Welcome back, my novice hackers! In a recent tutorial, I showed how the SNMP protocol can be a gold mine of information for reconnaissance on a potential target. If you haven't already, I strongly suggest that you read it before progressing here, as little of this will make much sense without that background.

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

Everybody knows not to store sensitive information in unencrypted files, right? PDFs and ZIP files can often contain a treasure trove of information, such as network diagrams, IP addresses, and login credentials. Sometimes, even certain files that are encrypted aren't safe from attackers. That's where Zydra comes in — a tool for cracking RAR files, ZIP files, PDF files, and Linux shadow files.

Hi there again, aspiring hackers (and veterans as well)! I'm going to explain how to perform a dictionary attack on a WPA/WPA2 protected network with Wifite. Please note that this doesn't work with WPA Enterprise For that end, you'd have to use an Evil Twin to get the "Enterprise" auth attempt, and then crack it.

Welcome back, my eager hackers! In recent blogs, I've demonstrated how to grab password hashes remotely using Metasploit's meterpreter and pwdump. Once we have the Windows passwords from the SAM file, we can then crack these hashes using tools such as Cain and Abel.

Welcome back, my tenderfoot hackers! Not too long ago, I showed how to find various online devices using Shodan. As you remember, Shodan is a different type of search engine. Instead of indexing the content of websites, it pulls the banner of web servers on all types of online devices and then indexes the content of those banners.

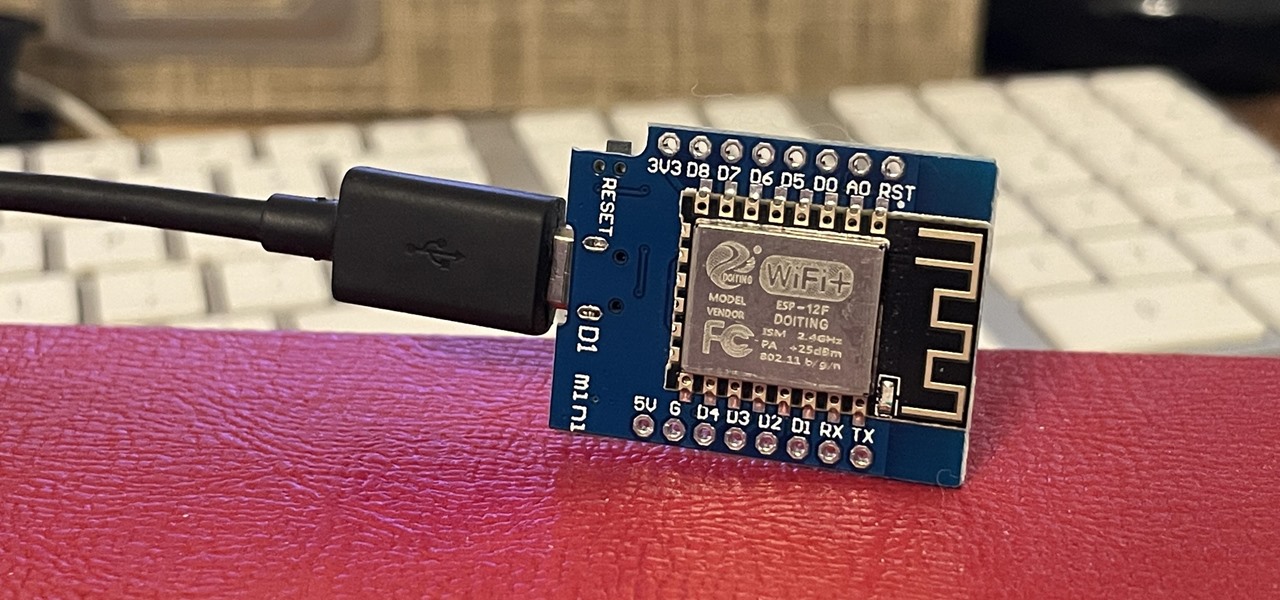
If you've wanted to get into Wi-Fi hacking, you might have noticed that it can be pretty challenging to find a safe and legal target to hack. But you can easily create your own test network using a single ESP8266-based microcontroller like the D1 Mini.

Dr. Michael Pound, a computer science researcher and professor at the University of Nottingham, uses hashcat and 4 GPUs in parallel to go through 1o billion hashes a second in this Computerphile video. He calls his deep-learning server the "Beast." If you're new to cracking passwords, he does a great job breaking down the process of what's going on as hashcat does its magic.

Master Lock combination padlocks have been known to be vulnerable to an attack that reduces their 64,000 possible combinations down to 100. I've devised a new attack for cracking any Master combo lock that simplifies the process and reduces the amount of work down to only 8 combinations.

Welcome back, my hacker novitiates! In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. In that guide, I promised to follow up with another tutorial on how to use THC-Hydra against web forms, so here we go. Although you can use Tamper Data for this purpose, I want to introduce you to another tool that is built into Kali, Burp Suite.

A weak password is one that is short, common, or easy to guess. Equally bad are secure but reused passwords that have been lost by negligent third-party companies like Equifax and Yahoo. Today, we will use Airgeddon, a wireless auditing framework, to show how anyone can crack bad passwords for WPA and WPA2 wireless networks in minutes or seconds with only a computer and network adapter.

This is my first ever how-to so I apologize in advance for any grammar mistakes or spelling errors. Introduction

There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.

Greetings fellow students! I'm currently reading a book called "Violent Python: A Cookbook for Hackers, Forensic Analysts, Penetration Testers and Security Engineers"

There is something so satisfying about dipping your spoon into a perfectly smooth slice of cheesecake. There is something a bit less satisfying about it if the top of the cheesecake is cracked and cratered.

Hi, dear co-apprentices and wise masters. I've been recently trying to learn the basics to hacking here, and I've read all guides on Wi-Fi hacking and noticed no word is dedicated to this awesome script that comes bundled with Kali!

Despite the security concerns that have plagued Facebook for years, most people are sticking around and new members keep on joining. This has led Facebook to break records numbers with over 1.94 billion monthly active users, as of March 2017 — and around 1.28 billion daily active users.

Weather - there's no escaping it! Mother Nature can be hard on asphalt: if you live in an area where there are extreme weather changes from season to season then your asphalt will eventually become damaged. As the ground freezes and thaws there is movement that flexes the asphalt. Repeated flexing can cause weakness to occur. In many cases the first damage you will see will be cracks forming in your asphalt driveway.

You may have asked yourself, "How do hackers take my password, if the website owner can't?" The answer is simple. When a website stores your login password for the site, it is run through a cryptographic hash function before it enters the database (if the website isn't Sony).

More password cracking action from Null Byte! Today we aren't going to be cracking passwords per se, rather, we are going to learn the basics of generating rainbow tables and how to use them. First, let's go over how passwords are stored and recovered.

Unlocking the secrets to the Masterlock by cracking the code. Crack the code on any Masterlock.

Watch this video to learn two methods for cracking a crawfish. Crack a crawfish.

Is the finish on your rims peeling off or cracking? If so, you may want to refinish them. This video shows you how using Dupli-Color wheel paint.

Mechanical locks have been around since ancient Egypt, with the oldest known artifact found in the ruins of Nineveh, an ancient city in Assyria, Mesopotamia, which is just across the Tigris River from what is now Mosul, Iraq.

Systm is the Do-It-Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. They will help you avoid pitfalls and get your project up and running fast. In this DIY episode, see how to waterproof your thumbdrive.

November 11th isn't just Veterans Day— it's Origami Day in Japan, where they celebrate the traditional art of paper folding. November 11th is also the last day of World Origami Days, a 2-1/2 week celebration held internationally.

If you have a problem with your drywall tape being exposed or possibly cracking, it could have happened for many reasons. But no matter what that reason may be, it's an ugly sight to see.

WPA-secured wireless networks, or WiFI Protected Access, is a form of internet security that secures your wireless LAN from being accessed by unauthorized users. Safer than WEP, or wireless equivalent privacy, WPA still has weaknesses that are prone to cracking - IF, that is, you know what you're doing.

Still using the same lightweight, oil-free lotion during the winter as you did last summer? Then it's obvious where your flaky, dry winter skin is coming from. The shift from warmer, more humid days to dry and cold immediately saps your skin of moisture, meaning you have to update your beauty routine to stay moisturized.

Master Gardener Rosamarie Maddox asks John White, Doña Ana County Extension Agent, about problems facing her pecans, grapevines, and native shrubs. An unidentified insect found on her pecan tree is identified by John White as a Twice Stabbed Ladybug. This ladybug is a useful insect that often over-winters on the tree and helps takes care of the aphid problems faced by pecans. Pink fuzzy coating on pecan nuts is also brought up. The coating is normal for pecan and contains bitter tannin. Too m...

Whatever your reasons for doing it, if you are trying to hack passwords, it helps to have the right software for getting the job done. With the Cain and Abel program, you will be well on your way to hacking even the toughest personal passwords.

Tony D'Angelo demonstrates his method of making hard boiled eggs. He starts with room temperature eggs to avoid cracking the shells, adds water to cover them, and adds a little salt and vinegar to prevent the eggs from cracking. Once the water boils, he takes the pot off the heat and lets it sit for about 11 minutes. He uses salad tongs to move the hot eggs into a bowl of ice water. Once the eggs are cool he stores them in the fridge. He claims that using this method to make boiled eggs ensur...

This is a great tutorial on cracking the iphone to record more than 30 seconds on the iPhone 3G's video camera. This is a hack of the previously still camera that comes stock with all of Apple's phones. Enable your iPhone to shoot video instantly and free!

Red, itchy, scaly, and cracking feet can only mean one thing, athlete's foot. Watch this how to video and learn how to treat athlete's with a simple home remedy from Pharmacologist Joe Graedon. He shows you over the counter products that you can buy and how to use a solution of vinegar, Listerine and Vick's Vapor Rub to help the foot fungus go away.

People who know that I am a professional hacker often ask me what they can do to make their computers and personal information safe from people like me. The answer, of course, is that nothing will make you completely safe, but there are a number of measures any computer user can take to reduce the chances of being a victim of a hacker.

Fortune cookies are fun little after-meal treats. It's always exciting cracking open revelations about our heart and souls as deemed fit by fortune tellers the Panda Express. Whether you believe in fortune cookies or not, they make very cute snacks and their shape can be transferred over to other realms of baking.

Turn an ugly duckling of 700 rather boring identical origami pieces into a beautiful swan by watching this tutorial, getting a few shots of Starbucks espresso, and enslaving yourself to the task for the next couple of days.

Don't waste any of the meat on a Maryland blue crab. In this video, you'll learn how to eat a Maryland blue crab the right way. Just follow along - first the claws, then the shell. Make sure to use a sharp knife, and don't cut yourself! What are you waiting for? Get cracking!