With CES in full swing, it seemed like Magic Leap would have little to announce at the major tech event, but it turns out that one of its partners has weighed in with a rather substantial update regarding the company.

Election Day is like the Super Bowl for network and cable TV news, so ABC News is breaking out the big guns with a new augmented reality experience to win over eyeballs of viewers.

The last time The Weather Channel showed off its broadcast augmented reality, the internet couldn't stop talking about how immersive the presentation looked, despite being shown on a 2D display.

If you've upgraded your phone to Android 9.0 Pie, you might notice some intermittent problems with your internet connection. That's because "Turn On Wi-Fi Automatically," while available with Android Oreo on select phones, is now enabled by default on all phones running Android Pie. If your Essential or OnePlus device is acting up, you'll want to check this out.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

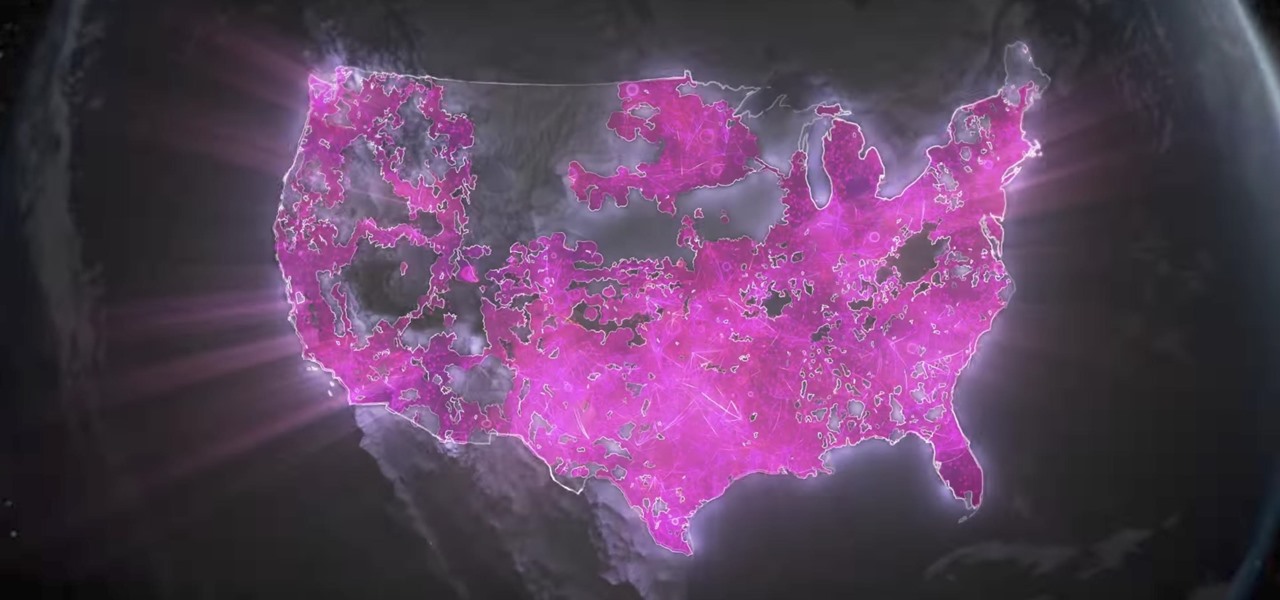
Another massive piece of the mysterious augmented reality puzzle known as Magic Leap fell into place on Wednesday as AT&T announced that it will be the exclusive launch carrier for the device.

When you can't reach your iPhone or don't have it on you, how do you get help from emergency services? Unless you have one of those life-alert mobile triggers, someone nearby, or some amazing telepathy skills, hope might be the only answer — unless you wear an Apple Watch, that is.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

Space might be the final frontier, but NASA is making a detour into augmented reality first. The Spacecraft AR app, developed by NASA's Jet Propulsion Laboratory (JPL) in collaboration with Google, debuted exclusively for Android this week (an iOS version is also in the works).

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

With Virtual Network Computing, you don't need to carry a spare keyboard, mouse, or monitor to use your headless computer's full graphical user interface (GUI). Instead, you can connect remotely to it through any available computer or smartphone.

Live theater doesn't typically benefit from the kind of computer-generated special effects that big-budget Hollywood blockbusters deploy, but that could change soon thanks to Microsoft's HoloLens.

Virtual private networks, or VPNs, are popular for helping you stay anonymous online by changing your IP address, encrypting traffic, and hiding your location. However, common IoT devices, media players, and smart TVs are hard to connect to a VPN, but we have a solution: Turn a Raspberry Pi into a router running through PIA VPN, which will ensure every connected device gets the VPN treatment.

Recently, I ran across SecGen, a project which allows a user to create random vulnerable machines. I absolutely love vulnerable machines, since a vulnerable VM is a safe and legal way to practice hacking tactics, test out new tools, and exercise your puzzle-solving skills.

A remote administration tool, or RAT, is a piece of software used for remotely controlling machines. They are commonly used by tech support to gain remote access for troubleshooting purposes, but RATs are also an important part of a hacker's advanced persistent threat (APT) toolkit. Unlike standard administration RATs, these tools are designed to be delivered stealthily and operate undetected.

A Norwegian carrier's launch of a pilotless container ship next year could lead the way to a new era in sea transportation and shipping if successful.

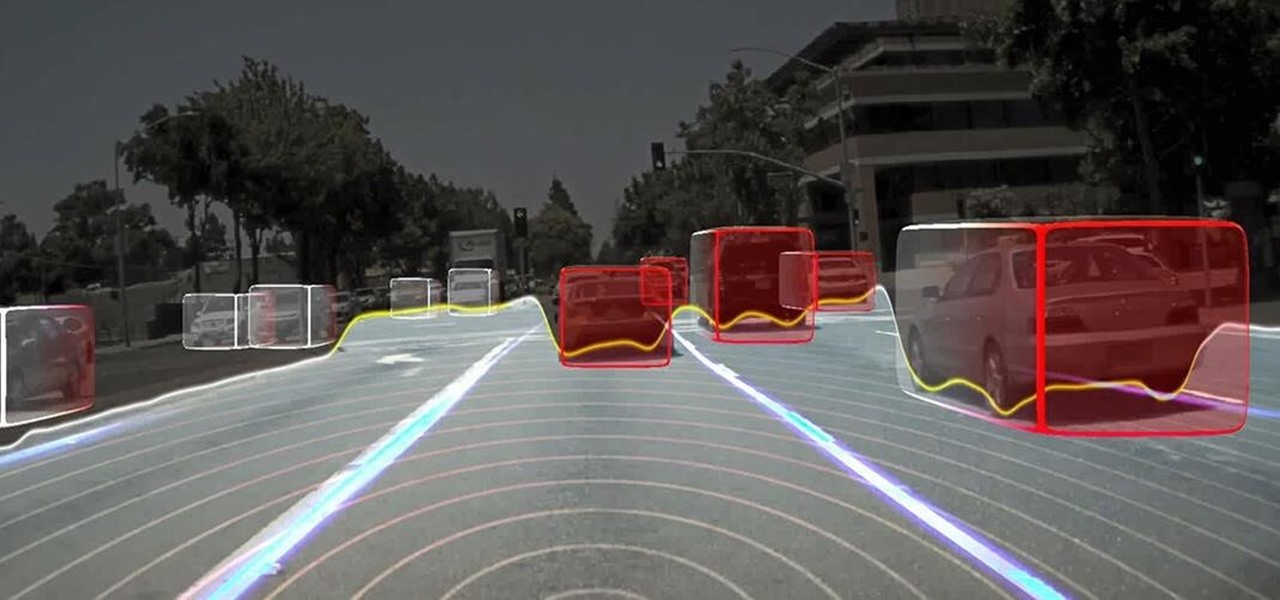
Long before Nvidia figured out how to embed neural networks in its graphics processor units (GPUs) for driverless vehicles, it and other chipmakers were already making the same kinds of devices for 3D games and other apps.

Your smartphone is the perfect place to watch Hulu on the go. Whether you're looking to catch up on your shows in a hotel, or your phone is the only screen available, mobile streaming can be a lifesaver. But what about when you have access to a TV? Wouldn't you rather watch your favorite Hulu Original on the big screen than on your comparatively tiny smartphone?

Nauto, which develops driver-monitor cameras and algorithms for autonomous vehicles, is among a growing list of driverless startups able to attract tens of millions of dollars in funding after raising $159 million in its latest round of financing.

Besside-ng is the hidden gem of the Aircrack-ng suite of Wi-Fi hacking tools. When run with a wireless network adapter capable of packet injection, Besside-ng can harvest WPA handshakes from any network with an active user — and crack WEP passwords outright. Unlike many tools, it requires no special dependencies and can be run via SSH, making it easy to deploy remotely.

Watching YouTube on your phone has never been a better experience than it is today — our smartphones have super-sharp displays that make watching the newest HD, QHD, and even 4K content look fantastic. But there are plenty of circumstances where we want to watch our content on a larger screen.

Last month, AT&T made headlines with its disastrous launch of its 5G Evolution network (spoiler alert: it wasn't actually 5G). T-Mobile responded to the embarrassing news by saying the company would be working on its own 5G network, and would take its time rolling it out. Well, T-Mobile may have just pulled an AT&T — T-Mobile is launching LTE-U in the US, and things seem pretty similar to the 5G Evolution's introduction.

Virgin Wireless, perhaps best known for Sir Richard Branson and all of his antics, is an affordable cellular option here in the US. Virgin customers can enjoy — if that's the right word for it — Sprint's cellular service, at a discounted rate, however, there are usually some compromises for that. Now, there will be yet another compromise for Virgin customers who don't like iPhones — Virgin will now only carry Apple's phone on their network.

UPDATE 5/12: According to Bloomberg, it looks like the merger is on. Anonymous sources claim discussions have already begun about consolidation. Looks like there might be a new 5G powerhouse after all.

With chips in four out every five PCs made since 2010, few companies are as pervasive in modern computing as Intel. That's why an advisory released Monday, May 1, confirming a remotely exploitable vulnerability in all non-server business hardware made in the last seven years has sent shockwaves through the technology world.

No one is safe anymore, it seems. Google's Project Zero has just uncovered how easy it is for attackers to target your phone's Wi-Fi chip, which is essentially a mini processor for Wi-Fi that detects and processes networks.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

The widget system on iOS leaves a lot to be desired when compared to Android's offering, but that's not really Apple's fault. The system is there, we just need some good widgets to really get the most out of it, so it's up to developers to create some awesome apps that work with the home screen and lock screen widget panels on iPhone, iPad, and iPod touch.

ProtonMail has long been the favorite of journalists and security-conscious professionals, with Edward Snowden the most famous example. But these days, everyone cares about anonymity, so it's no surprise that ProtonMail currently has over 2 million users. And now the service is even better.

You might notice that there's been a few changes around here. All of us here at WonderHowTo have been working hard to create fun new spaces and topic areas to dig our heels into. We've created a few brand new websites, spiffied up our design, and today we're launching the WonderHowTo network.

The Pixel and Pixel XL come with an awesome data-saving feature called Wi-Fi Assistant that automatically connects to open internet hotspots, then creates a secure VPN on your device to keep your data safe.

You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication between your browser and a website are unencrypted, which means it can be eavesdropped on.
Hello, I'm a new guy around here and since I'm not seeing much tutorials in C i thought of contributing with something relatively simple. This will be a short series.
Hello guys I am ROMEO 64 (sounds weird I guess but who cares. :D).. Alright....Ever wondered what happens when you login to your Facebook account?

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

How to do an NMAP scan on Armitage to find IPs within a certain range. Armitage is a gui interface of Metasploit, and advanced hacking/exploiting program. It can be downloaded from http://metasploit.com/ and http://fastandeasyhacking.com/ and you will need NMAP. http://www.nmap.org/
Greetings null-bytians. Say you have been able to penetrate your neighbour's AP, and of course you had spoofed your MAC address. Now you go on and test to see with excitement if the password really works and the MAC is still spoofed. You login successfully and you browse the web forgetting to check what your current MAC is. Well, if you may do an ifconfig command, you will see that your permanent MAC is being used. Oh!! and guess what, ... your real MAC has been logged. Even though there is t...

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.