Good skin care begins with knowing what kind of skin your have, what special issues you have, and what products work best for your skin. In this video we show you how to identify your skin type and choose skin care products that best suit you. Skin Care Routine

Purple eye makeup is a great, fresh look for weddings and springtime. We'll give you some ideas in this video on how to wear this daring look. Apply Moisturizer

Hello to all my readers, this is Kalsoom Nafasat. You all will be amazed to know that you can create some great nail art using needles. Although toothpicks are used more commonly in nail art, needles can be used for the tiniest of details. A needle is the best tool for creating sketches or painting faces on your fingernails. Isn't that amazing?

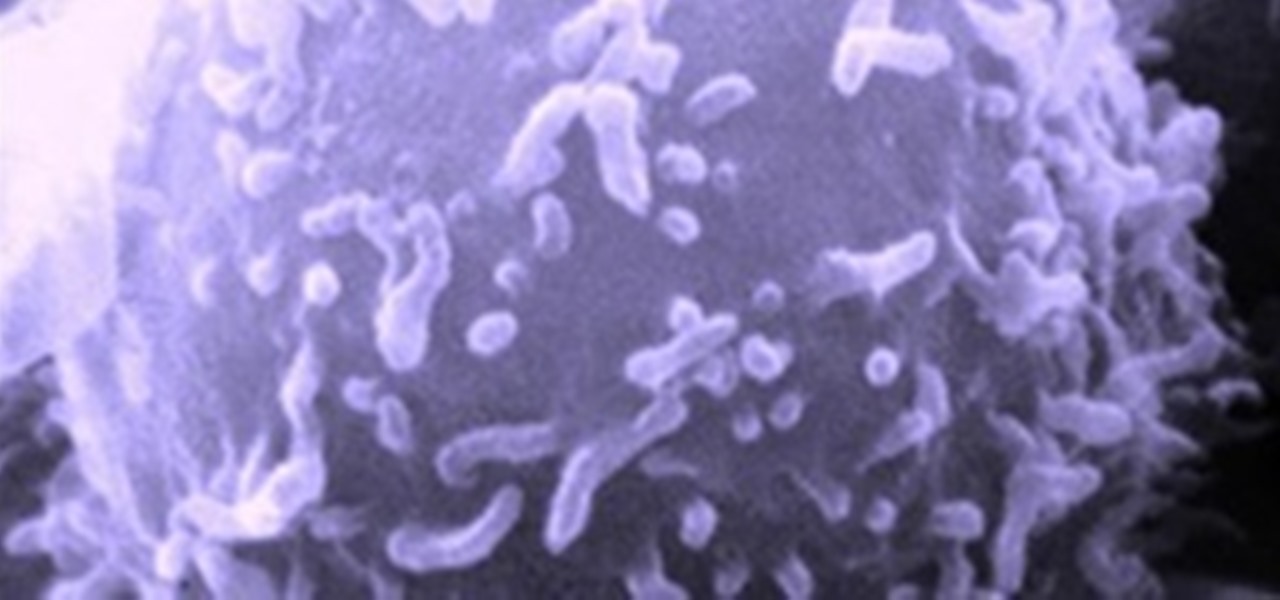
The immune system is not as simple as you might think. Simply, it's formed of two main groups of cells:

It's somewhat funny that the HTC ThunderBolt smartphone would be released around the same time as Apple's new Thunderbolt technology. Mainly because HTC's smartphone isn't exactly something I would compare to a flash of lightning, which averages around 60,000 miles per second. But Apple's new interconnect surely deserves the Thunderbolt designation.

Back in the eighties, I used to hate television commercials, but I eventually got used to them. Had to, in order to enjoy my favorite shows. Then, the increasing number of billboard ads annoyed me in the nineties. They followed me everywhere I went—no escape—persuading me to buy the newest whatever. It seemed like Big Brotherism—like They Live. But, I got used to it. When I finally entered the digital age and became a web addict, I was peeved at the constant sight of online ads everywhere I v...

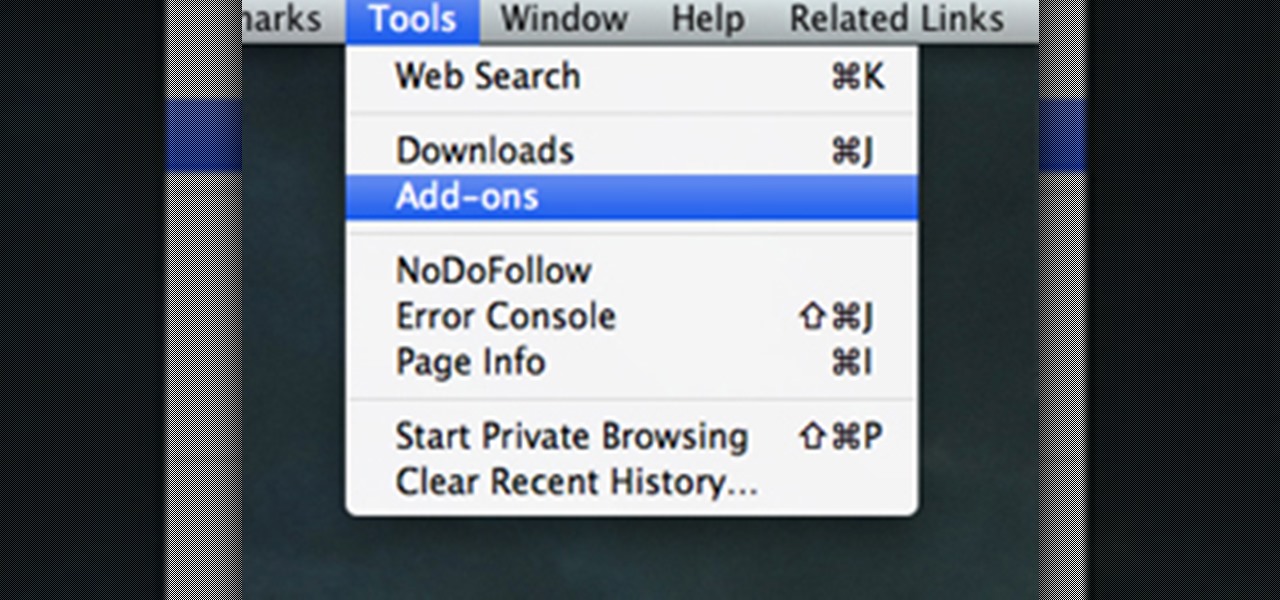
There's a whole lot of brouhaha going on right now about the hidden plug-ins being installed unknowingly in the Mozilla Firefox web browser, with companies like Apple, Microsoft and even Google being named top offenders.

So You're New to Counter Strike Source? So you're new to Counter Strike Source and you want to improve your gameplay? Great. You've come to the right place.

You've had a massive hard disk failure.. ...in your PC or laptop and like a large number of people who think it will never happen to them...you did not have a backup of those 2000+ family pictures, those hundred of important Word documents, those family videos that you downloaded from the camera then erased from the cameras disk...the inevitable "I'm Screwed!'

Professionally and academically speaking, I am a computer scientist, but I also enjoy lock picking as a hobby, so I thought I would share what knowledge I have with this. Before we start doing anything, first we need to understand the fundamentals of how locks work and then acquire and familiarize ourselves with basic lock-picking tools.

So, you scratched up your $500 Adobe CD and now it's unreadable. You could go buy a new one, but you already purchased it! Searching The Pirate Bay and downloading some Adobe software can usually be easy enough, but what should you watch out for?

We've talked about the deep web before, but we never really covered the details of what's out there. It occurred to me that a nice list of resources would be very helpful to all of you anons out there. Think of this like a helpful brochure to the hidden web.

Dreams are like an internal human holodeck. Inside your mind, anything is possible, from your grandest wishes to your worst nightmares. This is all well and good, but what if you could control your dreams and become the omniscient god of a handpicked reality whenever you go to sleep? Inception took this idea to the logical extreme by invading other people's dreams.

It turns out that the popularity of soft circuit electronics has leaked out of the interwebs and into the hands of the U.S. military. Soft circuit electronics allow you to literally sew electronics circuits into fabric using flexible conductive thread instead of wire. Soft circuits can be used for all sorts of fun projects, like the TV-B-Gone Hoodie and the Heartbeat Headband.

Holy hell have you believers just been PWND! Seriously, you have. Why, you say? Well haven't you heard the news? Of course not, I'm pretty sure you don't, since you believe in KONY 2012. Oh yeah. Let me hold on to the suspense for just a minute.

Wireless networks. Nowadays, everyone uses 'em, but most don't secure 'em. On average, I can drive up and down any block in my city and find at least one or two open or semi-open networks on any given day. With some changed MAC addresses for good measure, an attacker can use your network as a spring board for who knows what. When the police come a few days after, they are coming to your door—and not to talk about how nice your lawn is. Don't be that guy.

The most recent viral video on YouTube is just that. A viral video. After seeing all the hype and 'support' that the 'movement' is getting, I want to tell you that this is a misleading video and somewhat of a propaganda campaign. These are strong accusations against such a 'humanitarian' cause, but I'm here to show you why.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

For a moment, picture a situation where you want to host some files or images, but you do not want it traced back to you. Perhaps you're working on a project with others and need secure data storage. Anonymity is the new shield of the 21st century—and you best protect yourself. As always here at Null Byte, we are trying to make that happen. Before someone can learn how to root a box, they need to learn how not to be found. I can not stress that point enough.

As you progress in the world of information security, you'll find yourself in situations where data protection is paramount. No doubt you will have files to hide and secrets to share, so I'm going to show you how to use the GNU Privacy Guard (GnuPG or GPG for short) to encrypt and decrypt as you need. GPG is a great open-source version of Pretty Good Privacy (PGP), a similar application used for encryption, but licensing and patent problems led to the development of GPG in its wake.

The immune system is not as simple as you might think. Simply, it's formed of two main groups of cells:

In this article, I'll show you how to create a simple yet effective way of scaring off intruders. Of course, there are methods around this approach, but it's great for office pranks and general fun. The project requires a little background knowledge in electronics and circuitry, like reading schematics and using a soldering iron.
Does this video prove that otherworldly intelligent life has visited Earth? No. It does not prove anything other than there are designs ‘etched’ onto the surface of a field. Does the video immediately above prove that otherworldly intelligent life hasn’t visited Earth? Yeah, you saw it coming; no, it proves nothing more than humans are able to ‘etch’ designs in a field of grain.

Hello and welcome to another InfoSecurity World tutorial. The intent of this article is to teach one how to encrypt sensitive files. When set up correctly with a strong password, it would be almost impossible to hack. Even the FBI have had issues decrypting this software. I'm here to teach you how to create a general encrypted container—not the complex hidden TrueCrypt volume.

Previously, we talked about how to secure Firefox. Today, we will talk about securing a Chromium based Browser. Why? Because Chrome recently beat Firefox in holding more customers.

It's once again Monday, which means it's time to highlight some of the most recent community submissions posted to the Math Craft corkboard. Since two of these posts were on polyhedral versions of M.C. Escher's tessellations, I thought we'd take a look at building a simple tessellated cube based off of imitations of his imagery.

Formerly ipchains, iptables is a script-based firewall that's included with both Mac and Linux operating systems. In my opinion, it's the best firewall in existence. The only downfall is that it's complicated for some people to use due to its script-based nature. But this should be disregarded, as firewalls are nearly the entire security of your computer.

Last week's round up was all about third party services that sprang up to fill any Google+ voids. This week, I'll let you know how to keep up with the latest Google+ updates, and give you some great tips for interacting with your followers.

Antimatter15, author of the popular Surplus Chrome extension, was suspended from Google+ for using a pseudonym instead of a name that fits Google's community standards. As such, he's no longer supporting the extension, and if you're using it, now might be a good time to find a replacement. It's a reminder that nothing on the web is guaranteed to work forever. Luckily, there's no shortage of innovative coders whipping up creative and useful Google Chrome extensions.

So, you just bought Photoshop. It's time to familiarize yourself with the rudimentary tools. Let's start at the very beginning!

Founded by Zach Kaplan, a "serial entrepreneur" with a B.S. in mechanical engineering, Inventables is a futuristic online hardware store based out of Chicago. The company sells innovative materials at much smaller quantities than typically available—largely to artists, inventors, developers, and researchers. If you've got a brilliant idea and cash to spare, careful, you just may go hog wild. My premature "Dear Santa" wishlist-in-progress:

Remember what life was like before your iPhone? Before there were palm-sized smartphones with seemingly endless features, there were phones like Motorola's RAZR that peaked with its embedded camera. Before that, there were simple flip phones with texting capabilities, bulky two-pound Gordon Gekkos—even briefcase phones.

The widely used expression "free as a bird" intimates an enviable existence: delicate, yet mighty wings transporting to destinations no human could so breezily venture. But despite their fanciful, superhero ability, in truth, the avian race leads one of the most difficult existences in the animal kingdom. Yes, birds have existed for eons—they likely evolved from small dinosaurs of the Jurassic period—but for these creatures, life can be ruthless.

China is a hot mess of traffic and is stereotyped for spawning some of the craziest drivers in the world. The traffic jams are known to be so bad, drivers have been gridlocked for 9 straight days.

THE FOLLOWING IS ONLY FOR YOUR ALIENWARE WARTIME THE BELOW SETTINGS ARE FOR YOUR ALIENWARE WARTIME EDITION DESKTOP PC, THAT HAS THE CORE I7/X58 MOBO AND DDR3 TRIPLE CHANNEL MEMORY INSTALLED;

Hello, everyone. My friend and I recently released a Defense of the Ancients (DotA) map that went viral and thought I should share it with Minecraft World on WonderHowTo since you guys helped me out when I first started making videos! We were featured on Kotaku, RockPaperShotgun, Gamespy, The Verge, Joystiq and many more websites!Exciting!You can see the full details below are head straight here for the downloads.

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

Injection is an attack vector that involves breaking out of a data context and switching into a programming context through the use of special characters. These characters are significant to the interpreter being used, but not needed for the general user input being asked for.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

You want to put out a live web server, but you don't want to be owned in the process. An expert eye for security is not needed if you take a few basic steps in locking down the hatches. Most successful attacks today are not the complex, time-consuming tasks you might think, but simple lapses in policy that a hacker can take advantage of to compromise your server.