
How To: Use Gmail
Learn how to use Gmail to its maximum potential; get internet tools and computer networking tips from expert Drew Noah in these free instructional videos.


Learn how to use Gmail to its maximum potential; get internet tools and computer networking tips from expert Drew Noah in these free instructional videos.

This video tutorial from agseo presents how to unlock applications in Facebook social internet network. For more detailed information go to www.agseo.blogspot.comTo unblock Farmwille and other applications on Facebook social network login to your Facebook account.From top menu Account drop-down list select Privacy Settings.Then select Applications and Website from the newly opened window.Select Blocked Applications (click on Edit Blocked Applications button).A list of all blocked applications...

Consumers who haven't already delved into the interactive wonders of augmented reality are about to be pushed into the immersive waters by market forces.

Now that more people are working from home on unsecured networks and personal devices, hackers are having a field day accessing everything from private browsing histories to personal banking information. A virtual private network (VPN) is the first and most important line of defense when it comes to protecting all of your devices from digital intrusions, but not all VPNs are created equal.

Since its release in 1991, Python has become one of the world's most popular general-purpose programming languages. From data mining and web programming to cybersecurity and game design, Python can be used for virtually everything online.

In the coming years, artificial intelligence (AI) will revolutionize every facet of technology and business. AI researchers are in high demand. Salaries in this field are regularly in the hundreds of thousands of dollars.

With millions of people working from home as a result of the coronavirus outbreak, hacking is on the rise. Nefarious black hats are taking advantage of the fact that workers have been forced to abandon their secure office networks in favor of home wireless connections. And white hats are spending even more time at home trying to be the next great ethical hacker.

In today's data-driven world, being well-versed in Big Data and analytics can help land an exciting and high-paying career. Whether you're interested in working for a major tech company or pursuing freelance work in development, you need to have a thorough understanding of the latest and greatest platforms in analytics if you want to succeed.

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

There are countless ways in which a talented and trained programmer and tech pro can earn a lucrative living in an increasingly data-driven age — from writing and creating apps and games to working for a cybersecurity firm or even the federal government.

Mac users know why they love Apple. Of course, there are limitations. An entire universe of shortcuts is unavailable to the average user.

If you've jumped on board HBO Max to watch more than just HBO's content, such as DC films, Looney Tunes, Turner Classic Movies, Cartoon Network, and movies from Warner Bros., there is a downside to HBO's improved service. Namely, you cannot use it on all of your devices yet. The most notable omission is Roku players and TVs. But there are workarounds you can use until an official app comes out.

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

If you're reading this, you're likely a tech-savvy coding pro whose analytical talents are mostly applied to designing apps, cracking passwords, and infiltrating networks — all of which are admirable activities for both aspiring and seasoned white hat hackers. But there are other profitable ways that you can put these types of skills to use, namely in the world of investment and trading.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

With EA chief executive Andrew Wilson stating the official mobile version of Apex Legends won't arrive until the 2021 fiscal year, fans have to wait at least another year to enjoy their favorite battle royale game on the go. But for those who can't wait, there are ways to play the game on iPhone and Android right now.

After leaning on augmented reality for its outdoor advertising, HBO has called on augmented reality again via Snapchat to promote its Watchmen series.
QR codes are supposed to make life easier, but having to install potentially shady third-party apps just to scan one is more trouble than it's worth. Thankfully, there's a QR code reader built into all Google Pixels, but you wouldn't know it unless you stumbled across the feature.

Next to Apple, Snap is currently one of the most important companies on the planet in terms of delivering products that are moving augmented reality into the mainstream. That's why it's no surprise that Facebook, which is also focused on AR and tried to acquire the company for $3 billion several years ago, duplicates many of the smaller company's features.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

If your iPhone XS or XS Max has been suffering from Wi-Fi connectivity and charging issues, Apple just released iOS 12.0.1 on Monday, Oct. 8, as an over-the-air update for all compatible iPhones. The main focus of the update is to give fixes for users going through "Chargegate" and experiencing Wi-Fi issues.
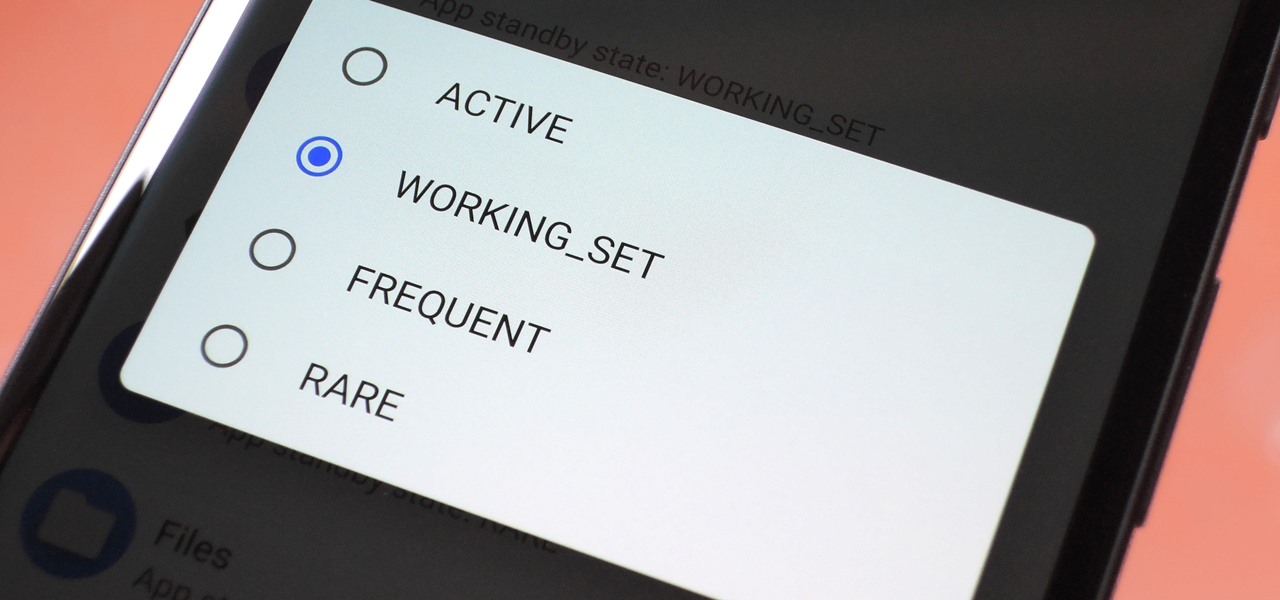
Battery drain is a major pain point for Android users, though that promises to change thanks to Android Pie's new Adaptive Battery feature. But Google hasn't said much about the inner workings of this feature, only publicly stating that it uses AI to boost battery life. So we dug in to find out what's really going on under the hood.

On Friday, at IFA 2018 in Berlin, Samsung invited attendees into the residence of Family Guy's Griffin family to learn all about its "smart home" products via augmented reality.

Magic Leap has been promising to launch a developer conference for years, and now the company is finally making good on that promise. On Wednesday, Magic Leap sent out the official announcement for its first L.E.A.P. conference, which will be held in Los Angeles in October.

Gmail conversations, Facebook private messages, and personal photos can all be viewed by a hacker who has backdoor access to a target's Mac. By livestreaming the desktop or exfiltrating screenshots, this information can be used for blackmail and targeted social engineering attacks to further compromise the mark.
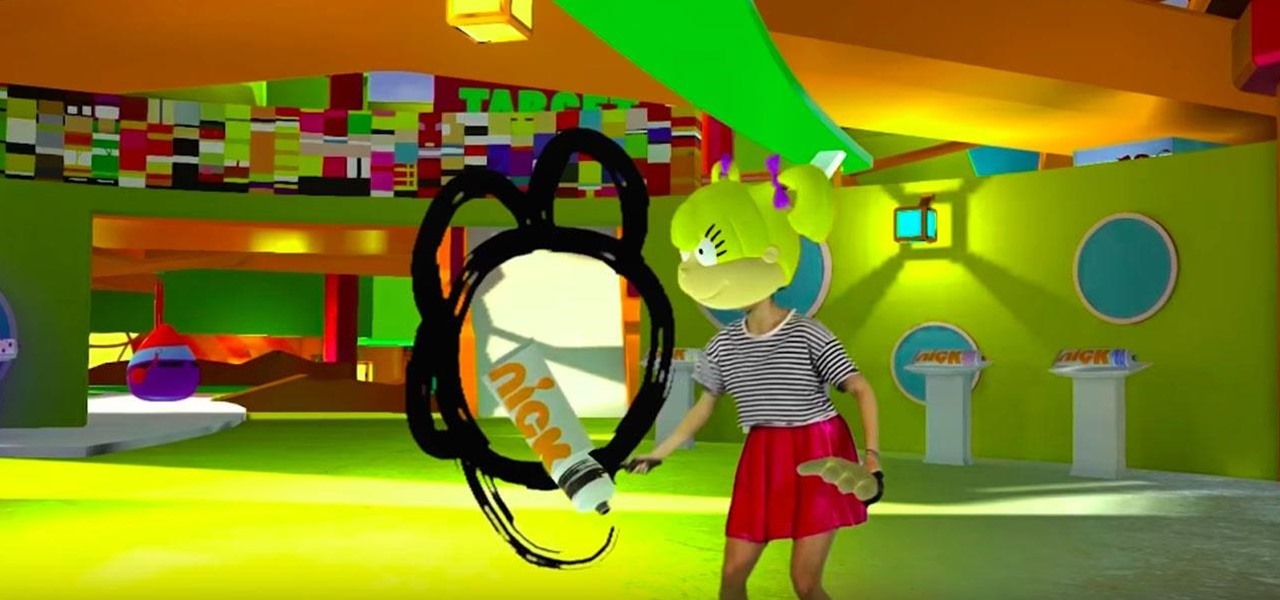
Cable TV network Nickelodeon is looking to break new ground with a new series that will be experienced in virtual and augmented reality.
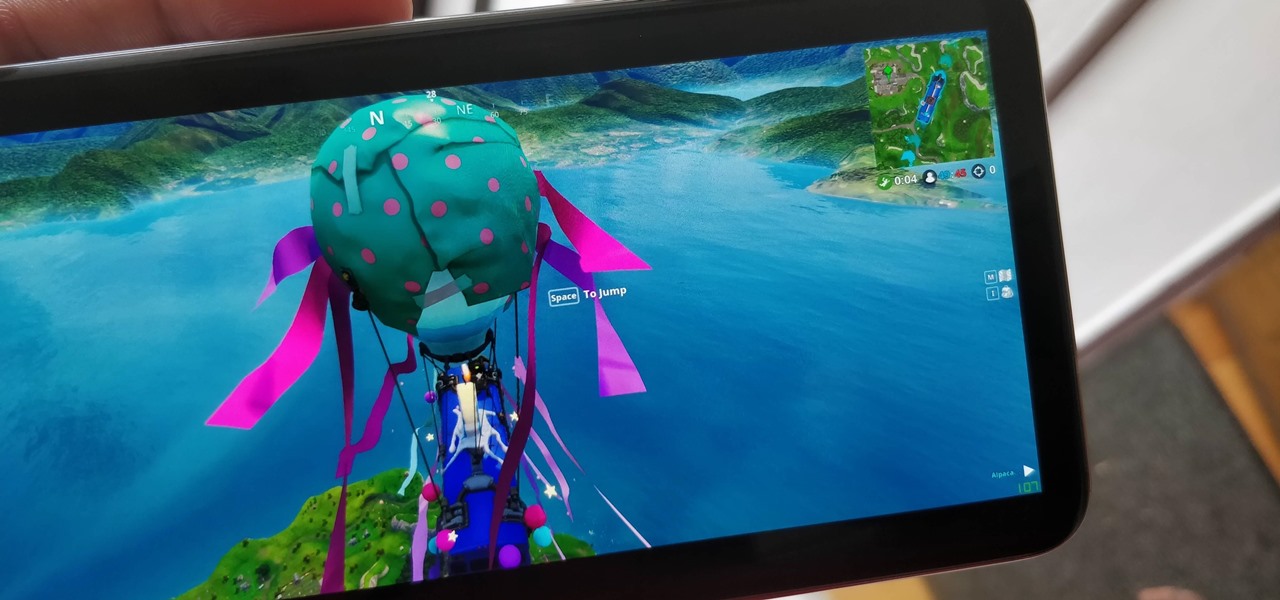
Since early March, iOS users have been able to enjoy the most popular video game sweeping the rounds. Android users have been left envious as they wait for a "few months," the only vague release date given by Epic Games. In the meantime, there are a few ways we can still satisfy our urge to play.

Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positive or negative tweets to amplify, gives rise to the ability to execute a number of disinformation campaigns.

A new study published by American University demonstrates how Pokémon GO and other augmented reality games can help city governments bring communities closer together.

Augmented Reality beauty tools have become quite popular lately, and while CoverGirl's didn't exactly turn heads, the new Wanna Nails app by Wannaby looks like a great tool for anyone who uses nail polish.

The misconception that macOS is more secure than the Windows operating system is far from the truth. With just one small command, a hacker can completely take over a MacBook and control it remotely.

Looking to inject a little more processing juice into your HoloLens? Unity can fix you up with the Standalone Universal Windows Platform Holographic Emulation.

Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full installation is better. A few simple changes can be made to a Kali Linux desktop to make it safer to use in this environment.

After the spectacular rise and fall (and rebirth) of Glass, Google is taking another run at augmented reality smartglasses.

Augmented reality might not be able to cure cancer (yet), but when combined with a machine learning algorithm, it can help doctors diagnose the disease.

The guy who recreated Super Mario Bros. as a first-person obstacle course is back with an augmented reality take on another classic game.

Just a week after rumors surfaced of a massive new investment in Magic Leap led by Saudi Arabia's Public Investment Fund (PIF), the investment has been confirmed by the company's CEO Rony Abovitz.
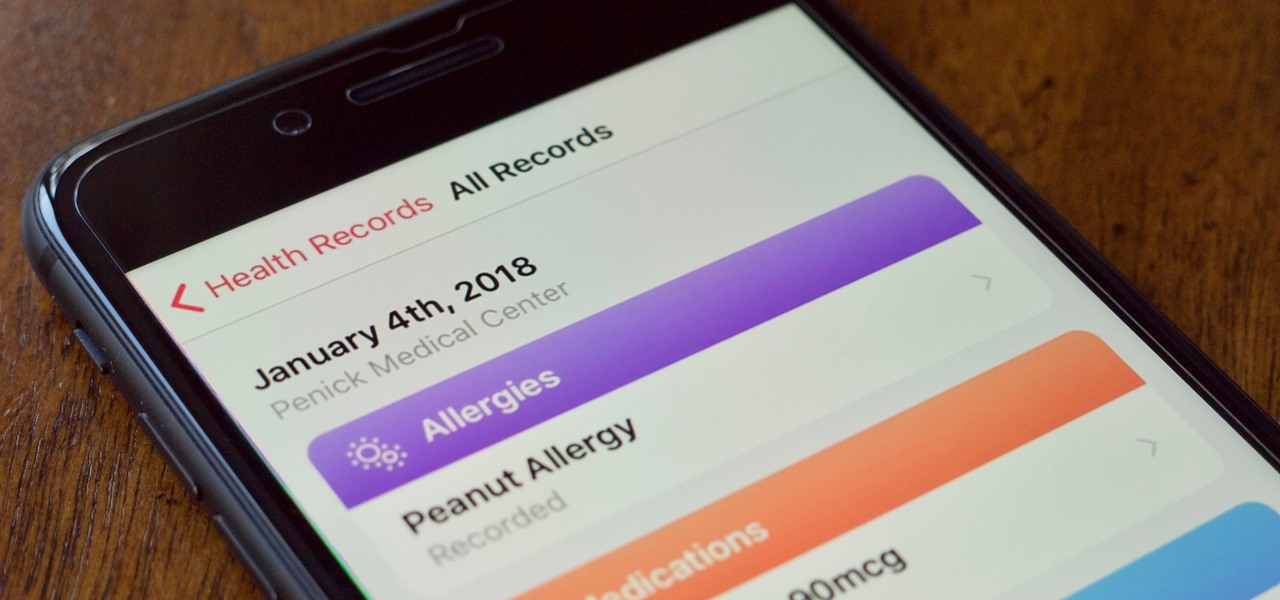
Mobile phones are not only essential for work and communication, they're quickly becoming an integral asset to our health. Your iPhone can store valuable data about fitness, nutrition, heart health, and so much more. And since iOS 11.3, your iPhone can even import a list of allergies, medications, immunizations, hospital visits, and other health information from your doctor or hospital.

Samsung's 2016 line of smartphones has a new update, at least for the devices on AT&T. The update brings the Galaxy S7 to version G930AUCS4BQL1 and the Galaxy S7 Edge to version G935AUCS4BQL1. Here's what's on the table.

The default tool for payload generation is MSFvenom, a Metasploit standalone payload generator as well as encoder. This tool is an incredibly powerful tool for payload generation, but it can be difficult and requires a bit of reading for newer users.