
You're Being Tracked: How Google Inc. Spies on Your Every Digital Move
The biggest corporation we know today is called Google, I bet you've heard of it yeah? How Google Tracks You:


The biggest corporation we know today is called Google, I bet you've heard of it yeah? How Google Tracks You:

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)

Welcome back, my tenderfoot hackers! Have you ever wondered where the physical location of an IP address is? Maybe you want to know if that proxy server you are using is actually out of your local legal jurisdiction. Or, maybe you have the IP address of someone you are corresponding with and want to make certain they are where they say they are. Or, maybe you are a forensic investigator tracking down a suspect who wrote a threatening email or hacked someone's company.

Two brands with affinities for augmented reality, Marvel and the NBA, joined forces to inject some AR superpowers into Monday night's matchup of the Golden State Warriors and New Orleans Pelicans.

How do spammers get your email? You give it to them. Not directly, no — you sign up for an app or service and happily hand over your email to verify your new account, then that app or service sells your email address to marketers who now know what kinds of apps and services you like.

UPDATE: Entries are now closed. Thank you for participating! Next Reality is where we help you literally 'see' into the future of augmented reality, and to help with that mission we're offering three free pairs of Snap Spectacles 3 to three lucky readers who sign up for the Next Reality daily AR email newsletter.

The words of three of tech's most important executives in the last 48 hours are providing some valuable insight into the near term future of augmented reality and the cloud infrastructures that support it.

It's safe to say that we can call the annual ranking of AR investments a holiday tradition at Next Reality.

The landscape of the augmented reality space is broad, diverse, and constantly shifting, perhaps more so than any other vertical in technology. At the same time, major players are attempting to standardize various hardware designs and delivery methods, while still others are rushing to claim their piece of virtual property through AR clouds and application stores.

The mysterious technology product teased via an eccentric TED Talk nearly five years ago has finally been revealed, and it's called the Magic Leap One: Creator Edition. After all of the non-disclosure agreements, furtive comments from CEOs and insiders given early access to the device, and a seemingly never-ending string of hints dropped by the company's CEO, Rony Abovitz, on Twitter, we finally have a real look at the product.

Welcome back, my tenderfoot hackers! Well, the first season of Mr. Robot just ended and Elliot and fsociety successfully took down Evil Corp! They have effectively destroyed over 70% of the world's consumer and student debt! Free at last! Free at last! Of course, global financial markets crashed as well, but that's another story.

Welcome back, my greenhorn hackers! As all you know by now, I'm loving this new show, Mr. Robot. Among the many things going for this innovative and captivating program is the realism of the hacking. I am using this series titled "The Hacks of Mr. Robot" to demonstrate the hacks that are used on this program.

Welcome back, my novice hackers! The worst thing that can happen to any hacker is being detected by a security admin, the security technologies (IDS, firewall, etc.), or a forensic investigator.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

Food labeling is a tricky beast. For instance, when I read the words "cage-free" on an egg carton, I think it means that happy chickens frolic in a sunlit meadow all the livelong day until they're gently herded into a clean, sweet-smelling coop to lay a few dozen eggs—which I can purchase for a reasonable price, of course.

Snapchat and its augmented reality capabilities have become a haven for music artists seeking to promote their new albums or simply amplify their art with immersive experiences.

The augmented reality industry has grown steadily over the past four years, but now it is on a collision course with uber-popular non-fungible tokens technology, with Looking Glass and music artist Reggie Watts among the latest to strike while the iron is hot.
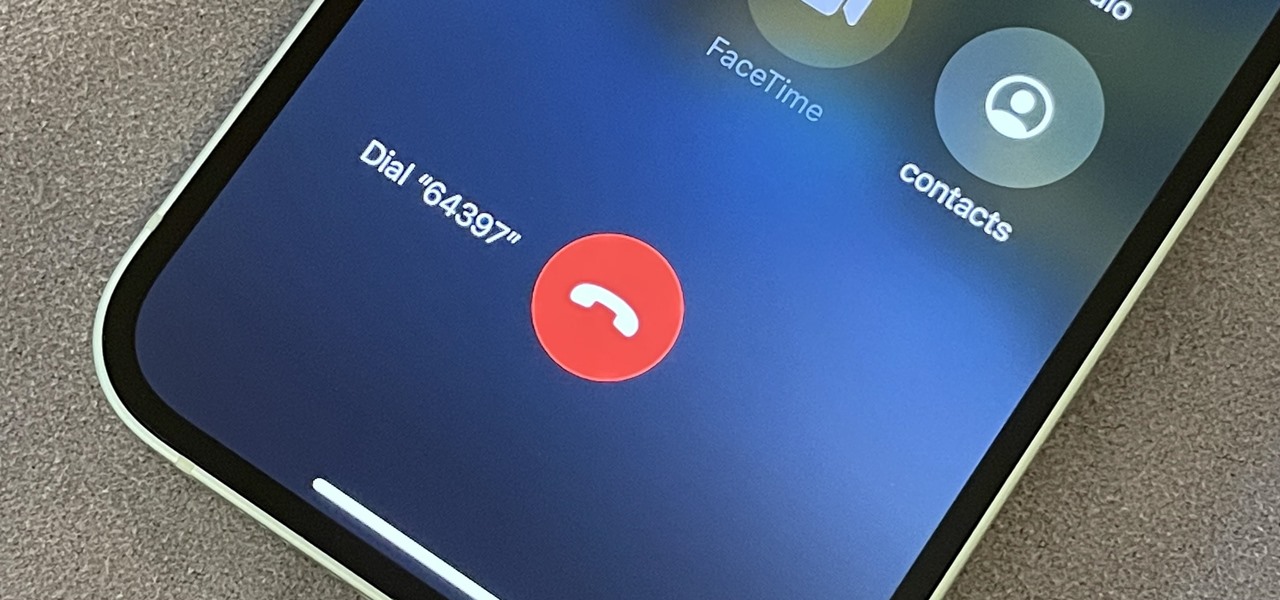
Automatic phone menus are the worst. You call the number, listen to prerecorded prompts, press button, listen, press button, listen, press button, listen, until you're routed or connected to the right extension, directory, menu, person, or whatever. But you can bypass these automated attendants to get right to where you need to go by setting up a simple shortcut on your iPhone.

There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.
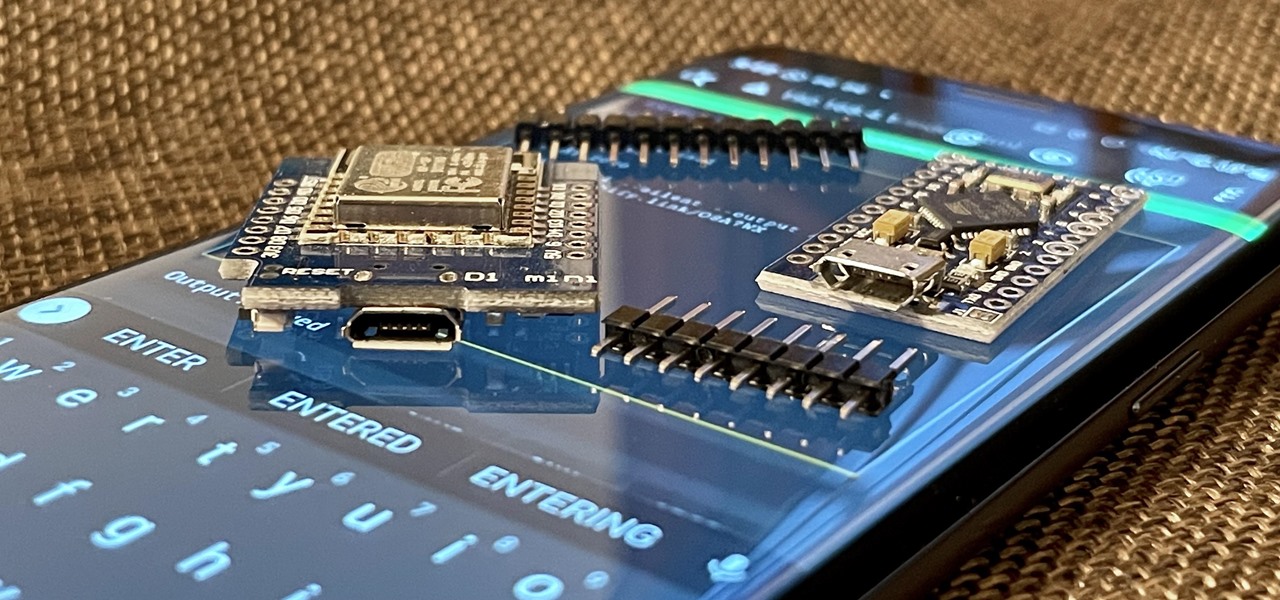
With just two microcontrollers soldered together, you can inject keystrokes into a computer from a smartphone. After building and programming the device, you plug it into a desktop or laptop, access it over a smartphone, and inject keystrokes as you would with a USB Rubber Ducky.

Android 11 is here. Prior to Google dropping the naming scheme, this would have been a dessert with an R name (maybe Rice Krispies Treat or Red Velvet Cake) — but nope, just plain ol' Android 11. And after months of betas and a global pandemic, it finally debuted a little over a year after Android 10.

Squash is a racquet sports game, seemingly similar to tennis, but played on a small indoor court with hollow rubber ball, much small than a tennis ball. Squash is an intense, high impact sport. This squash tutorial demonstrates a squash forehand volley drop off cross court.

When you resort to the small claims court, keep your case simple and your questions short. This video will tell you what you have to do in small claims court and how to do it. Represent yourself in small claims court.

Squash is a racquet sports game, seemingly similar to tennis, but played on a small indoor court with hollow rubber ball, much small than a tennis ball. Squash is an intense, high impact sport. This squash tutorial demonstrates Squash backhand drive from the front court.
The top-secret US National Security Agency is not required to reveal any deal it may have with Google to help protect against cyber attacks, an appeals court ruled Friday.
The link to this site takes you to the official website of the Supreme Court of the United States. It is a useful source for information about Supreme Court cases, journals, and orders of the court. The US government is separated by three branches of government one of them being the judicial branch. The power of the Supreme Court is to uphold the law and they make final decisions. To be part of the Supreme Court the qualifications are: if the president likes you, needs to have a law degree, a...

Ade Adepitan who plays for the Great Britain wheelchair basketball team, shows you how to maneuver your way around the court. The most impressive technique involves just hip action, leaving the hands free for dribbling, shooting and defense. Maneuver on the court in a wheelchair.

The U.S. Circuit Court of Appeals for the District of Columbia has demanded that the TSA explain why it has ignored a now year old order to conduct a public comment process with regards to its use of so called naked body scanners. » Court Orders TSA To Explain Why It Continues To Defy The Law Alex Jones' Infowars: There's a war on for your mind!.
Qualifications and Powers I. Executive (President)

Squash is a racquet sports game, seemingly similar to tennis, but played on a small indoor court with hollow rubber ball, much small than a tennis ball. Squash is an intense, high impact sport. This squash tutorial demonstrates a Squash backhand volley, boast, drive off.

Video games are the newest major expressive media. As such, their role in society is still being defined continuously. A monumentally important example of this took place yesterday at the US Supreme Court. After a long deliberation, the highest court in the land handed down a decision invalidating a California law banning the sale of violent video games to minors on the grounds that video games are protected speech under the First Amendment, like movies and books.

Rick Perry: Texas Won't Implement Obamacare - Fox News.

Despite Ruling, Jack Lew Refuses to Call Health Care Mandate a Tax - ABC News.


You just need a small urban area like in an alley by the back of a building, a bball court, or tennis court, or whatever. Line up two teams on opposite ends of each other (like in dodgeball) , line up a bunch of shit-smeared grapefruits in the middle, a "ref" (Loomis) shouts, "Pooball, GO!", and everyone runs towards the poofruits and begins pelting each other with shit-stained grapefruits. When you get nailed, you're out. Pelt away until you have a winner.

Your constitutional right to privacy cannot be violated by police, so ruled the United States Supreme Court in a unanimous decision on two cases from California and Massachusetts—a major ruling for privacy advocates worldwide.

Misty May shows you why passing is one of the keys to scoring on the volleyball court. Pass in volleyball.

Wiretaps, which have increased almost tenfold since data was first reported in 1969, are only the tip of the surveillance iceberg. In 2011 federal and state courts approved a total of 2,732 wiretaps; but government agencies made over 1.3m requests for data to mobile-phone companies. That figure includes wiretaps and pen/traps, but it also includes requests for stored text messages, device locations and tower dumps, which reveal the presence of everyone—suspects and not—within range of a parti...