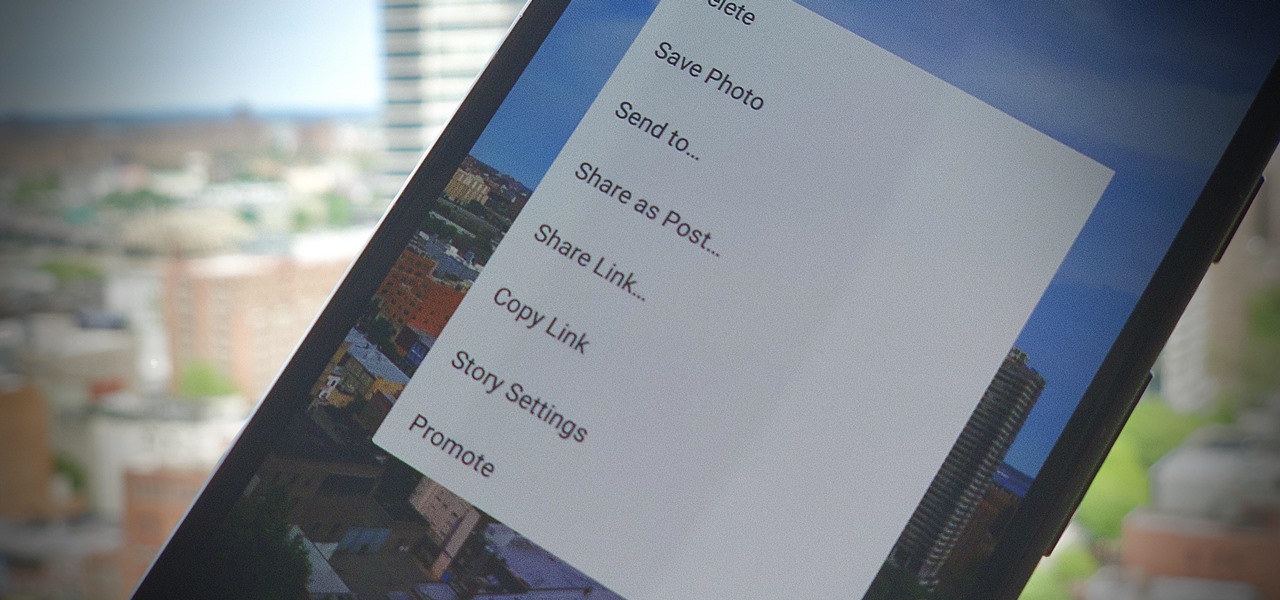
On Instagram, it's all about the sharing, but not all sharing is equal. Take stories, for example. Up until recently, stories couldn't be easily shared outside the Instagram bubble. Now, Instagram lets you share a convenient link to a part of your story or your entire story on any other platform — text, email, social app — pretty much anywhere.

Over the past two years, the tech industry has formed a series of symbiotic relationships that are now converging in the augmented reality space. This week, we took a look at these interrelated technologies and how they are shaping the future of AR.

Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.

Though many were hoping for it, a notification indicator around the Galaxy S10's front camera punch hole never came to fruition. Since then, we've been finding other uses for the camera cutout, from turning it into a circular battery meter to using creative wallpapers. Thankfully, there's now an app that will give you LED-style alerts with a ring around your S10's camera.

After reviewing the international plans for major US wireless carriers, it became obvious they're all pretty bad. Your data is heavily restricted, requiring a daily fee which can cost an extra $100+ on a seven-day vacation. That's when I learned about Google Fi, and how for most travelers, it's the best option.

To borrow from the canon of Game of Thrones, what is dead may never die. And while the Meta Company that we knew this time last year is no more, the patent infringement lawsuit filed against the company lives on.

In 2019, Sony is mixing up its design, attempting to stand out among the sea of familiarity. Instead of emulating Samsung with punch hole cameras, they decided to target a rare section of the market, content consumers. There's the Xperia 1 for those who want the best, and the Xperia 10 and 10 Plus for the budget crowd.

The augmented reality industry had enough twists this week to surprise even M. Night Shyamalan.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

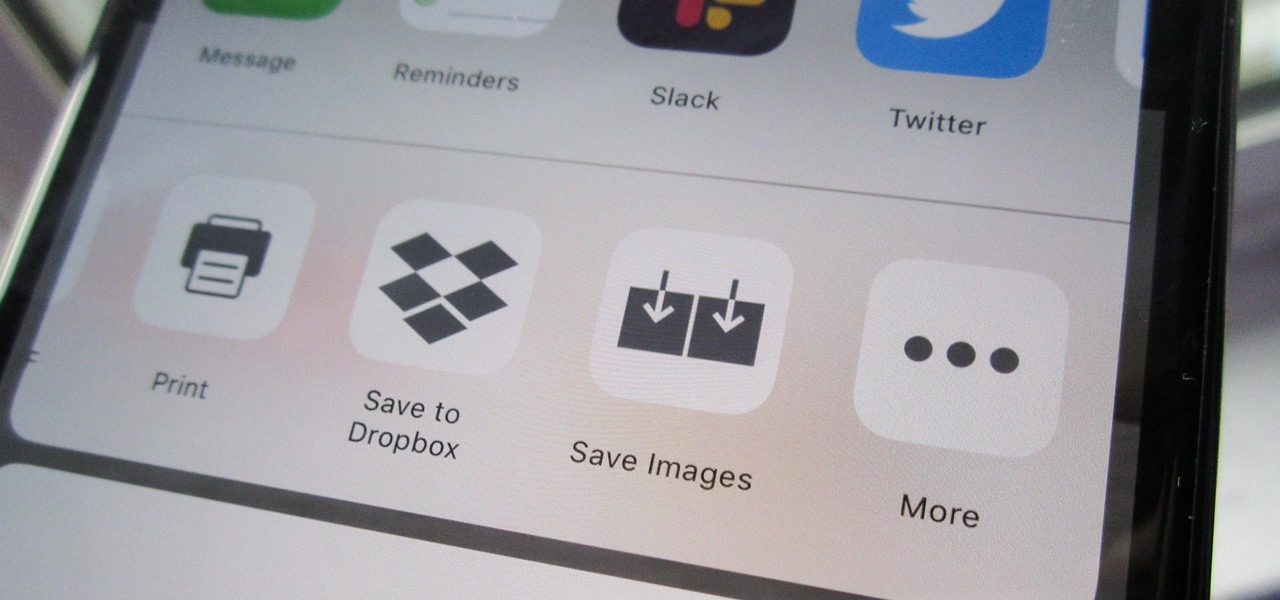
Some websites block image downloads on their webpages so you can't save them for reuse. That means long-pressing or force-pressing on protected images in Safari on your iPhone will not do anything or will omit the "Save Image" option. Taking a screenshot is the obvious solution to bypass restrictions, but you won't get the best quality. Thankfully, there's another way.

Unless you're one of the world's top golfers, there's a good chance you are not stepping onto the fairways of Pebble Beach Golf Links this weekend.

With the best selling phone on Amazon in 2018, Lenovo had big shoes to fill when making the successor of the Moto G6. Fortunately, Lenovo was up to the task. The Moto G7 continues to provide a high performance-to-price ratio, offering a worthwhile upgrade for G6 users while remaining budget friendly.

Despite its status as a hot commodity amongst emerging technologies, the augmented reality industry is not immune to the ebbs and flows that occur in every industry.

Despite being at the helms of the RCS push, Google Fi has yet to support the new messaging protocol. It would've made too much sense if the Google-created MVNO was one of the first to support the feature Google's been pushing on other OEMs and carriers for years, but alas, they haven't. Well, better late than never — Google has finally announced support for RCS Universal Profile on Fi.

As great as passcode and biometric security features like Face ID are for preventing unwanted access, they aren't needed 100% of the time. When you're at home with a locked door between you and anyone you wouldn't trust with your phone, they really only serve to slow you down. Android has long had a solution for this, but a new Cydia tweak has now brought a similar solution to iPhones.

Users are often the weakest link when probing for vulnerabilities, and it's no surprise they can be easily fooled. One way to do this is called clickjacking. This type of attack tricks the victim into clicking something they didn't mean to click, something under the attacker's control. Burp Suite contains a useful tool called Clickbandit to generate a clickjacking attack automatically.

The North remembers...that smartglasses are the future! Game of Thrones jokes aside, the smartglasses startup opened its doors, and we visited its Brooklyn store to get our hands the consumer-focused Focals smartglasses.

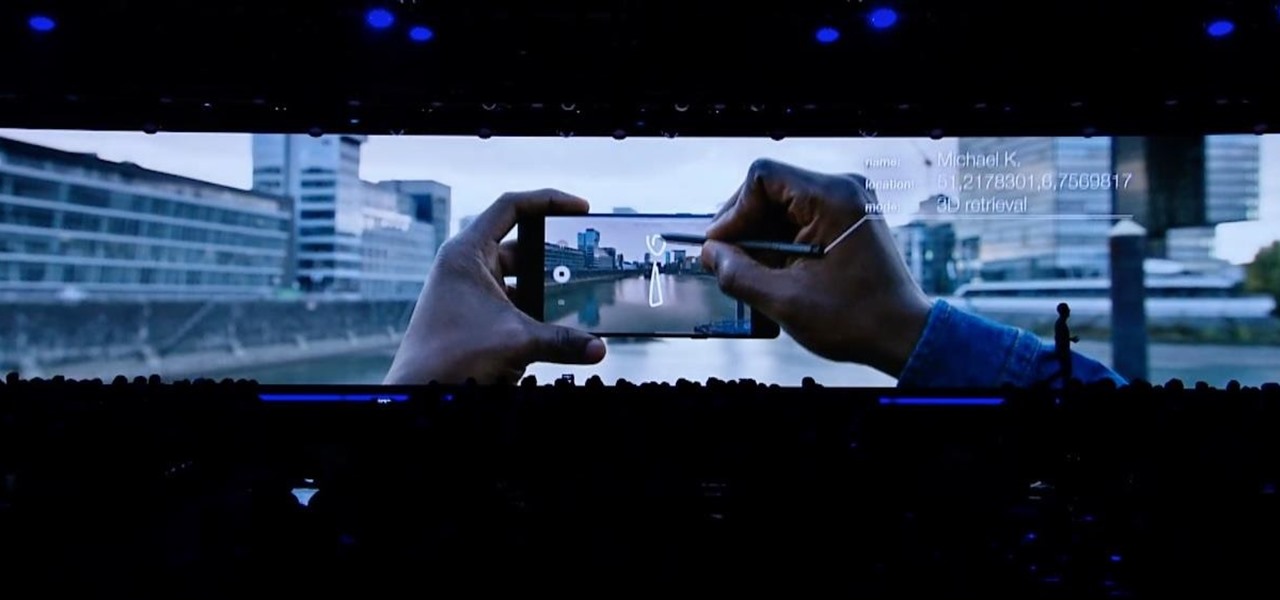
This week, at its developer's conference, Samsung took the wraps off a new tool from Wacom that bestows the S-Pen with AR powers, as well as its own entry to the AR cloud market called Project Whare.

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

When OnePlus announced their partnership with T-Mobile and the deal the magenta carrier is set to offer, mouths dropped. But as usual, this deal comes with some caveats. The bulk of these will hurt the folks who love to root, something a large portion of the OnePlus community enjoys doing.

This week, we continued our NR30 series highlighting the leaders of augmented reality space by profiling the venture capitalists and strategic corporate investors that sustain the industry.

The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for forensics.

Despite Huawei's ongoing battle with the US government, the Chinese company has continued to release phones in the US under its Honor brand. The Honor X series has been consistently released for several years, offering midrange specs at ridiculously low pricing, and the Honor 8X is no exception.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

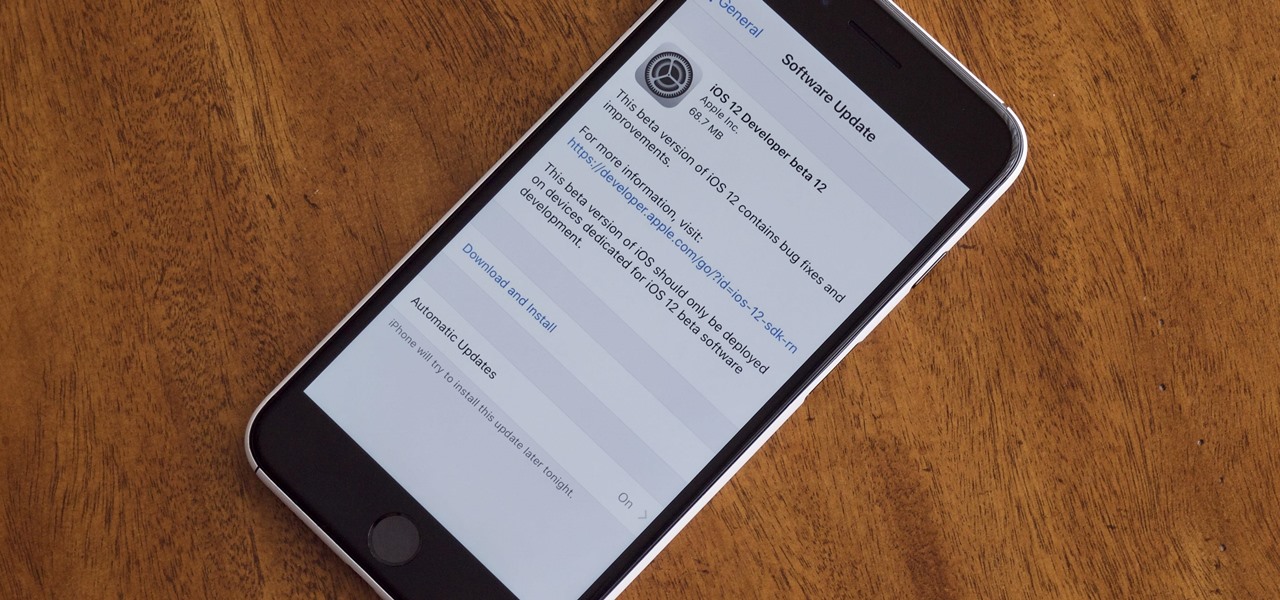
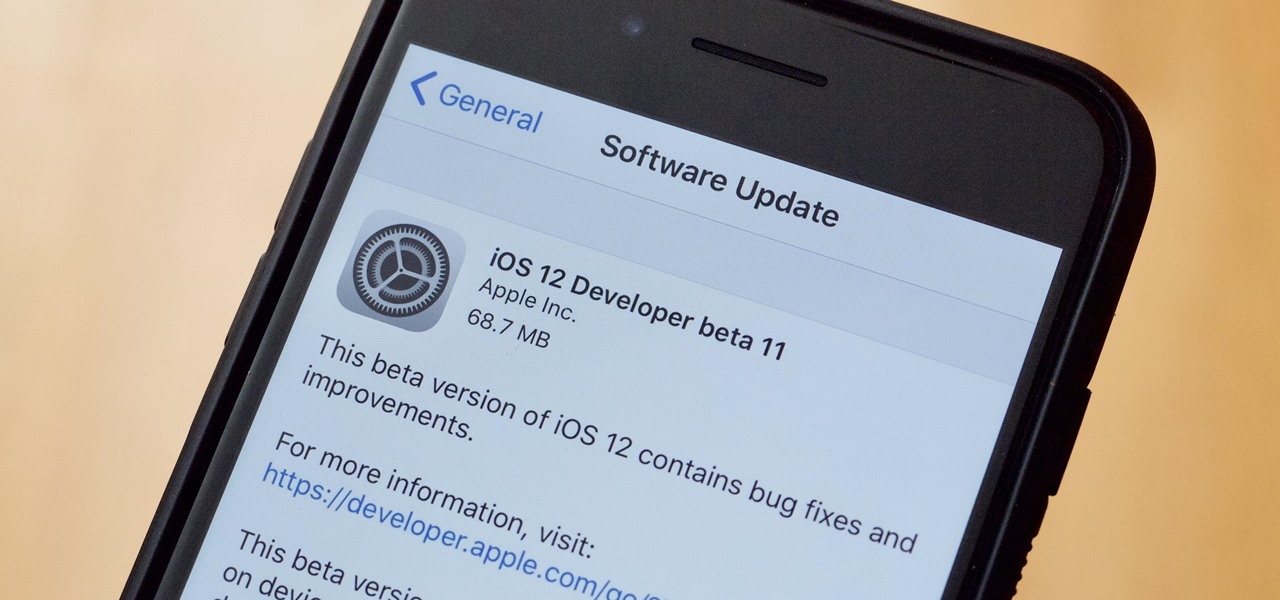
Right before the Labor Day weekend, Apple issued iOS 12 developer beta 12, which comes four days after dev beta 11 and public beta 9, and just one day after announcing the Sept. 12 event. This update primarily fixes a bug where you would be continuously prompted to install a new iOS update even when none existed.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

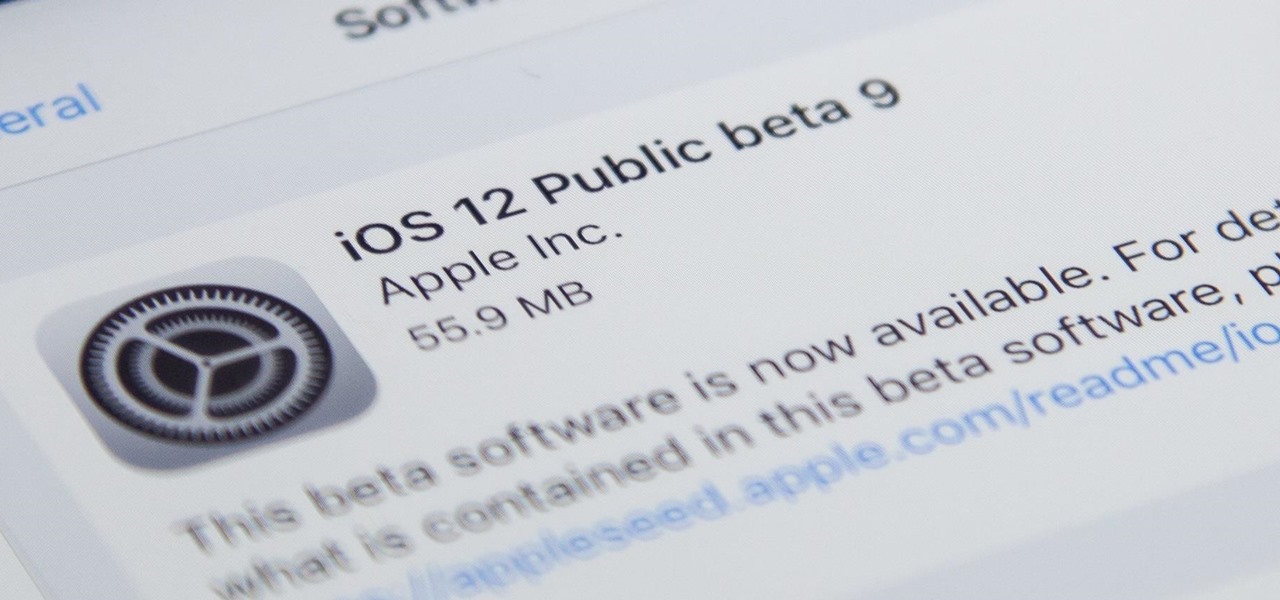
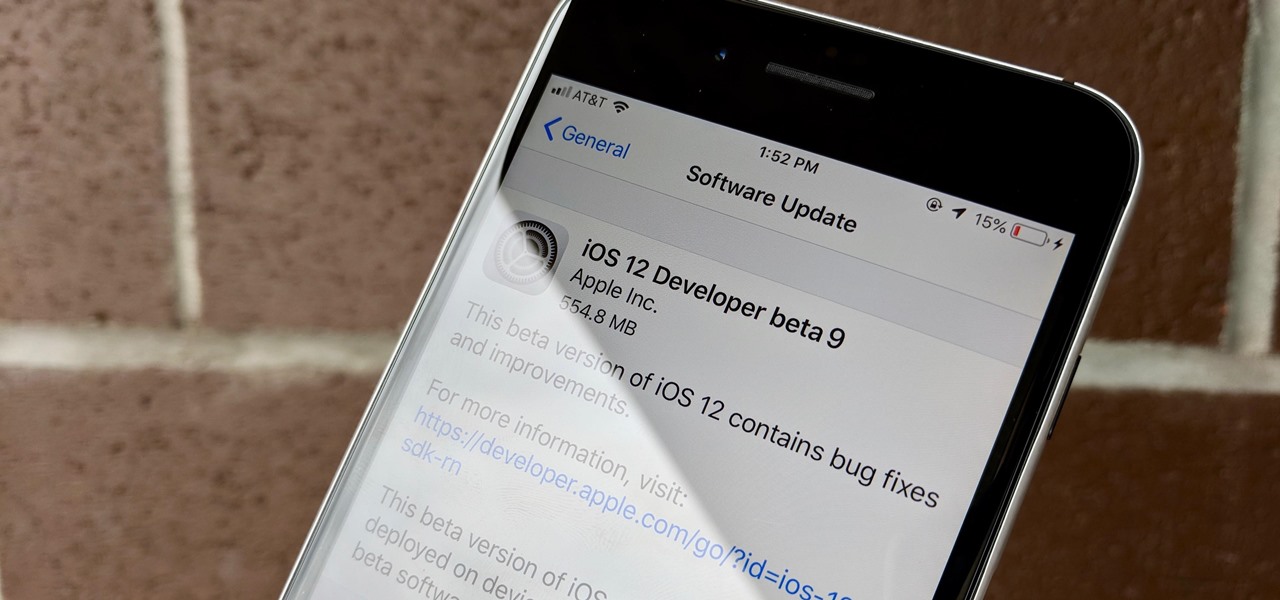
Apple released iOS 12 beta 9 to public beta testers on Monday, Aug. 27. The update comes at the same time as the release of dev beta 11. This is surprising, as Apple typically releases developer betas at least a few hours before the public version. Then again, everything Apple is doing with its iOS 12 beta as of late is surprising.

Apple released the eleventh developer beta for iOS 12 to registered software testers on Monday, Aug. 27, only four days after the company unexpectedly released both dev beta 10 and public beta 8. Apple has ramped up its beta release schedule as of late, offering minor updates twice a week in the lead-up to iOS 12's official debut in a few weeks.

Apple released the tenth iOS 12 developer beta unexpectedly Thursday afternoon, Aug. 23. The update comes only three days after the release of iOS 12 developer beta 9, a surprising move for Apple, even with the irregular releases the company has made in recent weeks.

OnePlus will be releasing a new phone in the second half of 2018, specifically, an upgrade to their T-series. Over the past two years, #T versions have come out about five months after their predecessors and have included small updates that fix any problems from the previous OnePlus device. While we do know a bit about OnePlus 6T, what it could be is much more exciting.

Can't say we didn't see this coming — Apple released iOS 12 public beta 7 on Monday, August 20, the same day it seeded the ninth version of the beta to developers. While the two betas may have different names, public beta 7 and dev beta 9 are virtually identical, so public testers shouldn't feel as though they are missing out.

Apple released iOS 12 beta 9 to developers on Monday, August 20. The company seeded the update just five days after releasing dev beta 8 to testers, itself a quick replacement for the problematic beta 7. This update was followed closely by public beta 7, confirming Apple's new same-day release schedule for both developer and public betas.

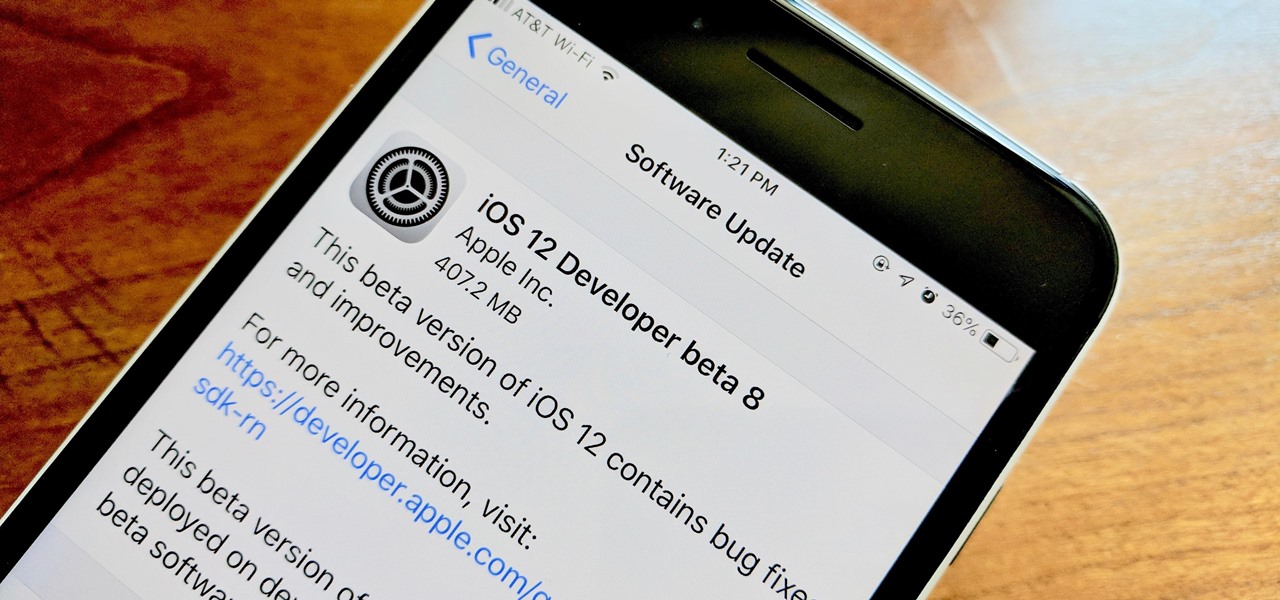
Apple developers, check your iPhones — Apple released the eighth developer beta for iOS 12 on Wednesday, August 15. This update arrives just two days after the release of dev beta 7, which Apple quickly pulled after complaints of unusual performance and stability issues.

Windows 10 and macOS have poor reputations when it comes to customer privacy and user policies. Our hacking Windows 10 and hacking macOS articles might make it seem like a reasonably secure operating system doesn't exist. But I'm here to tell you that there is a viable alternative that could provide some sense of security and trust.

A team of academics from three different universities and two private companies have just discovered a new vulnerability that affects almost every Android device since 2012. The vulnerability is known as RAMpage, and it could be used to gain complete control over the device.

During an event in Moscow earlier this year, Nokia announced a refresh to their Nokia 2, 3, and 5 series phones. While there is no official confirmation of a US release for the updated Nokia 2 and 5, we do know that as of July 2nd, you'll be able to snag a new Nokia 3.1.

Earlier this year, with the Developer Preview, we got a tantalizing glimpse of Google's upcoming Android 9.0 Pie and a whole slew of new features that comes along with it, such as iPhone X-like gestures and improved security features, to name a few. With its announcement at Google I/O, Android Pie just got a lot more accessible.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are all network services, which means we'll write our first remote exploits.