The creation of private browsing was brought upon by the backlash against ad tracking and other ways that sites and agencies take away users' privacy online. People were tired of getting spammed with ads for Vitamin C pills simply because they visited WebMD. Private browsing is now built into all of the major browsers and is used frequently. While private browsing is more infamously known as the "Porn Portal," and does prove to be a great way of keeping racy content out of the sight of others...

The new iPhone 5 was just revealed yesterday, and it's 18 percent thinner and just 1/5 the weight of its 4S predecessor. It's also taller with a larger screen, which gives you a fifth row for apps now. As far as speed is concerned, it has a speedy A6 chip and can tap into wireless 4G LTE networks for fast Internet. Both the iSight and front-facing FaceTime cameras were improved, too. The only downside seems to be the tinier "Lightning" connector, which replaces the standard 30-pin connector w...

All kinds of people pretend to be someone they're not on the internet, including scammers, people attempting to wind others up, hackers and web predators. Almost all of these people will leave bases uncovered and they're all easy to expose when you understand how to. Here are my favorite ways of finding out when somebody is lying quickly. Image Search

A few days ago, Russian hacker Alexy Borodin found a way to get free in-app purchases on an iPhone or iPad. In-app purchases include things like items and power-ups for iOS games, as well as subscriptions and "premium" memberships for certain apps.

This weekend, hackers broke into the servers of the popular shoe shopping site Zappos, giving them access to the personal information of 24 million Zappos customers. The user data taken included names, email addresses, billing and shipping addresses, phone numbers, the last four digits of credit card numbers, and encrypted passwords. However, full credit card data was not lifted, and passwords were cryptographically scrambled.

Building a DIY Alarm System: The Concept So, you want to protect your property, or maybe a room, car, or even your backyard. The concept of an alarm system is to notify the "alarm administrator" that there is an intruder entering the previously designated boundaries. The triggers for this boundary could be as simple as a pressure sensor, or as complicated as a laser network. They all do the same thing, but some work better than others.

Need a hair lift in IMVU? No problem, get some bad hair day advice with this vid. You just need a little Photoshop skills to get your IMVU avatar looking good.

How to sign up for a Myspace profile. The simple steps necessary to belong to this network. Part 1 of 14 - How to Sign Up for a Myspace Profile.

Fabulous and creamy, make this scrumptious low-country carb stew. Follow along as Paula Deen shows you how to make it. This cooking how-to video is part of Paula's Home Cooking show hosted by Jamie Deen, Paula Deen. Paula Deen, owner of Lady and Sons, a famous Savannah restaurant, is Food Network's resident southern chef. Step inside her kitchen and discover delicious food that's both uncomplicated and comforting, like this recipe. Watch how easy this low-country crab stew is to prepare and c...

You might have missed it, but the virtual keypad you use to enter phone numbers in your smartphone's dialer and contacts app isn't all numbers. Take a closer look, and you'll notice a few mysterious buttons you've likely been tuning out unconsciously. But it's time to stop ignoring them because each has a particular purpose that could come in handy one day.

You no longer have to resort to a third-party email client on your iPhone to schedule messages to send whenever you want. Apple built the scheduling functionality into its Mail app, and it works with any email service you use in Mail, whether that's iCloud, Gmail, Yahoo, Outlook, or another service.

There are many things your iPhone or iPad can do, and Apple does an excellent job of documenting everything on its website. But there are some features that won't show up in any Apple manuals or help pages.

With the holidays right around the corner, it's easy to miss a big software update on your iPhone, and by that, I mean iOS 15.2, which was pushed out Monday, Dec. 13. There's a surprising amount of new features and changes in the updated firmware, and there are a few big ones you need to know about.

"Unfortunately, no one can be told what the matrix is, you have to see it for yourself." That's the line just before Morpheus gives Thomas Anderson (aka Neo) the red pill, finally opening his eyes to the tapestry of code that has veiled his eyes for his entire life.

Apple released the fifth iOS 14.7 betas to developers and public testers today, Thursday, July 8. The update appears to be minor, adding new splash screens when opening Reminders and Podcasts for the first time.

If you've ever wanted to start learning to code but haven't known where to start, then one of the best places is with Python. It's great for introductory programmers, and it's also a must-have addition to the repertoire of anyone experienced in the industry. As of 2019, over eight million programmers have used Python, and the industry has only grown since then, so the best time to start practicing is today!

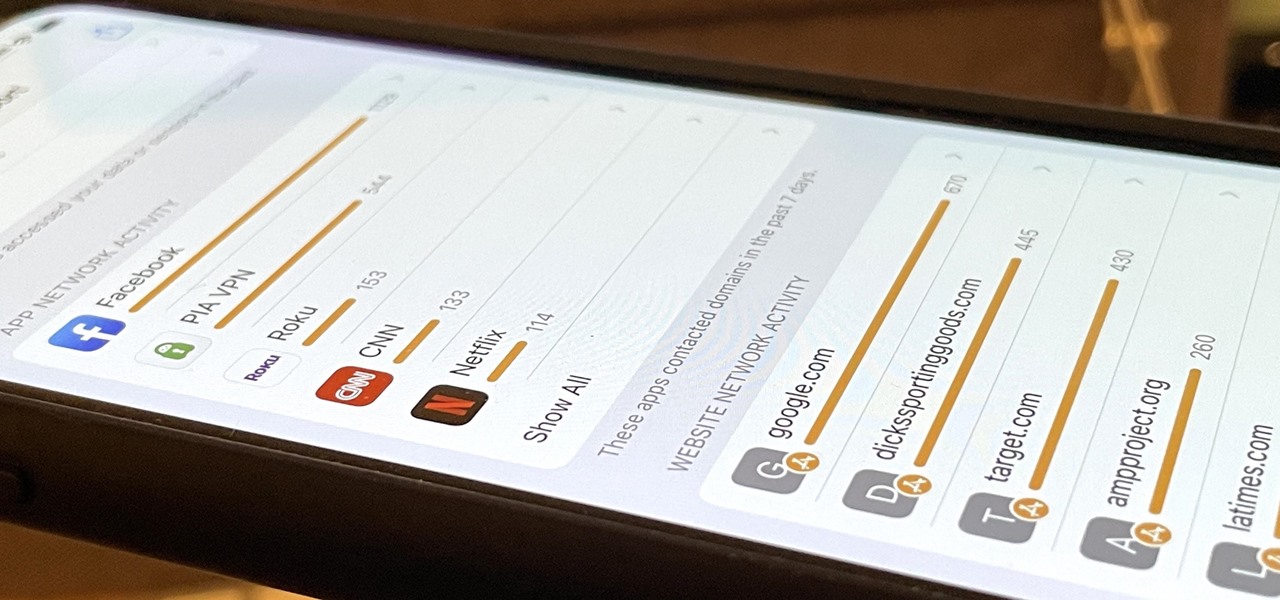
The ability to browse the web in coffee shops, libraries, airports, and practically anywhere else you can imagine is more than convenient, but convenience has risks. Using public Wi-Fi allows others to spy on you easily. Even your own internet service provider can see every website you've ever visited. Don't fall into the trap of protecting your identity, data, and devices after it's too late.

Apple released the second Release Candidate for iPhone on Friday, May 21. The new update, build number 18F72, comes four days after the company seeded the first 14.6 RC to developers and public testers, and two days after the first beta for iOS 14.7.

Apple pushed out the Release Candidate for iOS 14.6 on Monday, May 17. The 18F71 build includes new features and bug fixes, including an option to unlock your iPhone with Voice Control. It comes just hours after Apple announced Spacial Audio and Lossless Audio playback for Apple Music, new features that will require iOS 14.6 to run.

It's Earth Day, which means that nonprofits, individuals, and brands are making a concerted effort to raise awareness of environmental issues and how to change behaviors to reverse impacts of pollution, deforestation, and suburban sprawl, among others.

If you buy an Android phone from any of the big US carriers, it will come with several extra apps in addition to any apps the manufacturer preinstalled. It's all in the name of profit, of course. Some of these apps are from companies that paid the carriers to distribute their software, and some are from the carriers themselves, usually aimed at upselling you or perhaps collecting a little data.

Screen mirroring software has been around for ages, allowing you to mirror your iPhone to a projector, laptop, TV, or another device. It's useful to have during lectures, presentations, and meetings, so it's no wonder why Apple created its AirPlay technology. However, AirPlay doesn't work in all situations.

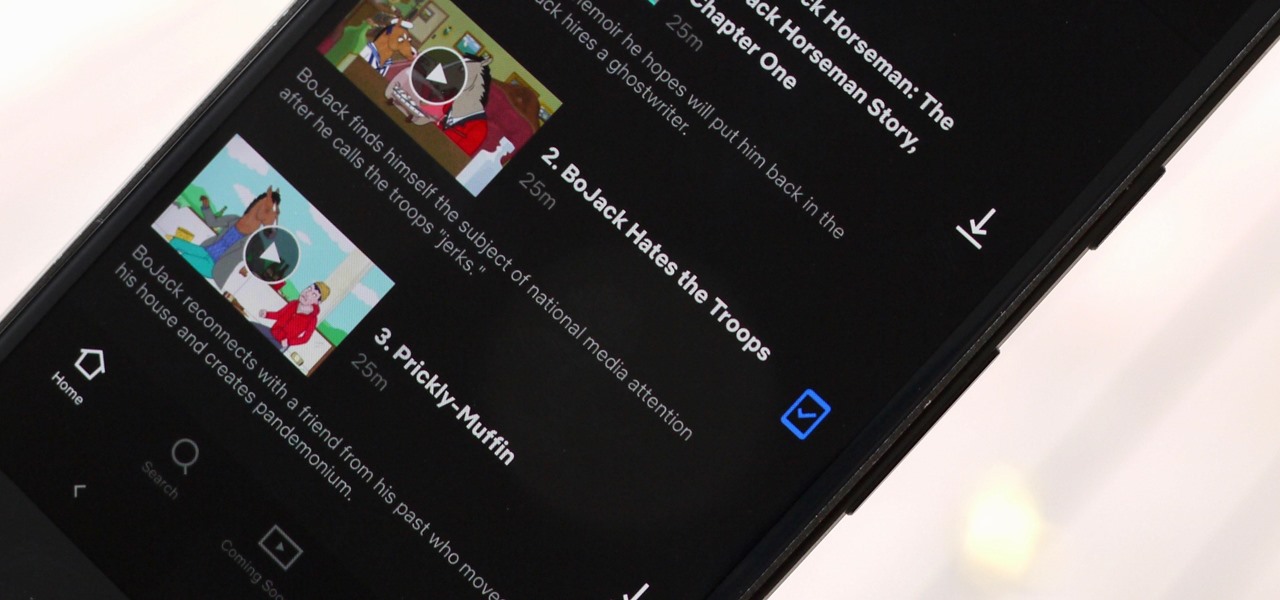
One of the most convenient features in the Netflix app is the ability to download movies and TV shows to your device, which lets you avoid potential streaming issues and watch content offline whenever you want. To make downloading even more convenient, you can automatically download new episodes of your favorite TV shows once you've finished the ones already stored on your phone.

Your sensitive personal data should be strongly protected, and it's never more vulnerable than when you are online. The internet connection is a prime avenue of exposure, and email is one of the least secure forms of communication. Fortunately, there is an easy solution to both of those problems.

Samsung's One UI 3.0 skin is built on top of Google's Android 11 open source code base, which means you get all of the standard features, plus some cool bonus stuff from Samsung. However, it's one of those standard AOSP features that you might find most useful if you send a lot of ADB commands.

The USB Rubber Ducky is a well-known hacking device in the cybersecurity industry, but it needs to be preprogrammed before it can be used. That means it's not easy to issue commands to a target computer since you can't interact with it from afar after plugging it in. And if you don't know what the target computer is, you might come up empty. That's where the WiFi Duck comes in handy.

Google TV gives the new Chromecast a home screen full of curated content from your various streaming subscriptions, but it's just that — a home screen app. Underneath, Google's new dongle is running Android TV, meaning its home screen is just a launcher that can be installed on countless other TVs and set-top boxes.

Amazon Web Services (AWS) is the premier on-demand cloud computing platform. Offering a wide range of APIs to companies, governments, and individuals on a pay-as-you-go basis, this Amazon subsidiary pulled in over $35 billion in revenue in 2019 alone.

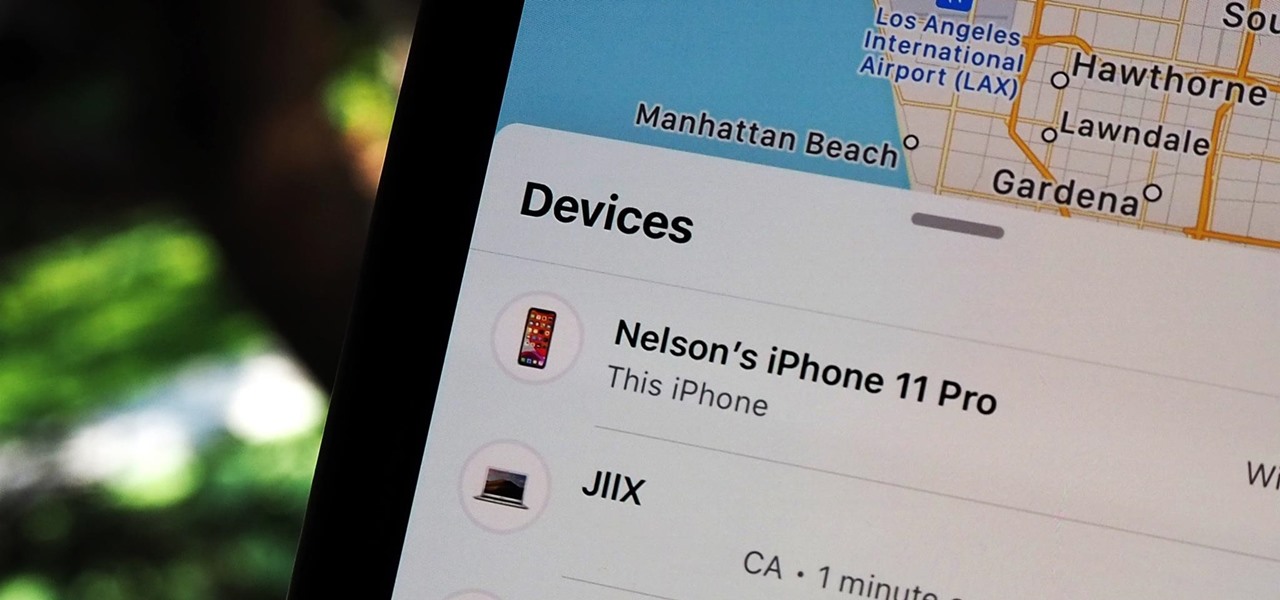
You might be giving out your name to every stranger you see, and you don't even know it. That iPhone of yours has a name — generally a combination of your first name and device model — and it broadcasts it to others via AirDrop, Personal Hotspot, Bluetooth, Wi-Fi, and other connections. Sure, it's useful to keep your device name simple and to the point, but there are upsides to changing it.

If you're an aspiring or even well-established web or app developer, the good news is that there's a virtually limitless number of lucrative opportunities waiting for you, regardless of whether you're looking to work for a company or as a freelancer.

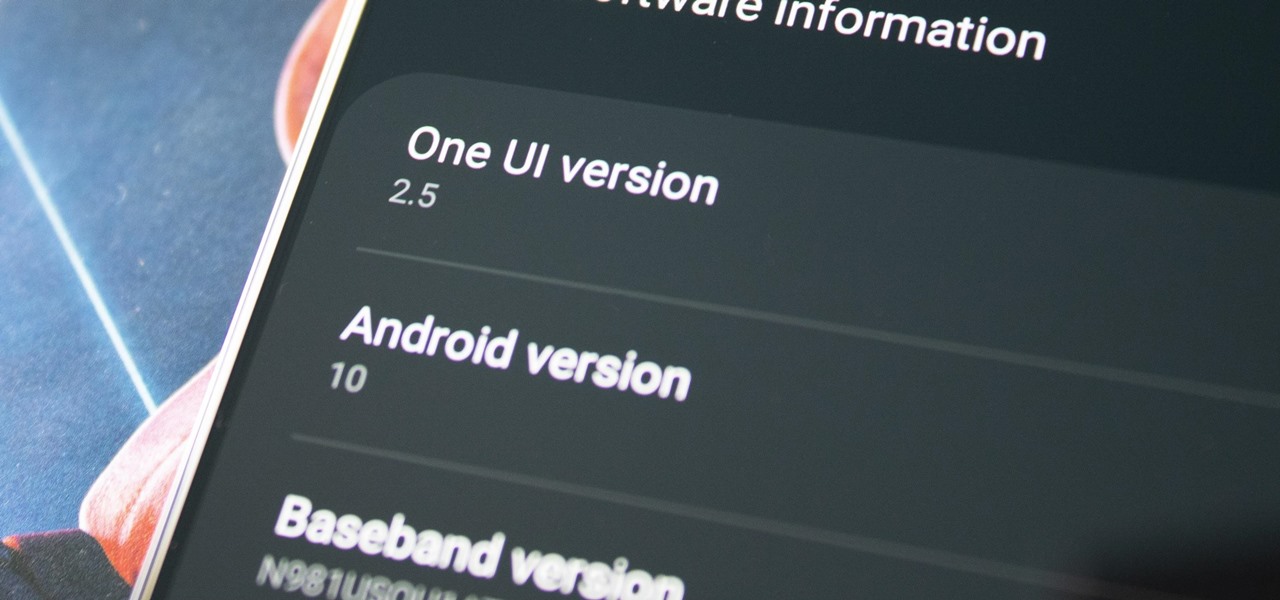
Samsung's One UI has slowly become the model for Android skins. The old iOS-like TouchWiz already feels like a relic, thanks in part to the newer user interface's exceptional design and fast but meaningful updates. One UI is so good, other OEM skins have copied elements of it. The latest release is One UI 2.5, which has over 20 new features that make the skin even better.

If you're ever in a situation where you need to take a peek at the wireless spectrum, whether it's for Bluetooth or Wi-Fi devices, there's a fascinating Python 3-based tool called Sparrow-wifi you should check out. It's cross-platform, easy to use, and has an impressive GUI that shows you the signal strength of nearby devices.

Many apps on your iPhone want to use your location, most of which are for valid reasons. But some apps can function perfectly fine without location permissions, while others have no business even requesting it. If you want to be more selective about which apps and services you give away your coordinates to, the best thing you could do is start from scratch.

The Internet of Things (IoT) is changing everything in our homes and at work, from security systems and lighting fixtures to smartphones and speakers. An estimated 50 billion devices are now hooked up to IoT.

In a world that's becoming increasingly dependent on a variety of AI and machine learning applications, Big Data reigns supreme. As the primary forces behind everything from self-driving cars and surgical robots to home automation systems and even space exploration, Big Data and AI stand at the heart of today's most important innovations.

No longer strictly relegated to the realm of science fiction shows and novels, artificial intelligence can be found behind important technologies that are driving innovation throughout the world. From space exploration and self-driving cars to data science and marketing algorithms, AI is the driving force behind many technologies that are moving humanity forward.

More information is available to us now than ever before. We simply cannot make sense of so much data on our own. Thankfully, we have programs to do the heavy lifting for us.

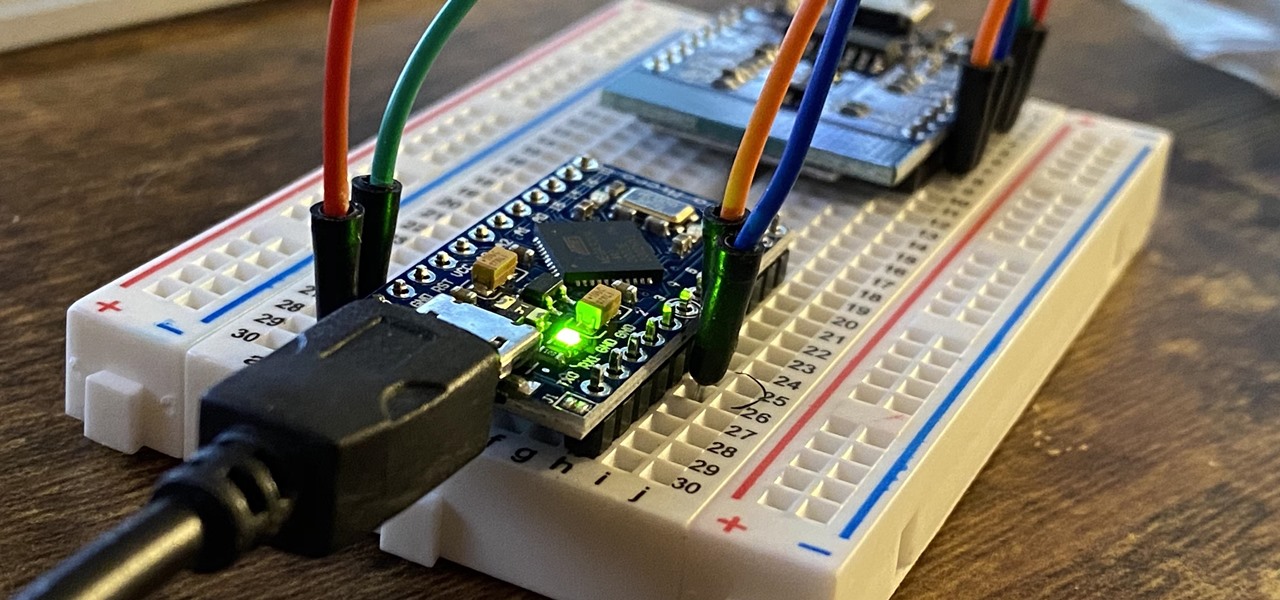
The only thing better than programming MicroPython is programming MicroPython over Wi-Fi. So once you set up MicroPython on a microcontroller and have it on its own power source, you won't need to use a data cable to connect to it whenever you need to interact with it, program it, upload files, or grab data.

If the interconnected worlds of blockchain, Bitcoin, and cryptocurrencies scare you a bit, you're not alone. Thanks in part to the extreme and seemingly random fluctuations in the value of Bitcoin over the past three years, more than a few developers and investors are wary of the cryptocurrency revolution and its ties to blockchain development.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.