Dropbox continues to make headlines with their recent programming blunder which left the accounts of its 25 million customers wide open during a four-hour time span. During the duration, anyone in the world could access any Dropbox profile by typing in any password. And seeing as this wasn't the first security failure, everyone, including the most loyal users are considering dropping the Dropbox.

In my earlier post about long-term strategies I promised I’d ask some of my neighbors who do what I call factory chicken farming (Let 1000 Chickens Bloom) if the coyotes that have shown up will change the way they play the game. The one guy who replied in any detail said that he wasn’t sure what he was going to do yet, but he thought that he was losing 50 chickens each time he harvested them pressing “Collect Bonus” using a coop.

The Farmer's airship is here on FarmVille to protect your crops!! Place it and nothing will wither for 10 days!

A team of Japanese researchers have developed an airbag system for the exterior of the car, rather than the interior, with the purpose of protecting pedestrians.

Life is getting more and more convenient. You can pick up a wireless signal at nearly any coffee shop these days (Starbucks is now officially free in every location across the nation), as well as airports, libraries, hotels and more. However, along with this convenience comes the risk of security breach. Passwords. Emails. Account numbers.

Alter Evo on Flickr has created this amazing starfighter and service unit vehicle. This is what he says about it:

Ok, this is a dumb movie. It's really, really, really dumb. But it's one of my favorites precisely because it's so stupid.

No kidding, watch below as 500,000 volts of electricity literally course over a man's body. Of course, he has a little protection: the faraday suit. The video was shot in Austin, Texas, for a German television documentary. Producer Johannes Wiebus is quoted as saying:

Cats are particularly prone to eye infections, which can cause serious health risks. Protect your cat! Learn how to safely and easily give your cat eye drops or ointment, with advice from Battersea Dogs and Cats Home in London. To keep your pet healthy you have to be able to apply the medicine it needs. Tips include: wrap your cat in a towel to prevent her from scratching you and point the tip of the bottle at an angle, not directly down onto the eyeball. Give your cat eye drops.

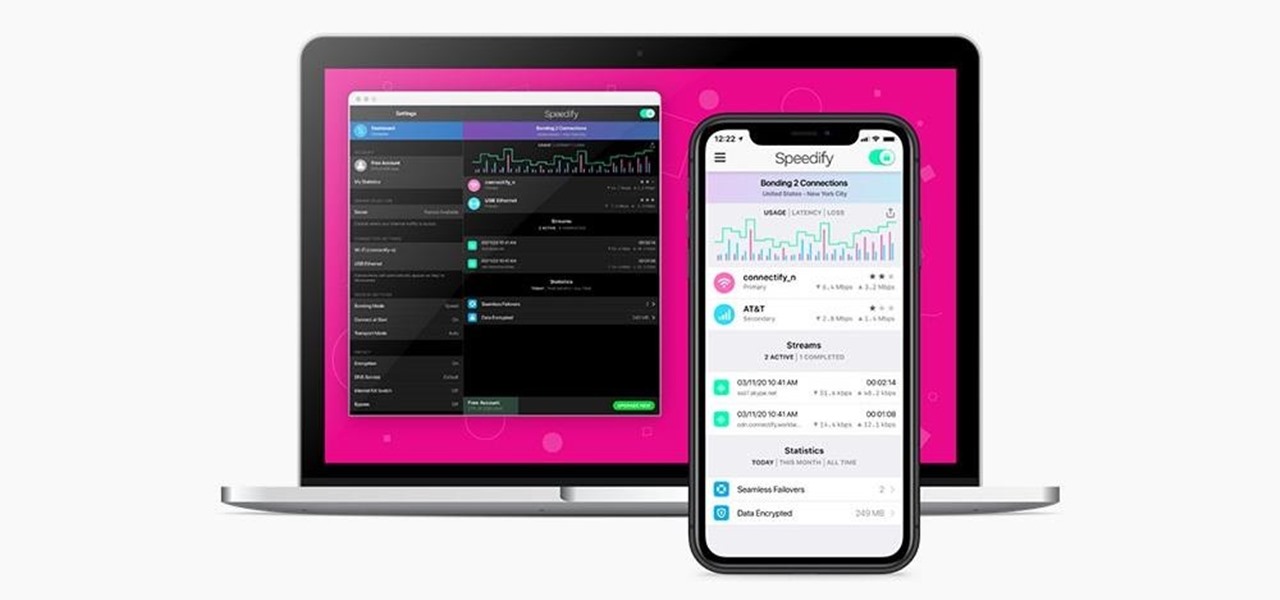
We've all relied on the internet more than ever during this pandemic. But while you're staying safe at home, are you being safe and productive while surfing the web? That's where a trusty VPN comes in handy!

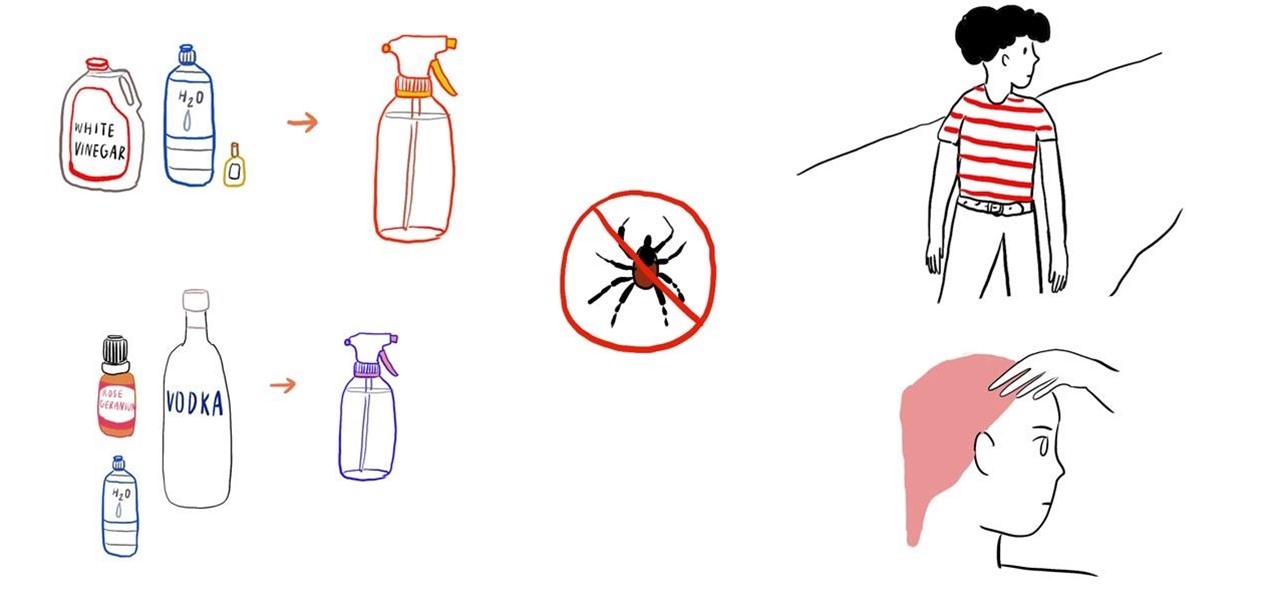
With tick-borne diseases on the rise, it is especially important to protect yourself from the prevalence of ticks in the outdoors, especially if you live in a high-risk region like New England, the mid-Atlantic states, and the upper Midwest.

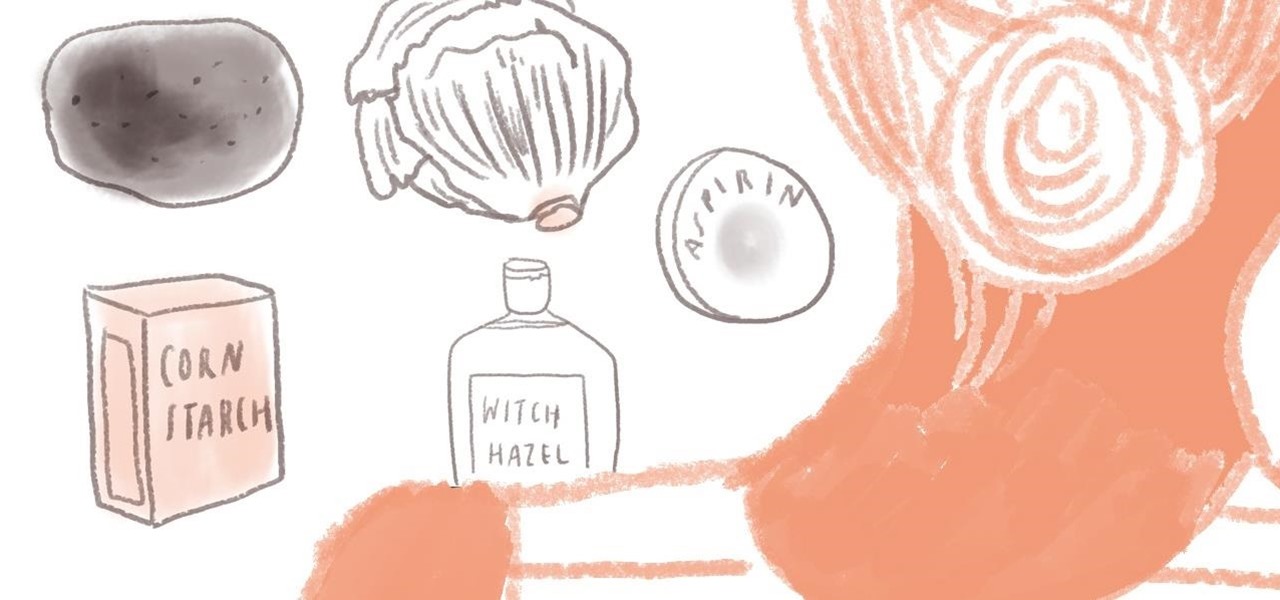
Though summer is almost over, that doesn't mean you should ever be lax when it comes to protecting your skin from sun overexposure. However, should you find yourself with red and burning skin after a last-minute weekend trip to the beach, listed below are 9 simple and cheap home remedies for relieving symptoms of sunburn.

chapped lips is a very common issue and usually face us in summer especially when sweating is excessive and water intake is at its minimum. all that affect our body and it induce inflammation in our lips which leads to fissuring in lip mucosa which is famously known as chapped lips.

If you ever need to wash your beanie and need some sort of hat mould to retain the shape of the fabric while it is drying, blow up a party balloon until it is about the size of your head. Place the beanie on top of the balloon until it dries.

Who doesn't want to decrease time wasted looking for misplaced car keys or remembering a long-forgotten computer password?

Though feeling cold during the winter is pretty unavoidable, you can definitely prevent the torment of having flaky, dry skin during the cold winter months.

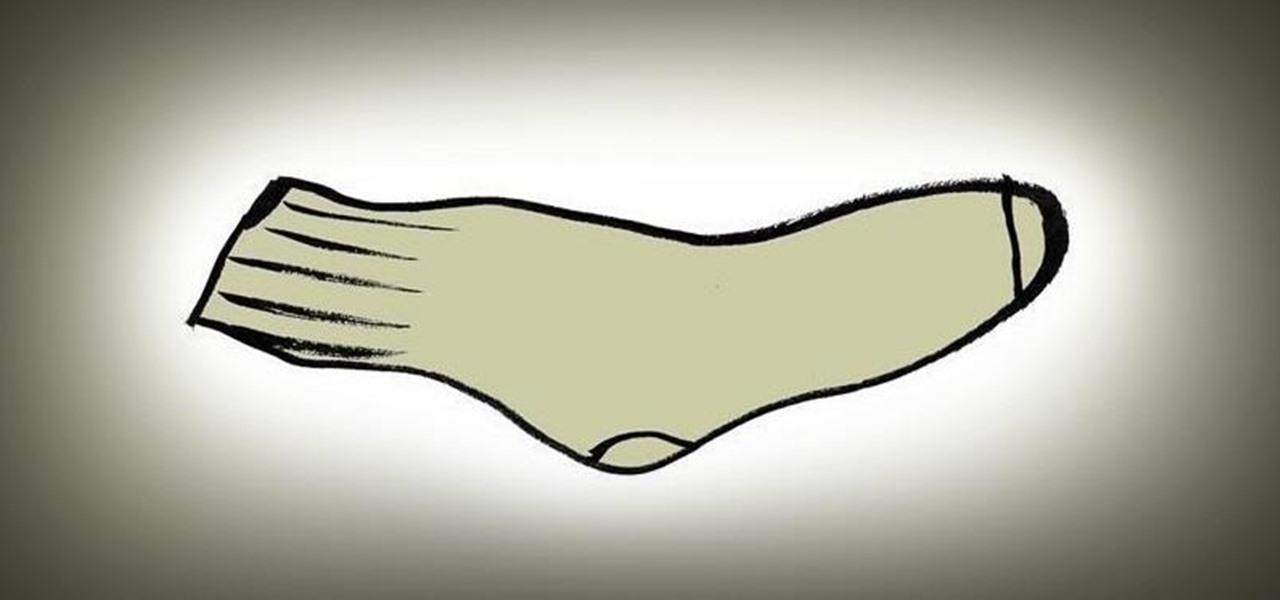
Need to give yourself a super-cheap back massage? Place a few tennis balls inside a long sock, tie the end, and place the sock on the floor. Then, lie down and roll your back against the sock to relieve your sore back muscles.

Looking for the best way to to pay or transfer money for your overseas property can be difficult. Should I make a money transfer with my bank or a broker? And many other questions that we ask ourselves.

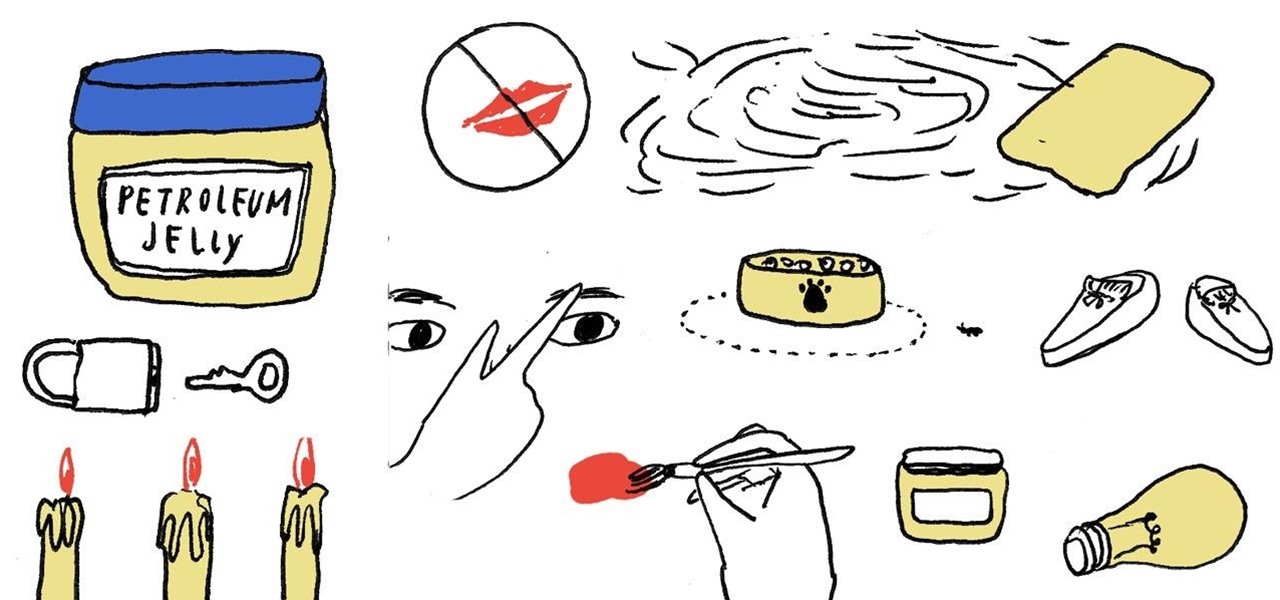
In 1859, 22-year-old chemist Robert A. Chesebrough accidentally discovered petroleum jelly when he visited a working oil well in Titusville, Pennsylvania. Oil workers complained of a gooey substance referred to as "rod wax" which kept getting into the machinery and slowing them down. Chesebrough noticed that oil workers also smeared this same substance on their burn marks or dry skin to help speed the healing process.

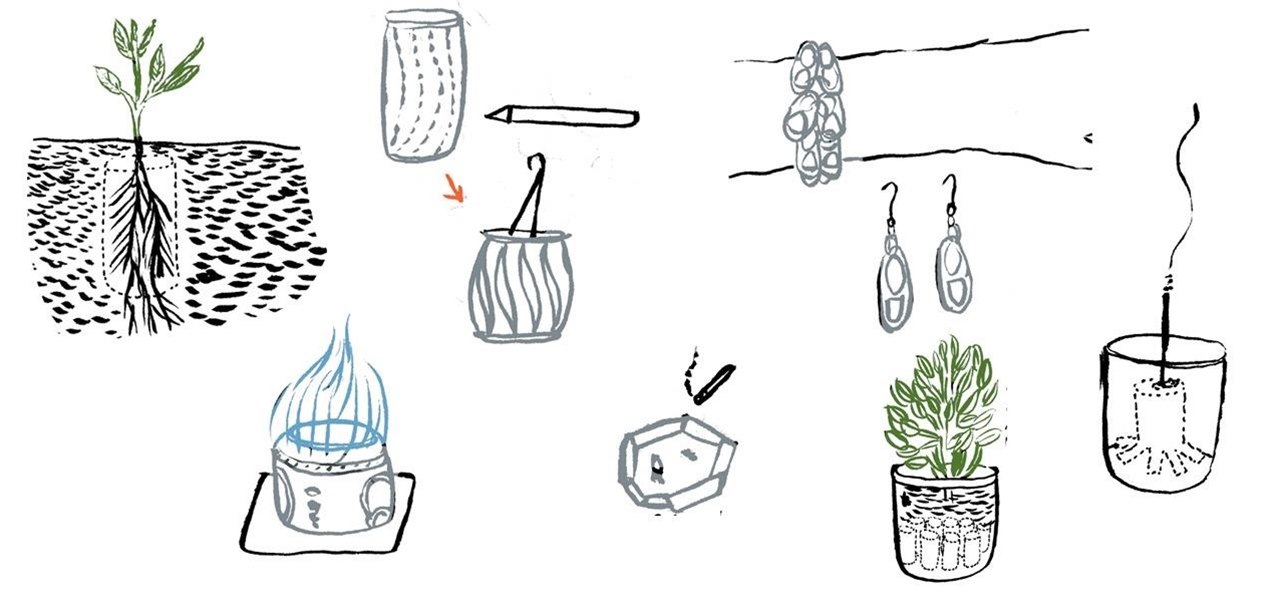
Other than providing a convenient vessel for your carbonated beverages so that they don't go completely flat, aluminum soda cans are also quite useful for a number of other things once they're completely empty.

Direct current (DC) by definition flows in one direction. Alternating current (AC), on the other hand, periodically changes direction, or reverses polarity. It is indeed possible for a portion of a circuit that is normally DC to periodically change direction, or reverse polarity like an AC circuit.

Other than serving as the raw ingredients for your epic spaghetti and meatball feast, uncooked spaghetti noodles can also be used to make a DIY knife block for your kitchen knives, light a candle with a deep holder, check the done-ness of your baked goods, and double as a DIY toothpick or skewer you can break into your desired length for cooking or serving.

The annoying thing about pantyhose? They snag and tear very easily. The amazing thing about pantyhose? They have about a gazillion practical uses even if you can no longer wear them.

Erik at Not-Me.org is a rare spirit. He's committed to helping people protect themselves. His non-profit studio in Massachusetts focuses on training at-risk individuals in self-defense.

Nothing on the web is ever private. If you thought you can control your privacy, you were wrong. Websites may give you security options to better hide your information from the world, but ultimately your privacy resides in the hands of the website itself. We've seen how websites let ad companies track our private usage. We've seen how Facebook mucked up their privacy controls. We even saw how websites like Gawker are prone to hackers stealing user information. And now, Etsy has made what was ...

Does your network begin to crawl right around the time your sinister-looking next-door neighbors get home from work? Do you harbor suspicions that one or more of them may be stealing your Wi-Fi? It's easy to find out. And equally easy to give freeloaders the boot. In the guide below, we'll show you how to secure your wireless connection in three easy steps.

There are many different formulations of foundation on the market. Here we show you how to pick the right foundation for your skin type. Why?

Rich pigmented lips are in right now, but not always an appropriate look. In this video, we show you how to use just one lipstick four different ways. Lip Stain

A natural makeup look really brings out the most beauty. Follow these steps for an easy, breezy, natural makeup look. Foundation

Industrial espionage, social engineering and no-tech hacking are all very real and there are simple precautions that you can take to protect yourself, which this article will discuss. Whether you are a high-profile businessman or a housewife (or husband), keeping information you want to keep private, private, should be important to you.

If you're a frequenter of Null Byte, I bet you have at least some interest in information security. Furthermore, you have a hobby that if applied in certain ways, will get you arrested. I've received quite a few messages from the community here about federal cybercrime law and how it applies to them, so I decided to get together with my lawyer to come up with some answers.

I'm not sure exactly when it happened, but it's awesome that you can now download music from the iTunes Store that's free of DRM (digital rights management) limitations. That was always my biggest problem with buying music from iTunes. Paying a buck for a song that I can only play on Apple devices? Really? That's what finally led me away to other legal music downloading services like eMusic and Amazon.

This is Null Byte's fourth part in a series about fully securing our computers (Part 1, Part 2, Part 3). In our last Null Byte, we went over how to encrypt an entire operating system to protect our data, however, this doesn't fully protect us. In the case of legal extortion, the government can actually make you give up your cryptographic key to your computer so that they can look through it.

Password strength and encryption are important things when it comes to computers. A password is the entire security of your computer, and OS passwords are not hard to break. Most users believe that if you have a password on your computer via the OS, that you are safe. This is not true at all, sadly.

Permanently deleting files is something that a lot of people aren't aware of. Actually, most people think that once a file is deleted, it is gone forever. This is not the case. Hard drives write to the disk via magnetic charges, positive and negative correlate to 1s and 0s for binary. This is then interpreted into information for the computer to use and access.

The internet is a scary place, and if you're like me, you don't want anyone tracking you or learning your search habits. It's a blatant invasion of privacy for companies to do this, but at least we have methods of fighting back—one of which is Tor.

Like the recent XSS 0day exploit found in the Mac and Windows versions of Skype, a similar one has been found in the Skype app for iPhone. The vulnerability allows an attacker to send a message that contains malicious JavaScript code in the "Name" parameter. This code can steal your phonebook, crash the app, and potentially do a lot worse. The URI scheme is improperly identified for the web-kit browser. Instead of going to a blank browser page, it defaults to "file://". The code could steal a...

If you're interested in bypassing Windows and Linux passwords, there is a great tool from the good people at Kryptoslogic. Have you ever forgotten your administrator password? Have you ever bought a used computer with a password on it? Well, Kryptoslogic have created a boot-disc call 'Kon-Boot', which allows you to bypass any Windows 32 or 64 bit OS, as well as Linux passwords. There is both a paid and freeware version available.

It's been a great year for video games, kind of. Sure, the AAA release lineup has been a trainwreck and hacking has been a bigger problem than ever. But two things have happened involving the federal government that have made video games more legitimate in the United States than ever before. The Supreme Court ruling establishing that video games were the equivalent of movies and books, not porn, was the more significant decision. But in May, the National Endowment for the Arts made another si...

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.