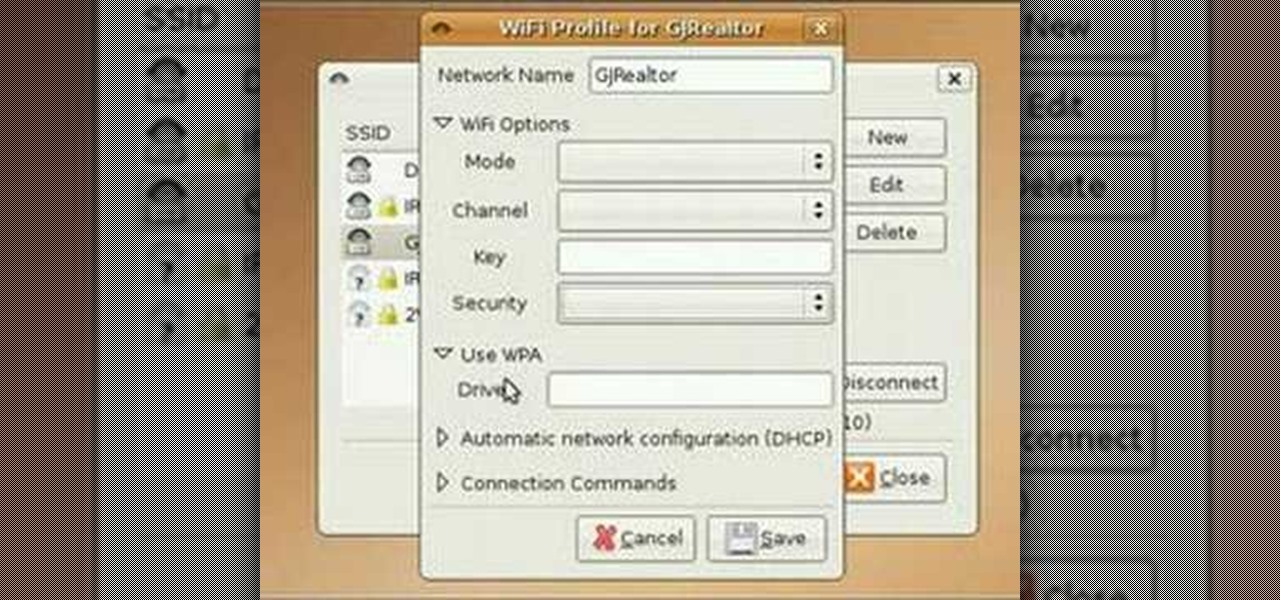
Not only can your T-Mobile G1 phone get Internet access by itself, you can also use it as a router or modem for your home wifi network. All you need is to download a single app from the market, install it, and you're ready to set up your home wifi network!
Go to Cydia and add a new source http://Cydia.xselize.com. Now search there for supreme preferences and install it.
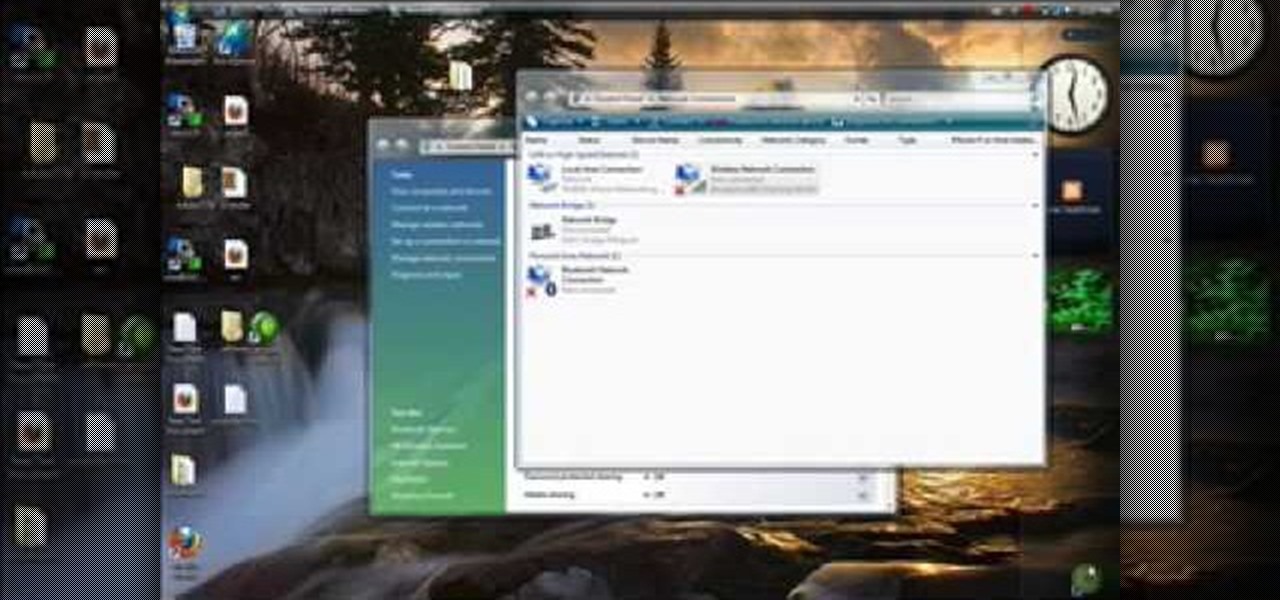
This tutorial gives a start to finish explanation of how to make an Internet Wi-Fi router with Windows Vista. With real time computer screen video and narrative, it is easy to follow along at home.

Google G1 users, want to switch your phone network? In this video, learn how to unlock the Google G1 HTC Dream Phone. All you need to complete this tutorial is your phone and a SIM network unlock pin code.

Just because you are using Linux, doesn't mean you have to be cut off from file sharing with those using a regular Windows PC. In this tutorial, learn how to share files between Ubuntu and Windows using a Samba local network. Samba is simple to use and can be obtained through your Synaptic package manager.
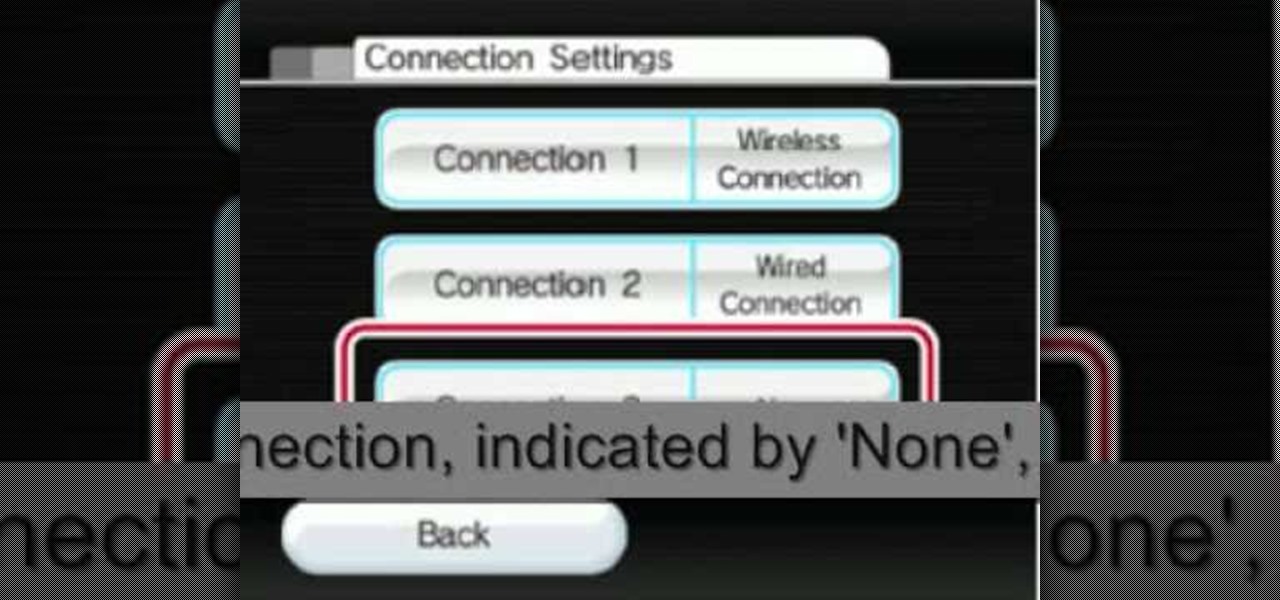
The video shows you how to connect the Nintendo Wii to an available wireless network. First, you have to turn the Wii on. When the menu screen appears, you then click on the "Wii button" in the bottom-left corner. Next, go to "Wii Settings". On the following screen, you have to use the blue arrow on the right to go to the second page of options and select "Internet". Go to "Connection Settings" and click on an "Open Connection". From here, go to "Select Wireless Connection" and then "Search f...

Take one end of the Ethernet cable and plug it in the back of the XBox, the other end of the cable you have to plug on your computer. On your computer go to Start and then go to My Network Places, now select View Network Connections. Right-click the Wireless Network Connection, and go to Properties. Select Advanced tab on top of the window and make sure the two boxes are checked, press OK to continue. Now turn on your XBox and go to Test XBox Live. Wait until the test ends and then you will b...

In this video tutorial, you'll learn how to use the WiFi Radar application to find wireless networks while running the Ubuntu Linux distribution. For more, and to get started finding and using wireless networks in Ubuntu for yourself, take a look!

A tutorial showing how to set up a free dynamic DNS address with DynDNS.org and configuring the home router/firewall to forward traffic to your webserver.

This is the second episode of Full Disclosure by InfinityExists.com. This episode includes how to crack WEP encryption, and why it can be cracked so easily.

When you look at the top corner of your phone, what do you see? Upon upgrading to Android 11 or iOS 14, you'll see either "5G," "5G+," or "5G E" if you're connected to the right network. But what exactly do these symbols mean? They indicate not only if you're using 5G, but also what type you're connected to.

5G is undoubtedly the future of mobile networks, and there's a good chance your next phone will have it. But just like with 4G, as carriers race to get the best 5G coverage, the ones running behind are abusing marketing terms to make themselves seem further ahead than they actually are.

When learning Wi-Fi hacking, picking a compatible Wi-Fi network adapter is the first step to learning to crack Wi-Fi passwords.

For the most part, Google Wifi and Nest Wifi systems take care of themselves. But there are still a few manual features that might come in handy, like being able to check on network activity to see which devices are using the most bandwidth when your connection gets bogged down.

Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.

Public Wi-Fi networks that have a captive portal sign-in screen can sometimes be broken on Android. This seems to happen randomly and on some devices more than others. You'll get the "Sign into Wi-Fi network" notification, but it just doesn't work. If that's happening to you, you'll be glad to know an app can help fix the issue.

Giving up your Wi-Fi password can be giving up more control than you think. Because of the way Chromecast and other IoT devices communicate, anyone on the same Wi-Fi network as your device can often make it do whatever they want. With a script called "Cast All the Things," we can hijack a Chromecast to play nearly any kind of media with a single command in terminal.

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

When Pokémon GO developer Niantic launches its Real World Platform for augmented reality gaming, it will run over 5G speeds courtesy of T-Mobile parent company Deutsche Telekom and the edge servers of its MobiledgeX subsidiary, the companies announced today.

The new iPhone XS and XS Max have more issues than just their hefty price tags. Customers have only had the phones for a handful of days, but some are already complaining of cellular and Wi-Fi connectivity issues on both models. If your experience is the same on your XS or XS Max, there are steps you can take to get your iPhone reliably back online.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

As Android bug bounty hunters and penetration testers, we need a properly configured environment to work in when testing exploits and looking for vulnerabilities. This could mean a virtual Android operating system or a dedicated network for capturing requests and performing man-in-the-middle attacks.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

Research group OpenAI, a research institute co-founded by Tesla CEO Elon Musk, says it is possible to trick driverless cars' neural networks into mistaking images for something else.

If you're on T-Mobile, you've probably had a rough morning. Reports are coming in saying that the carrier's LTE network is down in cities throughout the country.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

Last week, T-Mobile CEO John Legere got salty. He announced ever so cheerily T-Mobile's intentions to release the first true 5G network in coming years, all while gaily smacking AT&T around for their bogus "5G Evolution" reveal. But could Legere be wrong to say T-Mobile will be the nation's first 5G carrier? It looks as though that title may have to be shared with Sprint ...

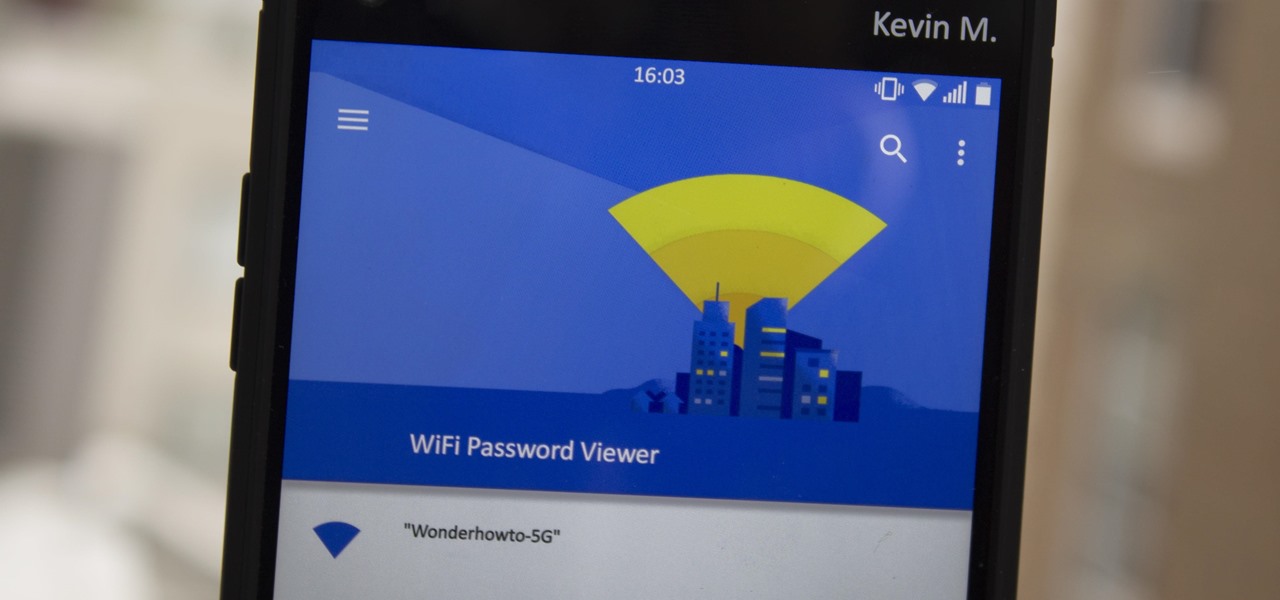
Have you ever gone to a friend's house and not asked for the Wi-Fi password? Probably not, and the same can likely be said of any friends that come over to your place. But the actual act of sharing Wi-Fi passwords is still incredibly clunky, and it's particularly hard if you have a nice and secure password with uppercase and lowercase letters, numbers, and symbols.

John Legere seems to operate under the philosophy of, "If you're going to be late to the party, throw a better one." On Tuesday, Legere announced T-Mobile's intention to build the nation's first true 5G network, following AT&T's rollout of its "5G Evolution" network. A network which many said was, to put it in polite words, nonsense.

Google's new Project Fi cellular carrier has been making waves across the mobile industry, so we decided to put it to the test against T-Mobile, one of the more established networks. For the actual testing, we slapped a SIM card from each carrier into two identical Pixel XL phones, which offer full compatibility with both networks.

Hello everyone! How's subnetting going? Did you practice a lot? I hope you did, but even if you didn't we will go through some more examples so you can be feeling confident after reading this article. It's all about that bad boy binary!

Keeping your online data and identity private is an uphill battle, but with the anonymity network Tor, you have a pretty decent line of defense from prying eyes.

Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you how to spy on somebody's Internet traffic.

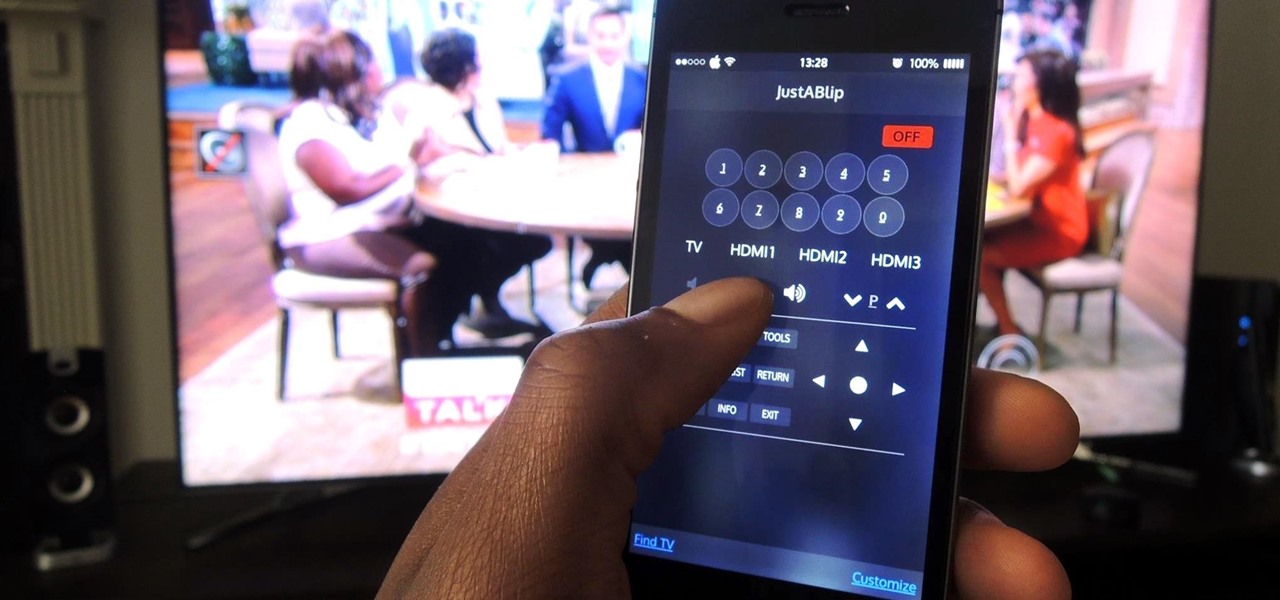
After I traded in my Samsung Galaxy S5 for an iPhone 5S, the one feature I truly missed was the Smart Remote app. My television remote was broken and the S5 saved me from, you know, actually having to get up and change the channel.

Android Debug Bridge, or ADB for short, is a very powerful utility that can remotely execute commands on your Android device. This remote terminal interface, however, is not very "remote" at all. You have to be tied down to your computer to use it, since a USB cable is normally required.

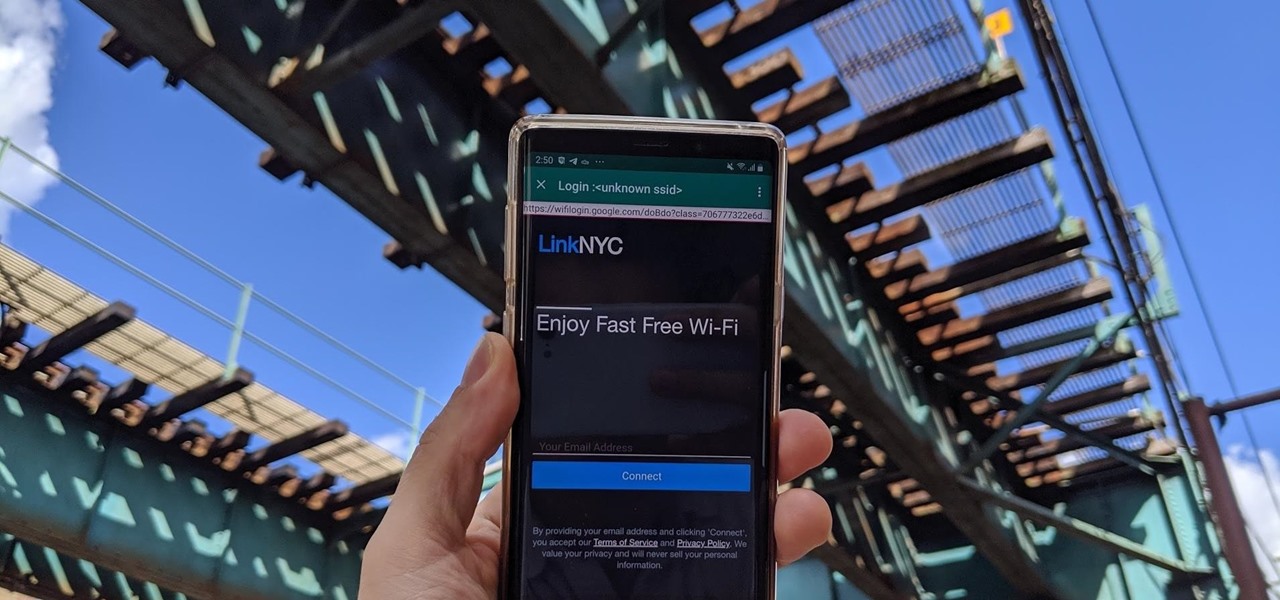
Thanks to Verizon Wireless, I pay over $220 a month for my phone bill. It's just me on the plan—no family members, and it's not even unlimited data. So, when I receive that data alert message telling me that I've used up 90% of my plan and that I've still got a few more week until my billing cycle starts over, you know that I'm left scrambling to connect to some Wi-Fi.

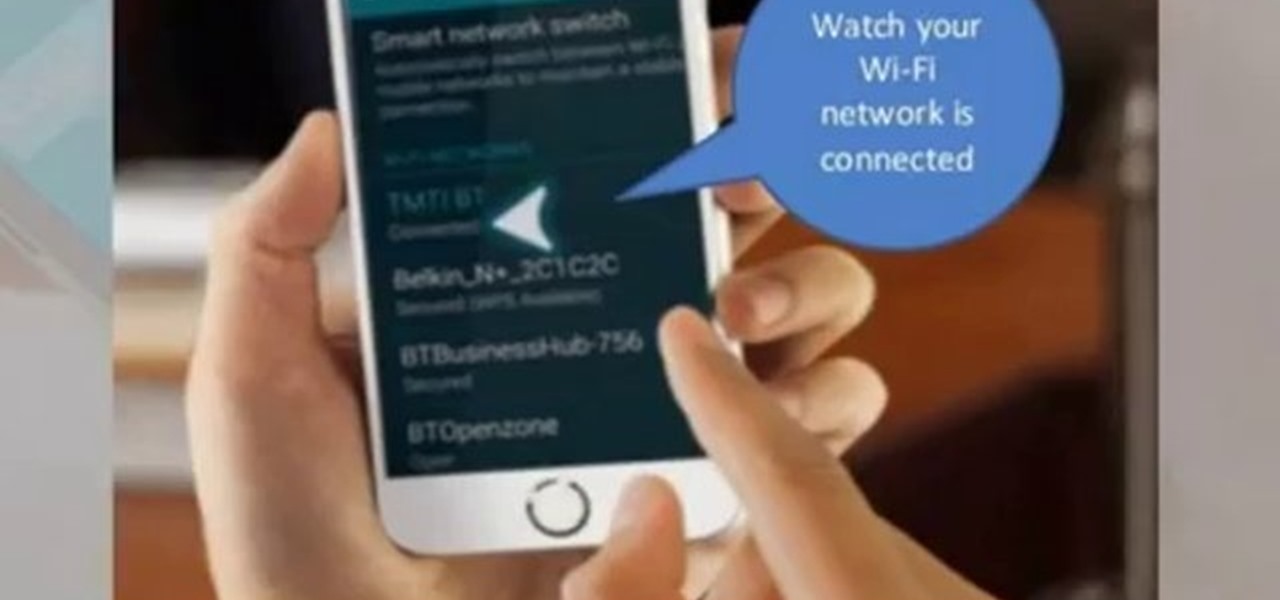
This tutorial video will show you how to connect a wifi network in your Samsung Galaxy S5. This is very easy to employ. So please watch the video. Follow all the steps to do it yourself in your Samsung Galaxy S5 phone and enjoy a wifi environment.

This video will show you how to set up a connection with wifi network in your Samsung Galaxy S5. So please watch the video and follow all the steps carefully. Employ the technique in your Samsung Galaxy S5 phone and enjoy a wifi environment.

When you're actively using your phone, a certain amount of battery drain is to be expected. But, if your device is just sitting in your pocket draining its battery, that's when you need to take action.