One of Android's biggest strengths is its ability to interact with other operating systems. When you plug your phone into your Windows PC, you instantly see all of the files it holds—and all it takes is a simple syncing app to do the same with Mac. To top that off, apps like Pushbullet and Join bridge the gap even further by allowing you to share links, files, and messages between all of your devices.

Welcome back my, tenderfoot hackers! Many people come to Null Byte looking to hack Facebook without the requisite skills to do so. Facebook is far from unhackable, but to do so, you will need some skills, and skill development is what Null Byte is all about.

When a headache strikes, I reach for the nearest painkiller. Forget closing my eyes, laying down, or even applying an ice pack—I seek the quickest and most immediate relief possible, and normally that comes in the form of pills. However, fast relief can be found from another, more natural source: herbal beverages. So if you're tired of popping pills when you have aches and pains, try some of these herbal drinks out instead.

As Android's official app provider, the Google Play Store is packed with thousands of useful programs. But Google's terms of service is extremely restrictive, which means that countless apps simply don't qualify to be hosted on the Google Play Store.

One of the best uses for an old Android device is to turn it into a security webcam that can be accessed over the internet. But most of the time, this is a rather difficult process, because existing apps usually require you to mess around with network settings and configure a personal web server.

Hello fellow Nullbytiens, today we will be talking about IRC again (if you haven't read OTW's post about head over there now)and more specifically about using 1 nickname with multiple devices or IRC clients.

Hello fellow gray hat hackers, I wrote a program in python that helps me to fill up my proxychains.conf file, so I don't have to manually enter in the proxies. I figured I will give a little how-to of how I did it and maybe I could help some of you(hackers) out there to stay anonymous.

Welcome to an introduction on writing basic malware, an optional sub-series in which I expose you to malware and its technologies. This is written for those who wish to seek a beginning in malware analysis or enlightenment on the subject. We will be justifying the writing and covering types of malware.

Welcome back, my greenhorn hackers! The Holy Grail of any hacker is to develop a zero-day exploit—an exploit that has never been seen by antivirus (AV) and other software developers, as well as intrusion detection system (IDS) developers. In that way, you can exploit systems with your newly discovered vulnerability with impunity!

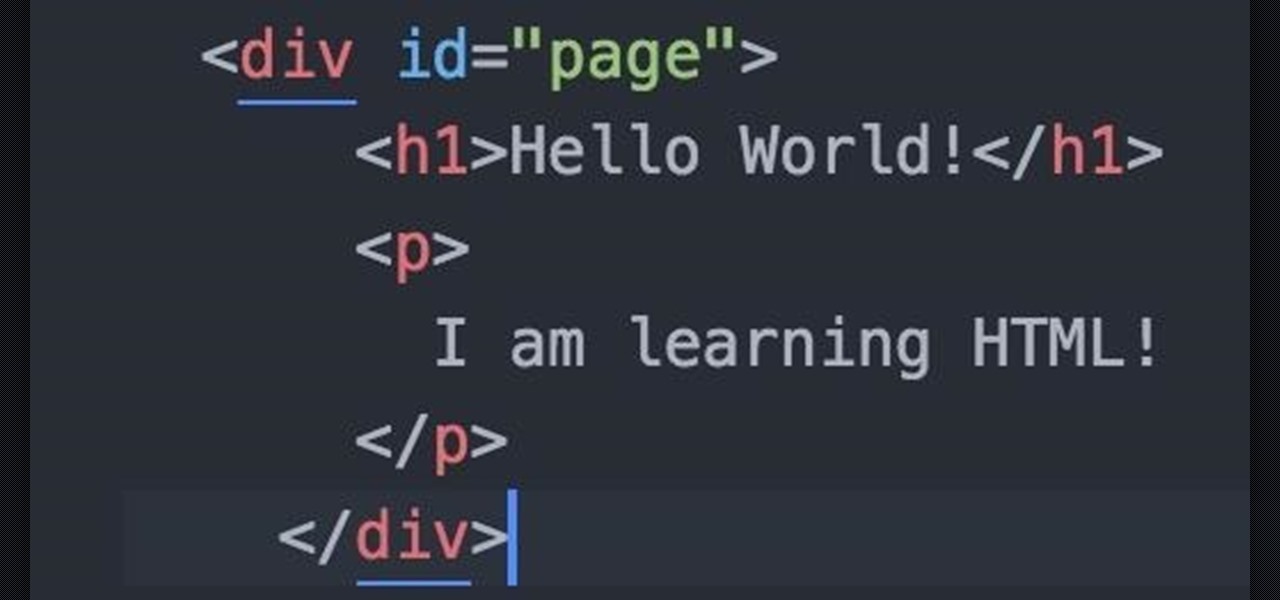
Welcome fellow Null-Byters! Sorry for the delay, this time of the year can be hectic for all of us. Hopefully this will not happen again. In this "tutorial" we will go over more styling and make our page look even better!
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...

Regardless of your culture or your age, eating with your hands is fun. Flouting social convention and just digging in with your fingers provides a whole other level of epicurean enjoyment. And one of the most entertaining hands-on foods is monkey bread. Food historian Tori Avey provides a comprehensive history of the origins of this pull-apart treat, including the important detail that no actual monkeys are involved in the making of monkey bread. Originally a savory culinary creation from Sou...

Hello All, So to recap in part 1 I went through setting up the dchp server. Part 2 detailed the bash script. Now in part 3 I will post the entire bash script. I am doing this in its own post because Part 2 is just way to much info on one post IMO.

I held the orange packet in my hands and presented it to my friend, Seth, as though it were a plastic-wrapped jewel—rather than three ounces of dehydrated noodles.

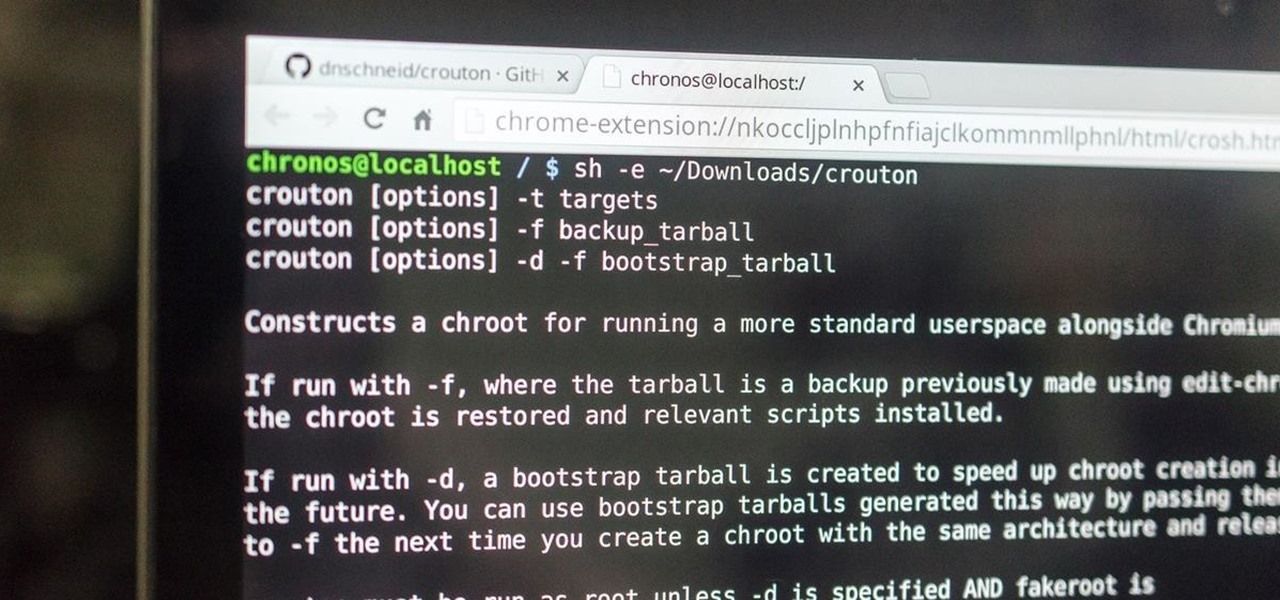
This is my first how-to for this site so feel free to let me know if I can somehow improve! Inspired by the great Jailbroken iDevice and Rooted Android PenTesting tutorials I decided to share how I use my Toshiba Chromebook 2 with Kali Sana.

CEO's of IT companies doesn't know this because they are not a hacker. Only a true hacker can become a successful Security head officer.

Amazon thinks that by simply removing an app from their Appstore, that they will stop users from accessing it. But with Android OS powering their Fire TV Stick and Fire TV, there really isn't anything they can do to prevent us from sideloading an APK onto the streaming media devices.

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.

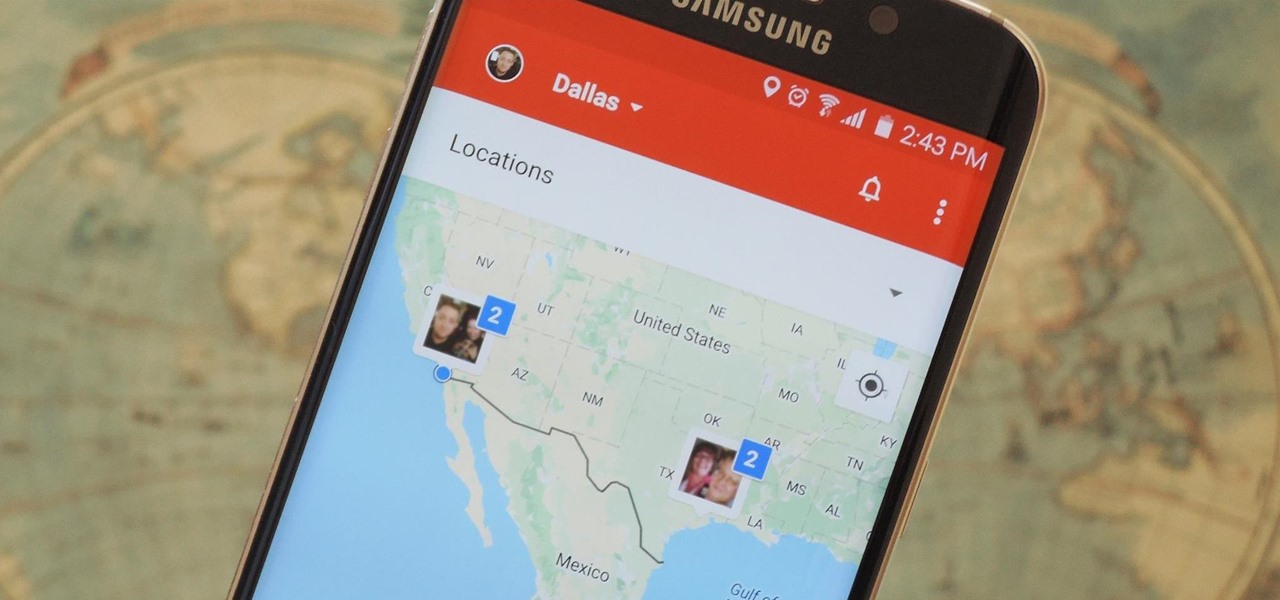
Instead of wasting time asking where your friends and family are at a given moment, then having them waste time by describing their location, there are several Android apps you can use that will automate this whole process. To top it off, it doesn't have to be about invading privacy or spying on someone, since most of these apps are offer two-way location sharing, or at least let you share locations only when you feel comfortable with it.

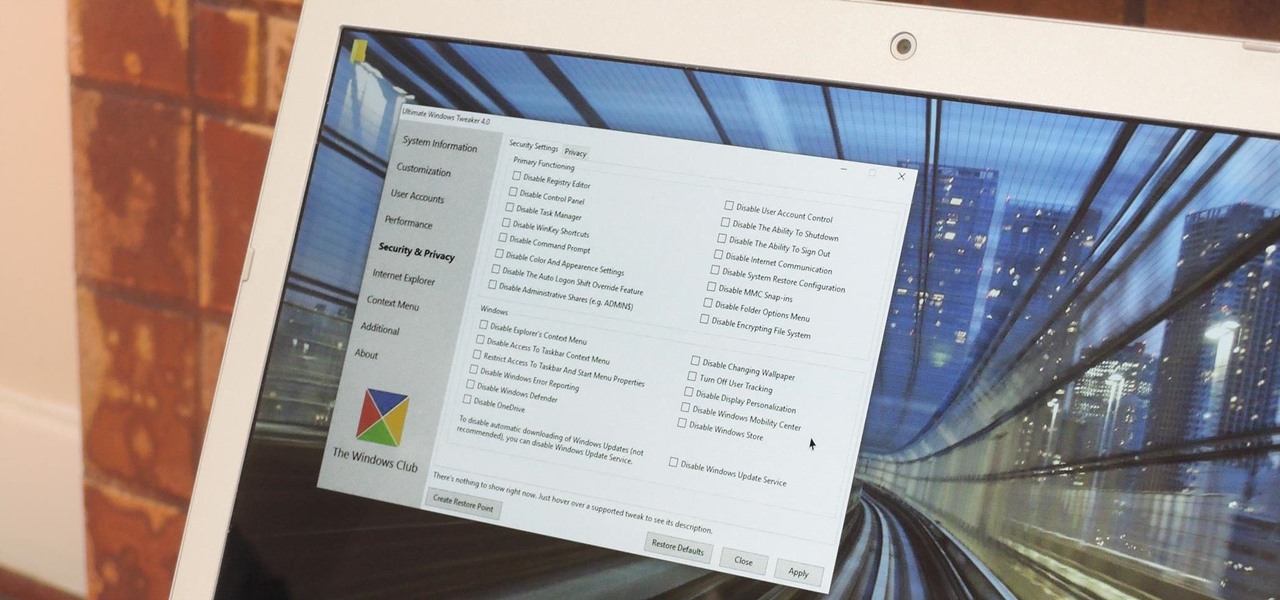
Every time Windows gets a significant update, the vast majority of existing tweaking utilities become obsolete. For every option that you fine-tuned with one of these tools on Windows 7 or 8, there's a change in the registry or system settings that cause your tweaks to now point to a dead end. This was definitely the case with Windows 10, since there were so many sweeping changes that very few existing options carried over.

Depending on your child's age, their first smartphone may be a little too open for them, or you, to handle. With essentially a world of information—both good and bad—available at their fingertips, it can seem like a huge hurdle to instill parental controls on their device.

Welcome back, my rookie hackers! As most of you know, Mr. Robot is probably the best hacker TV show ever! This is a great show about a cyber security engineer who is being enticed to hack the very corporation he's being paid to protect. This show is so good, I began a series to demonstrate how to do the hacks he uses in the show.

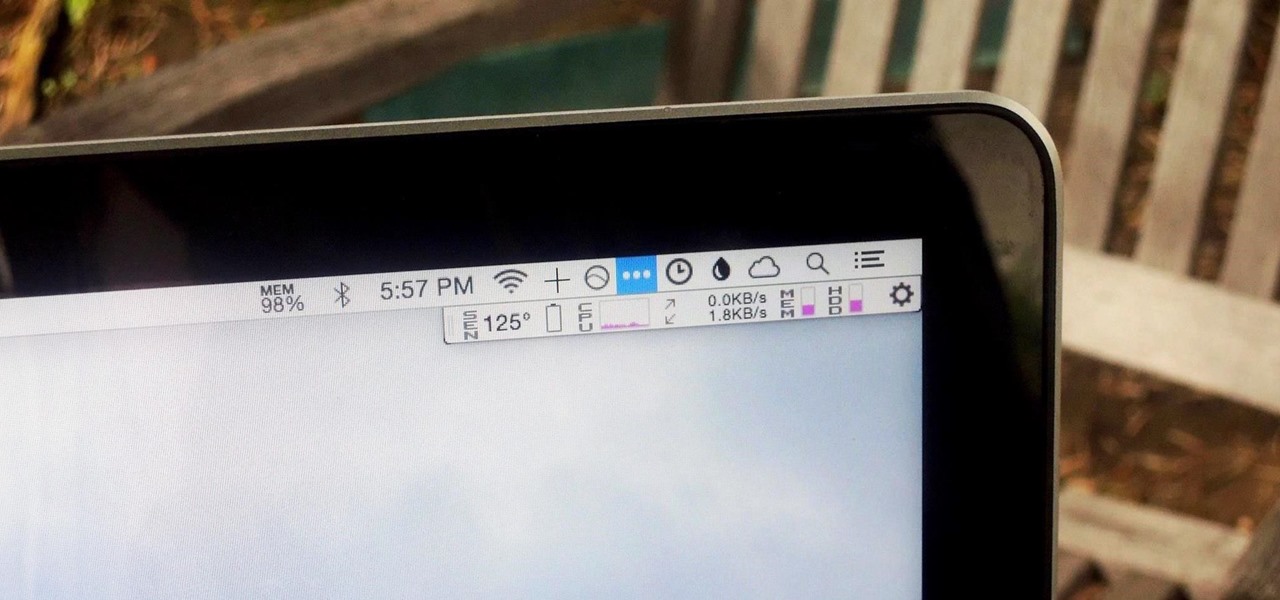
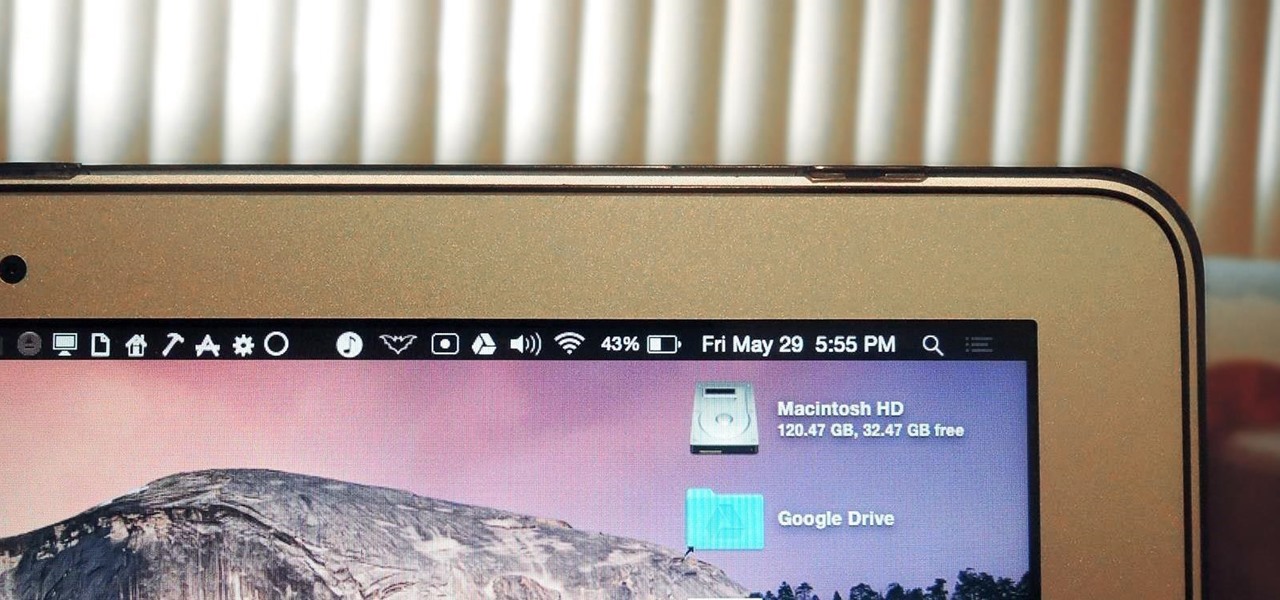
We recently showed you 8 menu bar apps that ever Mac power user should have, covering apps that allow you to control iTunes, eject drives, organize screenshots, and more—all from that tiny strip at the top of your screen.

If you remember last time, we successfully uploaded picture with a small hidden PHP command executer embedded in it onto a server. Now, our goal is to take this a step further and get an interactive shell. To do this, we need to upload another file that either binds a port for us, or connects back. For this tutorial, we will use a Python reverse Meterpreter shell.

Heads up! We've done a new, more thorough review of the best Android file-sharing apps. You can check that out here. Our old file-sharing app roundup can still be viewed below for posterity.

We recently lost Grooveshark, the free music streaming service that supplied users with a huge catalog of free music anytime, anywhere. Since its shutdown, I have been scrambling to find a half-decent alternative, and my expectations were more than exceeded when I found NetEase Music.

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

The menu bar is a great place to perform quick searches, track battery life, and switch Wi-Fi networks on your Mac, but it can do way more than that if you let it. I've rounded up some menu apps below that not only have features that will boost your productivity, but are lightweight enough to run entirely from the menu bar.

Welcome back, my rookie hackers! In my ongoing attempts to familiarize aspiring hackers with Linux (nearly all hacking is done with Linux, and here's why every hacker should know and use it), I want to address a rather obscure, but powerful process. There is one super process that is called inetd or xinetd or rlinetd. I know, I know... that's confusing, but bear with me.

Most of the time we only use the microwave to reheat or defrost, but you can actually save a lot of time by using it for cooking. These genius recipes make the most of this underused appliance, and also turn out some pretty tasty dishes.

Technology has progressed by leaps and bounds and has blessed people in a number of ways, but at the same time, it has troubled them also. Computers are now used in every aspect of life. No matter if you are a businessman, an employee, a student, or even a housewife, a computer can assist you in your routine work. You save your personal information, documents, and other similar sensitive stuff on your computer that can hurt you if they get compromised.

Welcome back, my tenderfoot hackers! Now that we have begun this trip down web app hacking lane, we need to first address target reconnaissance. Like any hack, reconnaissance is critical. (Are you tired of me saying that yet?)

HTC's Sense UI is generally regarded as one of the best manufacturer-skinned versions of Android. This is mainly due to the subtle and classy styling of the interface, as well as some unique features that are added in here and there.

The Nexus Player is one of the most robust set-top streaming devices on the market. This is mainly due to the fact that the base software it runs is a direct fork of Android, which is a very powerful operating system itself.

There are so many cutesy pink, red, and heart-shaped desserts and drinks put out on Valentine's Day, but none of those really get you into a low-light mood. Instead, turn up the heat with one of these aphrodisiac cocktails for grown-ups.

Oops... did you forget to connect to a Wi-Fi network before streaming HBO GO on your iPhone? While those episodes of The Wire may have been absolutely life-changing, your three-digit cellular bill is definitely going to hit you a little harder.

Christmas is just around the corner, which means holiday wreaths are decorating many doors across the nation. While we're always fans of a practical DIY, we especially love the edible kind, which are great for last-minute decorations.

There are those who prefer Thanksgiving leftovers to the actual official meal, much like people who prefer cold pizza over hot. I'm definitely in the latter camp. There's something luxurious about enjoying your perfectly cooked turkey and stuffing while wearing sweatpants and not having to make small talk with your weird uncle who drinks too much.

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.