It's no surprise that, with all their strength and agility training, soccer stars are highly acrobatic, but Iceland International right-back Asta Arnadottir has taken the soccer showboating to a whole new level.

Some of the most popular cellular devices on the market today are the iPhone 4 and 4S models. Seeing as they are made of glass, it's not uncommon for the back panel to break.

Wade Bourne of MyOutdoorTV.com shows you how important it is to take care of leather hiking boots. Leather boots are expensive, and they should be treated like an investment. This means giving them proper care to extend their life and receive the greatest use and value for your dollars spent. Here are tips on how to care for leather boots to extend their useful service.

I have had a lot of people ask me, "How does my neighbor keep getting into my wireless?!". Chances are, these people are all using WEP, a deprecated wireless encryption protocol. Either that, or you are using one weak WPA passphrase.

A book query letter must be well written and brief. Heading

When i went to class today, a good friend asked me a question. He wanted to know what the best hacking software was to basically do everything. What i told him was this: Well there isn't an "Ultimate" tool boot there are a number of tools which deserve a "Medal." So what i'm trying to say here... What are some of the best hacking tools available right now? For starters i created a list with some of the tools.

Archiving and compression is a great way to store and prepare files for sending. You can reduce the size of a file, turn a group of files into a single file, and even encrypt and password the contents! Just take a look at this image to see how much it compressed a 28GB text file.
I've decided I've not been writing enough and want to get back into writing more often. I have a few ideas for articles based on password cracking and breaking into Windows, and a basic general coding type of articles, but I wanted to know if anyone had anything they wanted to know how to do, a language they wanted to learn the basics of or something like that. Please comment with any ideas.

We've talked about the deep web before, but we never really covered the details of what's out there. It occurred to me that a nice list of resources would be very helpful to all of you anons out there. Think of this like a helpful brochure to the hidden web.

"A major hardware update to the masterlock cracking robot. Upgraded the previously non-working latch opening mechanism to be geared down 1:25, allowing it to open the shackle. I also revamped the motor mount to be sturdier, and the base of the unit to hold the lock better and also be easier to mount parts to.

With 32 countries, comes 32 different ways to verbally defile your mom. Watch out Rooney, FIFA is cracking down on your dirty mouth. Sure, a British official could catch his dirty mouth, but Saturday's England-US game was officiated by a Brazilian.

Rose Levy Beranbaum is an award winning baker, cookbook author (The Cake Bible), and authority on CAKE! I recently stumbled across a collection of "Cake Questions" on Beranbaum's blog that address a variety of issues that may come up:

So, you scratched up your $500 Adobe CD and now it's unreadable. You could go buy a new one, but you already purchased it! Searching The Pirate Bay and downloading some Adobe software can usually be easy enough, but what should you watch out for?

Your boss is pursing her lips and drumming her fingers on the table during your presentation. Your best friend is gazing downwards and crossing his arms when you ask him why the car you lent him for the weekend has a big dent. What could these body language signals all mean?

News in a nutshell: US to announce aerial blockade of Syria

Last Friday's mission was to accomplish solving HackThisSite, Realistic 5, the fifth and last in my series of realistic hacking simulation missions. This time, telemarketers are invading people's privacy, and it was up to us to stop them! The job was to get root on the site and delete the contact database in order to return the right of privacy to its victims.

When it comes to coffee, some people just like perfection. Most would agree that the best cup of coffee comes from home, after roasting your own green coffee beans. But not everybody has the time or money to have complete control over their coffee's flavor. Roasting via stovetop or oven produces mélange (not quite perfection), and home roasters can be pricey.

Ever since kernel 2.6.xx in Linux, a lot of the internet kernel modules for wireless interfaces ended up becoming broken when trying to use monitor mode. What happens commonly (to myself included) is a forced channel that your card sits on. No good! For users of airodump and the aircrack-ng software suite, the software has become unusable.

Have an old-school tabula recta lying around? No? Then just print out the chart below. Nothing ensures better password security than this centuries-old cipher technique. Here's how it works, via Wikipedia:

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

After stumbling across an interesting article by Hanne Blank—(apparent) hobbyist chef and widely known activist on the issues of weight, bisexuality, and sexuality—I've become even more fascinated by kitchen shortcuts. Former Microsoft CTO Nathan Myhrvold's recently released Modernist Cuisine also spurred a similar interest, particularly after reading a WSJ piece in which Myhrvold attests —by law of science, of course— that a ¼-inch-thick sheet of steel is more than adequate in place of an ex...
Beware the Canning Mission! The Zynga Community Forum is full of complaints about the new Canning Mission. Here is an outline:

This past Sunday, a group called Gnosis launched a massive hacker attack on Gawker media, one of the web's most popular blog networks (Lifehacker, Gizmodo, Jezebel, io9, Jalopnik, Kotaku, Deadspin and Fleshbot). 1.3 million registered users' passwords were compromised, and 188,279 of them were decoded and made public. The biggest takeaway? Many Gawker denizens use downright dumb passwords. (Guess they didn't see their own Lifehacker's story on avoiding such a thing.)

Jet engines combine oxygen from the surrounding air with on-board fuel to burn at very high temperatures and create thrust in the direction of the flame. Rockets, which we will learn about in a later post, are similar but carry oxygen internally and can therefore function in space!

We're officially seeking Null Byters on a weekly basis who would enjoy taking their time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (if up to par, of course). This is a job meant for anyone with the will to share knowledge. There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials...

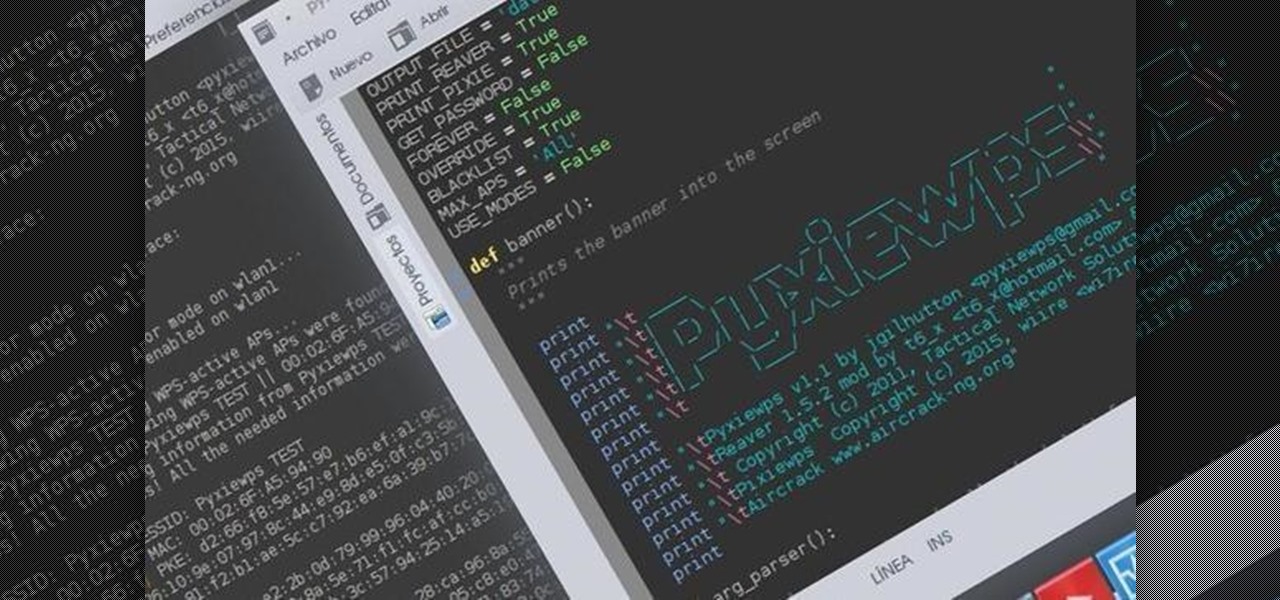
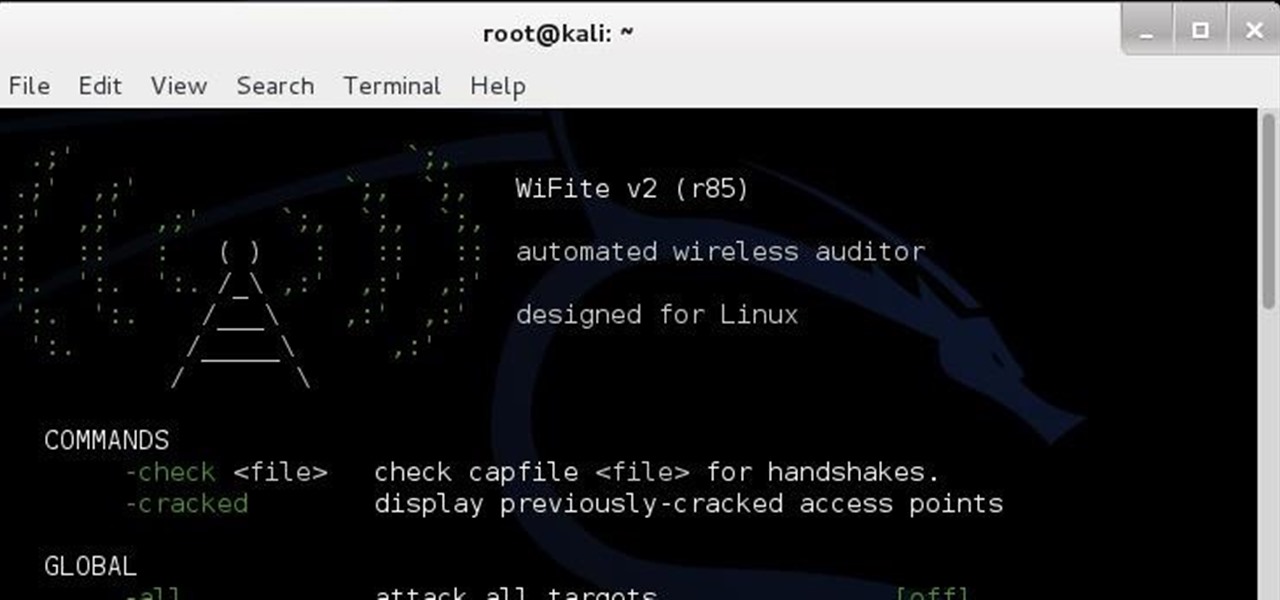
Helo my dear friends! A few days ago, I shared with this community my wrapper-script (a wrapper is a program that joins other programs that do the real job) to automatize the attacks on Pixie-Dust vulnerable routers. I was recieving complains from non-Kali users that had problems trying to launch the program, so I decided to make a good installer so anybody can use it in any DEB based distro.

Welcome, my aspiring hackers! In this tutorial I'm gonna be showing you how to hack Wi-Fi using the wps compatibility of a router, in , of course, Kali. First, fire up Kali.

Social engineering is described as the clever manipulation of the natural tendency of human trust. All of the passwords, locks, and encryption in the entire world are useless against a good social engineer who can charm or trick you into giving it up.

I've seen numerous tutorials on how to create a "strong" password. This makes me laugh. These titles imply "one" password, which is wrong in and of itself. A person should have many passwords, all different, and all extremely long. People may ask how they're supposed to remember lengthy passwords and why their current password isn't good enough. Well, I'm going to show you.

Have you ever forgotten your password and didn't know how to get back on your computer? Or ever had an annoying roommate you wanted to play a trick on to teach them a lesson? Or perhaps overly religious parents who think the internet is of the devil and won't let you read online articles about elliptic curve cryptography applications to C++? Well, then this article is for you!