Welcome back, my hacker apprentices! To enter the upper echelons of hackerdom, you MUST develop scripting skills. It's all great and well to use other hacker's tools, but to get and maintain the upper hand, you must develop your own unique tools, and you can only do that by developing your scripting skills.
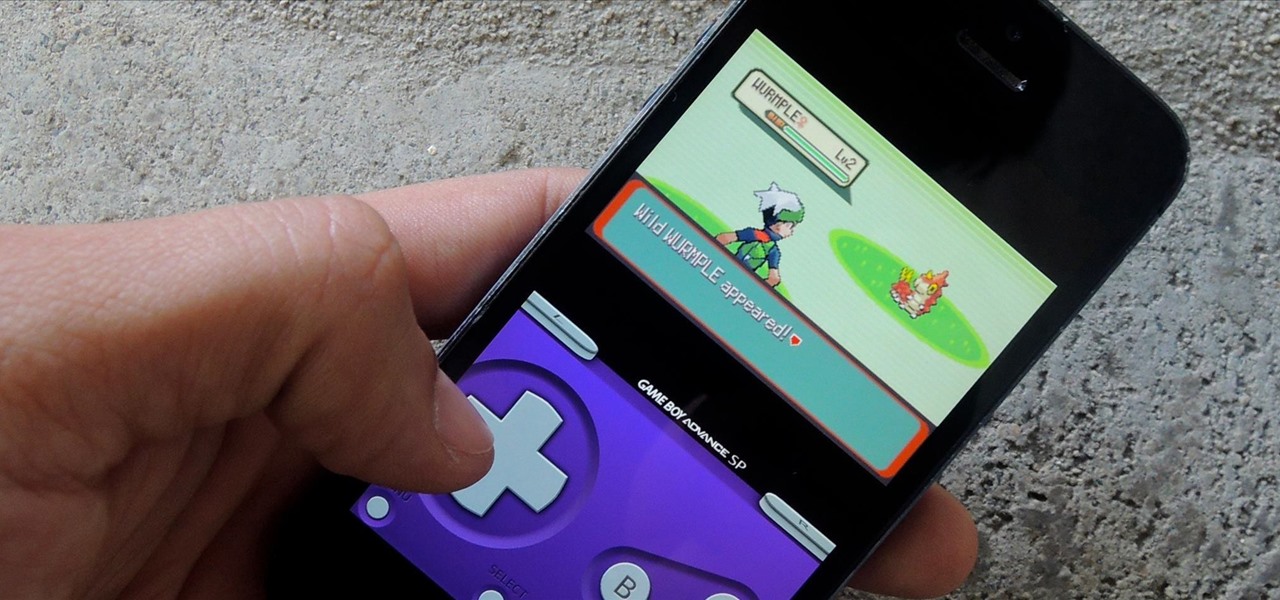
Normally, you'd have to jailbreak your iPad or iPhone to play any games that aren't available in the iOS App Store, like the now-extinct Flappy Bird game. But this isn't the case if you want to play some of your favorite old school Nintendo classics.

From personal photos and videos to online banking passwords saved in your web browser, your phone has all kinds of sensitive data that needs to be protected. One of the best things you can do for your Samsung Galaxy S4's data is have a lock screen with a hard-to-guess PIN or password.

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.
James Williamson for Lynda demonstrates designing for multiple browsers. The most frustrating aspects of web design is constantly dealing with the settle and some times not so settle differences in browser rendering. While they moved to a standard spaced, CSS control presentations has made life infinitely easier for web designs. Dealing with bad browser behavior is one of most unfortunate side effects. All browsers render our pages same because each browser reads and renders the HTML and CSS ...
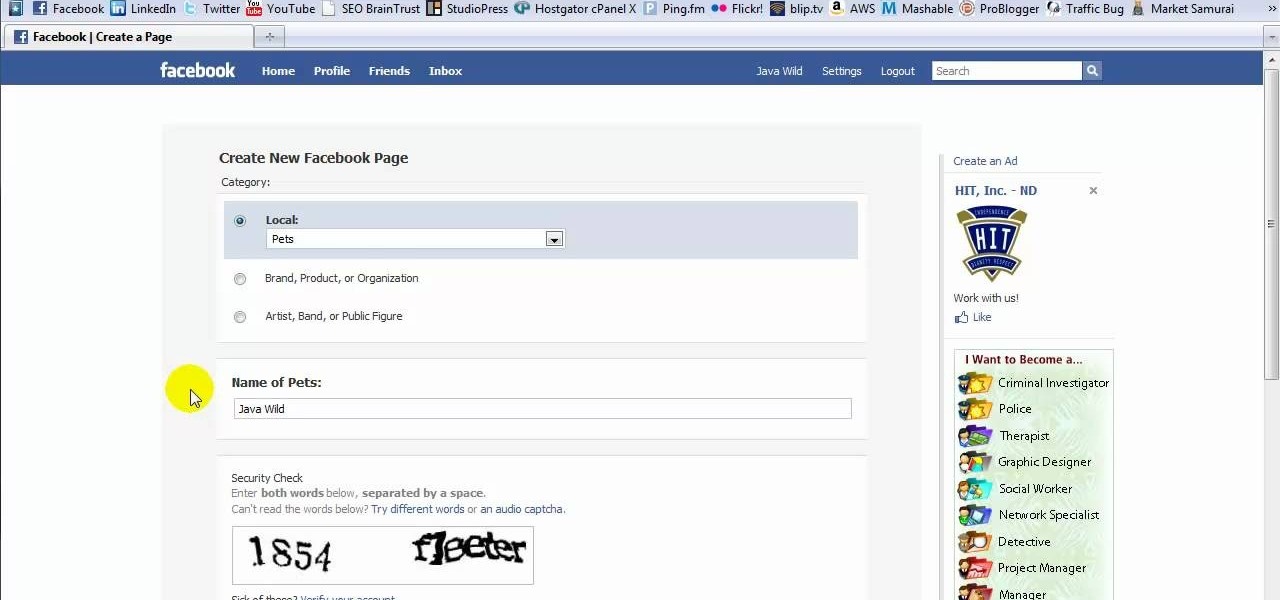
This tutorial is in response to mail to Facebook. Scott Wilde leads you through the process. You can start by creating a brand new profile page. In this case, Mr. Wilde created a profile page for his dog Java Wilde so he could have a fresh new page without having to alter his initial profile page. Fan pages are different than your base profile. Your base profile is not indexed, it is not public, it is private and limited to 5000 friends. A fan page is unlimited up to millions of fans and it c...

Is your neighbor creating a ton of racket? Suffering in anything but silence? It can be hard to approach a noisy neighbor without starting a big riff. Follow these steps to get the quiet you deserve.

Lose weight and have more energy by taking the refined sugar out of your diet. Learn how to break your sugar addiction with this how to video.

Here, Gina Trapani explains three cool ways to combine the camera on your iPhone or Android with two of their apps, Google Goggles and Shopsavvy, to accomplish productive goals. These include scanning bar codes, translating text, and storing your membership cards for the gym or the library.

In this video tutorial, you'll learn how to create a simple PHP/MySQL registration page using Adobe Dreamweaver. For more, or to get started creating your own registration page without having to do any hard coding yourself, take a look.

Take a look at this instructional video and learn how to build your own miniature computer numerical control (CNC) machine. A CNC machine acts as a controller that reads G Code instructions for machine tools such as drills and printers. To perform this task, you'll need some geared motors you can find in old analog camcorders with optical zoom.

Backpacks are handy for camping, hiking, school and travel, but they can be difficult to pack properly. In this tutorial, learn how to pack your bag so that its light and efficient.

Using a Phillips head screwdriver remove the screw under the handle in the back of your iMac. Remove the screws outlined in the picture below. Remove screws 1 and 2 with a standard Phillips head screwdriver. Screws 3 and 4 use a standard flat head screwdriver. After removing the screws, gently pull out all of the plugs. Next holding the clear handle just below the bar code, pull out the section of the iMac.

Since 2020, you've been free to set your preferred web browser and email app as the default on your iPhone or iPad. Now, four years later, Apple is expanding this flexibility in the U.S., allowing even more apps to be set as defaults for specific actions. Plus, there's now a centralized menu to manage all these default app settings.

When you download files from certain apps like Safari and Chrome on your Mac, those files are tagged with the "Where from" metadata attribute. Depending on where the file was downloaded from, this attribute may refer to the host's URL, a sender's email address, or another piece of identifying information. While not obvious, you can delete or even change this attribute.

You probably know of Apple's Text Replacement feature for iOS, iPadOS, and macOS, but you're probably not using it as much as you should. With it, you can create your own keyboard triggers for almost anything you can think of, whether it's an email address or an entire email. There are endless reasons to create custom text replacements — and we'll show you why.

The iOS 17.2 update for iPhone is a big one. Aside from huge new features like the Journal app, Contact Key Verification for iMessage, and a revamped TV app, there are 50 new URL schemes you can use in your self-created shortcuts.

You may use Safari on your iPhone or iPad to open links and browse the web, but there's so much more it can do for you. On updated software, you can implement third-party Safari extensions in your browser that go above and beyond content blocking, sharing, and performing basic actions.

After nearly two months of beta testing, Apple is finally pushing the iOS 15.6 software update to all iPhone users. While it's not as feature-rich as the iOS 15.5 or iOS 15.4 that came before it, there are still a few things you'll want to know about it.

You've probably already used a few Safari Extensions on your Mac, but if you haven't explored Safari's web extensions on your iPhone yet, you're missing out on some fantastic possibilities to increase productivity, make tasks easier, filter out noise, and bring more fun to your browsing experience.

Web applications are ubiquitous in the modern online world, and knowing how to attack them is an increasingly valuable skill. But the key to a successful attack is good recon since it's easier to be focused and efficient with the more information you have. There are many fingerprinting tools available, such as httprint and WebTech, but there are even more that can aid us in reconnaissance.

"I want to make video games" — Is there anyone who hasn't ever thought that? It's almost universal among gamers to want to get on the other side of the screen and design the games themselves, especially those of us who have played less than impressive games and thought that we could do a better job. But it's hard to know where to start — or how — when it comes to creating our own games.

If you're looking to improve your browsing experience, then a VPN is the right way to go. If you're tired of censored or geographically blocked sites and wary of companies selling your data, then a good VPN can be your answer to a problem that limits every aspect of your experience online.

If you buy an Android phone from any of the big US carriers, it will come with several extra apps in addition to any apps the manufacturer preinstalled. It's all in the name of profit, of course. Some of these apps are from companies that paid the carriers to distribute their software, and some are from the carriers themselves, usually aimed at upselling you or perhaps collecting a little data.

Python is one of the most widely used programming languages in the world. Professionals use Python in virtually every field where coding is a requirement, whether it's game design or data science. If you're looking to learn Python, then get started with The 2021 Premium Python Certification Bootcamp Bundle for just $34.99.

Becoming a successful web developer is more than knowing coding languages. Learning to craft functional, intuitive designs is as much coding as knowing how the user will interact with what you've built. The Complete Become a UI/UX Designer Bundle can take you from introduction to mastery in designing the best user experience, and right now, it's only $34.99.

Ethical hacking is a useful skill that can make you stand out in the field of cybersecurity. Whether you're just entering the field or are already established and are looking to stay current, learning the fundamentals of the white hat is an essential skill for your professional development.

How do spammers get your email? You give it to them. Not directly, no — you sign up for an app or service and happily hand over your email to verify your new account, then that app or service sells your email address to marketers who now know what kinds of apps and services you like.

Bloatware is a problem on Android, and it's not just a Samsung thing. Removing apps that have the Uninstall or Disable button grayed out in Settings has always involved sending ADB commands to your phone from a computer, which itself was always such a pain to set up. Thankfully, that has finally changed.

The USB Rubber Ducky is a well-known hacking device in the cybersecurity industry, but it needs to be preprogrammed before it can be used. That means it's not easy to issue commands to a target computer since you can't interact with it from afar after plugging it in. And if you don't know what the target computer is, you might come up empty. That's where the WiFi Duck comes in handy.

Nearly ten years since the first Galaxy Note and yet the Galaxy Note 20 still hasn't solved one of its biggest problems: bloatware. There are still over 20 redundant or unnecessary apps that are on this $1,000+ phone. But while it does require some advanced tools, it's still possible to remove them.

If you're interested in joining the increasingly popular and lucrative world of ethical or "white hat" hacking, you're far from alone. More and more coding and programming pros are turning to this field thanks to the high pay, countless opportunities, and exciting work environment.

If you're an avid programmer or developer, your time is likely spent creating apps and perhaps the occasional website. And while these go-to coding endeavors are exciting and occasionally lucrative, more and more coding pros are turning to careers in cybersecurity and ethical hacking — thanks to the high pay, flexibility, and unparalleled opportunities.

For a decade, Microsoft Azure has been transforming businesses across the globe. The cloud-computing service is leading the way in software as a service (SaaS), platform as a service (Paas), and infrastructure as a service (IaaS) protocols.

I've been steadily making my way through the series Hannibal, which arrived on Netflix in June. I've just now made it to the back half of the third season, which introduces us to a new villain who (spoiler alert) seeks to become the Great Red Dragon.

If you want to control electronic devices, such as a relay or motor, you can do so using MicroPython with an ESP8266 and web browser. Usually, you'd program an ESP8266 using Arduino, but C++, which Arduino uses, is not always the easiest programming language for beginners to learn.

Everybody knows not to store sensitive information in unencrypted files, right? PDFs and ZIP files can often contain a treasure trove of information, such as network diagrams, IP addresses, and login credentials. Sometimes, even certain files that are encrypted aren't safe from attackers. That's where Zydra comes in — a tool for cracking RAR files, ZIP files, PDF files, and Linux shadow files.

The career prospects for talented and trained IT professionals are nearly endless. As the world becomes more interconnected by the day, companies of all sizes are looking for people who can install, maintain, and troubleshoot a wide variety of networking infrastructures and web-based platforms.

It's no secret that learning how to code is one of the best things you can do if you want to land a high-paying career in a world that's heavily reliant on web and app development.

Knowing just one or two programming languages is no longer sufficient if you want to make serious money in the lucrative world of web design and development. But the good news is that you don't need to spend an excessive amount of time or money on a traditional coding education to get the skills you need to thrive.