
How To: Security-Oriented C Tutorial 0x10 - Pointers and Addresses
In previous tutorials we have encountered these things called pointers and addresses but we still don't know what they really are. Let's learn a bit more to clear things up.


In previous tutorials we have encountered these things called pointers and addresses but we still don't know what they really are. Let's learn a bit more to clear things up.
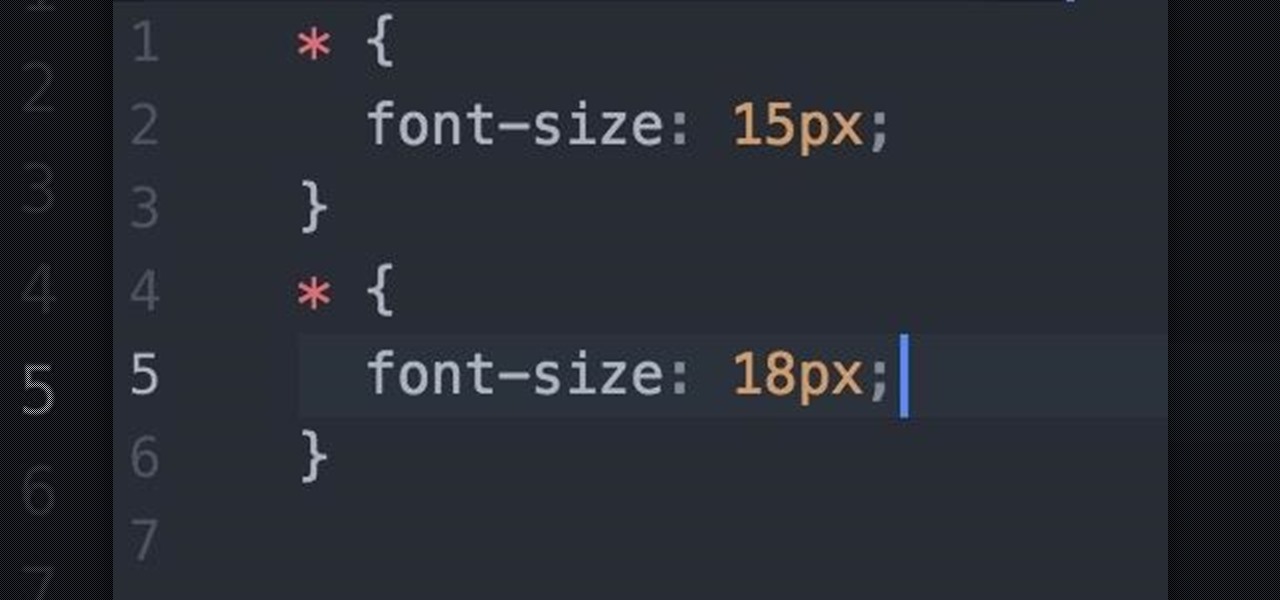
Welcome fellow Null-Byters! I would suggest you watch reading my last tutorial before we begin. In our last adventure, we began making a simple, ugly website. If we want it to make it look good, we should add some styling. But first, we need to understand the basics.

What's up guys! It's time to discuss strings in more detail. Review

The Nexus 5X and Nexus 6P have identical camera hardware—in fact, both use one of the highest-end camera sensors ever put into a smartphone. The only real difference between the cameras on Google's latest flagship devices is that the 6P natively supports electronic image stabilization (EIS) whereas the 5X does not.

Welcome back, reader! In this tutorial, we will be covering our first program! So let's get to it. We all know the unspoken tradition of the first program when learning a language and of course, here we will respect and complete it. Fire up your favorite text editor (be it vim, emacs, gedit, it's all the same to me, no h8) and try to keep up.
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...
Windows 10 universal apps are actually pretty awesome—regardless of if you're using a desktop, laptop, tablet, or convertible, the same app automatically scales up or down to suit your device. Definitely cool, but the Windows Store is pretty bare-bones as it stands, so the downside is that you can't always find a good universal app for every purpose.

Welcome back! In the last iteration of how to train your python, we talked about functions, and we even made our own! We're going to move on to more types of data arrays (much like lists) in today's discussion.

Welcome back, my tenderfoot hackers! As most of you know, I am strong advocate for using Linux as a hacking platform. In fact, I would say that without knowing Linux, you will never become a professional hacker/pentester.

The Xposed Framework was just recently made available for Android Marshmallow, but everything isn't quite back to status quo just yet. Sure, some Xposed modules function properly, but others are a bit buggy, and several don't even work at all. This is mostly a result of changes to the Android system that Lollipop modules relied upon, and such modules will need to be updated for Marshmallow compatibility.

With every version bump, Android gets a new Easter egg that can be accessed by tapping the "Android version" entry in Settings. For the most part, these have generally been little animations or live wallpapers that depict the Android code name, but starting with version 5.0 Lollipop, things got a bit more interesting.

In Minecraft 1.9 New Command Blocks can be used to make elevators. You types different commands to achieve controlling the elevator for movement you like. This tutorial tells in Minecraft 1.9 how to use command blocks to make elevator. Lets just have a look at it!

In the last iteration of how to train your python, we covered the concept of control flow and covered the booleans associated with it. Today, we'll be putting those to use as we discuss how to use if, else, and how to make conditional statements. So, Let's get started!

Welcome Back !! TheGeeks. SQL Injection (SQLI) Part-1

Hello, everyone! Many of you don't even know about my existence here on Null Byte, so I thought of contributing something rather interesting. Recently, someone asked how to make your own "Bad USB," and I promised to make a how-to on this topic. In addition, it would be nice to have something related on our WonderHowTo world. So here it is!

Cauliflower has become trendy again, and it's mostly thanks to the low-carb crowd who use its mild flavor and soft texture as a replacement for things like rice and pizza dough.

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.
Are you tired of uploading videos to different sites separately? It's really time consuming and difficult. Finally, there is a way to upload and distribute your videos to YouTube, Facebook, Dailymotion, and many more video-hosting websites in one go. No need to upload to every site separately and one by one.

Hackers have stolen over 225,000 Apple user's account information from countries all over the world—including the United States, China, and France—in what many are reporting to be the biggest known Apple hack in history.

It's official: The next version of Android will be code-named "Marshmallow," and we're getting a whole number bump to version 6.0. Lots of exciting new changes are coming to the world's most popular operating system, including a "Now on Tap" feature that will give you relevant information about any screen at the press of a button.

We've all been there. Channel surfing lazily whilst reclining on the sofa—then all of a sudden, the remote stops working. Out of frustration, you hold the remote up higher, press the buttons harder, or maybe a even give it a good smack hoping that will fix it. Right around this time, you start to wonder if your trusty old remote has finally called it quits or if it's just a dead battery.

When security firm Zimperium discovered Android's biggest security risk in years, it sent shock waves through the ecosystem. As a result, Google, LG, and even Samsung decided to change the way they issue updates to their devices, by pledging to release monthly security patches to plug up loopholes exactly like this one. Yeah, it's that big of a deal.

This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords

Security researcher Samy Kamkar, best known for his MySpace Worm, and most recently for his online calculator that can help you crack any Master Lock combination, is at it again. This time he's figured out how to break into security doors that have a motion-sensing egress system.

These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred.

Heads up! We've done a new, more thorough review of the best Android file-sharing apps. You can check that out here. Our old file-sharing app roundup can still be viewed below for posterity.

Do you remember the last time we used BeEF? Well, now we get to use it again, but this time with MITMf! We are going to auto-inject the hooking script into every webpage the victim visits!

Last year, Apple debuted a feature that allows families to share iTunes and App Store purchases across their various accounts. Us Android users, on the other hand, have to buy separate copies of apps for each of our accounts—well, at least from an official standpoint.

SoundHound, the Shazam-like song-matching service, recently announced a new mobile app called Hound, which wants to be your one and only intelligent personal assistant.

Believe it or not, not every Apple lover is willing to make the commitment and fork over $350+ for the Apple Watch. Like many others, I'm not willing to put that much faith into Apple's first attempt at wearable tech.

One of the many additions that appear on Android 5.0 Lollipop is a handy menu that lets users correct for or simulate different types of color blindness. While Google didn't flip the switch on this new feature until Lollipop was released, it turns out they had been working on it for quite some time.

What Is IPython? IPython is a richly featured replacement for the standard python interpreter. It offers a wider range of functionality, that the standard

Get some tinfoil hats and make a time machine because we are about to go back to the 90s and learn about some phreaking.

When you see a color depicted on your computer, smartphone, or tablet, odds are it was processed as a hex triplet before it was rendered. Most modern websites and operating systems use a hexadecimal coding system to signify certain colors, and these are represented as 6 letters and numbers.

Big box stores love to sell gift cards, and as consumers, we snap them up almost as quickly as they can be printed. This industry has become rather profitable, though, because portions of the gift card balances often go unused.
Now that the Xposed Framework has finally been updated for Android Lollipop, we're starting to notice that some modules function properly, while others are a bit buggy or even worse—don't work at all. Most of this is a result of changes to elements of the Android system that KitKat modules relied upon, and such modules will need to be updated for 5.0 compatibility.
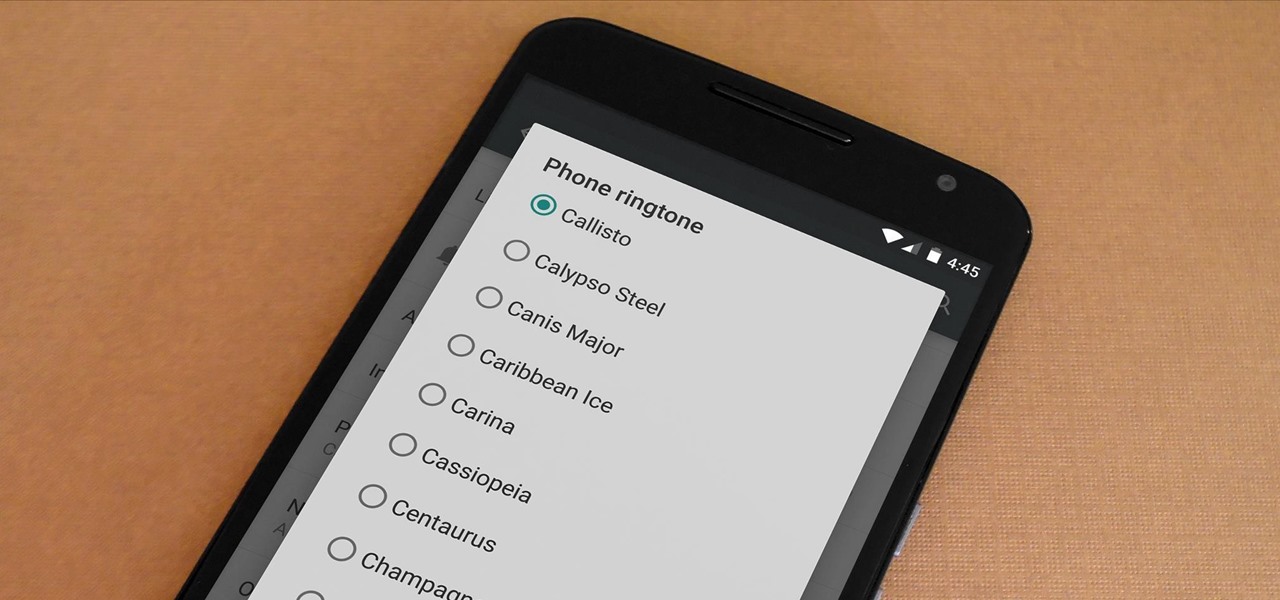
Most custom ROMs are built from the freely-available source code of AOSP, so they share a lot of common ground with stock Android. The difference, though, is the fact that Google adds many minor tweaks and finishing touches to AOSP while creating the version of Android that ultimately comes pre-installed on Nexus devices.

While shortcuts to your Camera and third-party apps like Snapchat are great for capturing fleeting moments, it still takes a few seconds to open them and snap a photo. That means you could potentially miss a great shot if you're not quick enough. But now there's a super-fast way to capture and send photos without having to waste time unlocking your device.
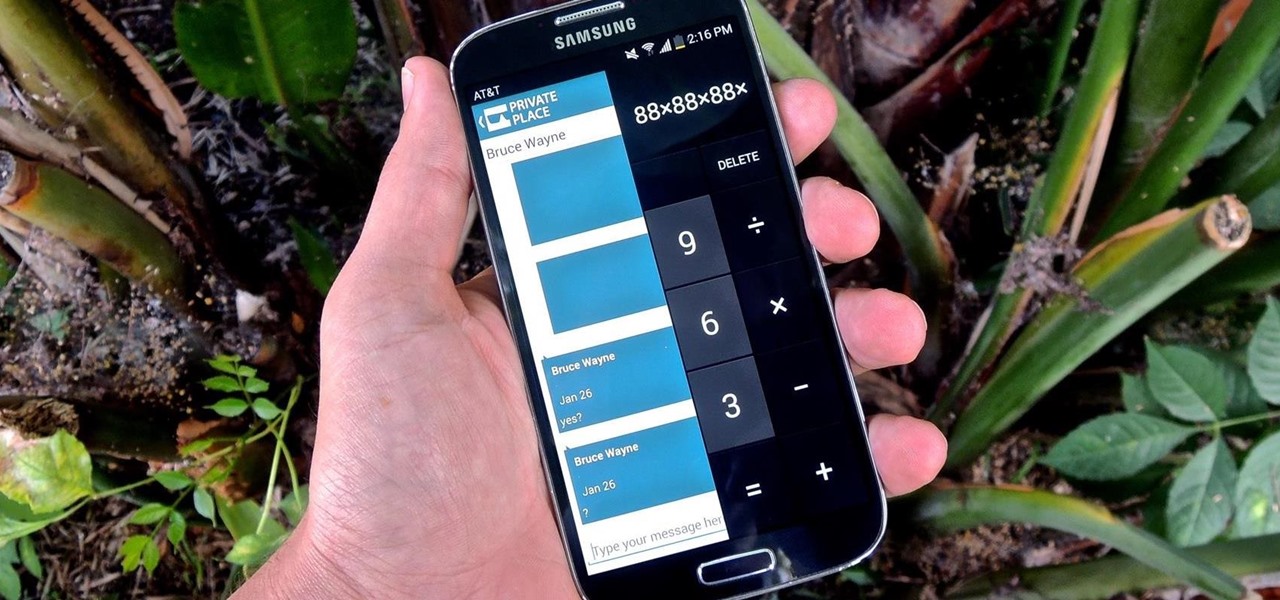
Whether you're a secret spy or just a regular person with a few secrets, you may want to keep certain information on your smartphone private, and it's totally possible on Android to do so.
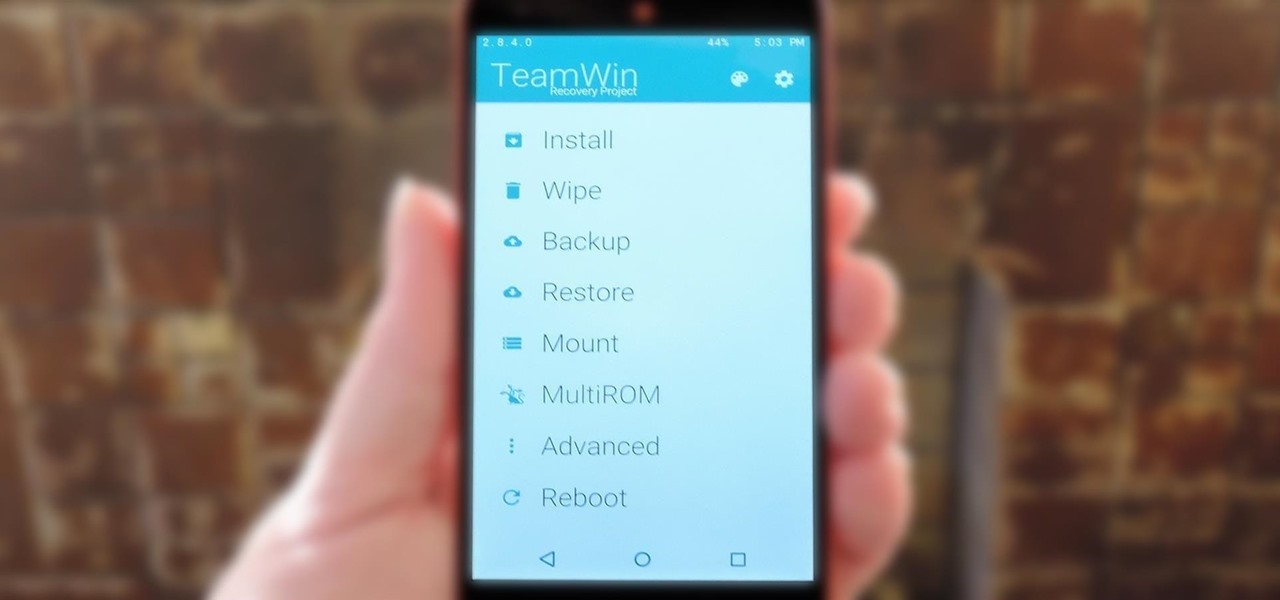
TWRP is hands-down the best custom recovery out there. Its interface, on the other hand, is... well, let's just call it utilitarian. The guys over at Team Win made sure that their product was robust, functional, and easy-to-use, but they didn't put a tremendous amount of effort into polishing the looks.