
How To: Repair basement floor cracks
Tim Carter demonstrates the right way to cure basement floor cracks and cracks in other concrete floors. This is an informative, step-by-step video.


Tim Carter demonstrates the right way to cure basement floor cracks and cracks in other concrete floors. This is an informative, step-by-step video.

Dr. Michael Pound, a computer science researcher and professor at the University of Nottingham, uses hashcat and 4 GPUs in parallel to go through 1o billion hashes a second in this Computerphile video. He calls his deep-learning server the "Beast." If you're new to cracking passwords, he does a great job breaking down the process of what's going on as hashcat does its magic.

Welcome back, my apprentice hackers! In this series on password cracking, I have been attempting to develop your skills in the age-old art of password cracking. Although it might seem like a simple and straightforward exercise, those of you who have attempted password cracking know that there are many subtleties to this art.

Welcome back, my hacker apprentices! Last week, I started off my password cracking series with an introduction on the principles and technologies involved in the art of cracking passwords. In past guides, I showed some specific tools and techniques for cracking Windows, online, Wi-Fi, Linux, and even SNMP passwords. This series is intended to help you hone your skills in each of these areas and expand into some, as yet, untouched areas.

This video will show you an easy way to fix a crack in the plastic cover of your pool filter. This is a great tip that will keep the air from coming through the crack in your pool filter cover.

In this Food video tutorial you will learn how to poach an egg with Chef Meg. Heat water in a pan to 185 degrees. When tiny bubbles appear at the bottom of the pan, the temperature is right. Now add a little bit of vinegar. Crack an egg and pour it in to another bowl, never crack an egg over hot water. Now swirl the boiling water and pour the egg in to it slowly. The egg will sink to the bottom and as it cooks, it will come up to the top. This is a very moist and gentle method of cooking an egg.

Password cracking is a specialty of some hackers, and it's often thought that raw computing power trumps everything else. That is true in some cases, but sometimes it's more about the wordlist. Making a custom, targeted wordlist can cut down cracking time considerably, and Wordlister can help with that.

There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

Losing your phone is a much bigger ordeal today than it was just 10 years ago. Our smartphones carry with them lots of sensitive data that, in the wrong hands, is capable of being used for identity theft and fraud.

The reason Amazon's Kindle has become so popular over the past several years is due to the amount of digital books one can fit inside—over 1,000 for the smallest Kindle. Gone are the days of lugging around heavy books to school and the airport. Instead we can fit our e-readers snugly inside our bags and never worry about forgetting a book.

Hashes are commonly used to store sensitive information like credentials to avoid storing them in plaintext. With tools like Hashcat, it's possible to crack these hashes, but only if we know the algorithm used to generate the hash. Using a tool called hash-identifier, we can easily fingerprint any hashes to discover the right Hashcat mode to use to retrieve a password.

Welcome, my hacker novitiates! As part of my series on hacking Wi-Fi, I want to demonstrate another excellent piece of hacking software for cracking WPA2-PSK passwords. In my last post, we cracked WPA2 using aircrack-ng. In this tutorial, we'll use a piece of software developed by wireless security researcher Joshua Wright called cowpatty (often stylized as coWPAtty). This app simplifies and speeds up the dictionary/hybrid attack against WPA2 passwords, so let's get to it!

Welcome back, my fledgling hackers! In the first part of my series on Wi-Fi hacking, we discussed the basic terms and technologies associated with Wi-Fi. Now that you have a firm grip on what Wi-Fi is exactly and how it works, we can start diving into more advance topics on how to hack Wi-Fi.

Lock picking is a great skill that takes lots of practice and patience to master, but some locks simply can't be picked, like a Master Lock combination padlock. With a combination lock, you'll have to do it the old-fashioned way—cracking combinations.

Everyone who spends a lot of time outdoors will get corner skin cracks eventually, and they are ugly and painful. Watch this video for some tips on how to cure these unfortunate facts of lip life with at-home remedies and medicine.
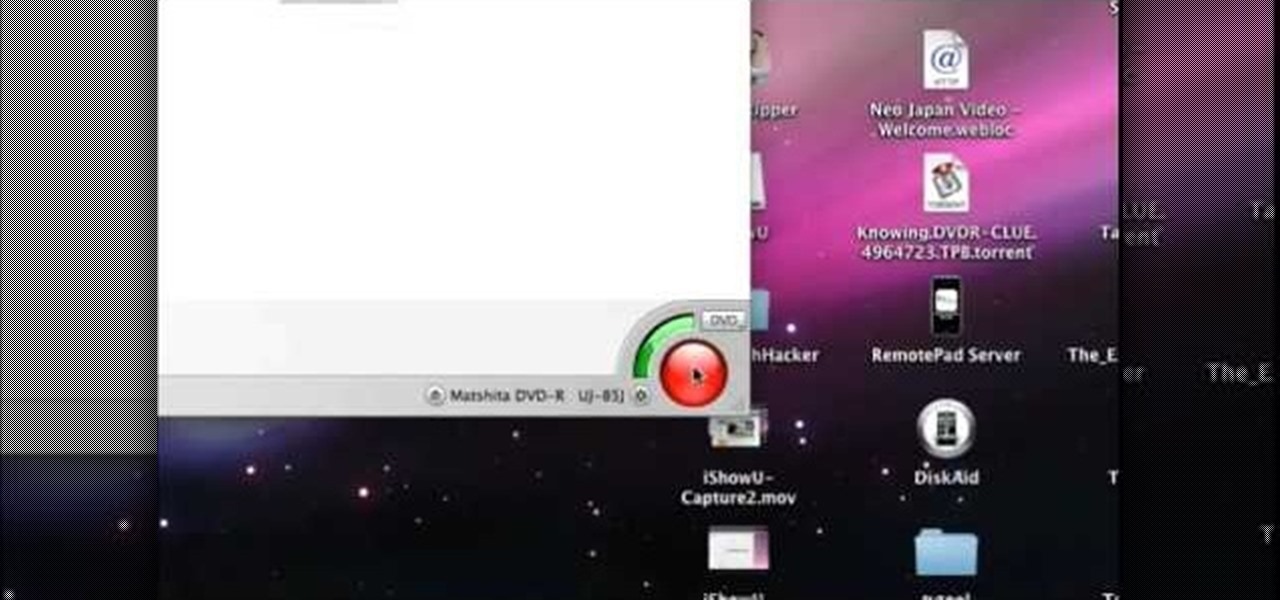
In order to copy a DVD, using Mac the Ripper, create a folder for your videos. Select the video that you want to copy from your folder. Store your copyrighted and your cracked videos in folders. A cracked video doesn’t have any of the copyrights. Use Toast Titanium, after you have a copy of your cracked video. Follow the steps that the computer prompts you to use. Insert a recordable disc. You will need to make sure that your recordable disc has enough space to hold your entire video. When ...

This how to video shows how you can use a concrete repair epoxy to repair cracks or holes in your driveway or walkway. This tutorial is great for at home DIY projects.

Vertical and horizontal cracks can mean structural problems in the foundation of your home. New carbon fiber technology can reinforce a cracked or bowing foundation cheaper and using less space than traditional methods. Watch this how to video to learn how to fix common foundation problems in your home.

Tim Carter, of AsktheBuilder.com, demonstrates how to get professional painting results by caulking all cracks between woodwork and walls.

Tim Carter, of Ask the Builder, demonstrates a few easy ways, like foundation watering, to keep the base of your house from getting structural cracks.

This is the second episode of Full Disclosure by InfinityExists.com. This episode includes how to crack WEP encryption, and why it can be cracked so easily.

Tim Carter demonstrates how to get professional painting results by caulking all cracks between woodwork and walls before painting.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.

I went to get my boat ready for the summer and discover that my engine block was cracked. I looked online to find the cost of a new block to be way out of my range so I decided to see if I could repair the cracked block. Cast iron is very sensitive to heat and I do not have the skills to weld cast iron. So I decided to see if JB Weld would repair the block or not. To discover if it worked or not, watch the video below.

Who wouldn't want to know if someone was trying to log onto their personal computer without their permission? Be it your annoying co-worker or your girlfriend, there are many cases where people may try to gain access to your desktop or laptop.

Learn How to draw Sid of Ice Age (Continental Crack-Up) with the best drawing tutorial online. For the full tutorial with step by step & speed control visit: How to draw

WPA-secured wireless networks, or WiFI Protected Access, is a form of internet security that secures your wireless LAN from being accessed by unauthorized users. Safer than WEP, or wireless equivalent privacy, WPA still has weaknesses that are prone to cracking - IF, that is, you know what you're doing.
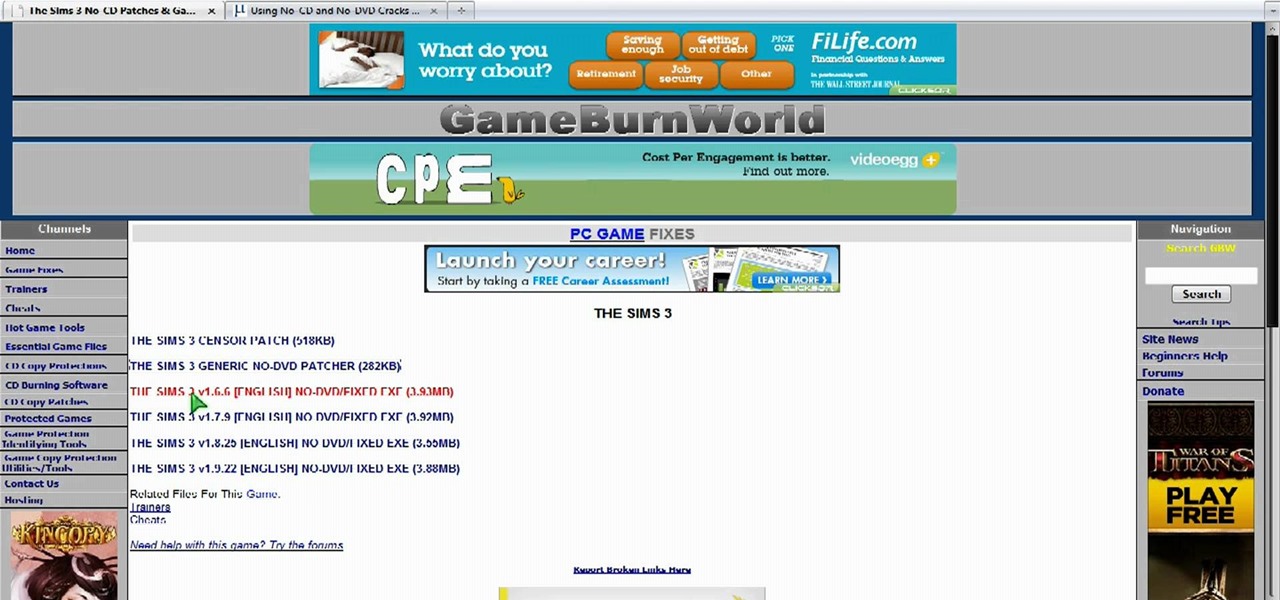
In this video, we learn how to use cracks to play a DVD or CD without the disk. First, go to Gameburnworld and download/install the patch to play your game. Then, open it up and go to the program files folder to find the files for the game. Drag this and drop it in, then you will not have to use the DVD for your movie or CD. Remember to only use this if you own the game or movie, not if you have downloaded it illegally. You can do this for all your discs, it's easy and just takes a few minutes!

In this tutorial, we learn how to repair and seal an asphalt driveway with Lowe's. First, make sure you wear appropriate clothing and have taken all the safety precautions before starting. Now, brush off all the dirt from the driveway, then clean it and scrub off any oil spots from the asphalt. After this, patch any cracks that are in the asphalt with crack filler. Allow this to cure according to the directions, now get ready to seal the driveway. Grab your asphalt sealer and brush it over th...

If you have a cutting board that you made or purchased from the store, excessive exposure to water can be bad. Water can be sucked into the wood and damage the wood board, eventually leading to a crack. Instead of throwing it out, you may want to let it sit for a couple of weeks so that the water is able to dry out.

In this tutorial, we learn how to draw a behatted cartoon skull. Start out by drawing hollowed out eyes , then draw a hollowed out nose underneath. After this, draw a wide open mouth with a goatee on the chin and teeth smiling in the mouth. Next, draw a hat on the top of the head, making a bow on the side of it. Next, draw cracks in the skull and add shading to the inside of the hat and on the entire skull. Draw lines around the mouth and head to show where cracks in the bone are, and when fi...
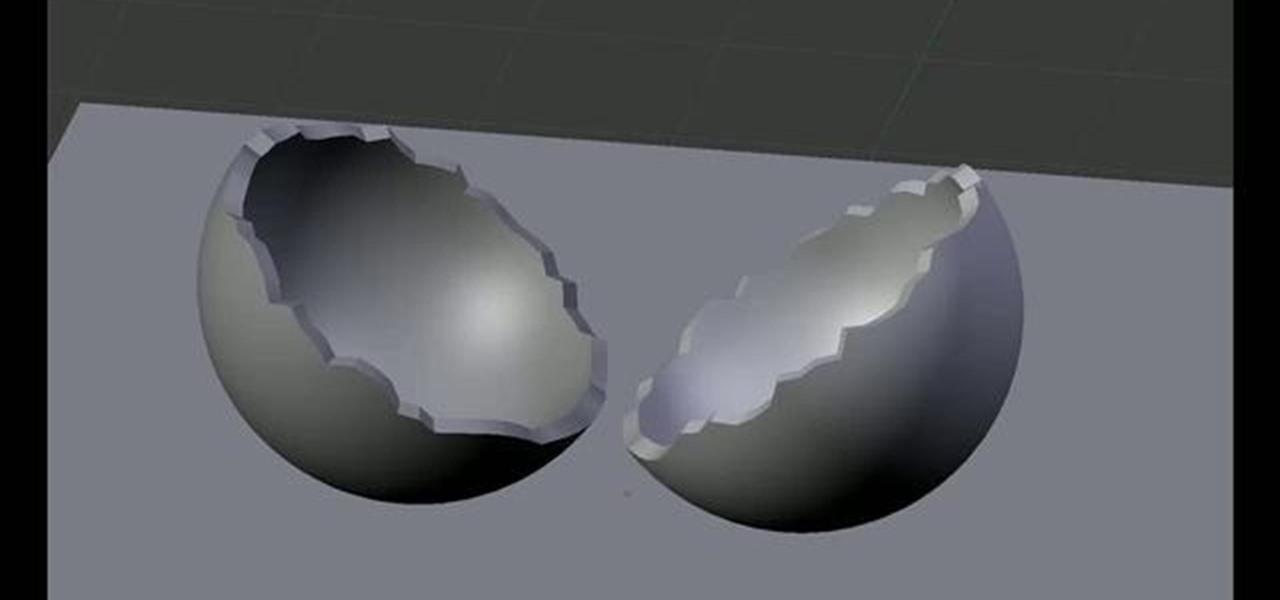
Learn how to create a crack in a 3D object in two minute or less with this video guide. The technique involves no scripts, just a powerful tool that has been right under your nose for years! Whether you're new to the Blender Foundation's popular open-source 3D computer graphics application or are a seasoned digital artist merely on the lookout for new tips and tricks, you're sure to be well served by this free video software tutorial. For more information, including step-by-step instructions,...

How to pick a lock! Lock picking is is a useful trade that should only be used when you lock yourself out. Do not use this lockpicking video to break into other peoples' homes or property. Watch this video and learn how to pick a lock next time you are in a jam.

Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/WPA2 password, we'll use it to play a Wi-Fi hacking CTF game anyone can practice for less than $10.

I don't know of a pain greater than of the one felt after cracking the screen of your phone. After I managed to crack my screen, rendered unusable, I immediately began to panic as to how I was going to recover all of the photos, videos, and documents stored on my device. After a few hours of searching, I came upon a thread by Mohamad Sabra that showed exactly how to alleviate my problem.

Welcome back, my eager hackers! In recent blogs, I've demonstrated how to grab password hashes remotely using Metasploit's meterpreter and pwdump. Once we have the Windows passwords from the SAM file, we can then crack these hashes using tools such as Cain and Abel.