Motorola changed the way users interact with their devices when they introduced their "always listening" feature on the Moto X. When I first saw it demoed, I couldn't wait to get the same functionality on one of my handsets, and now that has finally come to fruition.

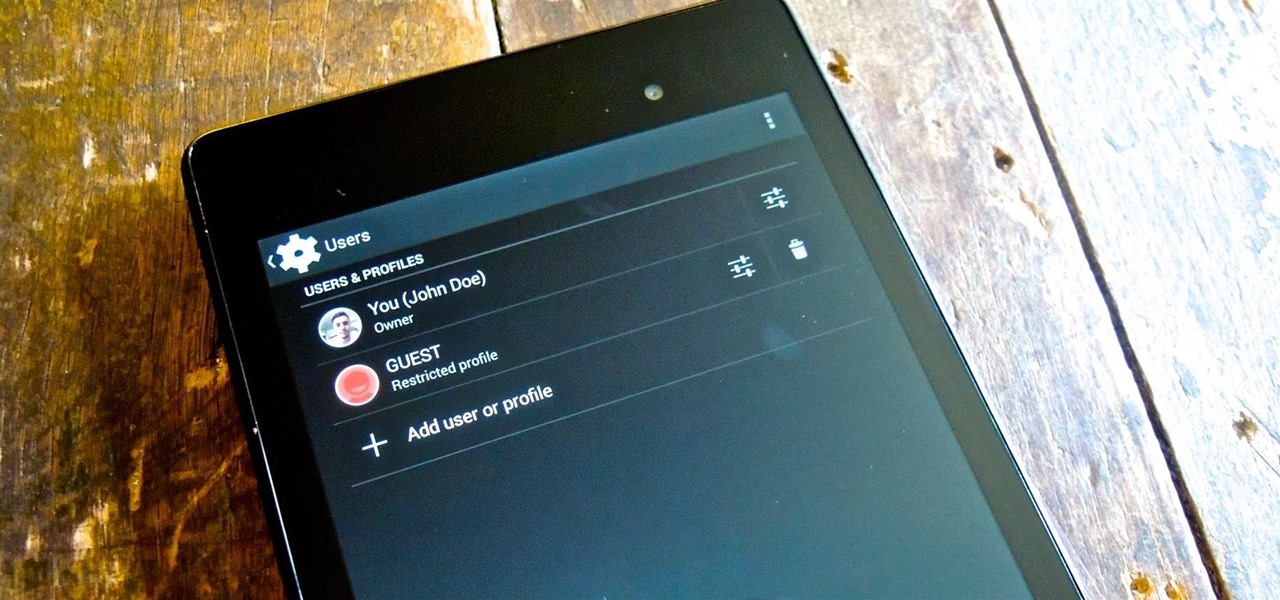
Whether if it's to play games or watch Netflix or YouTube, children love using our smartphones and tablets. As an uncle of many, I don't mind my nieces and nephews using my gear, but I do mind them opening apps they have no business being in, like my photo gallery or messaging app.

As you already know, Hong Hong has been rocked in recent weeks by protests against their Beijing overlords. Promised free and fair elections, Beijing has reneged on this promise and is now telling Hong Kongians (that's what they're called, aren't they?) that they will only be able to vote on Beijing-selected candidates. All that is interesting from a political perspective, but from a technological perspective, the more intriguing story is how the protesters are communicating. Faced with their...

Anytime you surf the web on your iPad or iPhone, Safari saves which webpages you visit, the information you enter into them, and other types of data. This not only make your internet experience quicker, but it'll also keep track of everything you're doing.

Only scumbags hide their call and message history, right? Wrong. While it may seem like a tactic for the unfaithful, it's still a good thing to do for certain contacts on your phone that you don't want to block outright.

Unlike the suave 007 that Daniel Craig portrayed, I am not a spy, nor am I that charming, but I do occasionally enjoy taking a stealthy video. Maybe I'm a jerk, but I often catch people doing ridiculous things and just think, "Aren't you embarrassed?"

Ever use an open hotspot on your Note 3, only to find out that it's severely restricted to what sites you can access? While getting online with free Wi-Fi is great for those who have a limited data plan, when that one site you absolutely need to visit is blocked, you're left frustrated and sent back into the Wi-Fi menu for another access point.

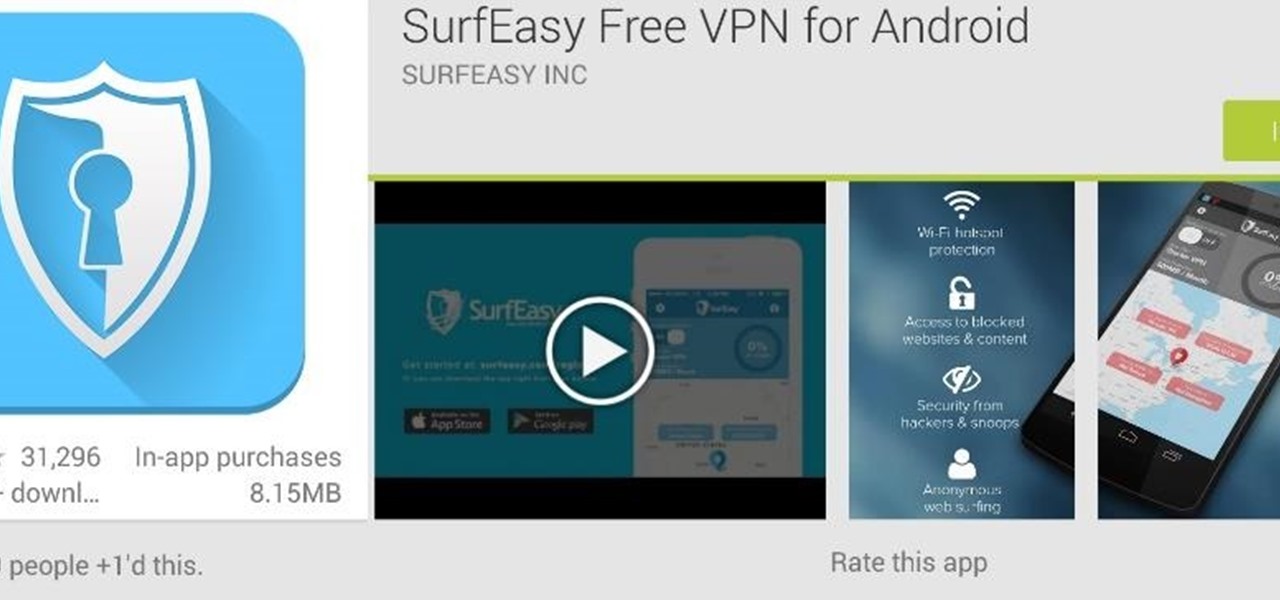
When browsing the web, you may not be quite as anonymous as you think, especially if you are using public WiFi. The easiest way to stay as anonymous and safe as you are going to get, is to use a VPN (there are a number of great free ones). In this tutorial, we will show you how to set up a VPN on Android, and how this protects you.

Cultured dairy products are great for topping chilis and soups, stirring into dips, and adding tanginess to breads and pancakes. They're extremely versatile and often interchangeable, and they contain probiotics that offer a long list of health benefits. They're also super easy to make at home with just a few basic ingredients. Here's how to make your own buttermilk, sour cream and crème fraîche.

Whenever I hand my tablet over to someone, my heart always races for a second at the thought that they may stumble across my private pictures, texts, and videos. I trust them, and they may not be the snooping type, but it can be easy enough to come across private stuff by accidentally opening a gallery or messaging app.

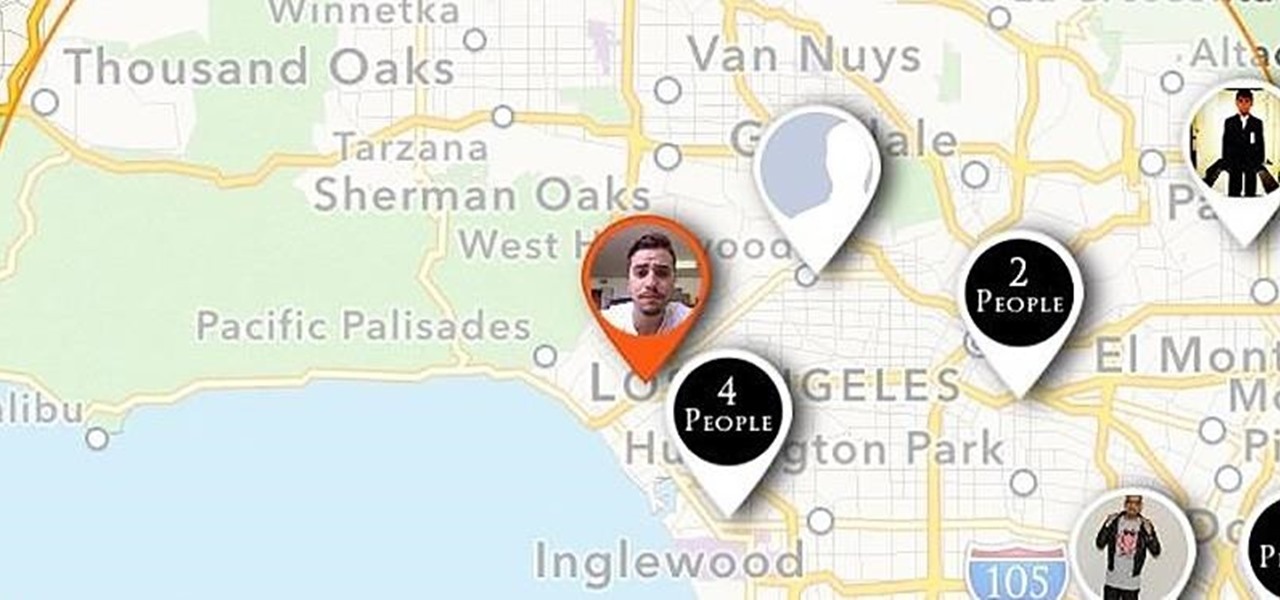
Imagine that Tinder fornicated with Facebook and had a baby. The product of that union would be the hideous, yet overwhelmingly interesting SocialRadar, an app dedicated to stalkers and stalkees.

Privacy features have become quite the hot commodity, emerging from the aftermath of the NSA scandals that rocked the United States this past year. While the NSA has the means to gather information on all of us (regardless of any security software we implement), it doesn't mean that they're the only ones looking.

Last week, Apple issued an iOS 7.0.6 update that fixed a serious security vulnerability that could allow hackers to steal passwords, read emails, and get info from other SSL-encrypted communications.

If somebody really wants to gain access to your iPhone, they'll get in. Phone thieves (and mischievous friends) can easily figure out your passcode just from looking over your shoulder or tracing over the oily smudges on the screen. And if you're using popular passcodes, birthdays, and addresses on your iPhone, you might as well disable lock screen security entirely.

Presentational video for our DIY Camera Crane project. Video: .

My friends can be pretty shitty sometimes, but they're my friends nonetheless. On various occasions, they've secretly taken my device and made me look foolish by posting crude and embarrassing posts to Facebook, Instagram, or Twitter. With friends like these, who needs enemies, right? And it's because of these types of friends that we need to substantially upgrade the app security on our devices.

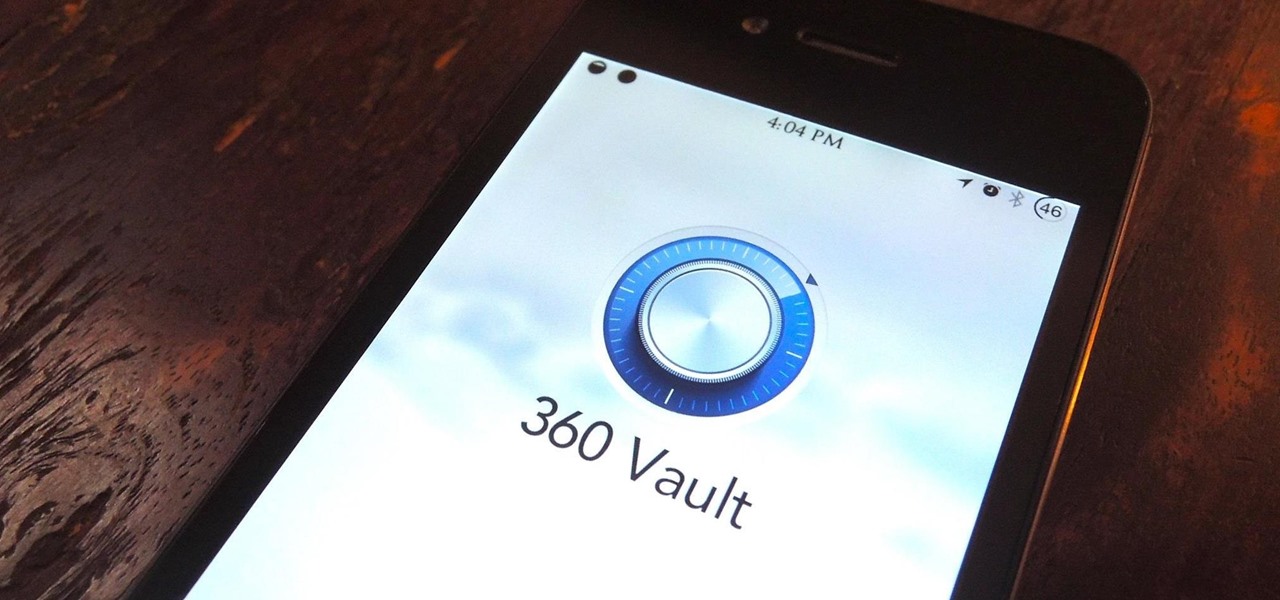
Let's be honest for a second; we all have sensitive material on our phones that we wouldn't want anyone else to ever see. Maybe it's to protect ourselves or someone else, or maybe it's none of your business why I don't want you to see pictures of my bachelor party. Regardless, sometimes we need to keep things hidden and safe.

Let's just say it's been a pretty bad year for spies and government agencies and an even worse one for the privacy of U.S. citizens. Edward Snowden blew the lid off the NSA's spy program, and the FBI was recently discovered to have the ability to access your webcam any time they want—without triggering the "camera on" light. Yeah, that means those Justin Bieber lip sync videos you recorded weren't just for your private collection.

Snapchat was created for the sole purpose of removing evidence from your mobile that a photo or video ever existed. That way, snoopers can't find any of these questionable selfies in your photo gallery. Of course, there are plenty of ways around this safeguard, but it's still more private than the standard social networking app.

Cars are quite different than they used to be. Sure, modern cars have some cool things, but repairing them are becoming difficult. Even simple things like changing a headlight bulb.

If you weren't aware, all music purchased online through iTunes, Amazon, and other digital audio providers have information embedded that can be used to identify the buyer and transaction of the digital music file. This may seem like something you should be disclosed about in their terms of use, but it's not.

Welcome back, my greenhorn hackers! Congratulations on your successful hack that saved the world from nuclear annihilation from our little, bellicose, Twinkie-eating dictator. The rest of world may not know what you did, but I do. Good job! Now that we hacked into the malevolent dictator's computer and temporarily disabled his nuclear launch capability, we have to think about covering our tracks so that he and his minions can't track our good works back to us.

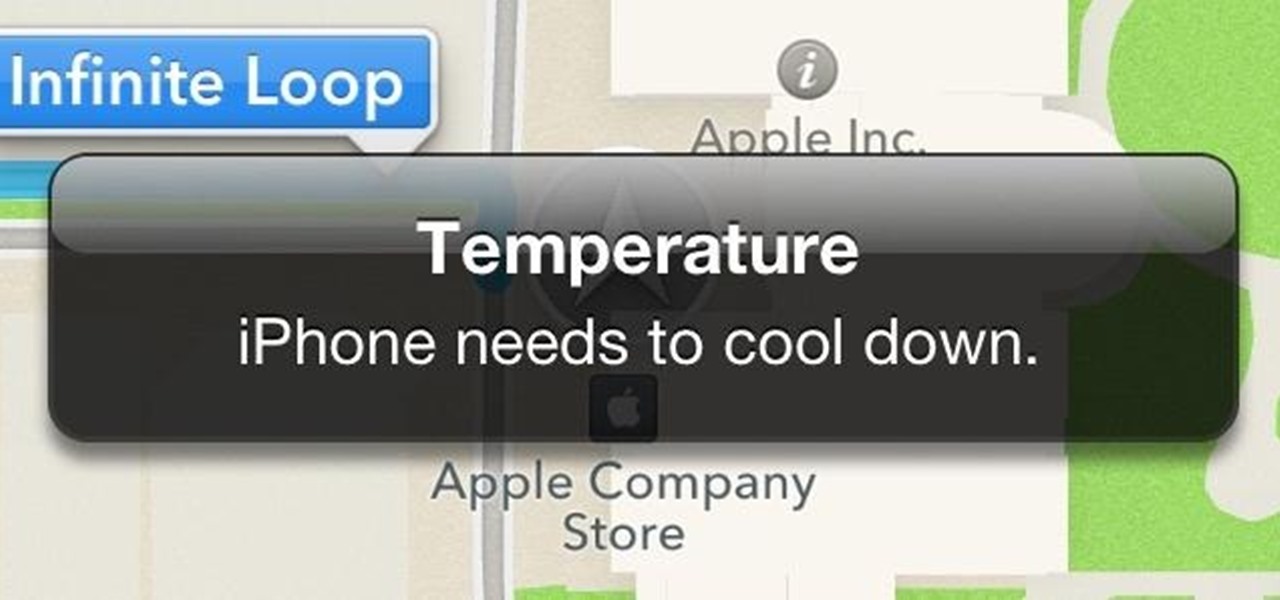
A few months ago I was driving around trying to find a store using Apple Maps (a terrible situation in and of itself), when my iPhone decided to shut off in the middle of giving me directions. I had no idea what happened, and when I looked at the screen, I saw this: My phone had never overheated and I really didn't know what to do. Needless to say, I couldn't really get to where I was trying to go without those directions. I pulled over and waited for the phone to cool back down, which took a...

I've had a thing against bananas ever since Mario Kart; not only do I believe it's the worst weapon in the game, but it's also a very funny-looking food. Nevertheless, bananas are a great source of potassium, and I can't overlook that.

In this video tutorial, I am going to demonstrate how to clean a spray gun by hand with a few simple steps.

The allure of Snapchat is that all pictures and videos sent through the app vanish a few seconds after being sent. They're completely obliterated not only from the phone, but from the Snapchat server, as well. The popularity of the application has even incited Facebook to release its own real-time picture and video messaging application, aptly titled Poke. One of the biggest criticisms (besides the wave of recent security issues) of Snapchat is that even though the messages self destruct and ...

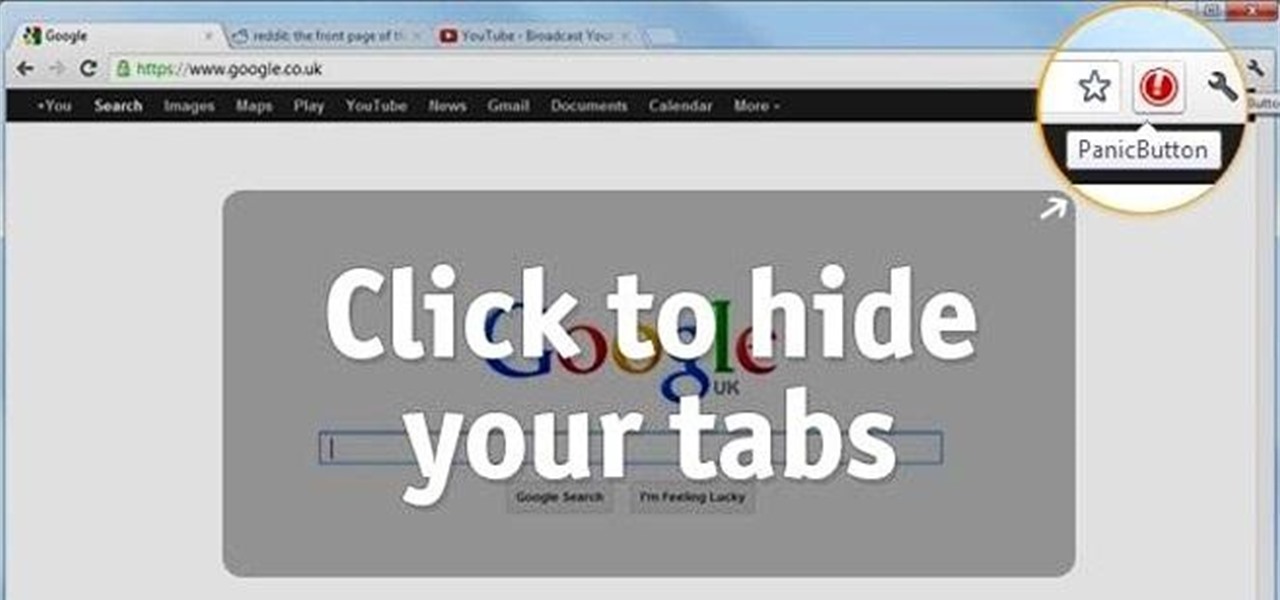
At some point or another, we've all been in that awful situation when someone walks up behind you while you're looking at something you don't want them to see. Whether you're tweeting during class, shopping for gifts online, or looking at something a little more NSFW, there are times when it would be nice to just click a button and have all your open tabs disappear.

No matter how many PSAs are published on the topic, studies continue to show that we are generally terrible at creating secure passwords and PINs. Using the same password (or variations of it) for multiple sites is another huge no-no that the majority of people ignore, and even though you should change your passwords frequently, most of us don't.

Here's a technique I used to whip up a batch of super cheap and easy to make smoke flares! WARNING: Ignition of an incendiary or explosive material may not be legal in your area, so check local laws before attempting. Use of this video content is at your own risk.

Microsoft's updated web browser, Internet Explorer 10, has only been out for a few days on Windows 8, and there is already a storm of controversy surrounding its launch.

Android has released a new application called ezNetScan, which is a free app that scans the wireless network you're connected to and gives you a full log of all of the devices connected to that network. This isn't new for smartphone users, let alone Android users. Fing has been around for a while and does practically the same thing that exNetScan does. It gathers information such as the IP and MAC addresses, device vendors, and ISP location. But while Fing is a great program, it does lack a f...

So you've decided to go as Captain America for Halloween and you've got everything from the helmet to a sweet pair of red boots. You've even managed to get your hands on some Super-Soldier Serum (or a realistic set of inflatable muscles), so you've got the physique, too. But what's missing? His shield! In order to make your Captain America costume legit, you cannot skip the shield. Fortunately, it's pretty easy to make yourself a DIY shield—so you can fend off enemies and look good doing it. ...

If you've ever logged on to the popular music application Pandora, your password is saved onto that computer in the local storage...for good.

If you're tired of your roommate stealing your Cheetos out of the pantry or simply want to indulge in something creepy, then keep reading. With the iPhone 5 finally released, many people will soon be selling or giving away their older iPhones. But should they? Instead of ditching your old iPhone, why not use it to engage in some Big Brother type espionage? There are some really awesome ways to use your old iPhone, but spying on people is definitely the most bang for your buck. First, you'll w...

Think your roommate's been using your computer while you're not around, but don't have any proof? Worried your little brother or significant other is snooping through your stuff? Here's how to check on both Windows and Mac OS X so you can catch and confront anyone who's logging onto your computer without your permission.

Facial recognition software is being more widely used with every passing day. Your local law enforcement is probably already using it, and it will be even easier for them now that the FBI handed out its own facial recognition software to state authorities. Even the fine folks at Facebook are using this technology. Obviously, this brings up some pretty serious privacy concerns amongst most people, because honestly, who wants to be tracked? Right now, there's not a lot we can do about it being ...

There are tons of situations that require you to give out your phone number, and I think just about everyone has regretted doing so at some point. It can be incredibly convenient to have a secondary or temporary number on hand, so if you don't want to provide your real digits, you can still get the call without revealing your true numbers. And that's where Burner comes in. Burner is a mobile app for iPhone and Android that lets you create alias phone numbers that you can take out of service a...
As a pale white boy growing up in Florida, you learn how to deal with sunburns. Most people will say to take cool showers to relieve the heat, but that only temporarily alleviates symptoms. The problem is that the sun has evaporated the moisture from the skin. The answer to relieve the stinging and pain is to re-moisturize the skin. I've done this countless times and it always works.

If you've read anything in the news about Skype recently, it probably hasn't been good. First, there was the controversy over the company listening to and recording users' conversations. Now, there's a new spam tool for Skype that can harvest usernames, see whether or not you're online, and even parse your log files. Image by Lloyd Dewolf

If you use Ubisoft's uPlay browser extension, you should probably get rid of it right now. An Information Security Engineer at Google discovered that the plugin has a hole in it that allows programs to be installed through uPlay, essentially letting anyone who feels so inclined to take over your computer. How the Exploit Works