Samsung decided to jump into the foldable category early, announcing the Galaxy Fold in February 2019. After a major hiccup, Samsung released the phone four months later to praise. But Samsung's not finished with foldables, as the new Galaxy Z Flip is just on the horizon.

Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/WPA2 password, we'll use it to play a Wi-Fi hacking CTF game anyone can practice for less than $10.

Windows 10 passwords stored as NTLM hashes can be dumped and exfiltrated to an attacker's system in seconds. The hashes can be very easily brute-forced and cracked to reveal the passwords in plaintext using a combination of tools, including Mimikatz, ProcDump, John the Ripper, and Hashcat.
Similar to last year, LG is mixing up its releases. Instead of the G series in the first half of the year and the V series in the second half, LG is releasing both heavy hitters together. However, unlike last year, this is a true upgrade from its predecessor, the LG V50 ThinQ 5G.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

Whether you're in high school or college, you no doubt will have your iPhone in your pocket all day long. To make your iPhone last the whole time and even help you out with your studies, these are the accessories you'll want to get your hands on.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

As smartphones become more accessible, billions of people have come to depend on their features for daily life. One of the most important aspects these days is the camera. OEMs have been working for years to improve camera quality, and they seem to have finally figured it out — the best way to achieve DSLR-quality photos wasn't just with better sensors, but with better intelligence.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

Since Android is an open source operating system, that means anyone with a little know-how can download, view, and even alter its underlying code base. Manufacturers do it all the time, which is how we end up with skins like TouchWiz and Sense. But when Android's awesome third-party development community gets their hands on this code, we end up with custom ROMs like LineageOS and MIUI.

So, you're all excited you went ahead and 'upgraded' your iPhone 3G to IOS 4.0X so you could reap all the benefits of all the new features.

Fish & chips is the most popular fish meal in the country, & you can make it yourself instead of paying a fortune at your local fish eatery. The special ingredient for these fish and chips… beer.

These lovely beef short ribs with wild mushrooms and tomato are just made for a cool fall or winter night. The succulent beef short ribs are slowly stewed in the earthy mushroom and tomato sauce until fork-tender, ready to then be piled on some mashed potatoes. Dried mushrooms are easy to find in any large grocery store, and just a small amount adds tons of flavor to this short ribs recipe.

This video demonstrates how to download a game from iTunes and transfer it to an iPod. It explains how to find the game you want in the iTunes store, how to buy and download the desired game, and how to transfer it to your iPod once the game is downloaded. Download games for your iPod using iTunes.

How to transfer a ball from a wine glass to another without blowing or touching the ball.

To make the Crust, mix the flour, sugar, baking powder and salt in a bowl. Cut in the butter and shortening with a knife or pastry blender until mixture resembles coarse breadcrumbs. Stir in the iced water, a little at a time while gathering the mixture to form a soft dough.

To replace a door, refer to Lowe's do-it-yourself for a step by step guide. Replacement is not very difficult. To replace just the door, tools and material required are: a new door, hammer, screw driver, tape measure, pencil, combination square, saw horses, clamps, chisel, a door lock installation kit, a drill with bits, circular saw, level, work gloves, dust mask, safety glasses, plane, shims, cardboard, and a utility knife. Before removing the old door, take a few measurements like the widt...

Try making an Indian cuisine inspired lamb chop masala. You will want to season your lamb with a combination of yogurt and masala spices. This can then be cooked up over the stove for tender and flavorful meat.

Making this braided egg bread from scratch is worth the effort. You Will Need

Tired of squinting over your laptop? There are several ways to turn a big-screen TV into your new computer monitor and enjoy video games, web content, and photos like never before.

Learn how to do single medicine ball on the shelf crunches. Presented by Real Jock Gay Fitness Health & Life.

Ingredients 1 tablespoon vegetable oil

You thought the normal Thanksgiving turkey took forever! Wait until you try out this recipe for turkey leg confit. If you have the patience, you could make this holiday dinner one to remember. Everyone will be more than satisfied. So satisfied, that Thanksgiving will always be at your place (which might not be a good thing).

Nothing tastes better than "fried". Even lobster. Even rice. Yes, and in combination, fried rice and lobster meat in a tightly pack crusted ball of yumminess is one of the best things you can try at home for the courageous at heart. What's it called? Lobster arancine.

A diamond ring is probably one of your most prized possessions. Like most possessions, it requires care to keep it as good as new. Learn how to clean a diamond ring with the folks from Martha Stewart's REAL SIMPLE. Diamonds are made to shine! But daily wearing can result in a less-than-sparkling stone. There's no need for a professional cleaning: Polish your gem at home using common household products.
Recently, Avid announced the upcoming release of Pro Tools HD Native, and caused a lot of stir in the audio community. There’s plenty of information about this new gear out there, so I won’t drop a spec sheet on you, just yet.

Google Poly, a repository of 3D objects for use in AR and VR experiences, is the latest Google offering to fall victim to the company's habit of axing products and services, regardless of popularity.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

Apple Card has generated quite the buzz since its March 2019 announcement. The iPhone maker's new credit card pairs with Apple Wallet on your device, is simple to sign up for, includes enhanced security over other cards, has zero fees, and provides daily rewards right to your Apple Cash account. And as good as that sounds, the fine print can complicate things real quick.

TWRP is a name many are familiar with since it allows your Android device to install any custom file of your choosing. You can create a NANDroid backup to keep your data safe or even use Magisk to achieve full root access. In fact, TWRP is often seen as the gateway to modding your system for creating a unique user experience.

Motorola is a shell of its former self. In 2010, it had just released the Motorola Droid, a phone so popular it led to all Android phones being called "Droids" by non-techies. But there have been some rough years between then and now, and Motorola's latest "flagship" doesn't look like it will help get them off this path.

Hot on the heels of all the talk about Google's newest Android Q update, known as Android 10, there's a new beta to check out. OnePlus is one of the many partners that can now offer its users a chance to test the latest version early. That means you can install the newest Android Q beta right this second on your OnePlus 6, 6T, or 7 Pro just like Google's Pixel smartphones.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

To hack a Wi-Fi network, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, but you can quickly test one you already own for compatibility, and you can verify that the chipset inside an adapter you're thinking of purchasing will work for Wi-Fi hacking.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

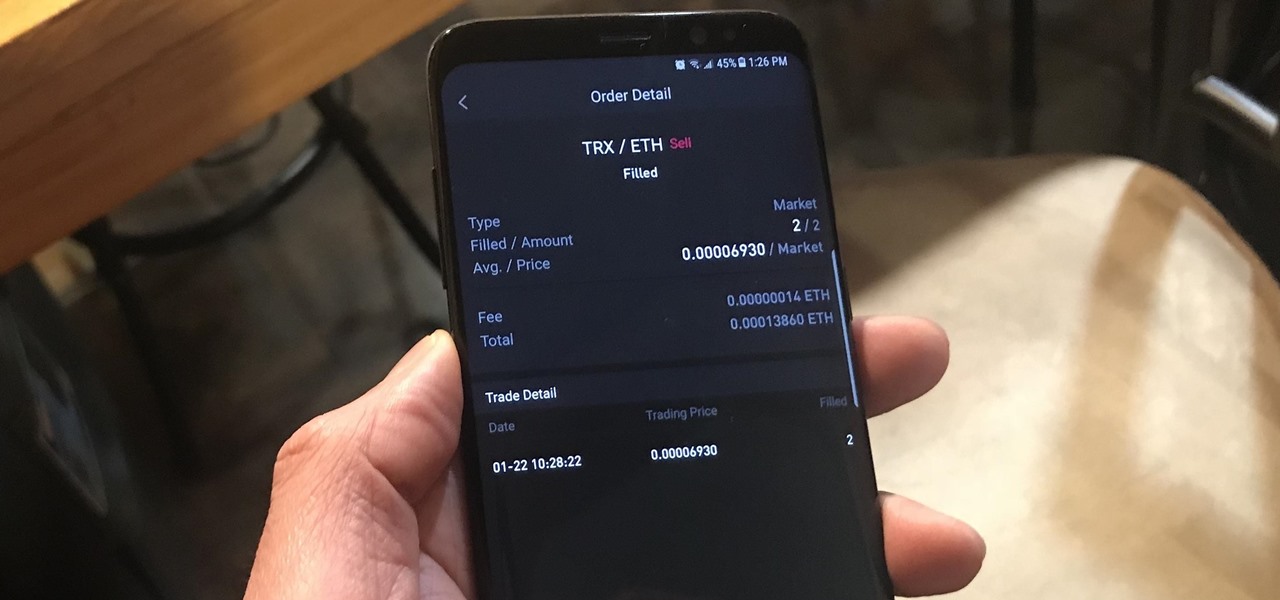
Selling alt-coins like Stellar (XLM) or Ripple (XRP) in exchange for more widespread coins like Ethereum (ETH) or Bitcoin (BTC) can be a daunting task if you're new to cryptocurrency. Though you'll still need to do your research to avoid potential disasters, Binance takes the hassle out of trading digital currencies on your smartphone.

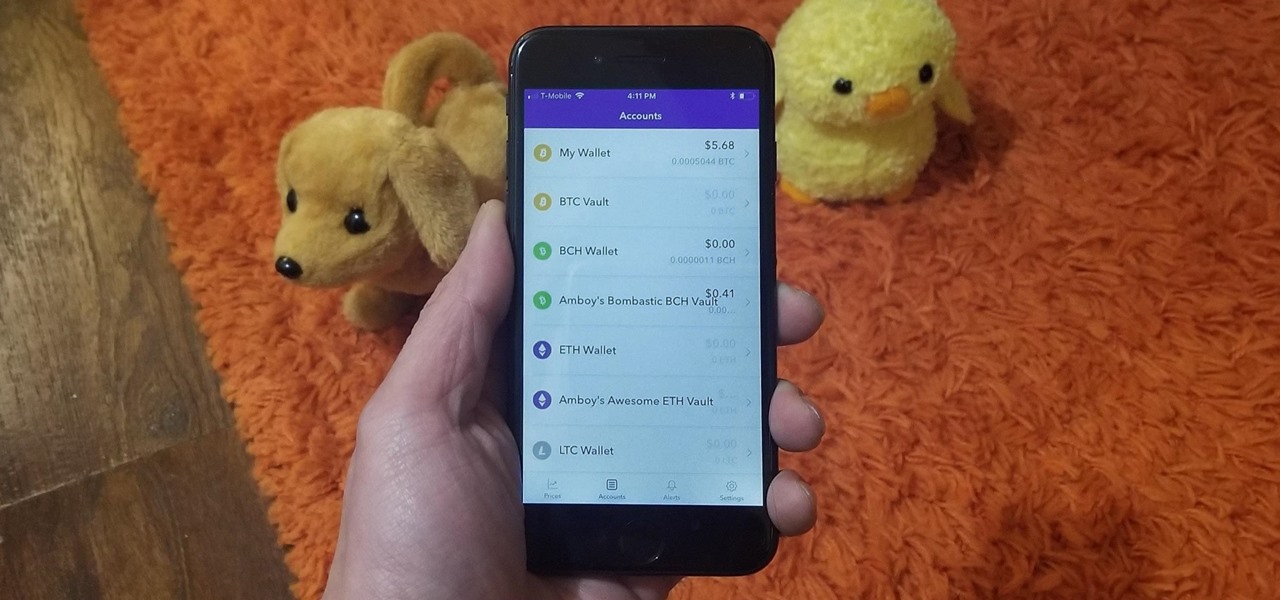
As cheesy as it sounds, #HODL became a thing for a reason. A lack of discipline when dealing with cryptocurrencies can lead to impulse buys and panic selling, and ultimately, depleted funds. Luckily, Coinbase has a way to safeguard your cryptocurrency savings to not only protect them against thieves, but to also help you resist the urge to sell off your investments.

When it comes to streaming services, Google Play Music is one of the best options for both Android and iOS. Perhaps its single greatest feature is the fact that you can upload as many as 50,000 of your own songs to Google's servers, then stream your library to any device without ever paying a dime.