Error code P0401 on a 2004 Ford Focus indicates EGR Insufficient Flow, which usually means your DPFE sensor needs to be replaced. If you're not sure though, and you shouldn't be, watch this video to learn how to perform a test that will make sure your DPFE sensor is actually broken before you replace it.
Facebook has provided developers with a whole library of code usable for creating applications. This tutorial shows you how to get the code, and then how to use it so you can start developing your own Facebook apps using Adobe Flash and Action Script
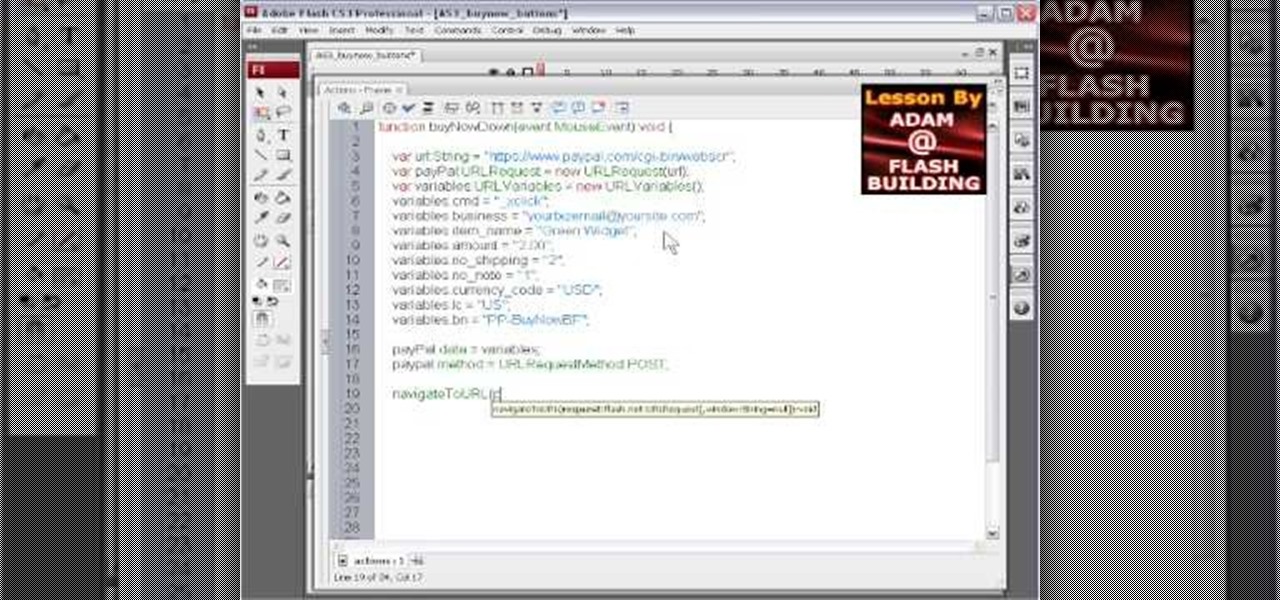
Add an extra level of security to your website by creating your own dynamic 'Buy It Now' button for PayPal-using visitors to your website. Coding this button is very easy, and you can even animate it to draw more attention to your webstore.
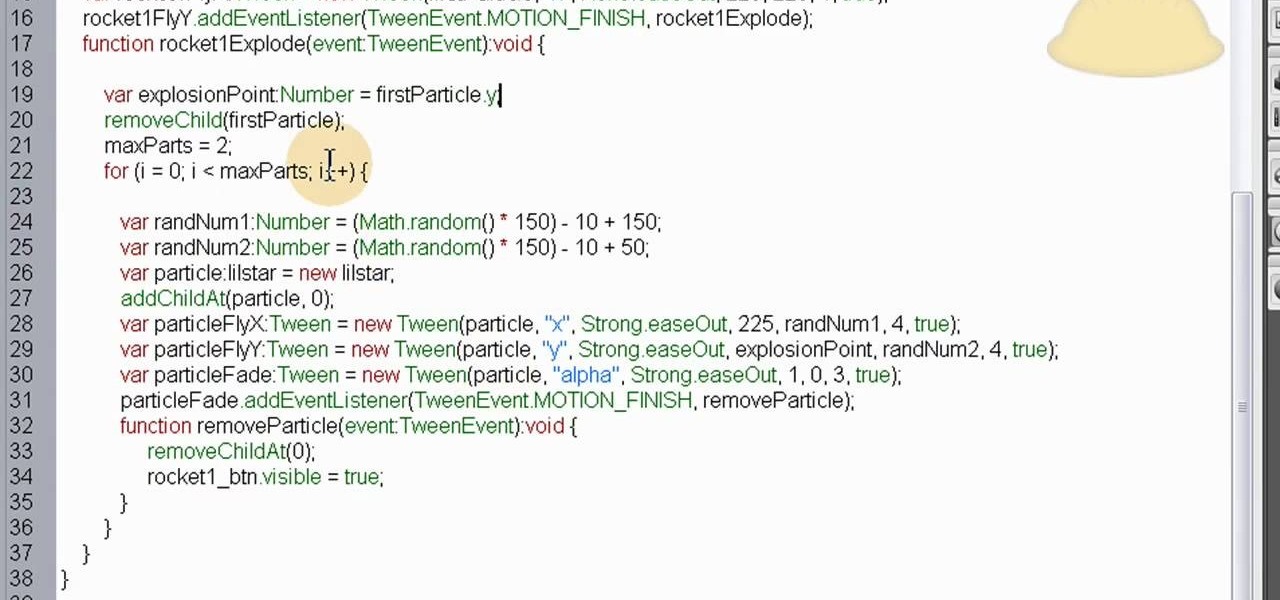
This is a custom particle effect, coded using ActionScript 3, that will recreate the effect of a rocket and fireworks explosion. The effect is also randomized, so you'll never get the same animation twice. This tutorial shows you how to code this effect using Fireworks.
In this clip, you'll learn how to tweak any existing Code Snippet when working in Flash CS5. Whether you're new to Adobe Flash or merely unfamiliar with Flash Professional CS5, you're sure to benefit from this free video software tutorial from Lynda. For more information, including detailed, step-by-step instructions, take a look.
In this clip, you'll learn how to use Code Snippets to display and hide movie clips in Flash CS5.. Whether you're new to Adobe Flash or merely unfamiliar with Flash Professional CS5, you're sure to benefit from this free video software tutorial from Lynda. For more information, including detailed, step-by-step instructions, take a look.

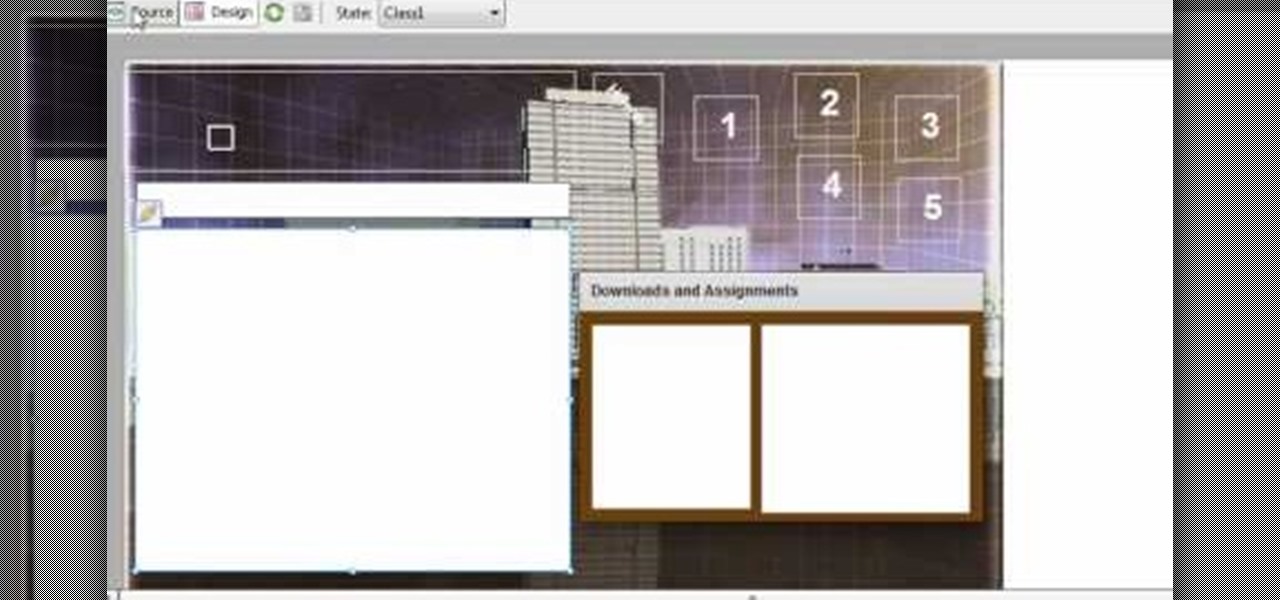
Whether you're new to Adobe Flash or merely unfamiliar with Flash Professional CS5, you're sure to benefit from this free video software tutorial from Lynda, which presents a thorough, step-by-step overview on how to work with code snippets within Flash Professional CS5.

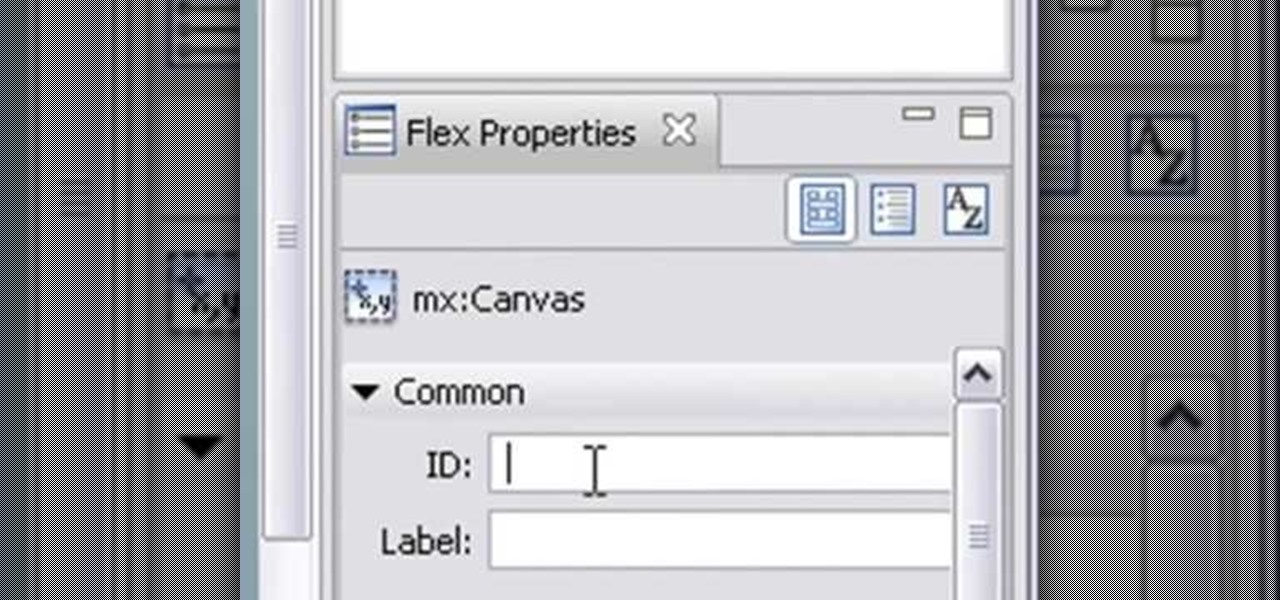
In this clip, learn how to program state codes and route buttons in Adobe Flash Builder. Whether you're new to Adobe's popular Flash IDE (previously titled Adobe Flex Builder) or simply wish to become better acquainted with the program, you're sure to find benefit in this free video software tutorial. For more information, including specific, step-by-step instructions, take a look.

See how to scan and read QR codes with your iPhone's camera. Whether you're the proud owner of an Apple iPhone 4G or perhaps just considering picking one up, you're sure to benefit from this free video tutorial. For more information, including a detailed overview, watch this iPhone user's guide.

It goes by many names. The RLoD (Red Lights of Death), the RRoD (Red Ring of Death), absolute disaster. Whatever you call it, the XBox 360 error that causes many console's front LED's to turn red in rage and cessation of function has caused all sorts of headaches for consumers and Microsoft. It can be caused by a couple of different cooling-related issues, and determining the error code that has caused your console to malfunction can go a long way to helping you fix it. This video will show y...

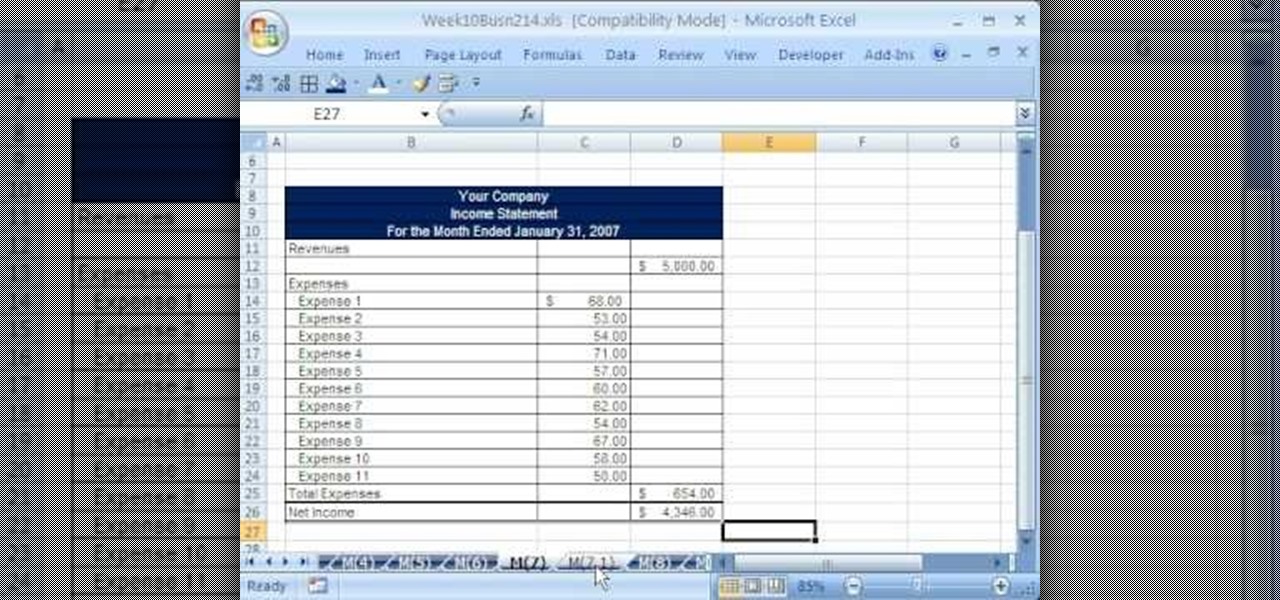
Whether you're interested in learning Microsoft Excel from the bottom up or just looking to pick up a few tips and tricks, you've come to the right place. In this tutorial from everyone's favorite digital spreadsheet guru, ExcelIsFun, the 54th installment in his "Highline Excel Class" series of free video Excel lessons, you'll learn how to find, download and use VBA code in your MS Excel projects.

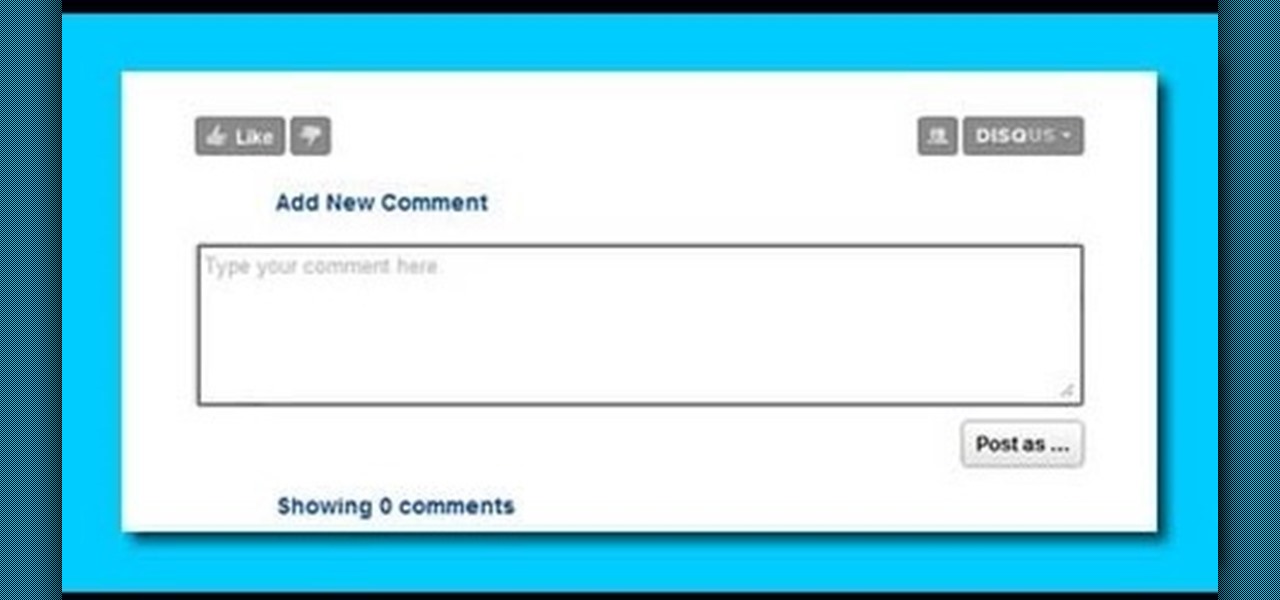
This Dreamweaver CS4 tutorial takes you on a step by step process for installing an automated comment box system for your website. The system is a great way for communicating and interacting with your website users. It has a great feature that automatically sends you an email everytime someone comments in your website. Also it will allow you to post a reply by email.

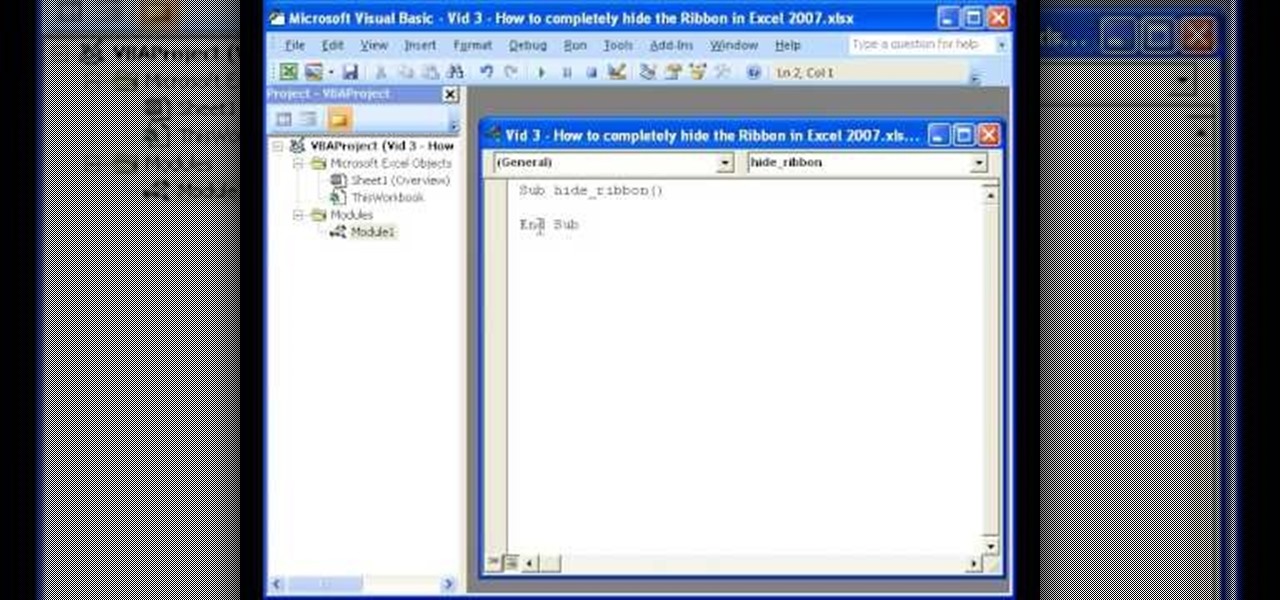
The instructor of this video shows you how to completely hide the ribbon, or the menu, in Excel. If you only want to partially hide the ribbon, you can use the shortcut control + F1. To completely hide the ribbon, though, go to the Visual Basic screen, hit Alt + F11. Then, go to insert, then module, and type in the macro "sub (Your name for macro)" then hit enter, then type in the code "application.executeExcel4macro''show.toolbar(""Ribbon"", false)''". To set up the code to show the ribbon a...

Cami, theburntmatches, shows us how to unlock all songs on Rock Band! It is a simple way to unlock all the songs in XBOX 360, PS3 or Wii Rock Band . This probably doesn't work with Rock Band 2 (RBII or RB2). This is a simple glitch or cheat code for the guitar hero like game.

Mike Lively of Northern Kentucky University demonstrates how to create a 3D plotting program for the sinc math function. Part 1 shows how to convert a Flash Package into a Flex application. Part 2 shows how to get the sinc function running and add different textures. Create a cool interactive 3D plotter in thie Adobe Flex Builder 3 and Papervision3D tutorial.

Mike Lively of Northern Kentucky University demonstrates how to build a jet band using Jeff Heaton's jet pack code. What is a jet band? Well, it's like a jet pack but smaller and allows you to go higher than 200 meters when flying in Second Life. Part one shows you how to create the code for the jet band. In part 2, the code is modified to remove the altitude reading below 70 meters.

There are a couple ways to include HTML when coding PHP. Learn two options that work equally well, then decide which one makes the code more clear and concise for you.

You may have seen a "check engine" sign on your car's dashboard when driving your vehicle. Maybe "service engine soon," or just "check". What does this mean if the alarm won't turn off, or comes on when you're driving? Find out in this automotive video tutorial how to read those trouble codes on your automobile.

Looking for some fun cheat codes to get some extra fun out of your game of Grand Theft Auto: San Andreas? These codes are specifically for Playstation users. Make cars fly or float away when they get hit, or enter into Chaos Mode!

If you have created a product that you want to sell, getting a UPC code for it will allow you to track purchases and give your business a more professional air. This video will explain how you go about getting a UPC code and using it to help your business.

Google loves their little Konami Code Easter eggs. The Konami Code is famous among gamers for letting you cheat in video games. The latest one they come up with lets you try it out on Google Docs. All you have to do is open up Google Docs, and type in with the following keys: up, up, down, down, left, right, left, right, B, A, and then enter!

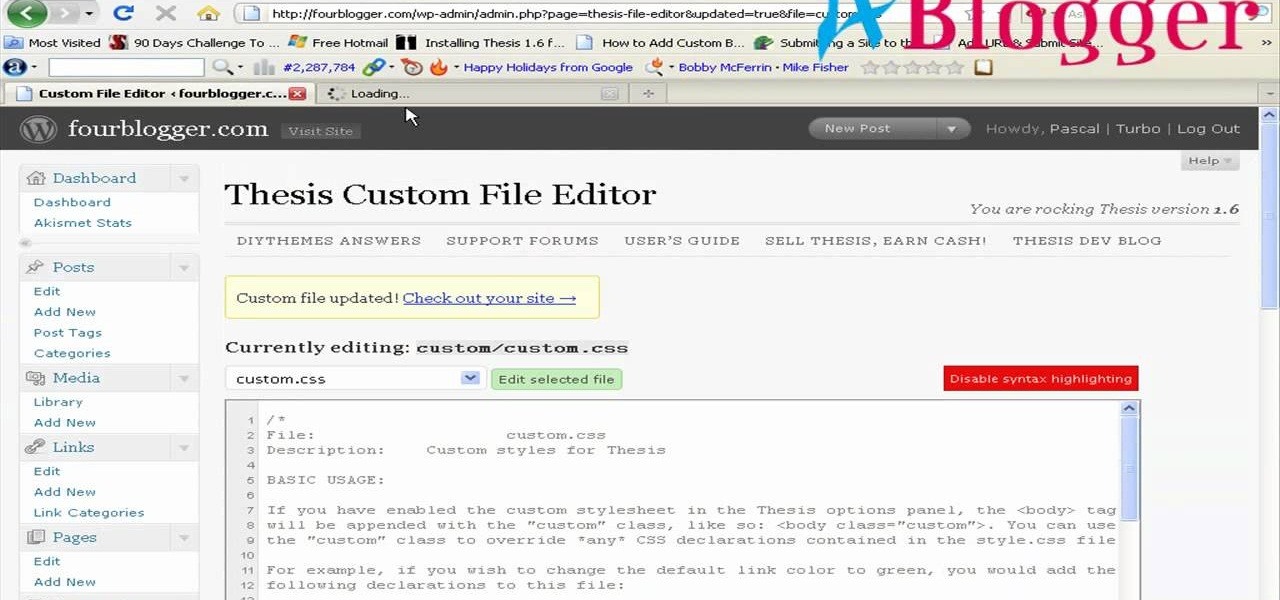
First you need to go to your site and click any post you want and see the simple heading and now you want to change the background. To do this, first you need to go to your word press admin and then click custom file editor in thesis options it will open your code window and here you will have to paste the code which is showing in the video. you will have to paste it in custom.css. After pasting the code you have to click the green save button.

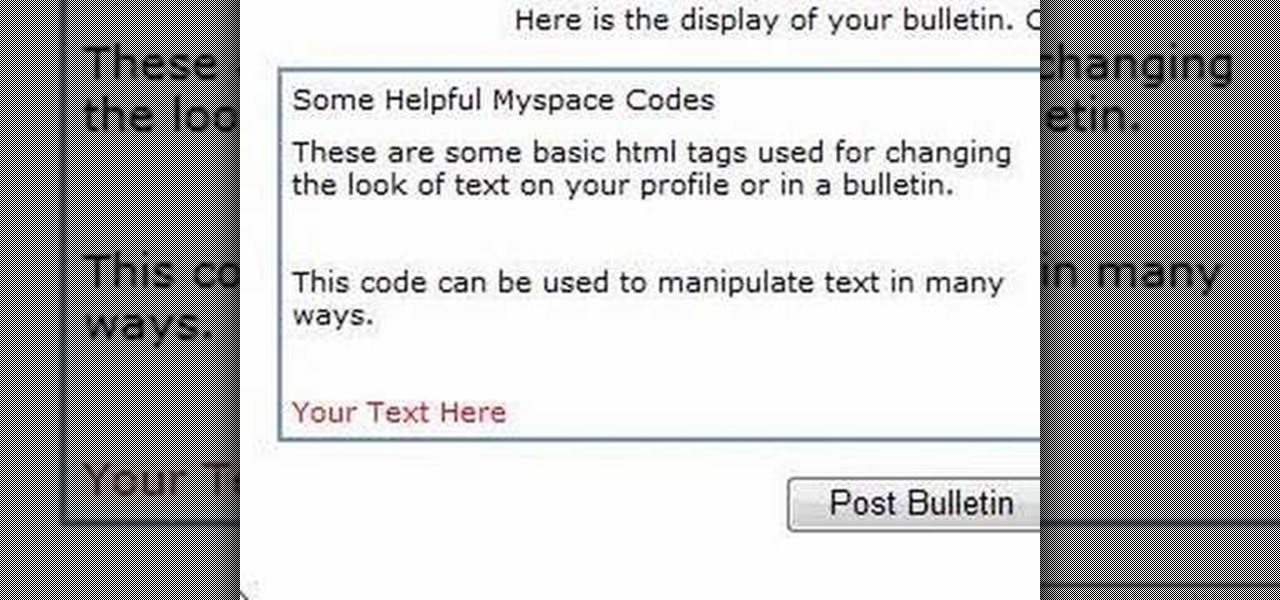
In this Computers & Programming video tutorial you will learn how to alter text on MySpace using HTML codes. Here are a few basic html codes used to change the look of text on your profile or in a bulletin. <b> for starting bold text and </b> for ending bold text. <i> this text will be italicized</i>. For underlining text use the code <u> </u>. <b><i><u> This text will be bold, italicized and underlined </b></i></u>. To change color of your text to ‘red’ use the code <font color=”red”> </font...

This video demonstrates how to import XML code from the Internet into Movie Maker. The video shows you how to find the XML code on the Internet, how to download it, and how to import it into Movie Maker.

Being stuck inside for the near future is less than ideal, but at least you have the world of eLearning to sharpen your skills while you kick back on your couch. Case in point, The 2020 Premium Learn To Code Certification Bundle has all the training you need to start coding like a pro right at home, and it'll only cost you $39 today.

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

For anyone interested in using cheap, Wi-Fi-connected microcontrollers like the ESP8266, the Arduino programming language can be a barrier to entry. Based on C++, Arduino requires knowledge of more computer science than languages like Python. Fortunately for beginners, setting up MicroPython on an ESP8266 allows anyone to write Python on affordable microcontrollers in a matter of minutes.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

One of the first steps in attacking a web application is enumerating hidden directories and files. Doing so can often yield valuable information that makes it easier to execute a precise attack, leaving less room for errors and wasted time. There are many tools available to do this, but not all of them are created equally. Gobuster, a directory scanner written in Go, is definitely worth exploring.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

QR codes have become a staple in our everyday lives. Companies use them for everything from marketing promotions to movie tickets thanks to security they provided for these types of transactions. But for years, Android users had to download an app to scan these codes. Well, not anymore.

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.

Using Hydra, Ncrack, and other brute-forcing tools to crack passwords for the first time can be frustrating and confusing. To ease into the process, let's discuss automating and optimizing brute-force attacks for potentially vulnerable services such as SMTP, SSH, IMAP, and FTP discovered by Nmap, a popular network scanning utility.

The first question people ask me when they come to my apartment is usually "What's your Wi-Fi password?" While I'm happy to give my friends free access to the internet, it's hard to walk each person through my secure password. Luckily, there's a way to create a QR code that will let people easily connect to a Wi-Fi network.

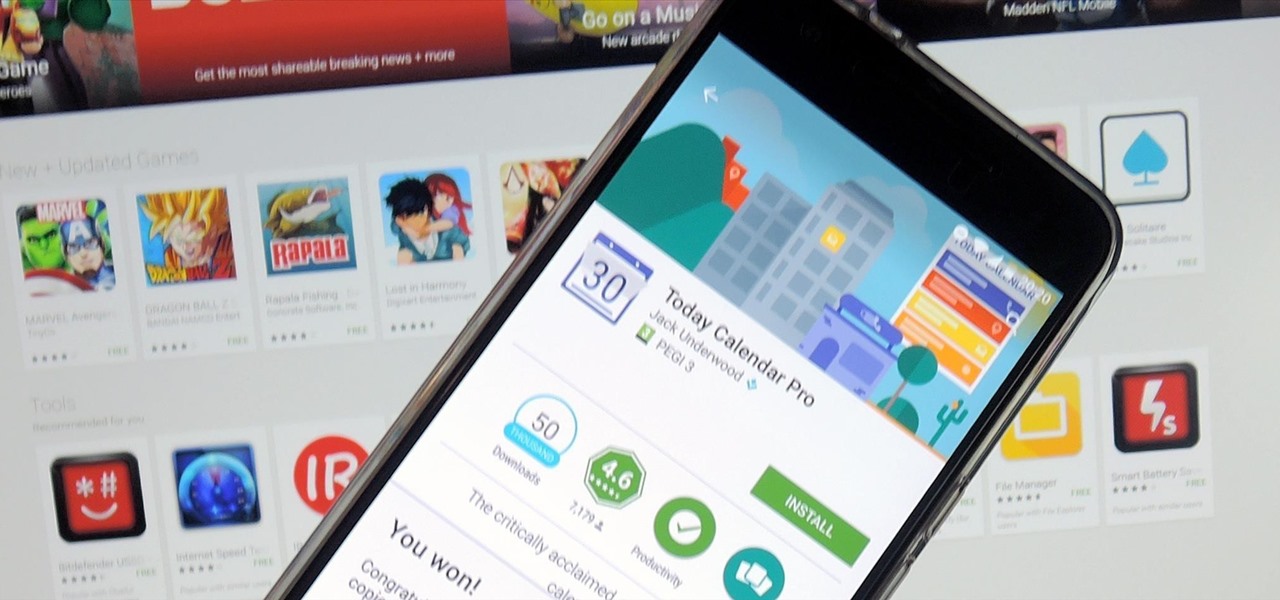
If you're a developer looking to get some exposure for your high-quality app, or if you're a user hunting for new apps and would like a chance to win a paid app at no cost, then Jack Underwood's new Promo Codes app may get you there, which you can install for free from the Google Play Store.

In the last tutorial, we learned how to make functions and how they work on the high level. This time, we will take a peek under the hood again, stare deep into its soul and see its ugliness face to face to see how it works in the lower level.

This is my first ever how-to so I apologize in advance for any grammar mistakes or spelling errors. Introduction

This is the first installment in a new series that I am calling "Hacker Hurdles." These are things, methods, techniques that make our job as hackers more challenging and difficult. Don't misunderstand me, these items don't make our task impossible, but rather more challenging and, therefore, more gratifying when we are successful. One of the most important new hurdles for hackers is DEP and ASLR. Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR) are designed to pre...