It can seem as though there's a virtually endless number of essential programming languages to choose from these days. And complicating matters even further for aspiring or even established programmers, developers, and hackers is the fact that most languages are a bit esoteric and suited for only a certain number of relatively finite tasks.

Now that more and more people are working on their personal computers and smartphones as opposed to their work computers as a result of the coronavirus outbreak, hackers are having a field day. Unencrypted home networks and public WiFi connections make it incredibly easy for cybercriminals and even government agencies to access everything from your browsing history to your banking information, and a Virtual Private Network (VPN) is the only way to stop them.

Almost 20% of the US population (about 60 million Americans) live in rural areas where mobile reception is weak or nonexistent. In times of crisis, these Americans can't rely on the internet to communicate with loved ones or receive new information. This is why being able to interact offline is so important.
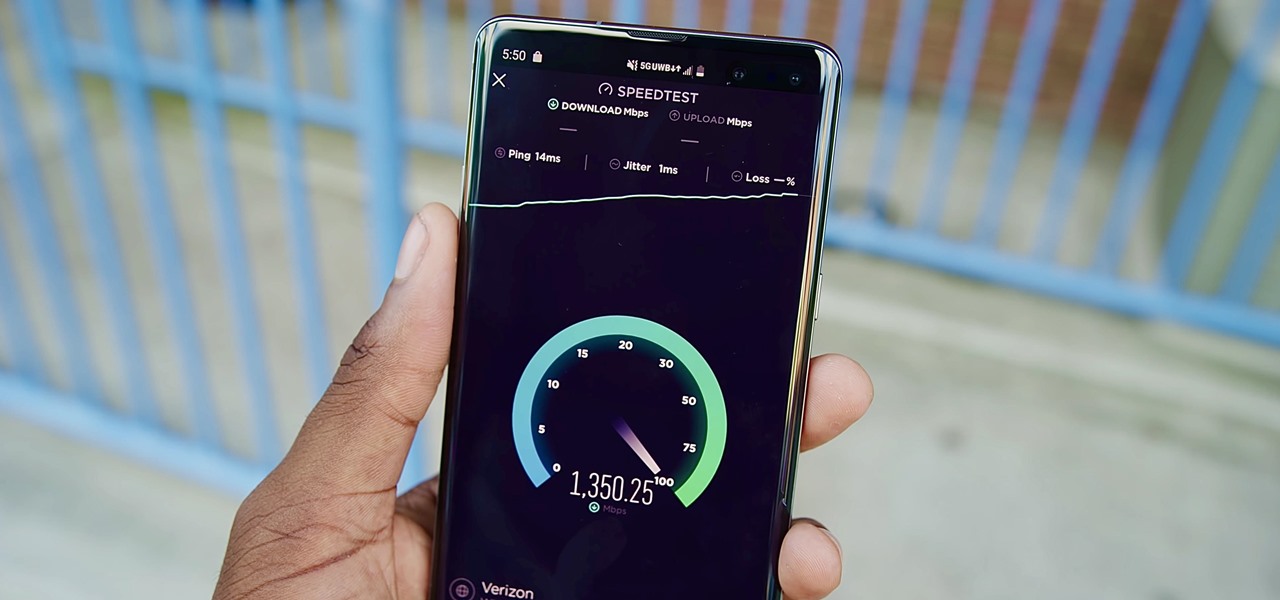
Not all 5G is equal. Even if you dropped the cash on a true 5G phone and you see it's connected to 5G in the status bar, that doesn't mean you're surfing the web, streaming Spotify, and binging Netflix faster than your friends with LTE phones.

From booting into Fastboot mode with a single command to installing mods without root access, there's no shortage of reasons to use ADB. The catch, though, you had to be tied to a computer with a USB connection. However, a new feature in Android 11 finally allows you to run ADB commands over Wi-Fi instead of being tethered.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

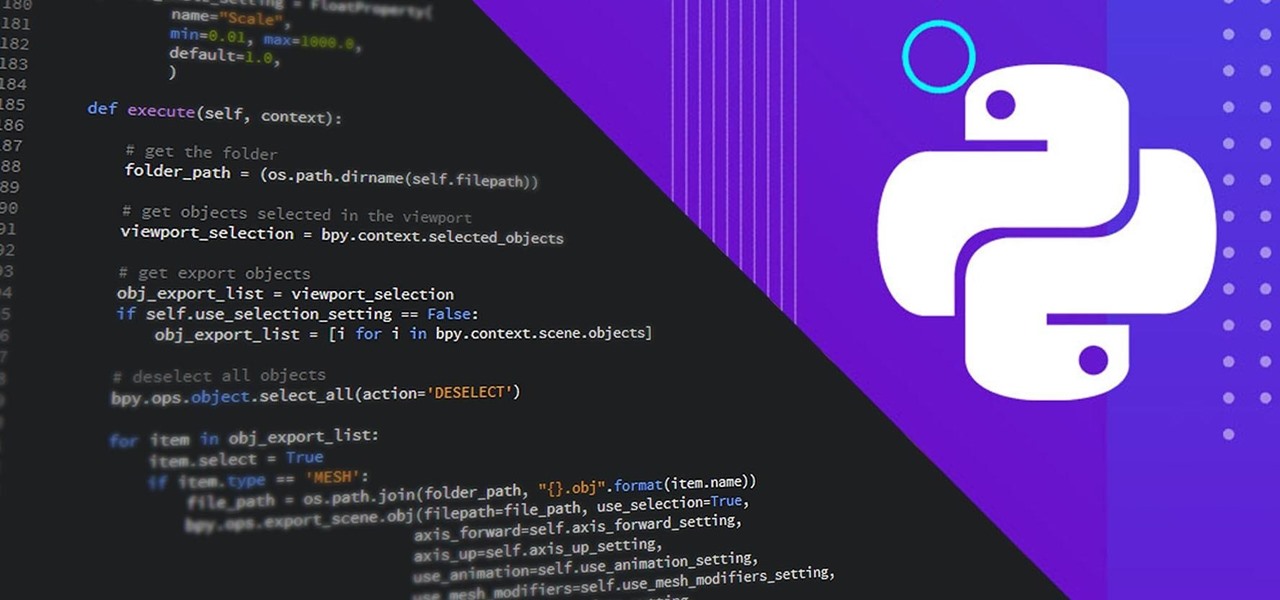
Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensive coding experience under your belt. On that note, we recommend Python for anyone who hasn't mastered it yet.

If you've tossed around the idea of turning your interest in white hat hacking into a career in cybersecurity or IT, now's as good as time as ever to invest some time and energy into improving your skill set.

Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.

After dipping its toes into the AR cloud arena last year, Ubiquity6 is now jumping in with both feet this year.

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

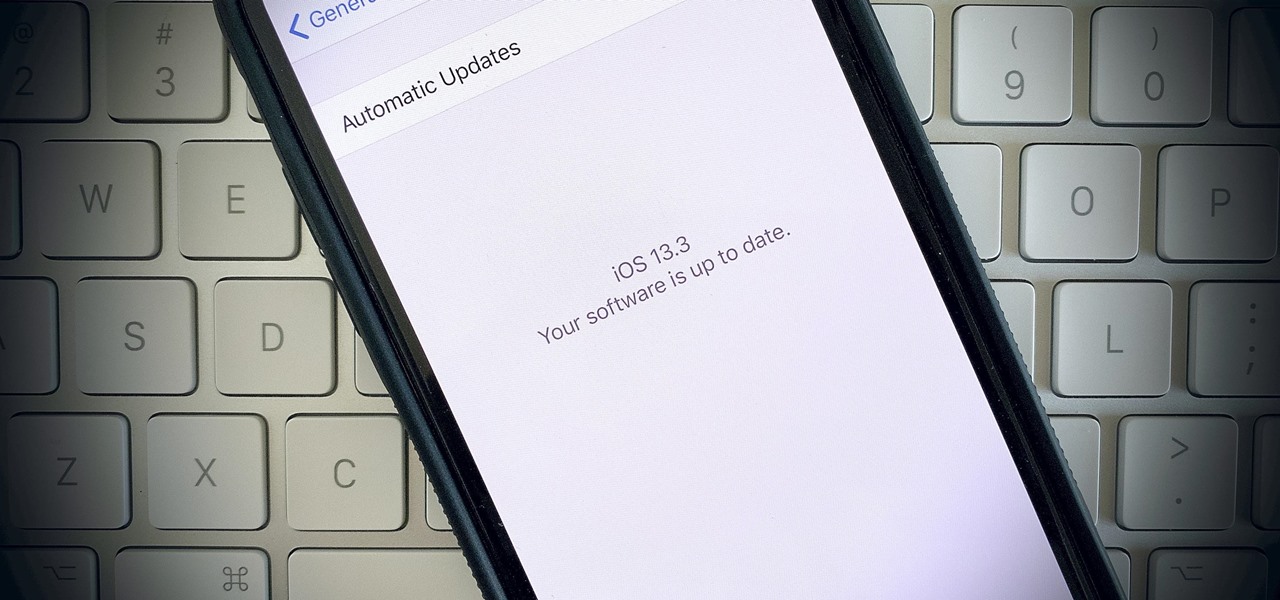
Apple is often unpredictable when it comes to beta releases, especially with public betas. Developers receive their updates first, then public testers have to wait and see if Apple will do the same for us. Sometimes, the iPhone OEM makes us wait until the following day, but not with iOS 13.3 public beta 2. This update is now available to download and install.

We're finally back in the swing of things. For the first 26 days after the release of iOS 13.2, which introduced 22 new features and changes to the iOS 13 era, there wasn't a new beta. Then, Apple released iOS 13.3 developer beta 1, and now we seem to be back on schedule, as Apple just released 13.3 beta 2 to developers.

The latest official update for iPhone, iOS 13.2, introduced 22 new features and changes to the iOS 13 era, building off the improvements brought by iOS 13.1 and iOS 13 proper before it. It's time to take our first peek into what's next for iPhone and iOS, as Apple releases iOS 13.3 developer beta 1 today, Tuesday, Nov. 5.

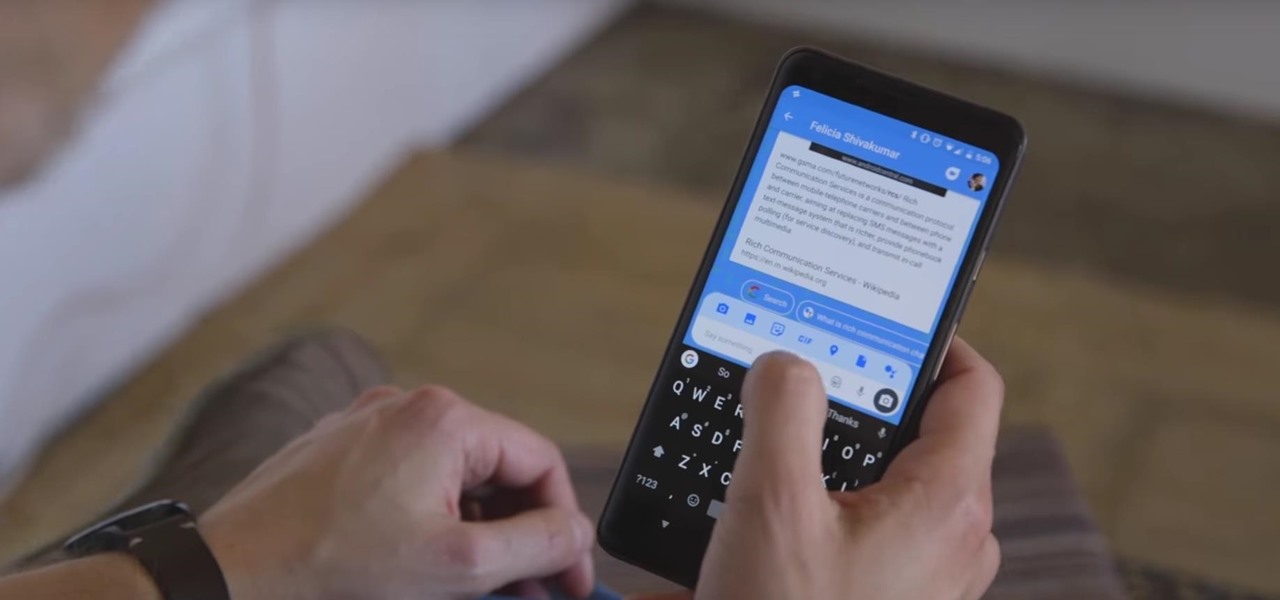
In November 2016, the RCS Universal Profile (Rich Communications Services) was introduced. The technology takes text messaging to the 21st century, emulating many of the features found in IM apps like WhatsApp and iMessage, but working through your phone number like regular SMS or MMS. The only thing is, your carrier needs to support RCS-UP to use the feature. Thankfully, the list is growing.

Just like Apple and Google, Facebook has been working to develop computer vision shortcuts designed to give mobile apps augmented reality superpowers.

A century-old opera is getting a revamp in the UK after swapping dusty wigs and curtains for augmented reality overlays and Snapchat filters.

Augmented reality plays a key role in the evolution of adjacent technologies, such as 5G connectivity and brain-control interfaces (BCI), and the business news of the week serves up proof points for both examples.

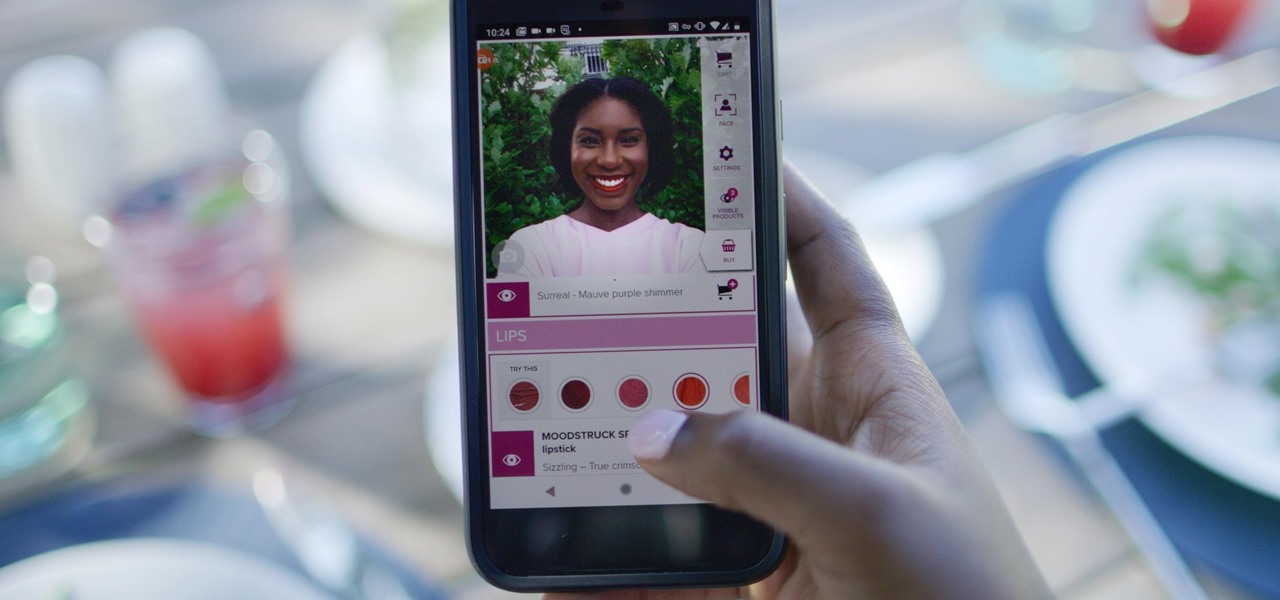
Now that some of the best-known beauty brands are leveraging augmented reality to market and sell products, the rest of the market is beginning to catch up — fast. The latest competitor to add AR to its arsenal is direct sales makeup company Younique.

Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.

When the Steam Link app was first introduced in 2018, I was impressed. As long as you were on the same network as your PC, you could play your Steam games on your phone. But now, it's even more impressive. By enabling a few extra settings, you can play your Steam library on mobile data anywhere in the world.

Fireworks are the best part about the Fourth of July and other celebrations, but they can easily cause accidental injuries. It's both safer and more fun to set them off remotely, so we'll hack some standard fireworks with nichrome wire, a relay, and an Arduino to ignite remotely over Wi-Fi using any smartphone or computer.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

I'm here at the annual AWE event in Santa Clara, California, and the venue is just as packed, if not more so, than last year.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

On Sunday, Microsoft did what everyone expected the company to do by unveiling the long awaited HoloLens 2.

The Oscars are fast approaching, which means that all the most talked about films are getting a second dose of heavy promotion in hopes of winning an Academy Award.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

The release of Avatar Chat for Magic Leap One and Spatial for HoloLens during the fourth quarter of 2018 appeared to revolutionize video calling via augmented reality.

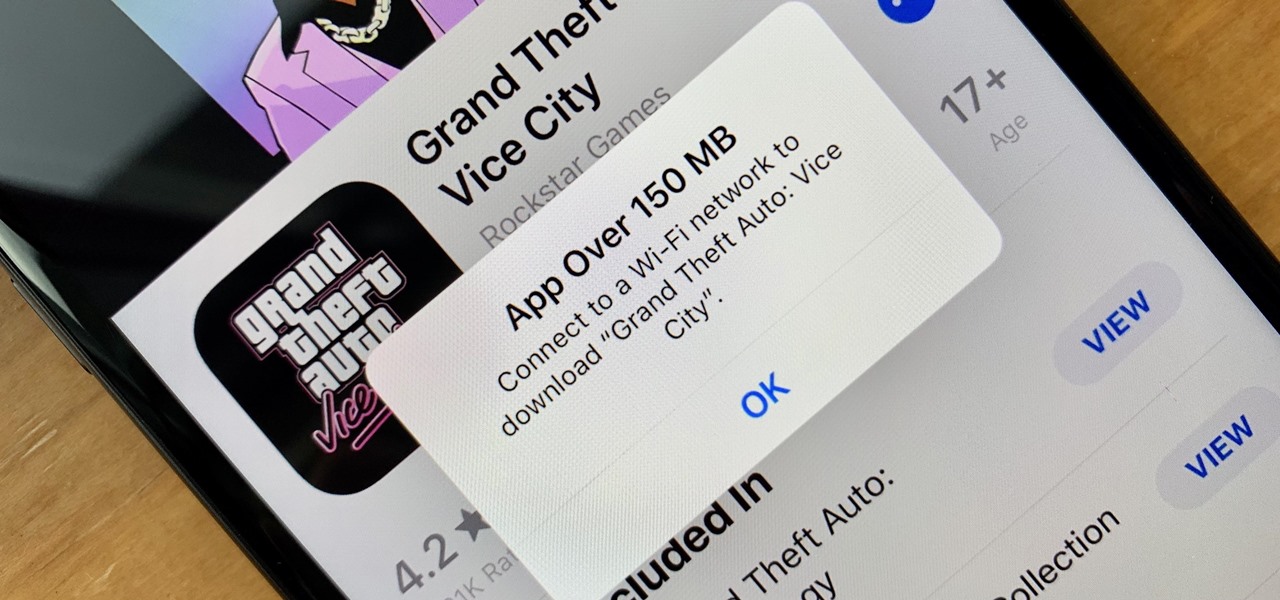
These days, cellular connections can be just as fast — if not faster — than traditional internet providers. That, coupled with the prevalence of unlimited data plans, means less worrying about hopping on a Wi-Fi network to download something. However, try to install an app or update over 150 MB, and your iPhone will insist you switch to Wi-Fi. We don't think this is very fair, so here's a way out.

The team at Magic Leap just got a millennial-style boost with the announcement that financial news network Cheddar is coming to the Magic Leap One.

So, you've lost your Apple TV remote. Maybe it's busted. What are you supposed to do now? You could go out and buy a new one, but they're expensive if you have a newer Apple TV with a Siri Remote, and wouldn't you rather spend that money on a movie? You might be without a working dedicated remote, but you likely have the next best thing already in your pocket.

The company behind augmented reality's first real gaming hit, Pokémon GO, is quietly making moves toward supporting the rapidly growing smartglasses space that may one day move its content away from smartphones and tablets and onto AR lenses positioned on your face.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

One of the biggest advancements in the new iPhone XS, XS Max, and XR is the dual SIM functionality that will let you use two cellular networks at once. Like Sinatra, however, Apple is known to do things its own way, so their dual SIM setup is a bit different than you might think.

The road to becoming a skilled white hat is paved with many milestones, one of those being learning how to perform a simple Nmap scan. A little further down that road lies more advanced scanning, along with utilizing a powerful feature of Nmap called the Nmap Scripting Engine. Even further down the road is learning how to modify and write scripts for NSE, which is what we'll be doing today.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Earlier this year, Samsung released the Galaxy J3 and J7 to select markets. These two devices are the latest in the J series, Samsung's super-budget series that tries to rewrite what it means to be a budget phone. Now, starting September 14th, you will be able to get them GSM unlocked.