Watch this video fromt the Concrete Network to learn proper function and use of the vibratory plate compactor tool for preparing the concrete subgrade before placing the concrete. This is done to provide a stable foundation for the new slab as well as provide drainage.

An overhead projector can easily be used to transfer high-end graphics onto a concrete floor in preparation for saw cutting or coloring. Watch this video from the Concrete Network to see how.

Watch this video from the Concrete Network to learn the proper function and use of the moisture test, calcium chloride test, and pH test when pouring a concrete overlay or epoxy.

Watch this video from the Concrete Network to learn the proper function and use of the mix-n-go tool, which is used to mix small amounts of concrete.

Watch this video from the Concrete Network learn how to use a Micro-Fiber mop tool to apply floor wax to concrete.

Watch this video from the Concrete Network to learn the proper function and use of the laser level or builder's leveling tools for forming a concrete slab.

Watch this video from the Concrete Network to learn the proper function and use of the hopper spray gun tool.

Watch this video from the Concrete Network to learn how to use the different types of hand floats and darbies. This video includes tips on selecting the proper trowel and an explanation as to why each concrete finishing tool is used.

Watch this video from Concrete Network to to learn the proper function and use of the gauge rake and smoothing paddle tools used for leveling concrete.

Watch this video from the Concrete Network to learn how to use the come-a-long concrete tool to push and pull concrete into place.

Watch this video from the Concrete Network to learn the proper function and use of the fresno tool.

Watch this video from the Concrete Network to learn how to use a variety of edging tools including hand, combination and walking edgers.

Watch this video from the Concrete Network to learn how to use the cut-off saw, used to cut control joints in concrete in order to prevent cracking.

Watch this video from the Concrete Network to learn the proper function and use of handheld concrete grinders and blades, used for making detailed cuts in concrete.

Watch this video from the Concrete Network to learn how to use high end decorative concrete tools, grinder and blades.

Watch this video from the Concrete Network to learn how to properly use the baracuda and shark air driven tools to engrave grahics into concrete.

During a Laneway Revitalization project some gang graffiti was encountered and replaced with vibrant art work. The event organizer is a Toronto Police Officer who volunteers for the not for profit organization-The Ontario Gang Investigators Association. In this video an explanation of gang graffiti is offered. The organization Notogangs.org is comprised of sworn members of all areas of law enforcement who network regularly in the mandate of the prevention, intervention and suppression of crim...

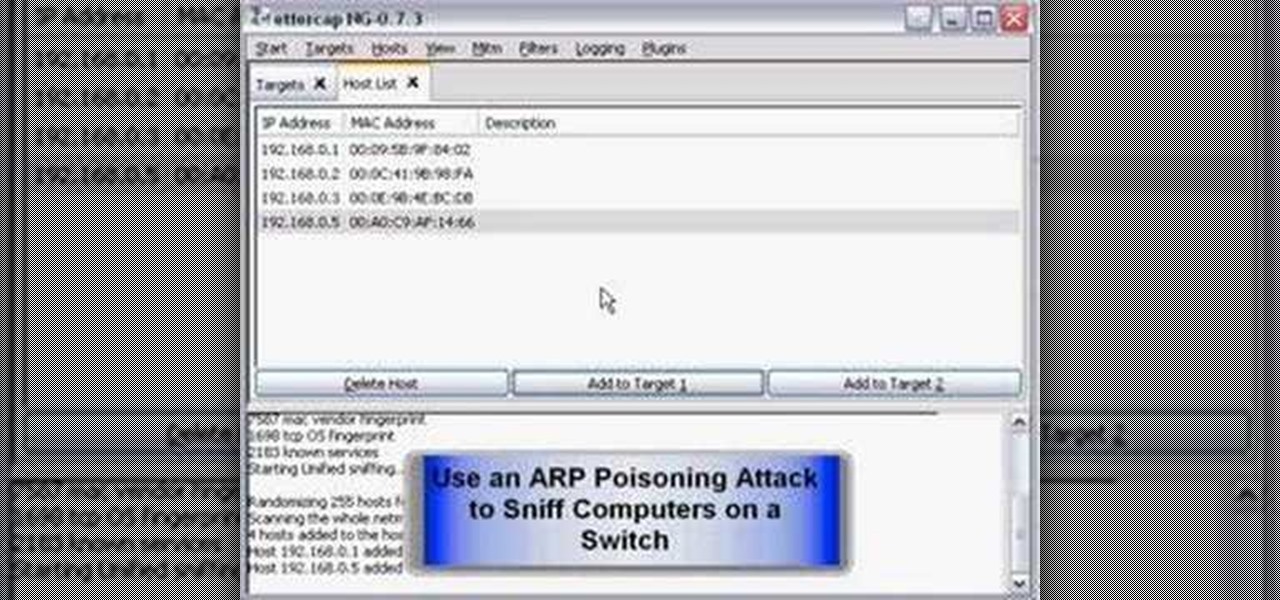
How to hack a network by sniffing passwords with Ettercap software.

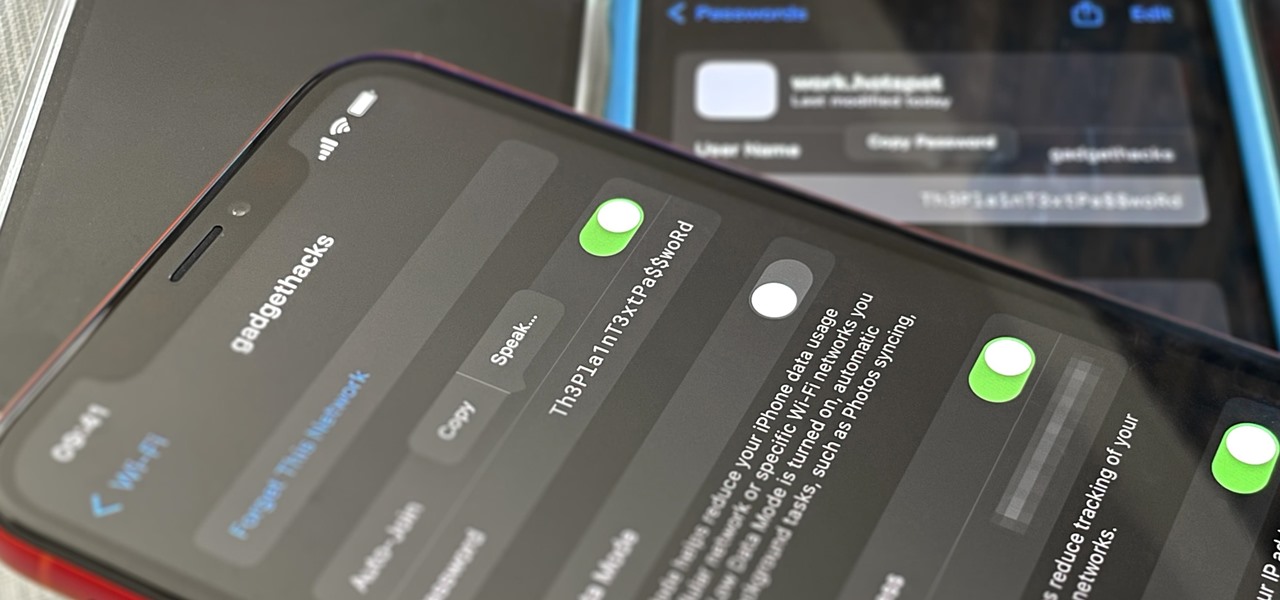
Your iPhone goes with you pretty much everywhere you go, and unless you have unlimited data on your cellular plan, you've probably connected to dozens of Wi-Fi hotspots over the years. Wi-Fi passwords are saved to your iPhone so you can auto-connect to the router or personal hotspot again, but finding the plain text password for a network hasn't always been easy.

When you don't have a steady cellular signal or immediate Wi-Fi access but need to communicate with others around you, you can set up an off-the-grid voice communications network using a Raspberry Pi and an Android app.

A virtual private network is a necessary part of your arsenal if you're insistent on surfing the web privately and securely on your iPhone. The App Store is littered with hundreds of different VPN services that encrypt traffic and mask your IP address, but what they all have in common are connectivity issues.

Can you be too lazy for video games? That's how I feel sometimes. I want to play the latest PlayStation has to offer, but I can't be bothered to get out of bed. As if Sony read the minds of lethargic gamers everywhere, the company has released an amazing thing — PS4 Remote Play allows you to play your PS4 on your iPhone, no TV required. The best part? It's 100% free.

Google's next-gen cellular carrier, Google Fi, which replaces Project Fi, is making waves across the mobile industry. With super-cheap plans starting at only $20 and the ability to connect to millions of Wi-Fi hotspots across the globe, it's tempting many users to make the switch from AT&T, Sprint, T-Mobile, and Verizon Wireless.

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.

I've seen my fair share of heartbreaks when it comes to used phones. As a repair tech, I often had to try and help out customers who bought used handsets which turned out to be useless, either because it was stolen or not working on their carrier's network. More often than not, there was very little I could do. To help you from being stuck in the same situation, here are some tips to prevent you from getting scammed out of your hard earned money when buying a used handset.

Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elliot asked him for some info that were really useful to gain access to his account, the target believed to be someone from the bank and gave him the info Elliot was looking for. But How Is It in the Real World?

If you haven't read the last article, feel free to stop by and give it a read, but abstaining from reading it will not, for the most part, be detrimental to your understanding.

Hi there again, aspiring hackers (and veterans as well)! I'm going to explain how to perform a dictionary attack on a WPA/WPA2 protected network with Wifite. Please note that this doesn't work with WPA Enterprise For that end, you'd have to use an Evil Twin to get the "Enterprise" auth attempt, and then crack it.

Remember the feeling you had the moment you removed your shiny new Nexus device from its packaging and booted it up for the first time? You swiped through the app drawer at lightning speed and thought to yourself, "This is the last Android phone I will ever need, they just aren't going to get any better than this."

Welcome back, my neophyte hackers! Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes you hear strange sounds coming from his home? You know he's up to no good, but you aren't sure what it is exactly.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

For the most part, transferring files from your computer to your Nexus 7 (and vice versa) is a simple process. Just hook up your tablet to your computer with the USB cable and transfer. However, most of the time you'll need additional software on your computer to do this, and then, of course, you need the USB cable.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

In this short video tutorial, you will learn an easy technique on how to draw Chowder from the Cartoon Network series of the same name. For the full tutorial with step-by-step and speed control, visit SketchHeroes.

Learn how to draw Ben 10 from the famous Cartoon Network animated franchise. For the full tutorial with step-by-step drawing instructions and speed control, visit Sketch Heroes.

Welcome back, my fledgling hackers! In the first part of my series on Wi-Fi hacking, we discussed the basic terms and technologies associated with Wi-Fi. Now that you have a firm grip on what Wi-Fi is exactly and how it works, we can start diving into more advance topics on how to hack Wi-Fi.

When this problem occurs most Windows users feel desperate because it can happen' at any point, every 10 seconds, minutes, hours - you name it and they don't know how to solve it.

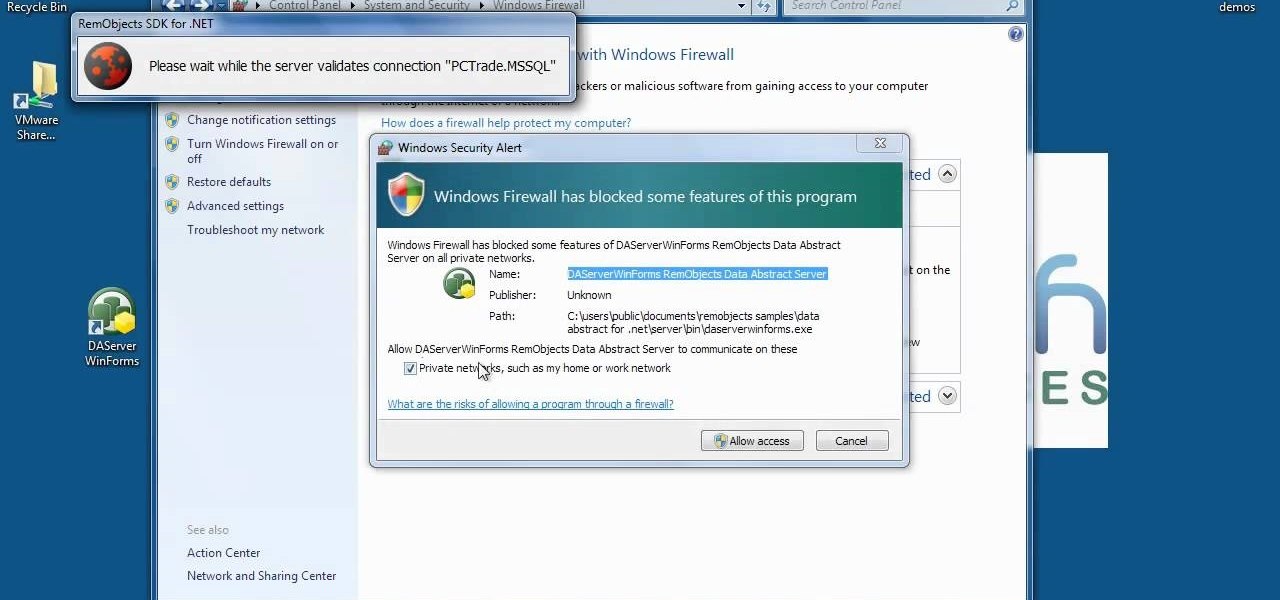
Firewall is necessary to protect a computer network from hostile intrusions. You can easily setup your Firewall setting. This video helps you to do it.

Welcome back, my fellow hackerians! Today we'll be hacking Facebook profiles on your local network. You may think, "How is this useful, nobody but me is using my network." Well, you can use this on other Wi-Fi networks that are available for free (like at Starbucks) and crack their precious Facebook profile!

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.