Choosing which programming language to learn next can seem like a nearly impossible task, regardless of whether you're a novice developer or a seasoned coding pro with years of experience creating apps and websites. But if you haven't already learned Python, look no further.

Mac users know why they love Apple. Of course, there are limitations. An entire universe of shortcuts is unavailable to the average user.

We know our Null Byte readers would like to see some iPhone-hacking scenarios on the site soon, but until we get some of those up, we understand that some of you actually use an iPhone as your primary phone. If that's you, and you would like an easier way to get information from point A (your iPhone) to point B (your computer) and vice versa, there's an all-in-one tool that can help.

If you're reading this, you're likely a tech-savvy coding pro whose analytical talents are mostly applied to designing apps, cracking passwords, and infiltrating networks — all of which are admirable activities for both aspiring and seasoned white hat hackers. But there are other profitable ways that you can put these types of skills to use, namely in the world of investment and trading.

Whether you're coding a simple app, trying to learn a new programming language, or building an entirely new operating system from scratch, being able to quickly and clearly organize your thoughts is absolutely paramount — even as an ethical hacker or penetration tester.

If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.

With everyone sheltering at home, gaming is even more popular than ever. And it was already popular. In 2019, mobile gaming was valued at $64.4 billion, PC gaming brought in $29.6 billion, and on the desktop, $15.4 billion. There are now over 2.5 billion gamers on the planet. That's a lot of playing.

When learning Wi-Fi hacking, picking a compatible Wi-Fi network adapter is the first step to learning to crack Wi-Fi passwords.

Just days ago, Georgio Armani canceled his live show in Milan and opted to stream it instead due to coronavirus concerns. Now, at the start of Paris Fashion Week — shadowed by similar worries — Burberry has launched an augmented reality tool that lets you view the latest high fashion from the comfort of your home.

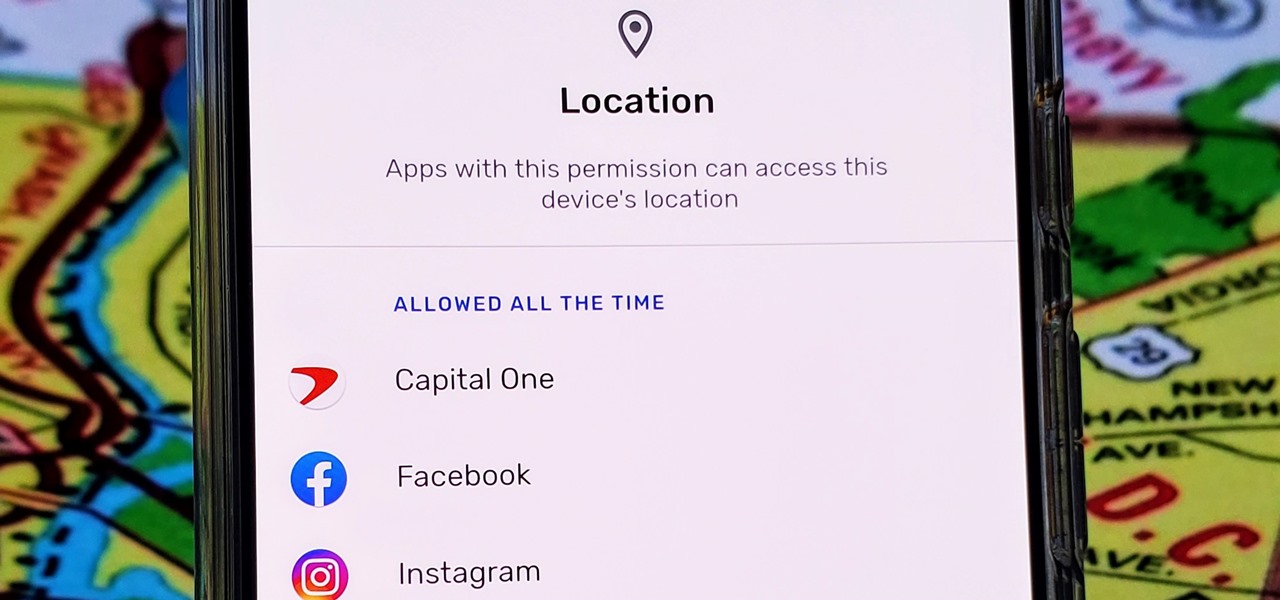
With Android 10, there are now three options when an app asks to access your location: Allow, Deny, and Allow While In Use. That last one prevents apps from seeing your location unless you're actively using them, and it's the default now. But when you first update, most of your apps will still be allowed to access your location in the background — at least, until you do something about it.

After introducing and launching Reality Composer alongside iOS 13 and ARKit 3 last year, Apple is making it easier for developers to create apps with it.

One of the more low-key functions to arrive with the Note 10 was the ability to easily record your screen system-wide. Thankfully, this long-awaited feature will finally make its way to popular Galaxy devices like the S10 and Note 9 thanks to One UI 2.

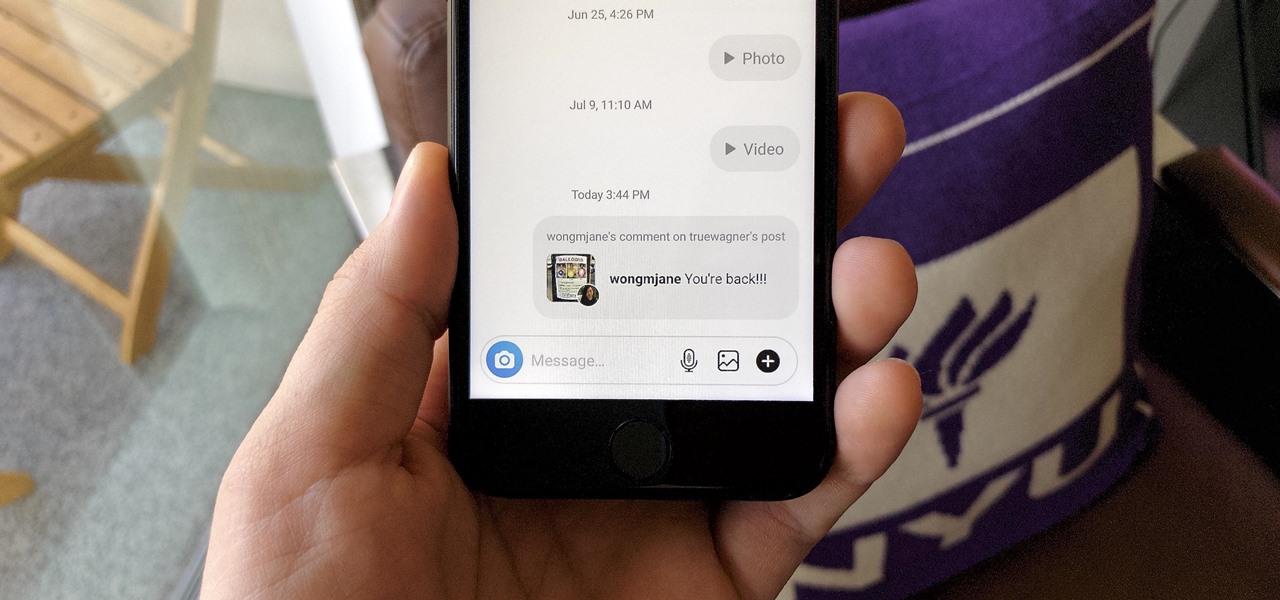
Sometimes, you'll see a comment on Instagram that you really need to share. Maybe it's something funny, possibly offensive. Whatever the case, the only thing to do is screenshot it and share that, right? Hopefully, not for long. Instagram is currently testing a feature that would allow you to share comments with others via a direct message and maybe even to stories and other apps.

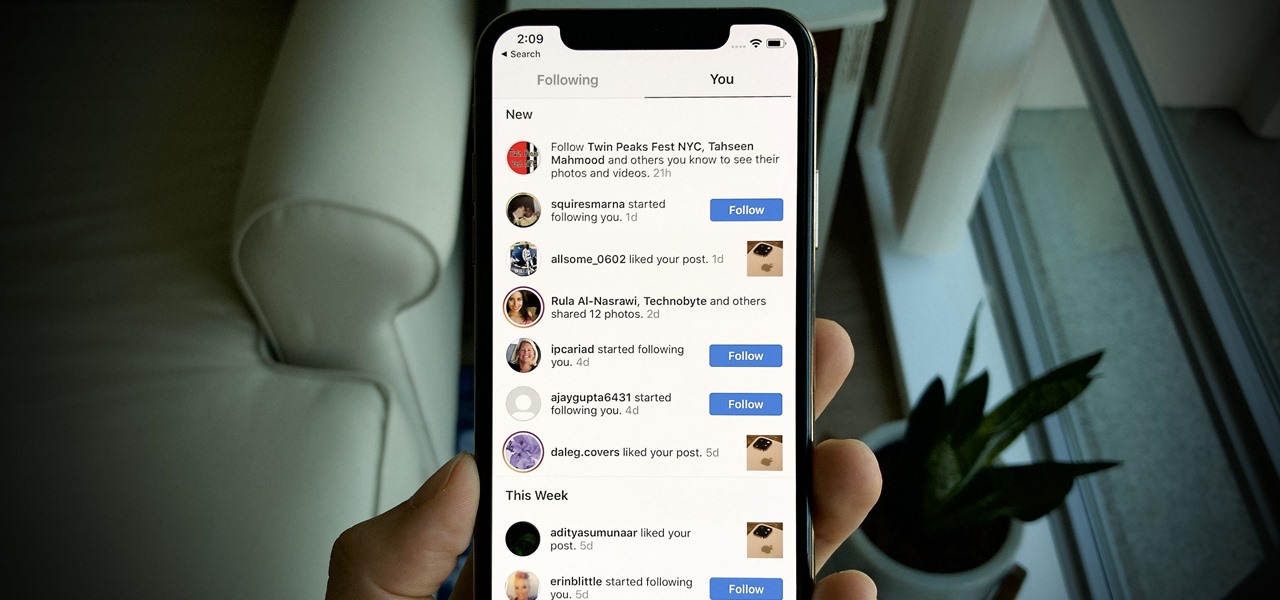
Does your Activity page on Instagram feel cluttered? You're not alone. Instagram lumps all alerts into one long, chaotic timeline, so if you want to see comments or likes, you have to weed through everything else including shares from other users, memories, recommendations, and new follows. Instagram knows its a mess, and the company plans to add notification filters to sort things out.

Data can be injected into images quickly without the use of metadata tools. Attackers may use this knowledge to exfiltrate sensitive information from a MacBook by sending the pictures to ordinary file-sharing websites.

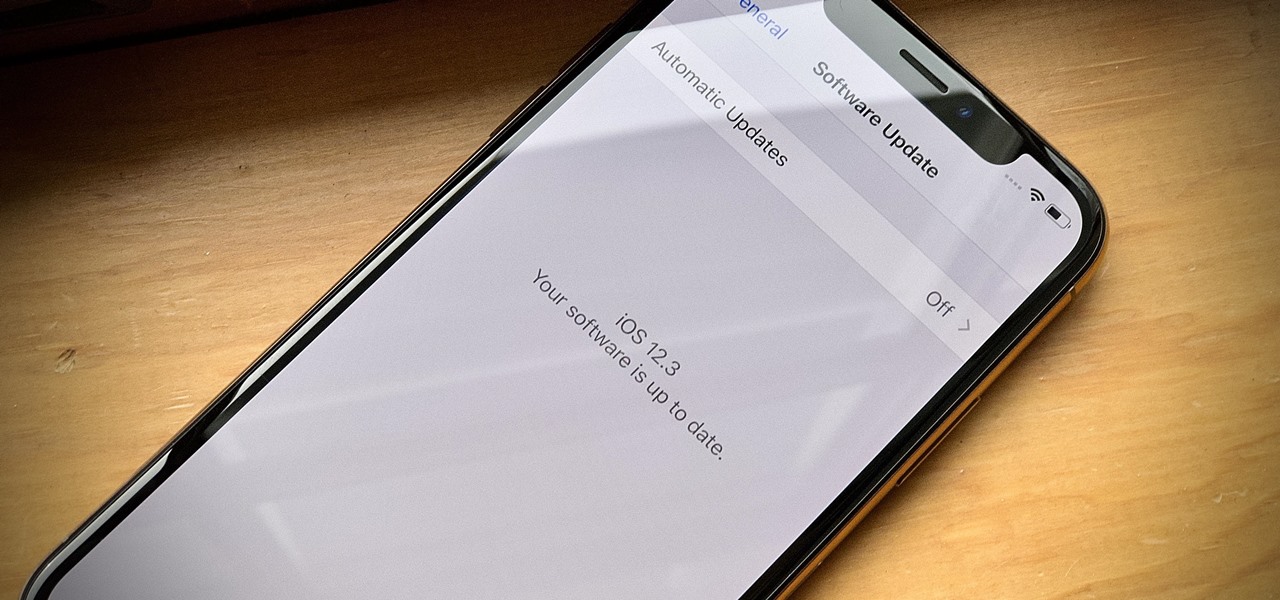
Eight days ago, Apple pushed out iOS 12.3 public beta 4 for anyone who wants to try it out. Now, there's a new version, iOS 12.3 public beta 5, released May 7, less than an hour after the developer software update. Just like it's developer version, the fifth iOS 12.3 beta for the public is a simple update with seemingly under-the-hood changes only.

The long-awaited augmented reality game based on the Harry Potter franchise from Pokémon GO masterminds Niantic is closer to release, as the developer has begun public beta testing of the app.

So far, the iOS 12.3 public betas have been on the heels of the developer betas by just over a day each time, but not anymore. Apple just pushed out iOS 12.3 public beta 4 today, April 29, just hours after the same dev version came out, meaning it's only been six days since iOS 12.3 public beta 3 was released.

If you're an iOS software developer, get excited, as Apple just pushed out iOS 12.3 dev beta 4 today, Monday, April 29. The new beta update comes exactly one week after iOS 12.3 dev beta 3 was released.

In the first guide, we laid the groundwork for our ultimate goal of uploading and running the unix-privesc-check script on our target. We identified an input field vulnerable to SQL injection and utilized Sqlmap to set up a file stager on the server. Now, we're ready to upload files and execute the script, so we can identify any misconfigurations that could lead to privilege escalation.

London-based developer Andrew Hart has been working on AR navigation since Apple's original ARKit tool was still in beta preview. Now, he's ready to unleash his technology on the world.

Hollywood loves sequels so much that studios and their marketing teams are not too proud to release a sequel of an augmented reality promotion.

Snapchat continues to deepen its roster of clients adopting its Shoppable AR Lens, with clothing giant Levi's and Disney becoming the latest brands to try on the e-commerce platform for size.

Microsoft has informed HoloLens users that the company will begin rolling out a mandatory update for HoloLens as part of its Windows 10 October 2018 release that brings a number of new features and quality-of-life improvements to the headset.

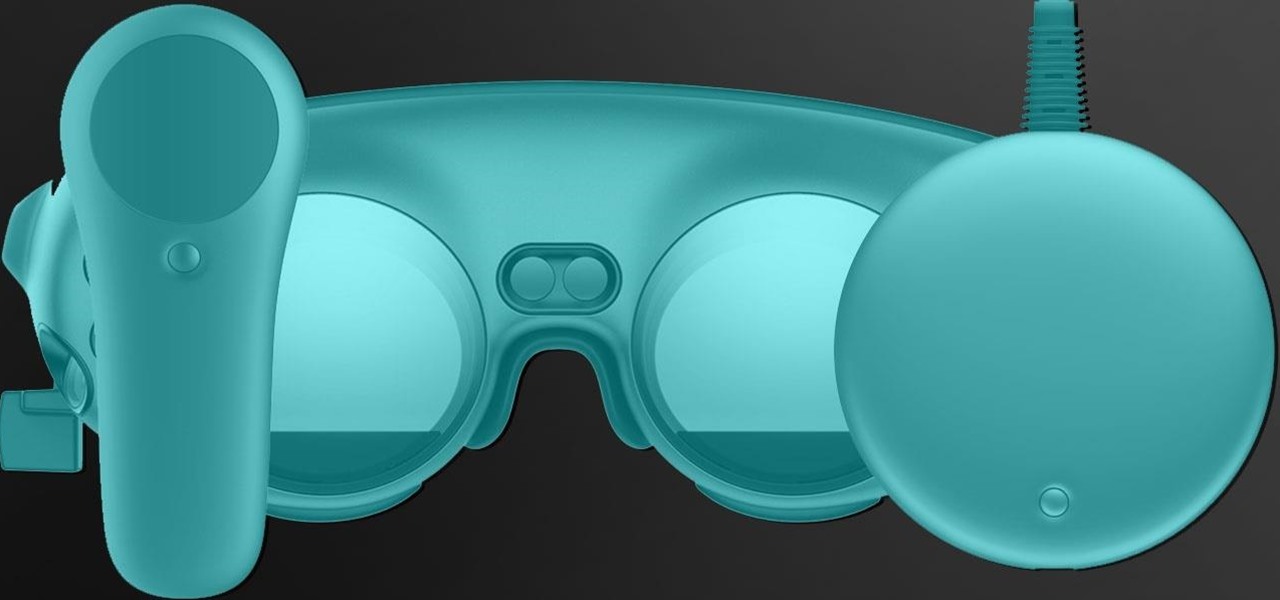
Last week, Magic Leap gave us an additional peek at its Lumin OS and more tutorials that show how its device works with virtual content. But details about the hardware wasn't included in the array of new information.

The Magic Leap One: Creator Edition has been teased for months now, and while we still don't know exactly when the sales will begin, it can't be long now because we've discovered a couple of new hints that the device's launch is imminent, hiding in plain sight on the company's website.

It's easy to run Kali Linux from a live USB on nearly any available computer, but many publicly accessible laptops and desktops will be locked down to prevent such use. School, work, or library PCs can be secured with a BIOS password, which is often an easily recovered default password. Once you have access, though, you can use a USB flash drive to run Kali live on any PC you find.

Hackers are always seeking zero-day exploits that can successfully bypass Windows 10's security features. There has been extensive research into creating undetectable malware and entire GitHub projects dedicated to automating the creation of undetectable payloads such as WinPayloads, Veil v3, and TheFatRat.

After the spectacular rise and fall (and rebirth) of Glass, Google is taking another run at augmented reality smartglasses.

It's not an official app, but for fans of Rick and Morty, it's a welcome piece of the series' universe until the recently renewed animated show returns to Adult Swim.

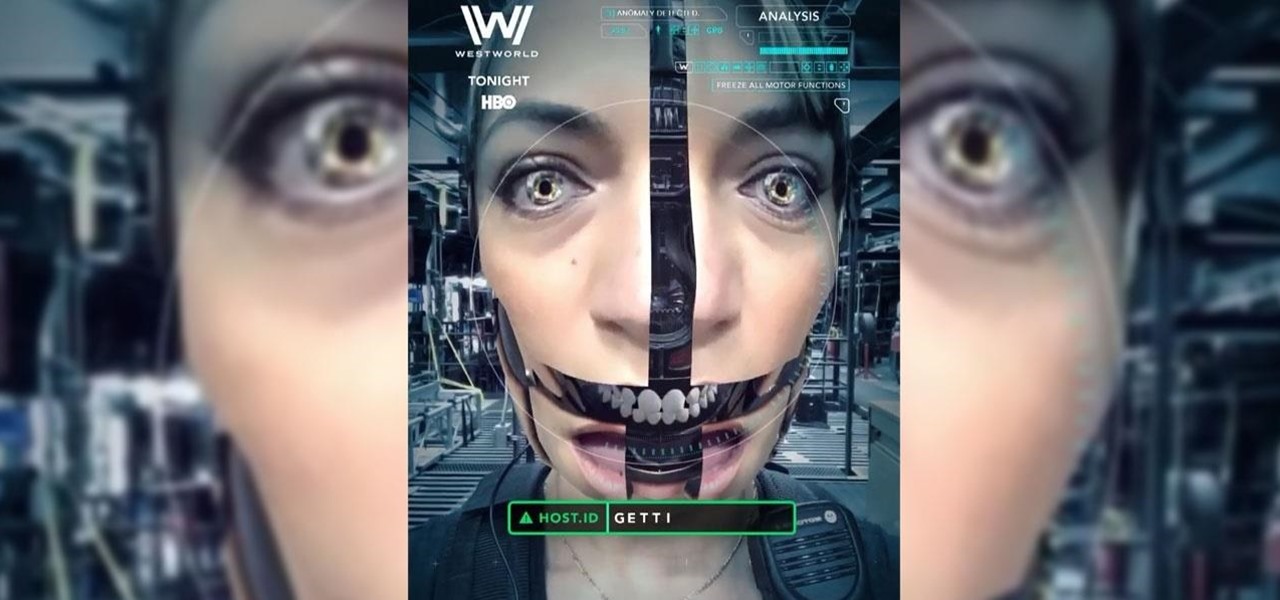
HBO is only a couple of episodes into the second season of Westworld, the television version of the classic science fiction movie about a robot resort gone awry, and the fan theories about the show are already reaching Season 1 levels of weirdness.

Before Google Chrome entered the scene and subsequently dominated the market, Firefox trailed only Internet Explorer as the most popular web browser. Now, Mozilla has its sights set on a new opportunity to revive its browser for immersive experiences.

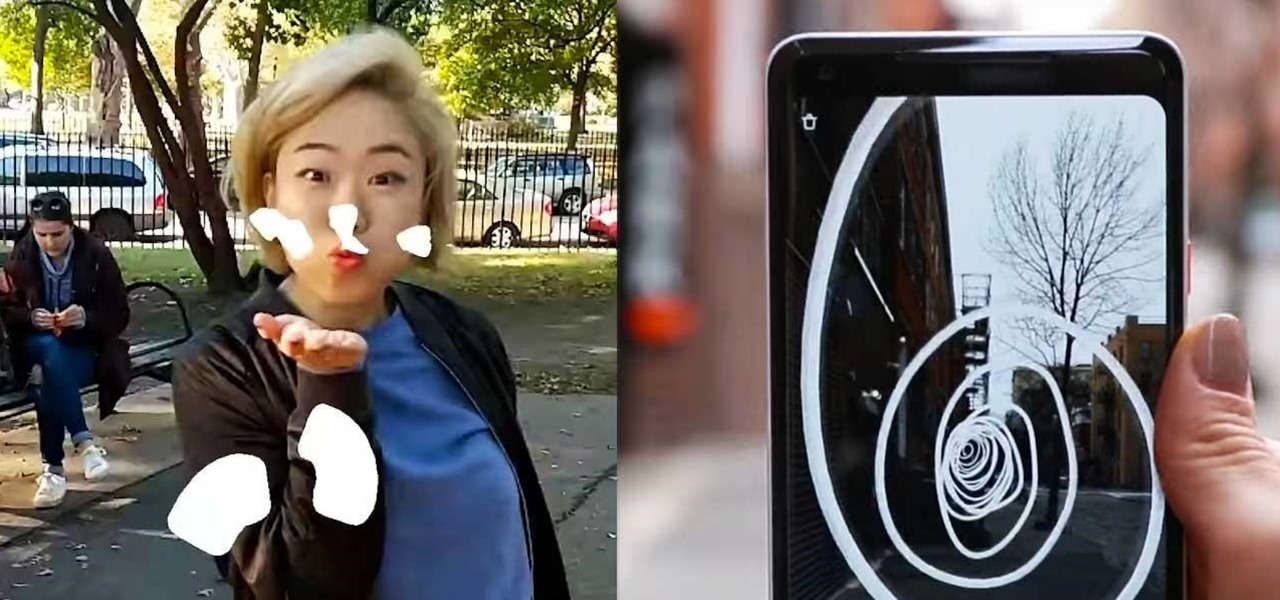
As part of its ARCore push this week, Google has promoted Just a Line from one-time AR experiment to a full-fledged app.

Earlier this week, Snapchat announced a partnership with NBCUniversal regarding the 2018 Winter Olympic Games in South Korea. Starting on February 10, Snapchat will be streaming a feed of NBC's live broadcast of the Olympics in Pyeongchang.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

Bitcoin Cash (BCH) has officially arrived on Coinbase, which means you can now easily buy, sell, send, and receive the digital currency without having to manually set up a wallet or trade on an exchange like Poloniex. This addition has boosted the price of BCH, which is currently trading at around $3,400 a coin.

Apple's codec for photos and videos in iOS 11, HEVC (High-Efficiency Video Coding), as well as the container, HEIF (High-Efficiency Image File Format), result in a reduction in size for pictures and movies without sacrificing quality. Seems like a win-win situation, but Windows-users can't open the .heic extension that these files use. In order to open HEIC files on a Microsoft Windows PC, you'll have to turn to third-party apps and tools. One of these tools, CopyTrans HEIC for Windows, essen...

As it turns out, Apple did get AR hardware into its retail stores for the 2017 holiday shopping season, but it's not the headset we've been hearing rumors about for years; it's the MekaMon battle-bot.

Internet Relay Chat, or IRC, is one of the most popular chat protocols on the internet. The technology can be connected to the Tor network to create an anonymous and secure chatroom — without the use of public IP addresses.

While hackers adore the command line, working with the GUI (graphical user interface) of an operating system has some advantages. This is especially true when it comes to post-exploitation. When we can control the mouse and keyboard of a remote computer, we can truly say we have complete control over the device. Today, I'm going to introduce to you the PyAutoGUI module, which does just that, and just how much fun you can have with it!