There are so many hackers around these days, and they are becoming very smart. So smart that they have successfully taken down many government websites. The most recent attack was on the Department of Justice (DOJ). To read about the history of these hackers, check out Wikipedia.

I'm starting a laminate tile installation next Thursday. I thought I will show what is involved from start to finish. It's going in a kitchen and two bathrooms. There is ceramic tile in these rooms now and I'm installing the laminate tile right over the ceramic tile. The problem with the ceramic tile is it has white grout and my client can't keep the grout clean.

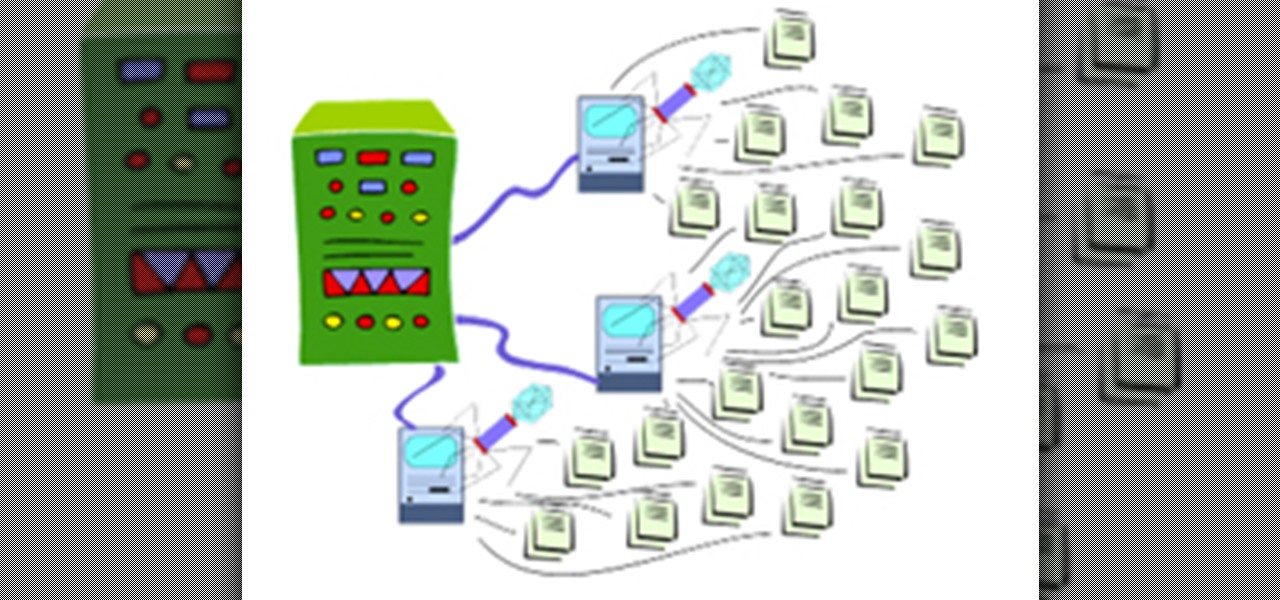
Anonymity is something that doesn't exist today. Everything you do in the world is tracked, from the purchases you make to surfing the internet—even taking pictures on your iPhone. Everything you have ever said and done on the internet is still there—somewhere. This is called caching. For example, when a site is down, you can view its cached page on Google.

WonderHowTo is made up niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

SSL stands for Secure Socket Layer. It's an encryption standard used on most sites' login pages to avoid their users' passwords being packet sniffed in simple plain-text format. This keeps the users safe by having all of that traffic encrypted over an "https" connection. So, whenever you see "https://" in front of the URL in your browser, you know you're safe... or are you?

The dreaded moment you hope never happens—someone has stolen your laptop. You could have private information, pictures, or even private information belonging to the company you work for, all lost forever. It can cause you pain, money, or even a job.

Once you get past the initial quick start setup of the Canon EOS 5D Mark II, capturing pictures in auto mode is a breeze. But what do you do after you've snapped those photos? This quick guide will show you the easy steps to viewing your images directly on the camera.

Minecraft was first released just a few years ago, but when a paradigm-shifting piece of media comes along the rest of the world is quick to take inspiration from it. The absolutely terrible XBLA knock-off FortressCraft was the first, and last month a much more interesting game called Terraria came out on Steam for $9.99. It is clearly inspired by Minecraft, and there is a long checklist of identical features. It is, nonetheless, a very different product, and just might be called the first in...

There’s no point to playing all of the different tower defense games available today. Most adhere to the original formula, so playing 2 or 3 really good ones (like those mentioned in my previous post) would be more efficient.

Yes. That's right. The 2010 National SCRABBLE Championship (NSC) is almost here. In fact, it starts in less than 2 weeks! And if you were lucky enough to register for the competitions, you could win a first place prize of $10,000!
DRUM! Magazine — the leading magazine for drummers and percussionists worldwide — has announced the biggest drumming event ever to take place in Northern California. On Friday, August 13, drummers will descend on the San Jose Repertory Theatre in the heart of Silicon Valley to witness three of the world’s most exciting drummers — extreme drumming sensation Marco Minnemann, Tower Of Power funk master David Garibaldi, and former Mars Volta wunderkind Thomas Pridgen — for an evening of mind-blow...

I've been curious to watch one of these famed '3D' games for a while now. Last April at NAB, I attended several 3D panels and folks from ESPN suggested that one of the strongest experiences that would bring 3D into the home would be live sports. I've missed opportunities to watch the PGA Masters broacasts, and NCAA games, but being a hardcore Soccer (Futbol) fan, I've been most excited about this possibility. It did not disappoint, but not without some concessions. I will be as detailed as po...

Update: New Trailer (7/9/10) In July of 2008, Fawaz Al-Matrouk, director of "To Rest In Peace", brought me on to shoot his USC graduate thesis film. Two years, 3 cameras, and over 15,000 miles later, the film is in its last week of post, having completed our final color correction at Light Iron Digital in Culver City yesterday.

Roses, the world’s favorite flowers, are great garden performers that, if well cared for, will live for many years and produce thousands of exquisite blooms.

Many cooks refer to well-seasoned cast iron skillets as the original non-stick pan. A cast iron skillet is a versatile piece of cookware, going from the top of the stove to the oven with ease, provided the handle is also cast iron. The secret to a non-stick skillet is in the seasoning and cleaning process. Improper seasoning, cooking acidic foods and incorrect cleaning methods can all remove the non-stick capabilities. Achieving and maintaining a non-stick cooking surface is uncomplicated and...

It seems like nowadays, whenever Facebook rolls out a new feature, it's immediately controversial. Social Ads put your name and face in the spotlight, Instant Personalization shared your information with partner sites, third-party apps were allowed to access your home address and phone number, and now Tag Suggestions implement facial recognition software to automatically identify your friends in uploaded photos. Most are calling it problematic or creepy, some insinuate CIA involvement, and it...

For lazy children, winter snow means snowball fights, snowmen and snow days. For lazy homeowners, it can mean leaky roofs and costly repairs. Fortunately, where snowy roofs are concerned, a little bit of preventative maintenance can go a long way.

As many of you know Windows is not the most secure Operating System in the world, but then again no OS is really secure if the user doesn't know how to protect themselves. Later I will show you how to lower the risk even more on your (the user's) end.

In many ways, we center a large portion of our lives around festivals. They provide us days off from work, allow us time to be content with our families and loved ones, and a give us a chance to eat as much as we want without Aunt Carol saying something about our necks (it's thyroidal, Carol). However, some festivals are determined to push the needle to crazy. Here, for your consideration, are those offenders.

Google is great. They provide us with tons of free services and open source APIs that we can code fun tools for, one of which I don't think gets enough credit: Google Voice.

We love tearing apart security here at Null Byte. Several years back, upon returning items to Wal-Mart due to a malfunction, I noticed something very peculiar about the way their overall procedure goes. I brought the item up to the desk, and the woman asked if it didn't work, which I responded affirmatively. Without a moment's notice, she takes it right off to the defective items area and asks if I would like cash or store credit.

Scrabble Bingo of the Day: * FINNESKO [n/pl.] A finnesko is a boot made of tanned reindeer skin, with the reindeer's fur on the outside. It's an especially good, warm boot for subarctic regions. These boots originate from the Sami, indigenous people from the cultural region of Sápmi, located across four countries in the Arctic Circle; Norway, Sweden, Finland, and Russia. This area is also referred to as Fennoscandia.

Null Byte is looking for moderators. More threats to computers exist every day. Not only do we have computer viruses and malware, but we have rootkits and other nasty pieces of code that can log your keyboard strokes or even add your computer to a botnet to attack other websites. Your computer can be infected even if you have anti-virus software installed. I can't stress enough how easy it is for a hacker to write a piece of code that gets around every piece of anti-virus software.

Most of the car owners pay attention to the maintenance of the vehicle but among them, many forget to include windscreen maintenance in their periodic checkups. Car windscreen maintenance is quite simple and can be done on your own. In order to maintain car,the drivers should treat this with utmost care as they do for tyres because neglecting small issues in windscreen can land you in deep trouble and on safety prospects as well,it is unsafe.

Here at Null Byte, we've spoken a lot about securing and anonymizing traffic. This is a big deal. With all of today's business taking place electronically via computers, we need to be secure when on-the-go. A lot of businesses don't even train their employees to secure their computers to protect from various threats. Here are a few things that should always happen when doing business on computers:

HEXEREI n pl. -S witchcraft 67 points (17 points without the bingo)

1/3 of the city gone, the red colored buildings and homes are the ones that got destructed in the fire..

Got a knack for speeding? Like running red lights? Believe or not, the police have better things to be doing than pulling you over, like catching real criminals. That's why more and more cameras are popping up at known speeding zones and on street corners—so the cops can clean up the streets, compared to just ticketing them.

After getting slammed with a crazy-big earthquake/tsunami, the Japanese nuclear plant Fukushima Daiichi might be on the brink of meltdown. Not as bad as Chernobyl, but maybe as bad as Three Mile Island. Nobody wishes such a disaster on anyone...anywhere in the world. In the US, there are about 100 nuclear facilities, about 8 of which are located near hot beds of seismic activity.

Immigration is a serious political issue in the United States, and those who oppose or support stricter immigration laws are often outspoken and candid about their beliefs, imposing their will on future legislation to not only politicians, but the general public—the voters. And what's the best way to reach the public? Entertainment.

If you tried visiting the Apple Store online this morning, you were probably prompted with the same notice as the one below, which lasted a good portion of the a.m. What could Apple have been doing to shut down their online store for so long?

I'm not going to lie. I was Catholic. But one of my reasons for my faithful departure was having to tell my innermost secrets— my sins— to a silhouetted figure behind a latticed screen. With the creepy enclosed booth structure and separation of sinner and confessor, its anonymity was clear, yet deceiving. You always knew the priest and he always knew you. If I wanted total privacy, was there really a need for this intermediary to God?

When I used to play Magic every day during 7th grade, one of my regular opponents was a kid named Eddie. He played an all-Blue, deck, the first I'd ever seen. At that point I was even more creature-obsessed than I am now and my deck were unwieldy hulks practically begging to be shamed by an all-Blue deck. I couldn't hurt him. Every time I tried to do something he had a response, a way to negate what I was doing. He would barely ever hurt me. He would win games just by making me play for so lo...
Windows Live SkyDrive which is initially termed as Windows live folders is one of the parts of Microsoft Windows online service. It is a password protected service that allow users to store file and share them with others. Here the windows live id is required to access the users profile. Anyone can make his/her files private or public. Public share file are easy to access without requiring any Windows live id.Initially it was available only few states in United States. But nowadays it expande...

Lifehacker posts an article on the art of cracking weak passwords, courtesy of Internet standards expert, CEO of web company iFusion Labs, and blogger John Pozadzides. Pozadzides certainly knows a thing or two about password logic. (Note: this information is not intended to hack into accounts, but rather to protect you from using weak passwords).

The Motorola XOOM was just released last week to Android-hungry fans waiting the next best thing to Apple's iPad. But should it have been released, considering Verizon's switching to the 4G LTE network soon?

Remember KODACHROME? That color reversal film from Kodak? The film that was the inspiration for Paul Simon? The only brand of film to have a state park named after it?

Get that salon blowout feeling at home! Follow these tips for a perfect at home blowout. Shampoo & Condition

In this video Robert Ashforth shows you how to curl hair with tongs. Product such as spray net protects hair and encourages curl. Wrap hair from top to bottom. Open your tongs and without closing them wrap the hair around from root to tip along the length of the tongs. Let the hair cool. After the hair has been curled around the tongs slide them out and hold the curl to allow hair to cool and set.

WikiLeaks. In recent weeks, it's been the hottest topic on the web. It's been attacked on a multinational level by political influence peddling.