If you're looking for your bathroom to be a bit more shiny, you might want to look into installing a stainless steel vanity. If you don't have the money to buy it, you can easily cover your existing one using a foil that gives off the look of stainless steel.

When Apple first released the iPad, they only offered a WiFi enabled version. This would make your iPad similar to an iPod Touch. If you are one of the impatient Apple fans who couldn't wait til 3G, check out this tutorial.
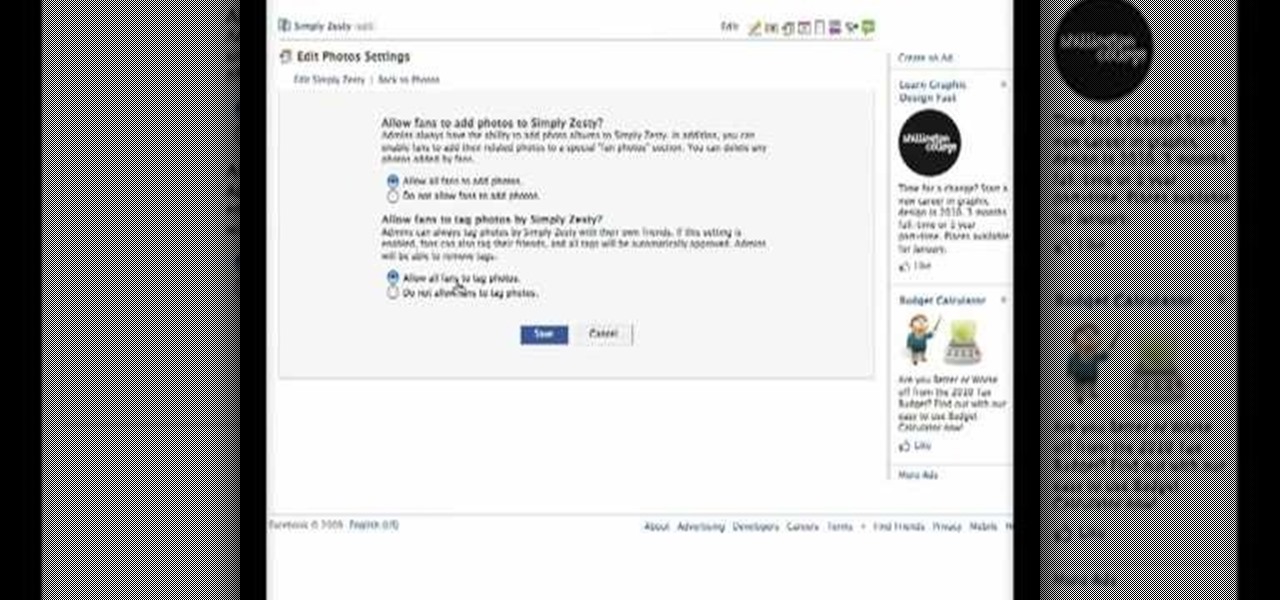
Facebook is the most popular social networking websites that can be used to stay in touch with friends and family. Using facebook you can look up your friends and even see the photos they have uploaded. You can also tag photos in the application. To do this go to your editor page and scroll down to photos. Now click edit settings inside it. At the bottom select 'Allow all fans to tag photos' option and save it. Now when you go to your home page and open the photos section you can tag them and...

Iphone is a innovative product from Apple, which can be used for many purposes. Some times even when using different applications and having a collection of music in your Iphone you may still be left with some space on it. Now you can use this space to fill it with other files which are not necessarily supported by the phone. Air sharing is a wonderful application which lets you drag and drop files into your Iphone. You can now browse it from any connected computer in your local network. So a...
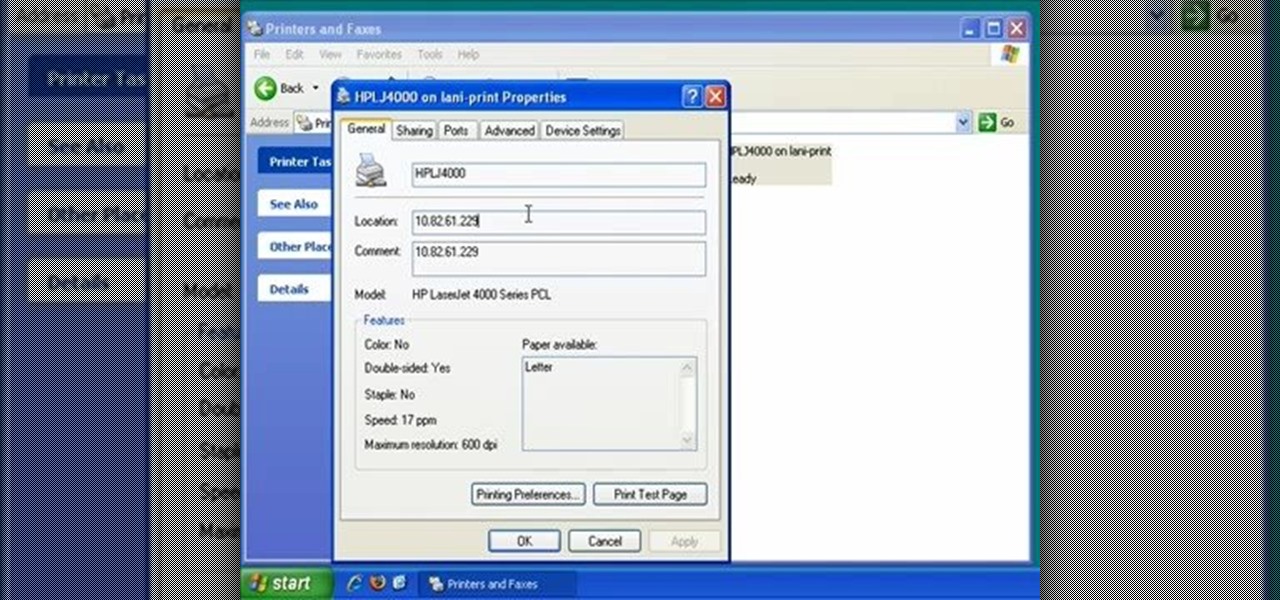
In this video, we learn how to find the IP address of a printer on your computer. Before you begin, make sure you start on your main desktop. First, click on the "start" menu, then click on "control panel" and last click on "printers and faxes". Once you're in there, right click on the printer you want to see the IP address for and then click on "properties". After this, you will find the IP address under the "location" section. You can look up the IP address for all the printers in your netw...

First, on your computer access your command prompt and type in ipconfig. Find the line called default gateway and write it down for later. Type your default gateway into your internet address bar and it will bring up your router setup page. Find your upnp and enable it, this will open your NAT. Start your XBox 360 and go to system settings on your XBox dashboard, go down to network settings and test your connection. Next go to IP settings then manual then IP settings. You want to change your ...

FROMAN1115 teaches you how to change your NAT type to Open on your PlayStation 3. On the PlayStation 3, go to Settings-Network Settings-Settings and Connection Status List and write down your IP. Go to your PC and start your internet browser. Type in 192.168.1.1. This will bring up the router settings page. Go to Applications and games and then DMZ. Check the first box that says Enabled. Enter your IP address below and click ok. Your settings have been saved and you can enter a new internet m...

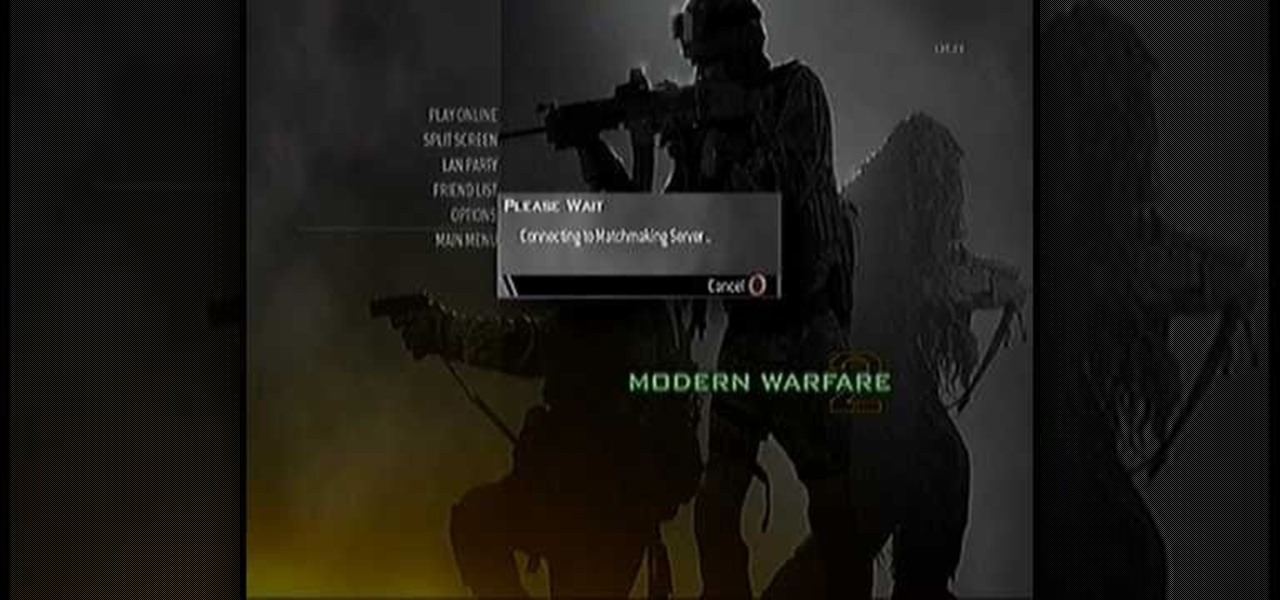
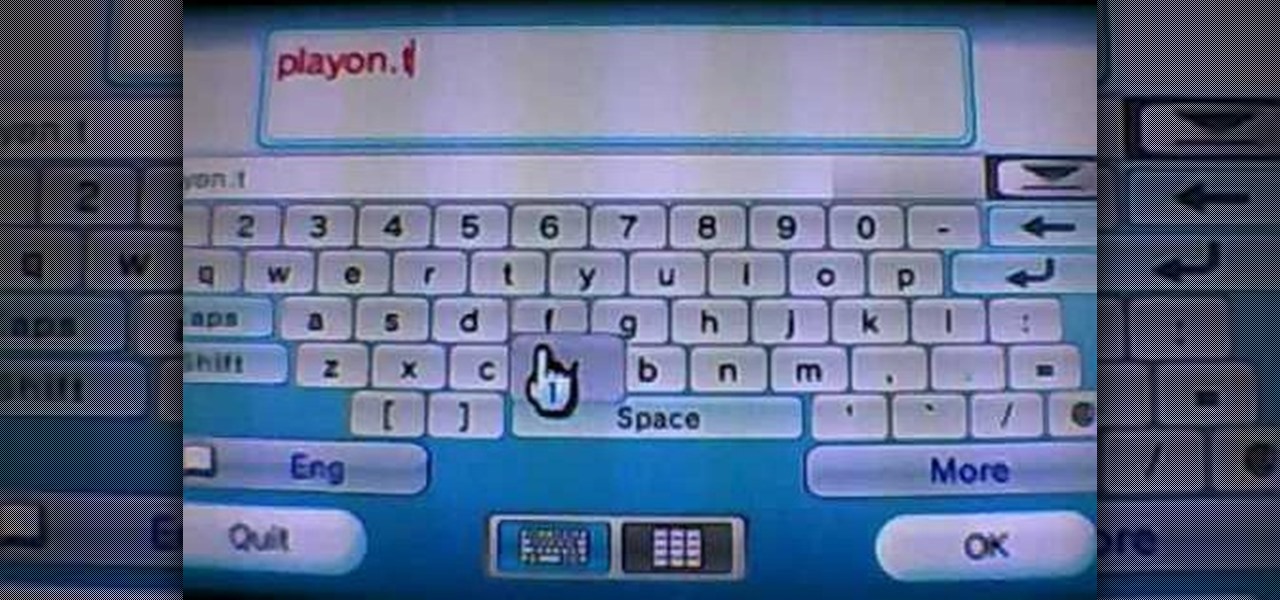
Evan shows viewers how you can use the PlayOn option on your Wii to watch videos on Netflix or Hulu. He starts off by showing how you can set up your wireless network and your connection settings. You will need to do this first if you have never done this before. To get PlayOn you will have to purchase it from the Wii Store using Wii Points. Evan also shows how you can link your internet channel to PlayOn so that you can view videos in just seconds. Watch all his tips and techniques and you c...

CreativeIceDesigns shows you how to make a "Polaroid"-style image on Photoshop CS3. Open a new 400 x 500 pixel image, and create a new layer, and drag underneath the original background layer. On the original "Layer 0" (the top-most layer), take the marquee tool and cut out (delete) a square, so that what you have in front of you looks like a Polaroid picture. Drag the the picture you want in, transform it into the right shape (ctrl + T) and drag it underneath "Layer 0." You can add effects (...

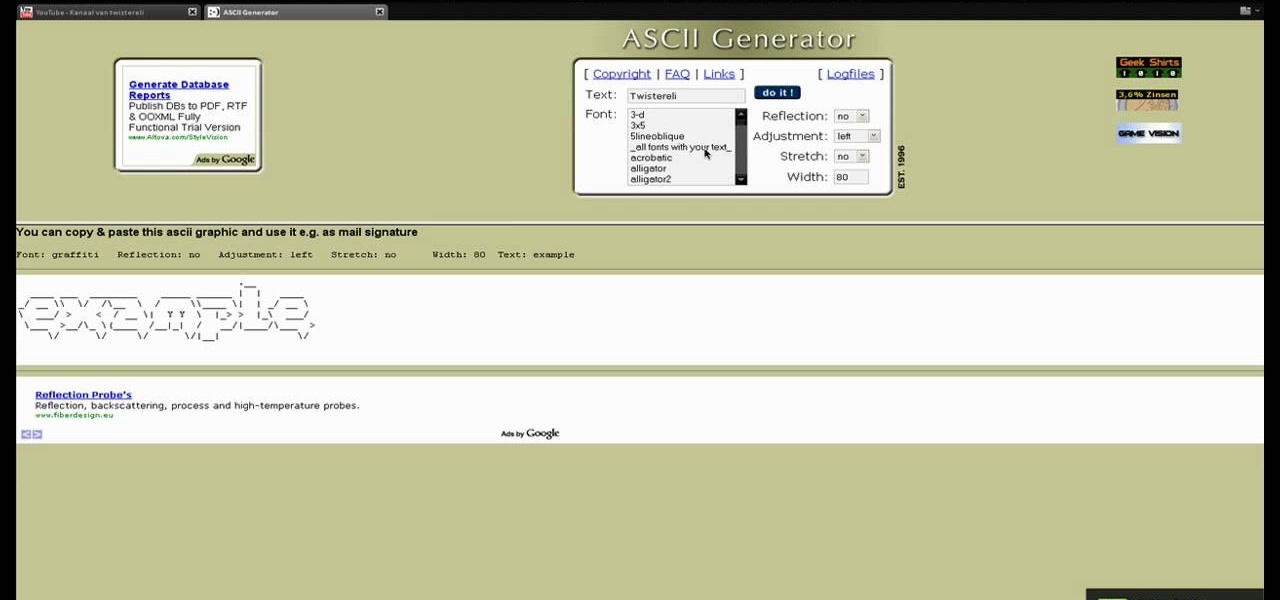
In this tutorial the author shows us how to make your own 'Subscribe' ASCII text for your channel. He says that almost every one has that text on their channels but they usually copy it from somewhere else. So in this video the author how to do this using a web application called ASCII Generator which is found at http://www.network-science.de/ascii. He goes on and shows how to generate that ASCII text using the different configurations and settings available in that web application. He shows ...

Can't wait until you get home to get onto MySpace? This video gives step by step instructions on how to try and unblock MySpace while you are at school or on a server that does not allow access to the site. This video does not have narration, but has written instructions on how to get around blocked sites with out using a proxy server. However, you have to have access to the system 32 files for this tutorial to work, and accessing these files does go against a lot of network policies.

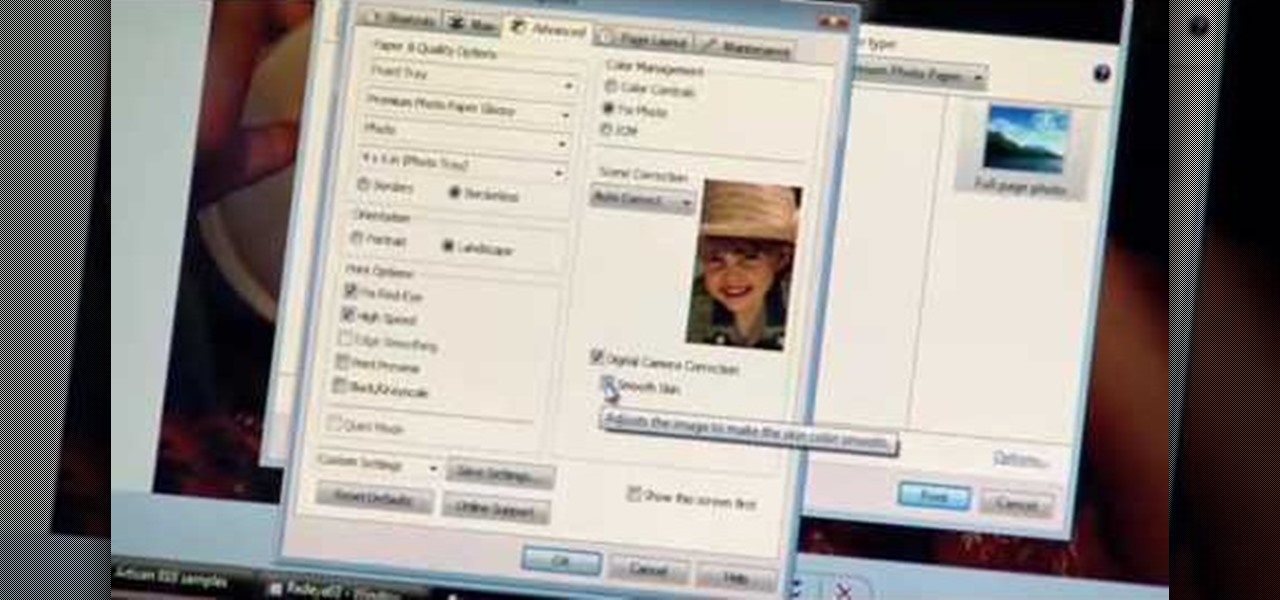
Watch this Epson video tutorial to learn how to automatically enhance digital pics with the Epson Artisan 810 All-in-One Printer.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to hack a SharePoint site.

Go beyond the traditional 3D workflow to an immersive creative experience with the software Modo, created by Luxology. Modo is the next evolution of 3D modeling, painting and rendering for Mac and PC. Modo includes 3D sculpting tools, animation and network rendering, and advanced features such as n-gons and edge weighting.

Go beyond the traditional 3D workflow to an immersive creative experience with the software Modo, created by Luxology. Modo is the next evolution of 3D modeling, painting and rendering for Mac and PC. Modo includes 3D sculpting tools, animation and network rendering, and advanced features such as n-gons and edge weighting.

Go beyond the traditional 3D workflow to an immersive creative experience with the software Modo, created by Luxology. Modo is the next evolution of 3D modeling, painting and rendering for Mac and PC. Modo includes 3D sculpting tools, animation and network rendering, and advanced features such as n-gons and edge weighting.

Check out this instructional science video that teaches you about surface area. This is a NISE network demo training video for how to do a demonstration about surface area. By watching the step by step instructions outlined in this science tutorial video, you can learn all about surface area and the most effective method to killing germs.

"What's your Wi-Fi password?" That's usually the first thing guests ask for when you have them over. You tell them the network name, then try to explain your complicated hacker-resistant password, which becomes a whole ordeal. But there's a better way to do it, which doesn't rely on using the same mobile OS as your guests.

You're out and about, and nothing on your iPhone will load. A glance at the settings shows a saved Wi-Fi network with full bars that your iPhone had connected to automatically, but you're not getting any internet. If you've experienced this, you're not alone, and there's something you can do about it. You'll even increase privacy and security on your iPhone in the process.

For all the benefits 5G brings to cellular data, it isn't without weaknesses, the biggest being privacy. Yes, the latest standard comes with breakneck downloads speeds up to 4.3 Gbps, but at what cost? Like with all things on the internet, 5G devices open opportunities for both good and bad actors.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

In recent years, unwanted calls have become a top priority for the FCC. In 2016, analysts estimated that US customers received over 2.4 billion robocalls per month. As a result, the FCC has provided carriers new tools to combat this problem.

The Raspberry Pi Zero W and Pi 3 Model B+ include integrated Wi-Fi, Bluetooth Low Energy, and more than enough power to run Kali Linux. They sound like perfect all-in-one penetration testing devices, but the lack of support for monitor mode and packet injection usually meant buying a supported Wi-Fi adapter. Now, it's possible to use monitor mode on the built-in Wi-Fi chip with Nexmon.

Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

The nemesis of music streamers is data caps, cell phone or otherwise. Restricting monthly data and forcing users to decide between quantity and quality of music has had audiophiles tearing their hair out since streaming toppled the iPod. While the problem regarding music quality seems difficult to tackle, it's far from impossible.

The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

When hacking Wi-Fi networks, having the right wireless adapter is essential. But hunting online for one can be a frustrating experience. To see how the handful of Kali-compatible adapters on the market measure up, I ran a series of tests to benchmark and compare their range, signal strength, and ability to enter monitor mode and perform packet injection. This should help you determine which adapter is right for your own hacking needs.

Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.

In my previous article, I discussed installing and configuring OpenVAS on Kali Linux. Now it's time to start using OpenVAS with the Greenbone Security Assistant to audit networks for security issues. This can be extremely helpful when you are looking for vulnerabilities or misconfigurations in a large number of hosts.

OpenVAS is a powerful vulnerability assessment tool. Forked from Nessus after Nessus became a proprietary product, OpenVAS stepped in to fill the niche. OpenVAS really shines for information gathering in large networks where manual scanning to establish a foothold can be time-consuming. OpenVAS is also helpful for administrators who need to identify potential security issues on a network.

Nvidia's decades-long development of graphics processor units (GPU) for PCs has given it a major leg up in the driverless space.

Chromecast comes to mind when "casting" video from a smartphone to a big screen television, but it's not the only way to "cast" streaming content. This is especially true for Netflix, where you can cast movies and TV shows to not only a Chromecast-enabled TV, but to smart TVs, video game consoles, and other streaming media players so that you have complete control right from your smartphone.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

Hello ladies and gentlemen, I'm back with another informative(hopefully) article for you all. Once again I would like to apologize for my absence for about a week or so. I have some stuff going on with my life and university and I haven't found enough time to make a fully in-depth article. In this article I'm going to walk you through one of the main networking protocols when it comes to communication across the Internet between programs, aka UDP(User Datagram Protocol).

So, you want to perform an exploit on a victim, but you're not on the same network as their machine. In this tutorial, I'll be showing you how to set up a meterpreter reverse_tcp attack to work over the internet.

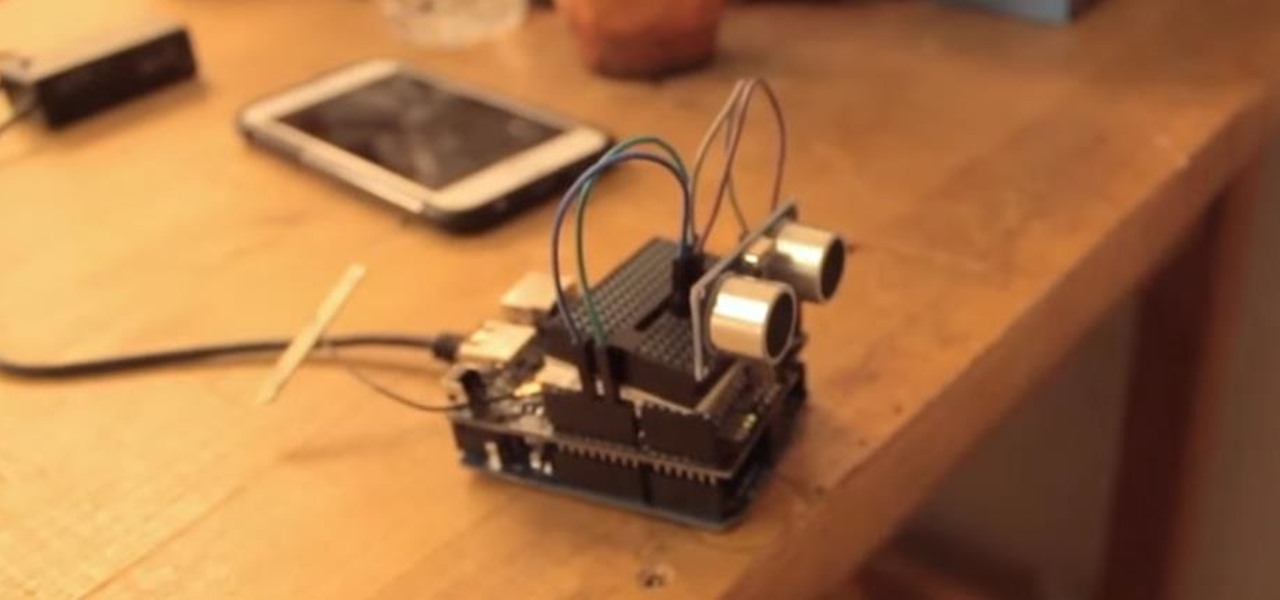
This tutorial shows you how to create an intruder alarm that sends you text message alerts when motion is detected. This may sound complicated but I am pretty confident any beginner with electronics should be able to do this just fine. The range sensor senses motion and tells your Arduino board to send the text (SMS). So you can leave the intruder detector at home, connected to your network, and still receive the SMS alerts, no matter where you are, as long as you have cell phone service.

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...
Welcome back Hackers\Newbies!