With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

Google's new Pixel phones will ship with Android 7.1 Nougat pre-installed, but early reports stated that Nexus devices wouldn't be getting the new version until "end of year" 2016. For people that purchased a Nexus 5X or 6P under the assumption that Nexus devices get Android updates first, the fact that the Pixels could be getting 7.1 a full two months ahead of them felt like a slap in the face.

We've already seen plenty of shopping potential for mixed reality headsets, from holographic car showrooms to trying on clothes and picking out furniture. Very few of those ideas have been put into actual practice, but we're getting closer, and consulting firm Valorem is making headway. They created HoloTire for the Microsoft HoloLens to demonstrate the advantage of experiencing a product in mixed reality. I'm hard-pressed to think of a more boring product to put on a holographic pedestal tha...
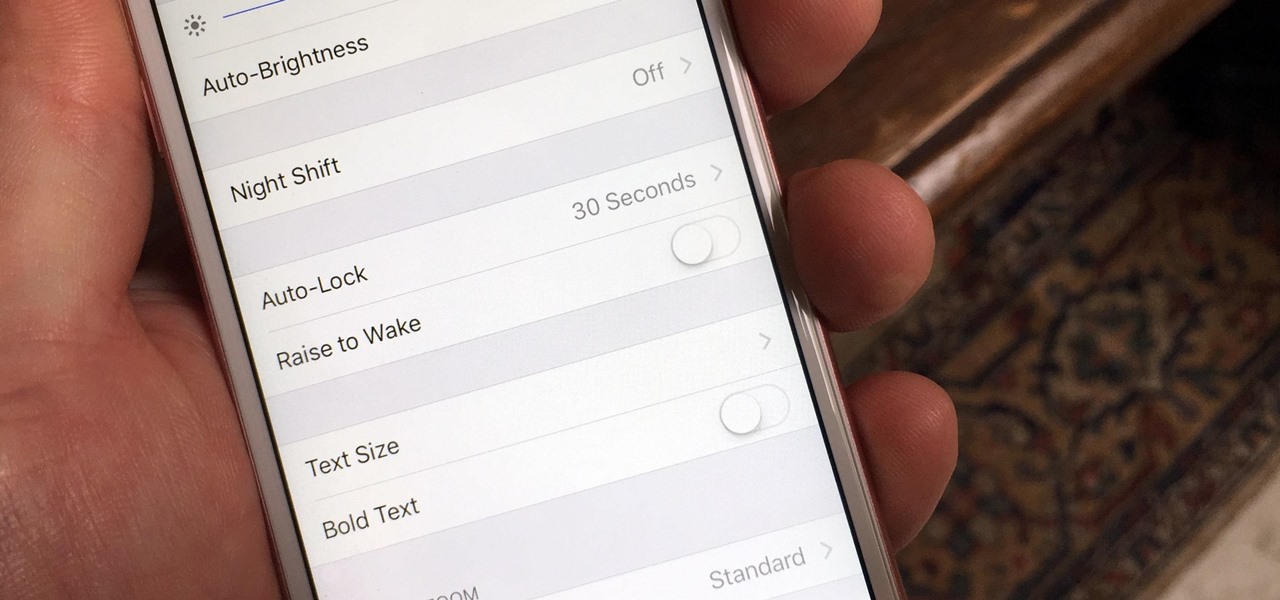
After updating your iPhone to iOS 10, you may have noticed that your screen will wake up whenever you pick up the device to look at it, or even when it's just in your pocket or dangling in your hand.
There's a lot of great things to be excited about with iOS 10 on your device. You can remove annoying stock apps, search emails better, remember where you parked, and much, much more. Seriously, there's actually more outstanding features in iOS 10 than in Apple's latest iPhone 7 models.

Virtual and mixed reality experiences feel immersive because they take over your senses in various ways, but they still lack tactile feedback. Haptic gloves can change that, and you can make a pair yourself.

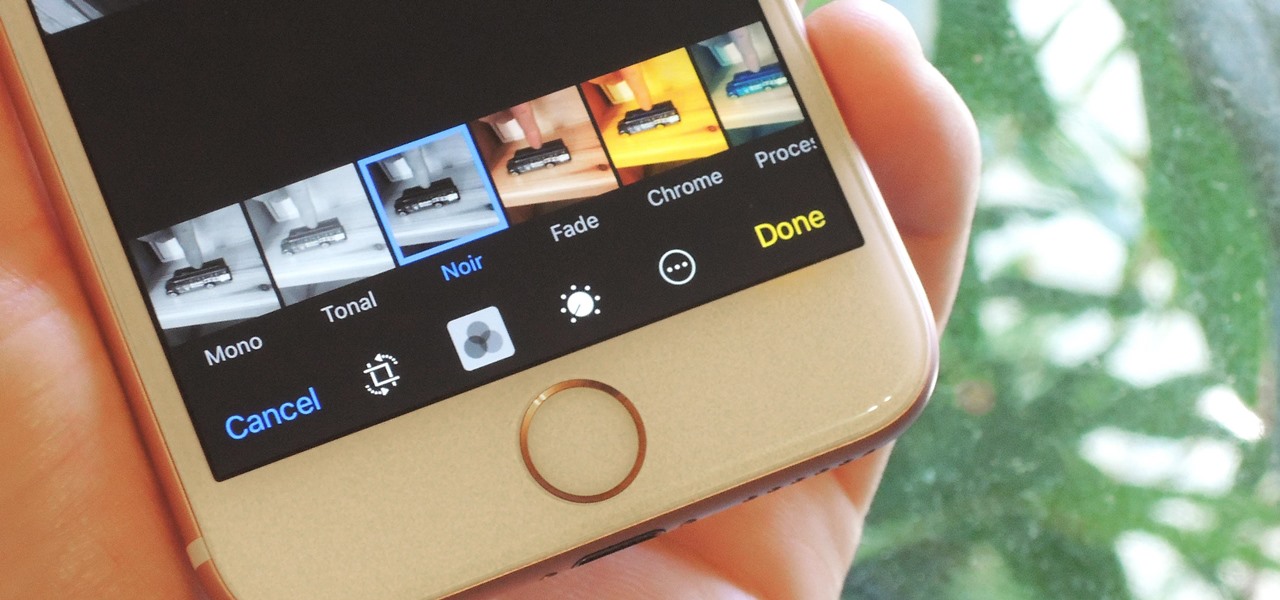
The iPhone 6s models introduced Live Photos in iOS 9, a cool new camera feature that takes a GIF-esque moving image every time you snap a pic, but the cool factor pretty much stopped right there. You couldn't take them on older iOS devices, share them with non-iOS users, or even edit them.

When we tell folks how often we use apple cider vinegar, they are baffled and bewildered. "I've had a bottle sitting in my pantry for 10 years," is the response we encounter most. And "I never use it!" Some have never even used apple cider vinegar at all in their lifetime, believe it or not.

In the revamped Messages app in iOS 10, you can now send animated GIFs from your iPad, iPhone, or iPod touch without a third-party keyboard like Giphy or GIF Keyboard.

The Oculus Rift's virtual experiences become a little less immersive when you're barely moving in a chair with a headset on, playing on a gamepad—but you don't have to accept that reality anymore.

Normally, you have to hold down the on-screen button to record videos on Snapchat, but if you want to go hands-free for some more creative video selfies or less shaky landscapes, there's a workaround on iPhones that lets you do just that.

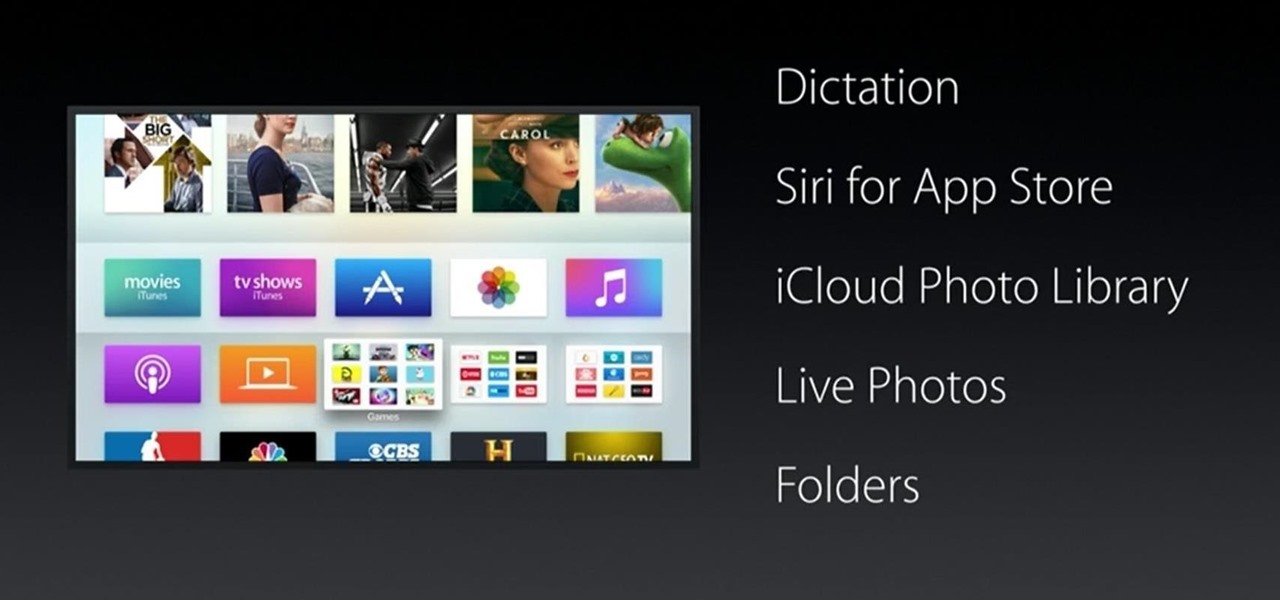
Apple will release tvOS 9.2 for the latest Apple TV today, bringing some major features to the streaming device. The software update, announced at today's Apple event, comes with Siri voice dictation, full iCloud photo viewing, and support for Bluetooth keyboards. Since Apple has already been beta-testing tvOS 9.2 for months, it's ready for a public rollout.

We like our Egg McMuffins around here, albeit homemade with our preferred ingredients: whole wheat (or homemade sourdough) English muffins, a slice of thick Tillamook cheddar cheese, a meat, perhaps, like Canadian bacon, and finally—that perfectly-fried, perfectly-shaped egg.

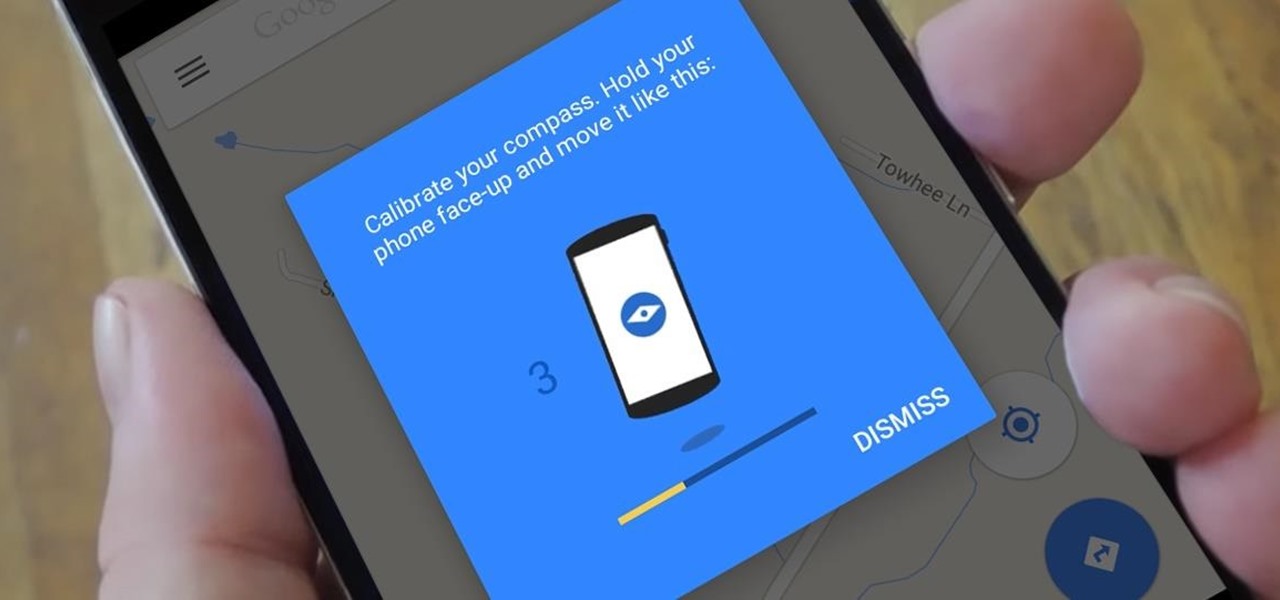
A lot of users with newer Android devices, particularly the Nexus 6P, have been complaining about issues with their device's compass. I've experienced the issue a few times myself—when you open Google Maps and try to get directions somewhere, you're prompted to calibrate your compass before you can proceed.

Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.

Many websites are crowded with ads, pictures, and other irrelevant content that make it harder than necessary to read a simple article on your iPhone. In many cases, you have to zoom in just to get a better view of the text you're attempting to read—unless the webpage blocks zooming.

In this tutorial I am going to show you how to change some file metadata, this could be very useful if you want to edit or access a file and remove any evidence of your changes.

Greetings all. Before I get into the tutorial, I would like to mention that I am fairly new to Null Byte (been lurking for some time though), and what really appeals to me about this place is its tight, family-like community where everyone is always willing to help each other and the constant search for knowledge that inhabits this subdomain is a driving motivator for me to join in. I'm glad I arrived at the right time. Anyway, wipes tears (not really)...

Technology can move really fast. Just consider the format for which we consume videos and movies, which has transformed from film reels to VHS to DVD to Blu-ray to steaming with nothing physical at all. But for some odd reason—maybe because it strikes a nostalgic chord or it's just the new hipster trend—VHS is in again. Yes, shaky, grainy, low-quality videos with timestamps are cool again, and I dig it.

You would think that with each major iOS update, there'd be fewer ways to bypass the lock screen. Unfortunately, Apple's developers have consistently failed every year since 2013 in this department, leaving open lock screen exploits for iOS 7, iOS 8, and now the latest iOS version, iOS 9, with each exploit being discovered within days of the OS release.

A fire snake, also referred to as a black snake or sugar snake, is a classic science experiment you can do right in your own kitchen using a baking soda and sugar mixture and a fuel to ignite the reaction.

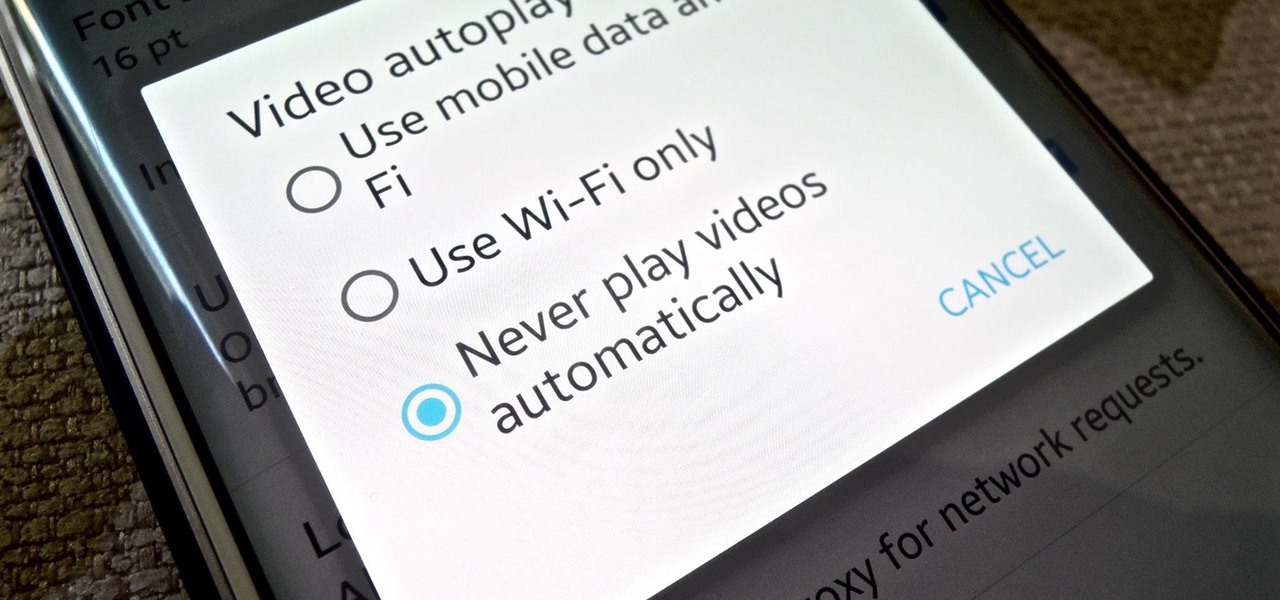
It's bad enough that we have to deal with autoplaying video advertisements all over the Web, so why do we have to be subjected to autoplaying videos on Twitter, too? Autoplay video are muted by default, but that doesn't make them any less annoying, especially if you have a small data plan on your phone.

Although wear and tear on kitchen knives is unavoidable, it's extremely frustrating when I can't cut through tough, fatty tendons in meat or even make a clean slice through an onion. If you don't have a steel rod or water stone to sharpen your knives, or even a cheap knife sharpener, you can get creative by using a coffee mug and even a newspaper.

You know what's in your folders, so it's not always necessary to label them and ruin that clean look you're going for on your iPhone's home screen. I mean, how many folders am I going to have to title "Stuff" or "Junk"?

There's a recently discovered flaw by iDownloadBlog that lets thieves reset a stolen Apple Watch without a hitch, which is the result of Apple not including the Activation Lock feature that iPhones have had since iOS 7.

As with any software, Android apps can occasionally suffer from bugs. But finding the root cause of such issues can often be difficult, and reporting bugs is a cumbersome experience.

Depending on how many Watch-compatible apps you have, the Home screen on your Apple Watch is either insanely clean or absurdly messy. When I first synced my Watch with my iPhone, I was attacked with a huge honeycomb of apps, strewn across my Home screen in no particular order.

Hi, dear co-apprentices and wise masters. I've been recently trying to learn the basics to hacking here, and I've read all guides on Wi-Fi hacking and noticed no word is dedicated to this awesome script that comes bundled with Kali!

After receiving the fourth beta for iOS 8.3, we can assume that the official release shouldn't be too far behind. Along with plenty of bug fixes from prior iOS versions, Apple is also ushering in a few minor features that are sure to ease some annoyances.

Just a few days after unveiling the Apple Watch and pushing iOS 8.2 to their current products, Apple has, for the first time ever, made a beta version of their mobile OS available for the public to test out.

It's been a long time coming, but HBO will finally be releasing their cable-free streaming service next month in the U.S., over two years after they had released similar standalone subscriptions in countries such as Norway.

Welcome back, my aspiring hackers! As I mentioned in earlier posts, the best hackers (or at least those not behind bars) have a keen understanding of digital forensics. If I am tasked to intrude upon an enemy's file server to retrieve war plans, such as in this tutorial, it is essential to my country's (and my own) well-being that it not be traced back to me. Understanding digital forensics helps us to leave without a trace and never have a trail back to us or our employer.

Cheesecake is pretty awesome. It's super versatile, allowing you to change crust bases and toppings quite dramatically and still end up with something that's elegant and delicious. Which is why it's a great dish to add to your dessert repertoire! There are a number of approaches to making a cheesecake base: classic, new york style and no-bake. Today we're going to go down the more classic route.

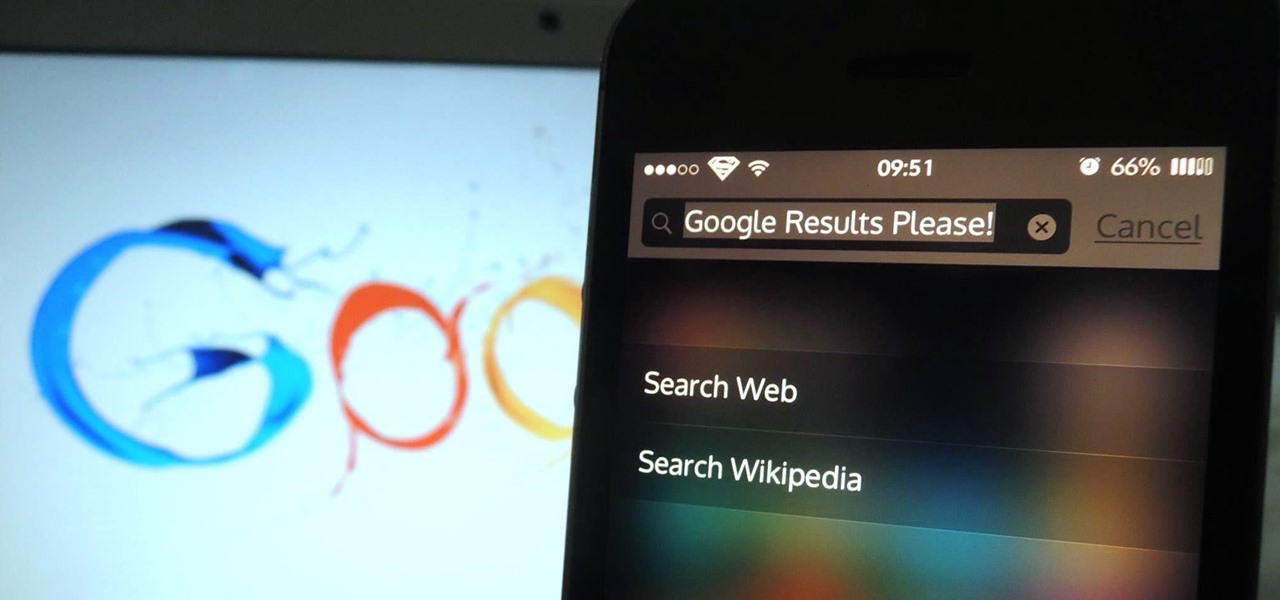
Spotlight makes finding apps, contacts, emails, songs, and old messages extremely easy on an iPad, iPhone, or iPod touch. You can even search for Wikipedia articles online, as well as perform general web searches.

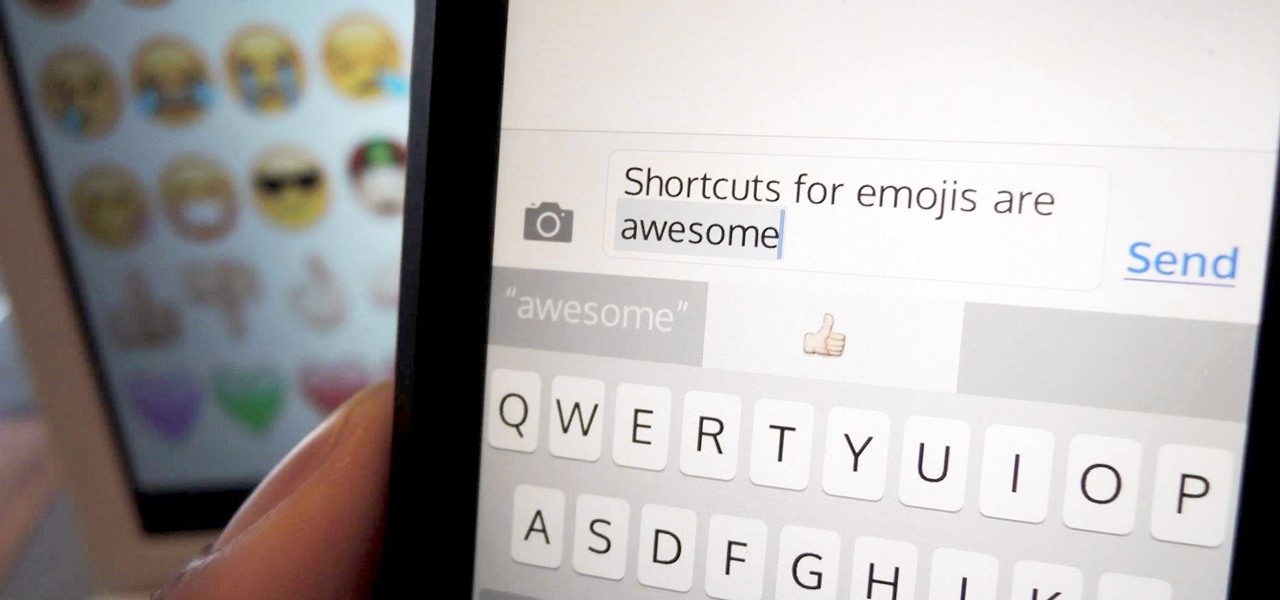
If I told you that people who use emojis in their conversations have more sex than plain-text users, would you believe me? According to a recent study launched by Match.com, men and women that use emojis have more sex than those who do not. If you were looking for an excuse to increase your emoji output, you may not find a better one than that. To make your emoji typing as smooth and seamless as possible, I'm going to show you how to create shortcuts in iOS 8 for all your favorite use cases. ...

The buttery scent of crescent rolls bring me back to my childhood, but those tubes that open with such a satisfying pop are more than just retro reminders. Crescent rolls can morph and serve as the base for hundreds of creative and cool dishes.

Apple's iPhone is one of the most popular, most expensive smartphones in the world, yet with a broken Home or Sleep/Wake button, it might as well be a doorstop. There are many different DIY ways to fixing a busted Home button, but the Sleep/Wake button (aka Power button) is a little more averse to DIY trickery.

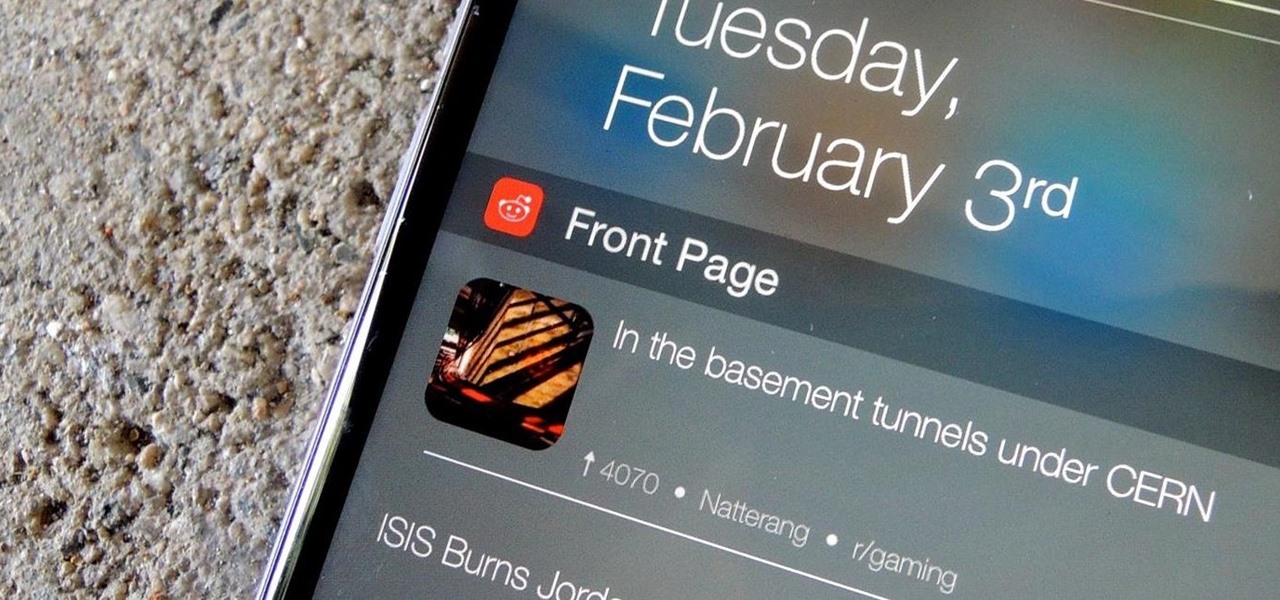
Reddit is a force to be reckoned with. What started out as link aggregator has become one of the world's most popular websites, with over 170 million unique visitors and 6 billion monthly pageviews. Whether you're into cute animals, crazy conspiracy theories, sports, or Taylor Swift's armpit, Reddit definitely has something for every taste, interest, and morbid curiosity.

If you've had your Gmail account for awhile, it's probably a cluttered mess thanks to unread messages, out-of-control newsletters, and never-ending email threads. This is one of the main reasons for the creation of Google's streamlined Inbox service, but the adoption rate for it hasn't indicated a huge shift over for most of us yet (partly because it's invite-only still).

There is no built-in way, or any options in the iOS App Store, to customize the vacant top half of the screen that appears when the newer Reachability feature is triggered in iOS 8. However, there are many Reachability tweaks for jailbroken iPhones, one of which lets you use the feature on devices other than an iPhone 6 or 6 Plus.