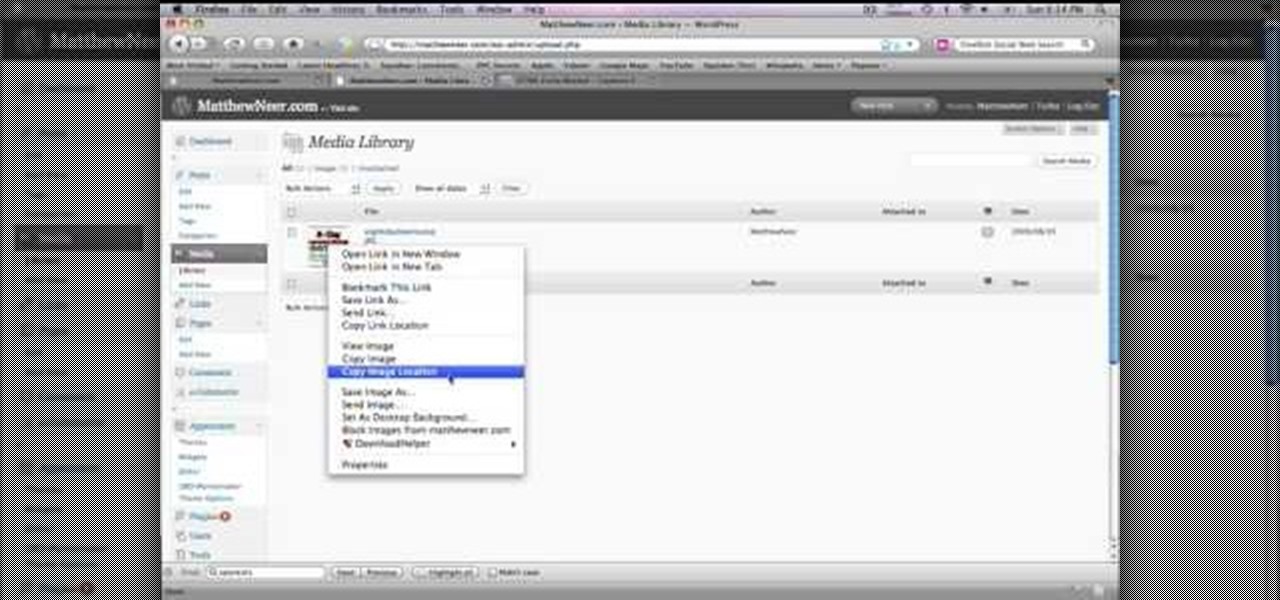
In order to create a custom caption box in WordPress you'll need to go to your dashboard. Here click on appearances, then on editor. Now over on the right select the sidebar option. Here you'll see some code, what you need to do is find the word that you want to replace on the main page, you can use ctrl+F to find the word. When you've found it within the code just replace it with whatever you want and then press the 'apply' button. You'll see that the main page will now be displaying the wor...
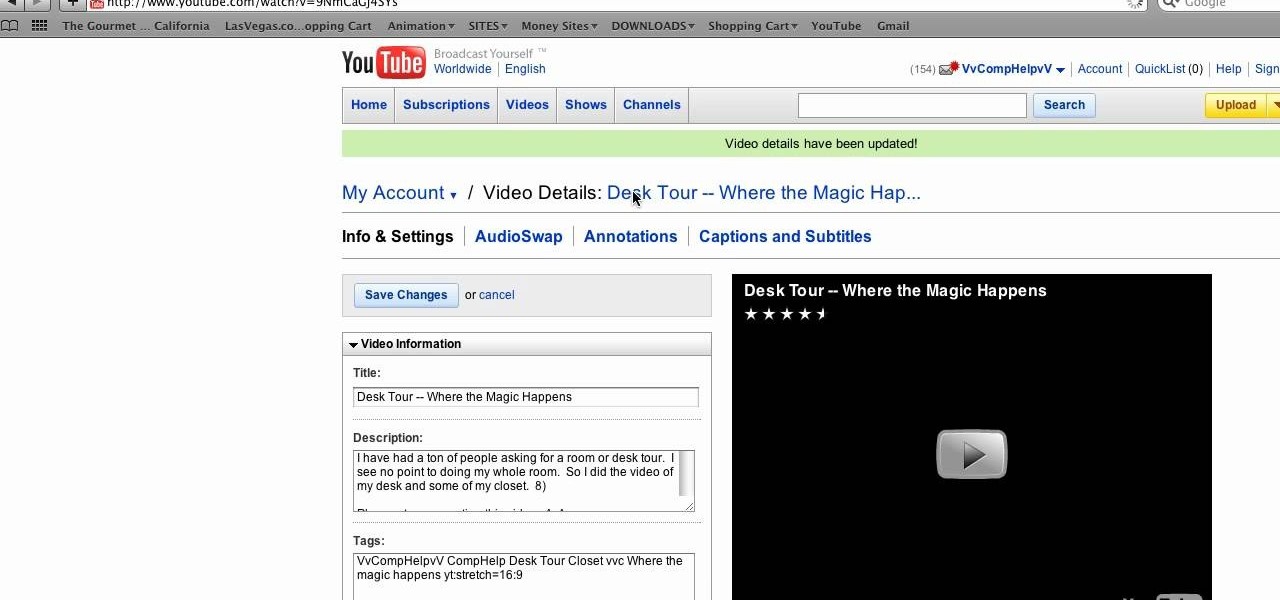
CompHelp uses his Mac to show us a new feature that the website has recently introduced. This feature allows people to use a simple code to crop, change, stretch, and even increase the quality of YouTube videos before they are uploaded. He starts out by showing viewers the memo where this information was released, then goes step by step to show interested parties how to use the special codes.He uses one of his own videos as an example, demonstrating what was wrong with it, then using the new ...
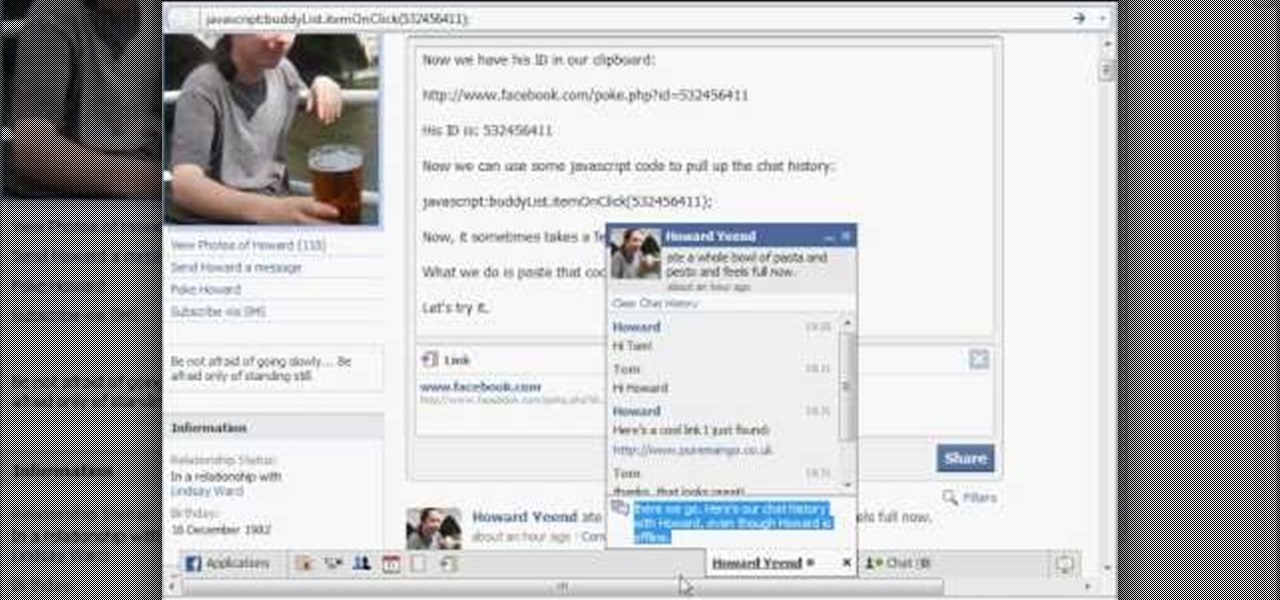
A Facebook profile page shows up explaining the steps on how to get chat history of a friend on Facebook. It explains that you need to go to the profile of the person you would like to find chat history with. It then explains steps on how you can copy there Facebook ID. Once you have accessed that he provides you with a JavaScript code to use to pull up chat history. He gives you step by step examples explaining how to set up the ID and apply it to the JavaScript coding. Once that has been es...
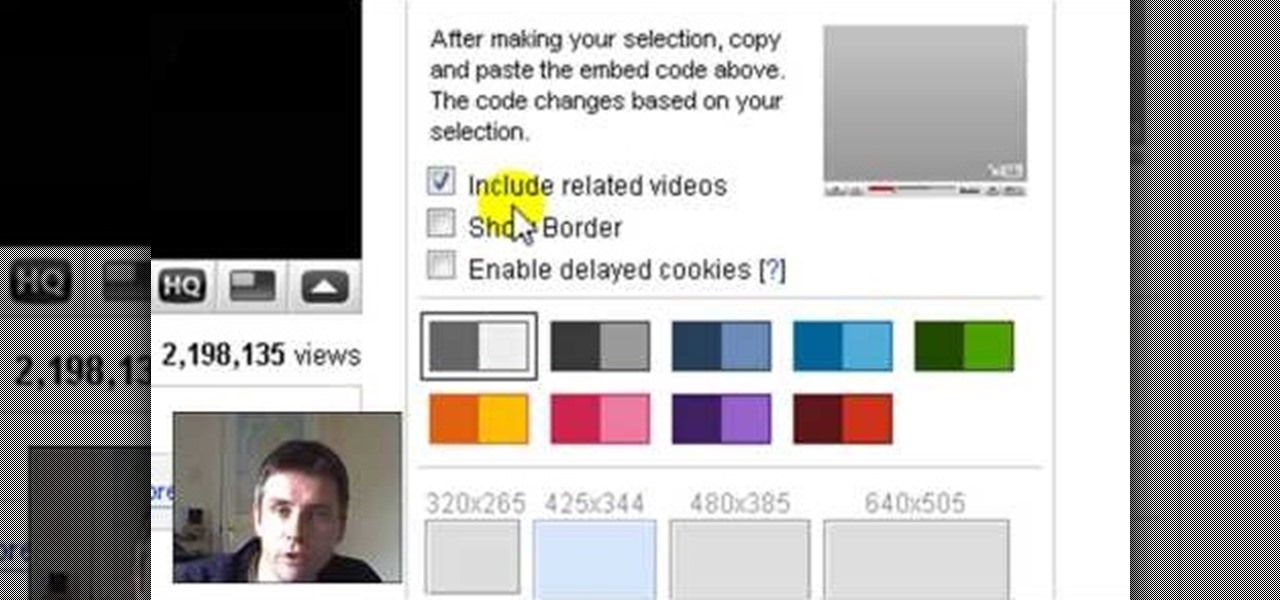
Learnasyouwatch shows viewers how to automatically play YouTube videos. First, you need to open your web browser and go to YouTube. Find the video you want to automatically play or upload your own video to YouTube. On the ride bar there is a section that says 'Embed'. Click on the pin wheel icon next to it that is 'customize' and you can set various parameters. Now, you need to copy the embed code and right click and copy this code. Paste this code into a word document. You will need to add '...
Cool tips and tricks on Facebook give you some extra edge on others. This trick will demonstrate that how to talk to your special loved ones that no one else can understand.

This video demonstrates tethering the MetroPCS Samsung Code to both a PC netbook and a Macintosh running Snow Leopard via bluetooth. Learn how to monitor your network speed, and see for yourself how webpages load through a thethered phone.

Going to be a nurse? Then one important part of your nursing responsibilities involves doing a daily check of the code blue cart or crash cart. The crash cart is checked every shift for emergency items and function. In this how-to video we review the nurse’s responsibility to test the defibrillator oxygen tank, most hospitals change tanks at 500 or 1000 psi. Follow along an see how simple it is to do a daily check of the code blue cart.

Looking to install a physics engine for Flex or Papervision? In this video lesson, Mike Lively of Northern Kentucky University demonstrates how to install the Wow Physics Engine into Flex 3 for use with Papervision3D. For more, and to get started installing the WOW-Engine on your own machine, take a look!

In this video we cover downloading Papervision 3D using tortoise svn then using those Papervision classes with open source code in Flex 3.

Mike Lively and Alissa Gilley show you how to use and customize their open source Flash video player in this tutorial.

In this video tutorial, Chris Pels will show how to make standard HTML elements in an .aspx page accessible from server side code so they can be used in page processing like a standard ASP.NET server control. First, see how the addition of a runat=”server” attribute to a standard HTML control like a div allows it to be referenced in server side code with full Intellisense. Next, see several examples of how you might manipulate HTML elements on a page with this technique. Lastly, see how this ...

I may be a bit weird, but I enjoy listening to music at night as I fall asleep. Sure, you could create a playlist of songs so that it stopped after all the songs finished playing, but I have a rather extensive database of music and I enjoy listening to them randomly. Also, I like to ensure it terminates after a specific amount of time (I don't want it playing all night). Or sometimes I use it when I am cooking so that when the music stops, I know I need to check on my food, etc.

Whether you're looking to add a substantial coding foundation to your hacking skill set or want to get a job in programming and development, knowing one or two programming languages just isn't going to cut it.

A stager is a small piece of software that's typically used by malware to hide what's happening in the early stages of infection and to download a larger payload later.

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.

One of the first steps when pentesting a website should be scanning for hidden directories. It is essential for finding valuable information or potential attack vectors that might otherwise be unseen on the public-facing site. There are many tools out there that will perform the brute-forcing process, but not all are created equally.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

In our last ARKit tutorial, we learned how to measure the sizes of horizontal planes. It was a helpful entryway into the arena of determining spatial relationships with real world spaces versus virtual objects and experiences.

If you're anything like me, when you first find a good song, album, or playlist on Spotify, your initial reaction may be to share it with your family and friends. While there are the usual share methods available in Spotify that are available in other streaming music services such as Apple Music and Google Play Music, Spotify goes one step further with QR-like codes users can easily scan.

If you own a Pixel or Nexus device, Project Fi is a great alternative for cellular service outside of the four major US carriers. Project Fi is a Google-managed MVNO, providing service primarily through the T-Mobile and Sprint networks. One of the biggest mysteries on Fi is which network you're connected to at any given time, but there's a simple solution.

We all know about partying like it's 1999, but what about gaming like it's 1999? The folks over at Irrational Games, the studio behind the new BioShock: Infinite, which was just released today, decided to go a little retro and include a hidden game mode for the most hardcore gamers. By default, the game starts out with the normal Easy, Medium, and Hard difficulties, with "1999 Mode" made available only after you beat the game. But if you enter in one these secret Konami codes provided below, ...

The cost of scrapbooking can really add up. You can still create wonderful scrapbooks to artistically document your memories by shopping smart and cutting costs by being resourceful. You can use things you already have around the house.

Unlock cheat codes on Guitar Hero III (3).

This four-part video tutorial is furnished by the (FCC) Federal Communications Commission shows you how to get ready for the digital television transfer. Is your television ready for digital? By February 17th, 2009 TV stations will stop broadcasting in analog and broadcast only in digital. Your TV needs to be ready so you can keep watching. Digital television, also known as DTV, is here, and after February 17th, TV stations will turn off their analog signal. The FCC wants to be sure you are r...

With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardriving data into Jupyter Notebook, we can map all Wi-Fi devices we encounter and slice through the data with ease.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

Password cracking is a specialty of some hackers, and it's often thought that raw computing power trumps everything else. That is true in some cases, but sometimes it's more about the wordlist. Making a custom, targeted wordlist can cut down cracking time considerably, and Wordlister can help with that.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

Hashes are commonly used to store sensitive information like credentials to avoid storing them in plaintext. With tools like Hashcat, it's possible to crack these hashes, but only if we know the algorithm used to generate the hash. Using a tool called hash-identifier, we can easily fingerprint any hashes to discover the right Hashcat mode to use to retrieve a password.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

MouseJack vulnerabilities were disclosed over three years ago. Some wireless keyboard manufacturers have since issued firmware updates, but millions (if not billions) of keyboards remain unpatched worldwide, either because they can't be updated or because the manufacturer never bothered to issue one.

While hackers know and love the Raspberry Pi, many don't know of its cheaper cousin, the microcontroller. Unlike a Pi, which can be used more or less like a regular computer, microcontrollers like the Wi-Fi connected ESP8266 require some necessary programming skill to master. In this guide, we'll build an Arduino program from scratch and explain the code structure in a way anyone can understand.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.