taking advantage of scripting. This doesn't have to mean writing everything from scratch — it can simply mean integrating existing tools into a single, comprehensive script. Luckily, it's easy to create your own subdomain enumeration script for better recon.

Becoming a competitive candidate in IT and Data Science takes more than knowing a few coding languages and being good with computers. To really stand out from the crowd, your knowledge should be extensive and your experience should be diverse. The 2021 Complete Computer Science Training Bundle provides that depth of knowledge and a starting point for gathering that experience. Right now, it's on sale for just $39.99.

There is plenty of evidence to suggest that learning to program is becoming a highly lucrative and useful skill. Monster.com called coding "the skill you need today" if you want a job in some of the highest-paying fields out there. If the last year has proven anything, working online requires a strong digital infrastructure that someone has to help build. That someone can, and should, be you.

As we've seen with other tools and utilities, administrators typically use certain things to do their job more efficiently, and those things are often abused by attackers for exploitation. After all, hacking is just the process of getting a computer to do things in unexpected ways. Today, we will be covering various methods to perform banner grabbing to learn more about the target system.

When approaching a target, having a precise and detailed plan of attack is absolutely necessary. One of the main goals is to increase the attack surface since the more opportunities there are for exploitation, the greater the chances of success. Subdomain enumeration is one method used to increase the attack surface, and we'll be using a tool called Subfinder to discover hidden subdomains.

GTFOBins and LOLBAS are projects with the goal of documenting native binaries that can be abused and exploited by attackers on Unix and Windows systems, respectfully. These binaries are often used for "living off the land" techniques during post-exploitation. In this tutorial, we will be exploring gtfo, a tool used to search these projects for abusable binaries right from the command line.

Secure Shell is one of the most common network protocols, typically used to manage remote machines through an encrypted connection. However, SSH is prone to password brute-forcing. Key-based authentication is much more secure, and private keys can even be encrypted for additional security. But even that isn't bulletproof since SSH private key passwords can be cracked using John the Ripper.

It's not so difficult to stay at home during the coronavirus lockdown when there's so much free entertainment to take advantage of. That seems to be the M.O. for many studios and streaming services, as they've made so many shows and movies available to the public for free. That said, they aren't running charities here. These deals won't last forever, so make sure to jump on board before it's too late.

Downloading third-party screen recording apps can be dangerous. The primary function of these apps is being able to record everything on one's display, so it's easy to see how a malicious developer could exploit this for their own gain. That's why the addition of Android 10's built-in screen recording is so impactful.

With many office workers in the US being asked to work from home if their job allows, Magic Leap's customary updates for the Lumin OS and Lumin SDK brings some help to keep distributed workforces connected.

With the Galaxy S20, Samsung has officially removed the Bixby button from its flagships. While it was a controversial key, in its later days, it did give us the ability to launch an app or custom action at the press of a button. There's still a way to do something like that, but now, you'll have to use the power button instead.

Network enumeration is one of the essential phases of an attack, but it can take a lot of time and effort depending on the size. We've all been spoiled by Nmap and similar tools, and while there is a learning curve involved, they are extremely useful. But there's also GoScan, a tool that builds upon Nmap, offering an automated way to enumerate networks and services quickly.

Sudo is a necessity on most Linux systems, most of which are probably being used as web servers. While the principle of least privilege is typically applied, sudo misconfigurations can easily lead to privilege escalation if not properly mediated. Which brings us to SUDO_KILLER, a tool used to identify sudo misconfigurations that can aid in privilege escalation.

While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatically detect ransomware encrypting your files and watch for unauthorized access to your microphone and camera.

If you want to carry a variety of network adapters without looking suspicious, a perfect solution is accessing them through Airserv-ng. Tucked away in the Aircrack-ng suite, this tool allows a hacker to plug any number of network adapters into a Raspberry Pi and access them over a Wi-Fi or Ethernet connection.

After months of waiting, the iPhone 11 is here. At an event in Cupertino, Apple unveiled the iPhone 11, 11 Pro and 11 Pro max. You probably have a lot of questions after reviewing the specs sheet, including wanting to know more about the IP68 rating that all three phones have. We're here to clarify.

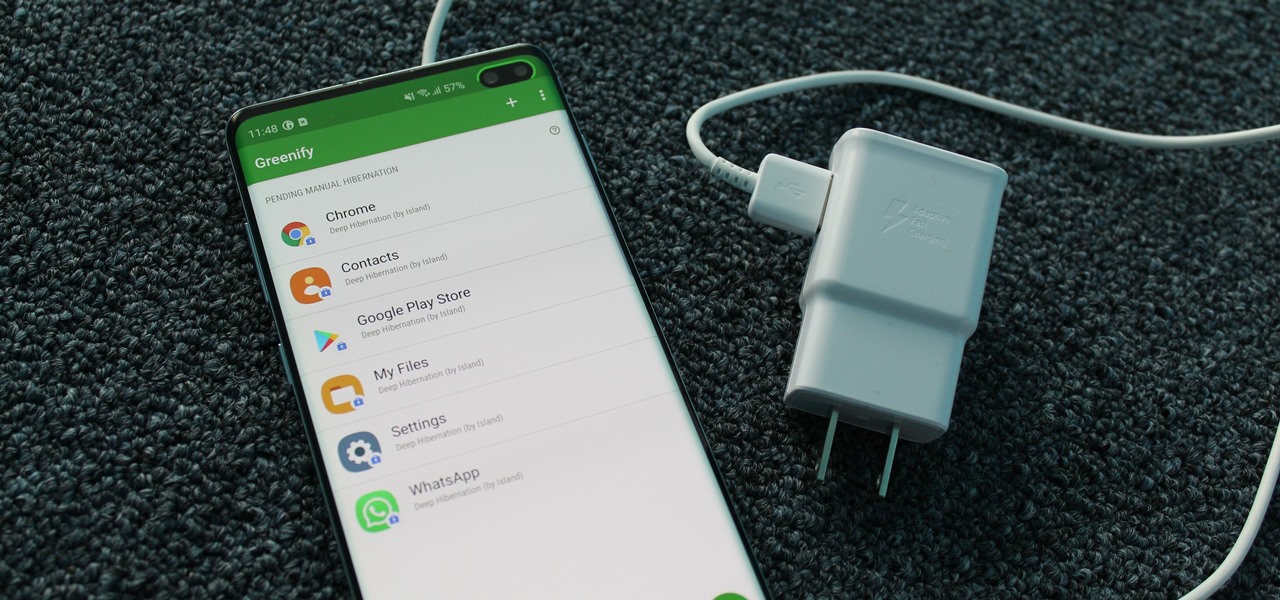
Despite newer phones having larger batteries, after a few months, my battery life drops significantly. I started researching solutions after my third phone. No matter who I asked, the most recommended solution was always Greenify. And unlike other solutions, you don't need root to use it.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

When Stardew Valley launched back in 2016 on Steam for PC, it was instantly deemed a success for steering the RPG farming simulator genre back on the right track. Before its release, we hadn't seen too much in this particular field of games that caught the eye of the general public. Since then, the mega-hit Stardew Valley has made its way to the mobile world of Android and iOS.

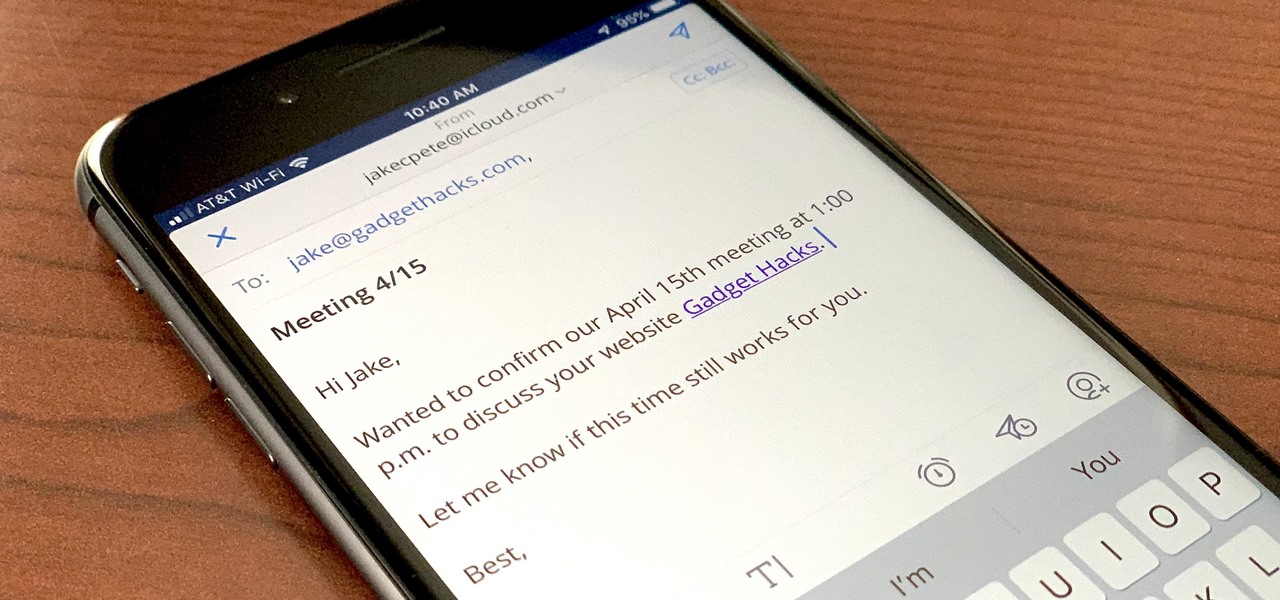
If you're a long-time Spark user, you'll know that one of the only drawbacks to the app used to be its lack of rich text-editing tools such as hyperlinking. If you needed to link out to a site in an email, your best bet was to grab a computer to get the job done. Well, close those laptops and shut down those PCs — Spark corrected this issue, implementing support for hyperlinking right into the app.

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.