
How To: Invest in a bear market
Don't hide in a cave when the market is down. Find stocks that will pay off when the bull makes its return.


Don't hide in a cave when the market is down. Find stocks that will pay off when the bull makes its return.

Step away from the tequila shooters and stop the morning-after agony before it starts. You Will Need

You've drafted a promising team, and the season's under way. Now increase your chances of making the playoffs.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to hide secret data inside a photo.

Learn how to grind coffee beans. You don't have to do everything the easy way. Coffee tastes better with fresh-ground beans, and it doesn't take long to learn how.

Learn how to cope when a pet dies. Few will ever love you as unconditionally as your pet does. So when you lose them, it's can be hard to move on. Here is some help.

Your friends want you to marry them! Before you can officiate their big day, you'll need to jump through some legal hoops. Learn how to officiate at a wedding.

Don’t know your LCD from your A-S-S? We’re going to fix that. Learn how to choose the right flat screen for you with this Howcast guide. Flat screens are pricey, so make sure you know what you're doing.

Motorcycle fatalities are on the rise. Make sure you're doing all you can to protect yourself. Practice good motorcycle safety.

Brian Brushwood and Scam School give you another way to score free booze at the bar. Memorize a few configs and you'll hold the key to another unbeatable game and loads of free drinks!

Learn how to play "If I Were A Boy" by Beyoncé Knowles, an acoustic guitar tutorial. Follow along with this demonstration, tabs and lyrics here:

Learn how to play "Faith" by Limp Bizkit, an acoustic guitar tutorial. Follow along with this demonstration, lyrics here:

Here’s the thing—dogs will do things just to please you. But cats want to know what’s in it for them. Learn how to train a cat.

Check out this instructional legal video sequence that shows you how to file a motion in family court. This video contains important information on preparing and serving a motion in family court. The most common reasons for filing a motion are to request a court order affecting child custody, parenting time, or child support. The court has forms and instructions for the most common problems. Please remember the court is a very formal place with a set of language and rules. This is the video i...

Learn tips, rules and strategy on how to play and win at Monopoly, the popular board game, in this free how-to video series on the game of Monopoly.

Shooting and dunking are some of the most exciting things you can do on a basketball court. Get expert tips and advice on basketball rules, shoes, and history in this free video.

Dribbling is a basketball skill you'll want to improve if you plan on making it to the next level. Get expert tips and advice on basketball rules, shoes, and history in this free video.

This is the basic prayer that should be meant from your heart and soul, and not just saying the words from your physical tongue. A true redeeming confession to the lord Jesus Christ, asking Him to come into your heart as your personal lord and savior, asking Him to forgive you of all of your sins, rejecting all evil from continuing to be involved in your life, and rejecting this world's ways, and listening and following God's rules and directions.

Hello, my name is Nicole Valentine and on behalf of Expert Village, I'm here to talk to you about how to coordinate birthday games for a birthday party. Now let's talk about another common game that you can use at a birthday party. And you may recall this game from youth. Paper, rock, scissors. We're going to display this game for you. You ready Robert? Now, let's go over the hand movements. This hand movement represents the paper. Of course it's flat, and it's kind of easy to remember. This ...

You may have recently seen a plethora of Instagram users, including celebrities and politicians, sharing a screenshot declaring that the platform will implement a new "rule" where it would own and could use your photos and videos however it wishes. The screenshots are part of an internet hoax, one that's been around in one way or another since 2012, but what can Instagram actually do with your media?

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

After getting confirmation from Tim Sweeney, CEO of Epic Games, we now know Fortnite Battle Royale will not be available on the Play Store when it's finally released for Android. Instead, users will have to download the APK directly from Epic Games' website — and quite frankly, this is a bad idea.
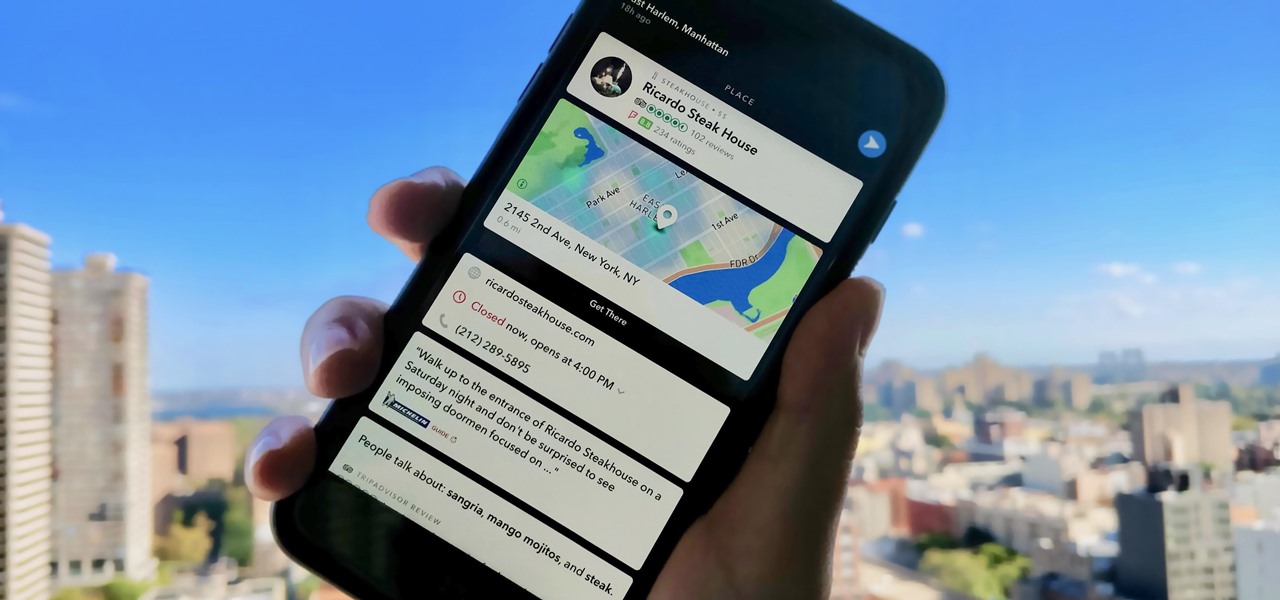
Not that long ago, Snapchat was an app with only one purpose — to send and receive self-destructing picture messages. The app has clearly grown since, adding many features that both adhere to its original function as well as ignore it. One of these new features is Context Cards. You may have heard about them, but what exactly are they?

GE Aviation and their software partner Upskill are seeing success by giving their mechanics smart tools and smart glasses, the latter in the form of Google Glass.

Research group OpenAI, a research institute co-founded by Tesla CEO Elon Musk, says it is possible to trick driverless cars' neural networks into mistaking images for something else.
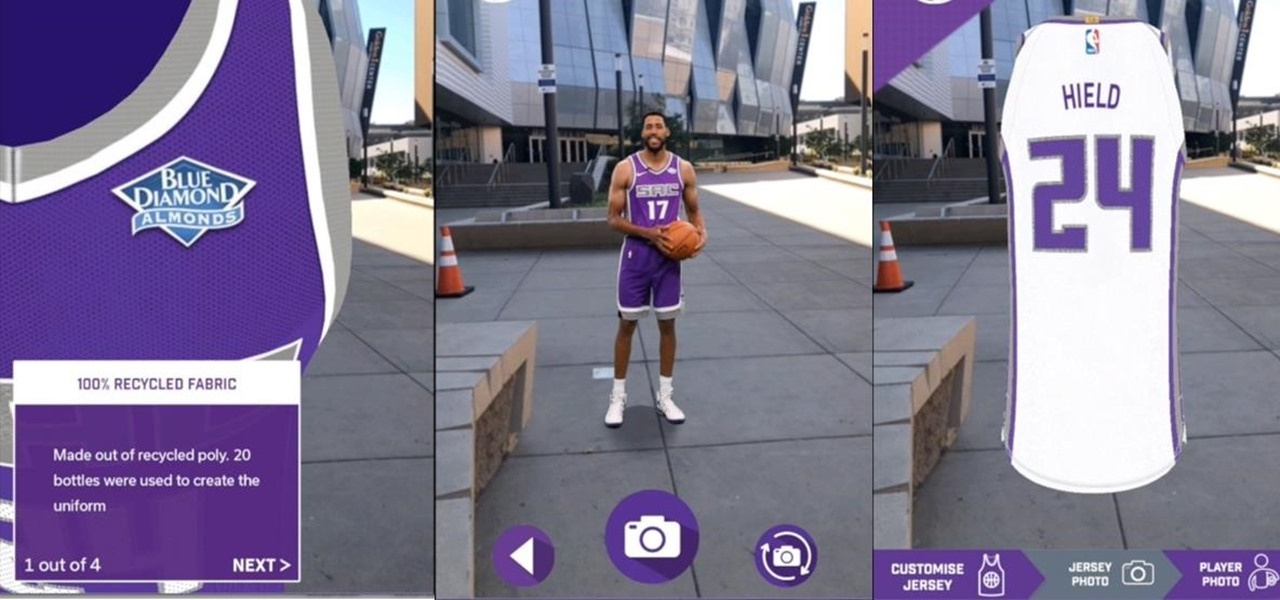
Though the Golden State Warriors won the crown as the NBA's best team again this season, the Sacramento Kings continue their rule as the sport's technology leader, debuting their new uniforms from Nike through augmented reality today.

Prepare yourself for a trip back to the days when a Sega Genesis was your gateway to premium gaming. The mid-nineties classic, Comix Zone, has been soft-launched in the Philippines, and while it's not officially available for gamers in the states, you can install it right now with a little hackery.
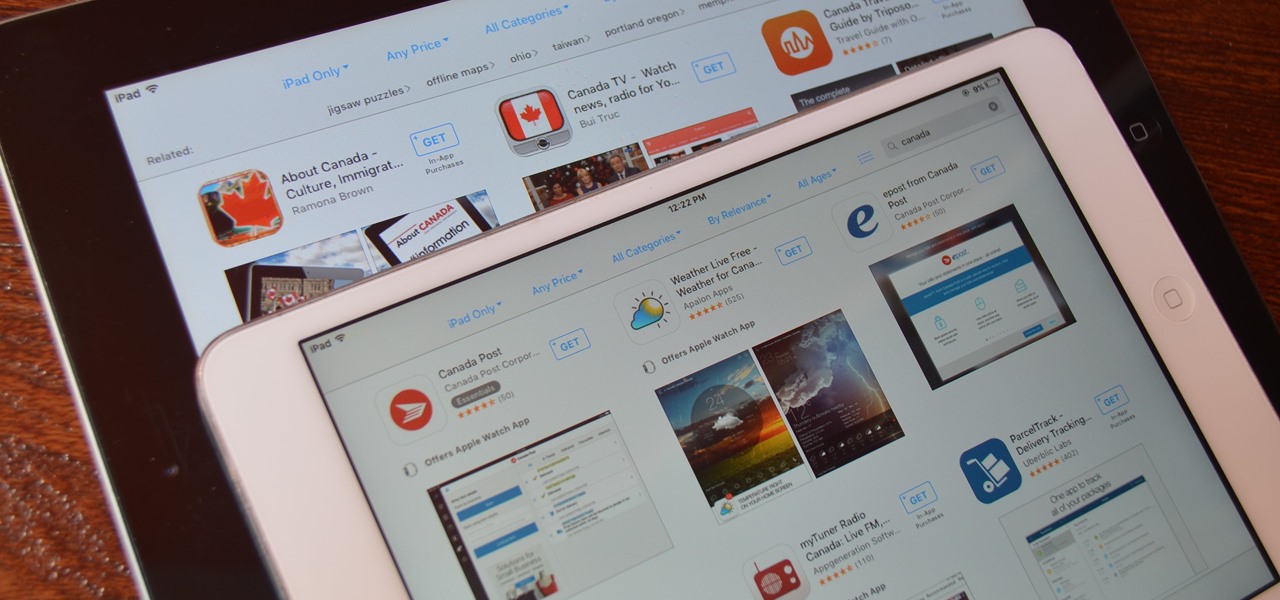
Before many games make it to the US-based iOS App Store, they get "soft launched" in a smaller country to get real-world testing for bugs. It's a pilot program, so to speak, as countries like Vietnam or the Philippines have far fewer iPhone users than the US, thus offer a more controlled environment for developers to get feedback and zero-in on issues that may occur in a game's early development phases.

When it comes to hacking guides, most are written from the perspective of a Linux user. There are a few outliers, but it's mainly Linux, which leads to the idea that Linux is the only OS that's viable for hacking. This couldn't be further from the truth. A properly set up Apple machine can do quite a bit of heavy lifting.

Pokémon GO, the global augmented reality game that's brought fans out of their homes to catch Pokémon across the planet, has brought about plenty of real-world positives. Unfortunately, when players get power hungry and start taking game hacks too far, we all get a little screwed—both digitally and in real life.
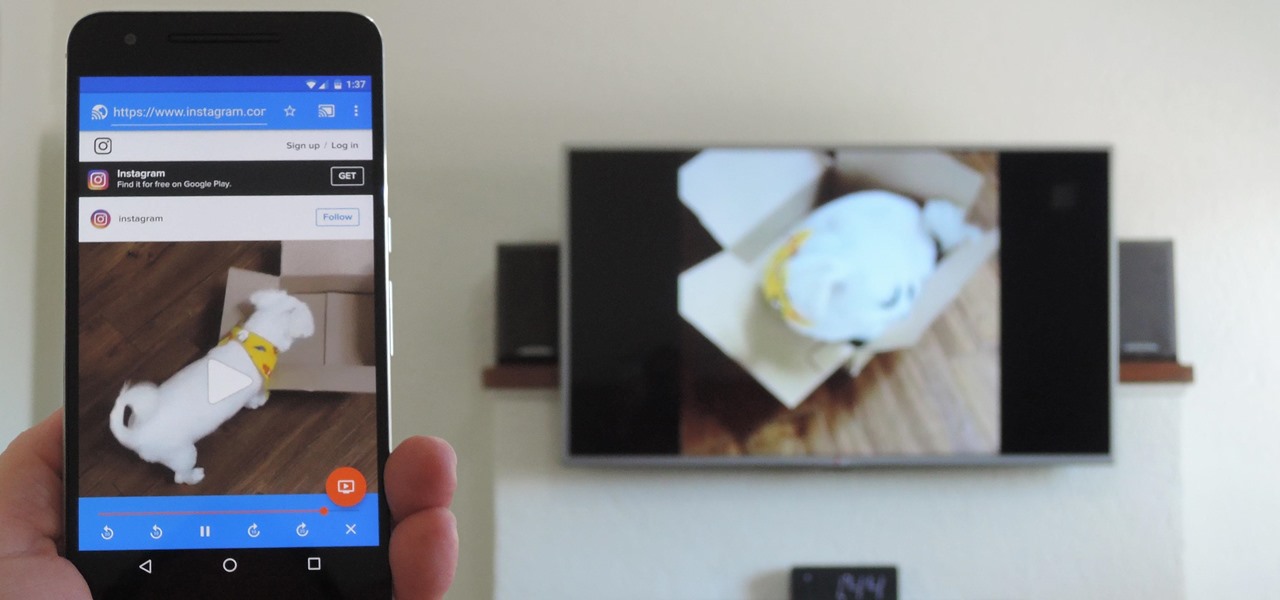
The Google Chrome browser for Android allows you to cast quite a few different videos from the web to your TV, but some sites actively disable this functionality, and others have outdated video players that won't allow for it. For example, Instagram's mobile website won't let you cast any videos, and the official app doesn't support Google Cast.

Gender standards are entirely pervasive. We raise our sons to be masculine and our daughters to be feminine, which perpetuates the gender role formula when they grow up to be parents and raise their own children. Part of this whole equation is that boys are supposed to remain stoic and project an air of strength, and girls are expected to be amiable while being held to unrealistic standards of outward beauty.
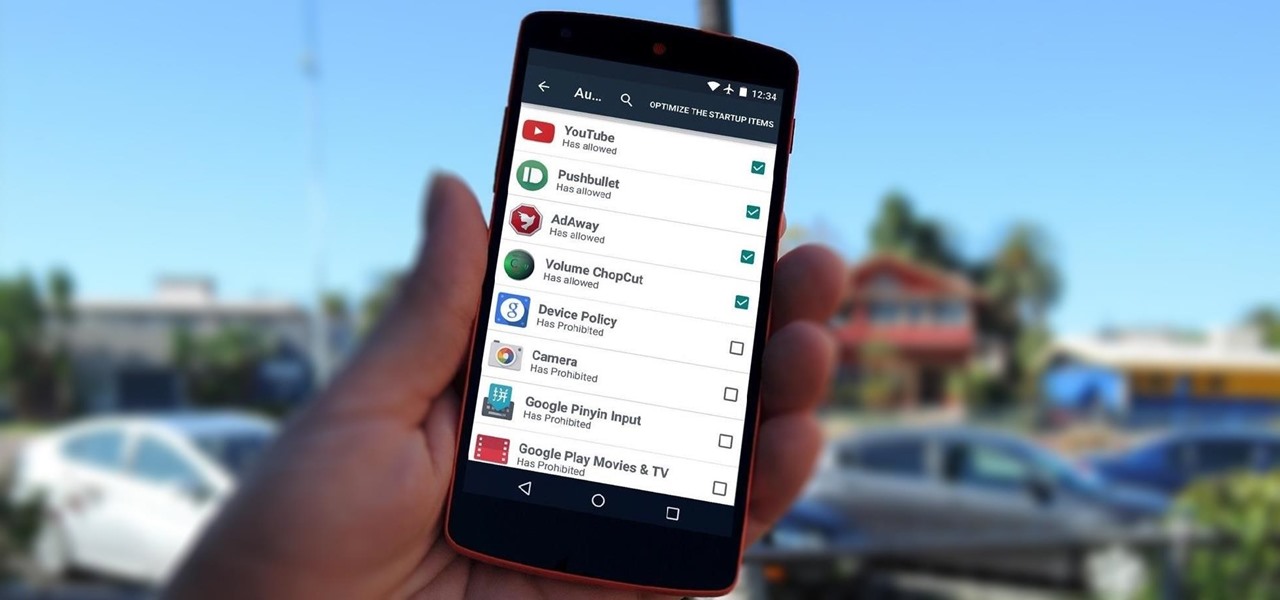
By default, any app that requests a certain permission can run automatically as soon as you start your device. Since Android doesn't offer a granular permission control system like iOS, this gets lumped in with all of the other permissions that you have to accept when you're installing an app from the Google Play Store, and you effectively have no choice in the matter.

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

Welcome back, my hacker apprentices! Last week, I started off my password cracking series with an introduction on the principles and technologies involved in the art of cracking passwords. In past guides, I showed some specific tools and techniques for cracking Windows, online, Wi-Fi, Linux, and even SNMP passwords. This series is intended to help you hone your skills in each of these areas and expand into some, as yet, untouched areas.

I miss the days where my hardest assignment was drawing a Thanksgiving turkey using the outline of my hand and trying to stay in between the lines. It seems that there is some unwritten rule that adults shouldn't feel the need to draw. Well, not anymore.

There is nothing more refreshing than an ice cream in a hot summer day. And even though, here in Australia, summer is "just" a couple of months away, I still like to have a scoop or two every now and then. However, I like to make the ice cream on my own. In this way, you can make whatever flavour you want, plus you know what type of products you have used and it usually tastes better than a commercial one.

How to Concrete in a Post: Step 1:
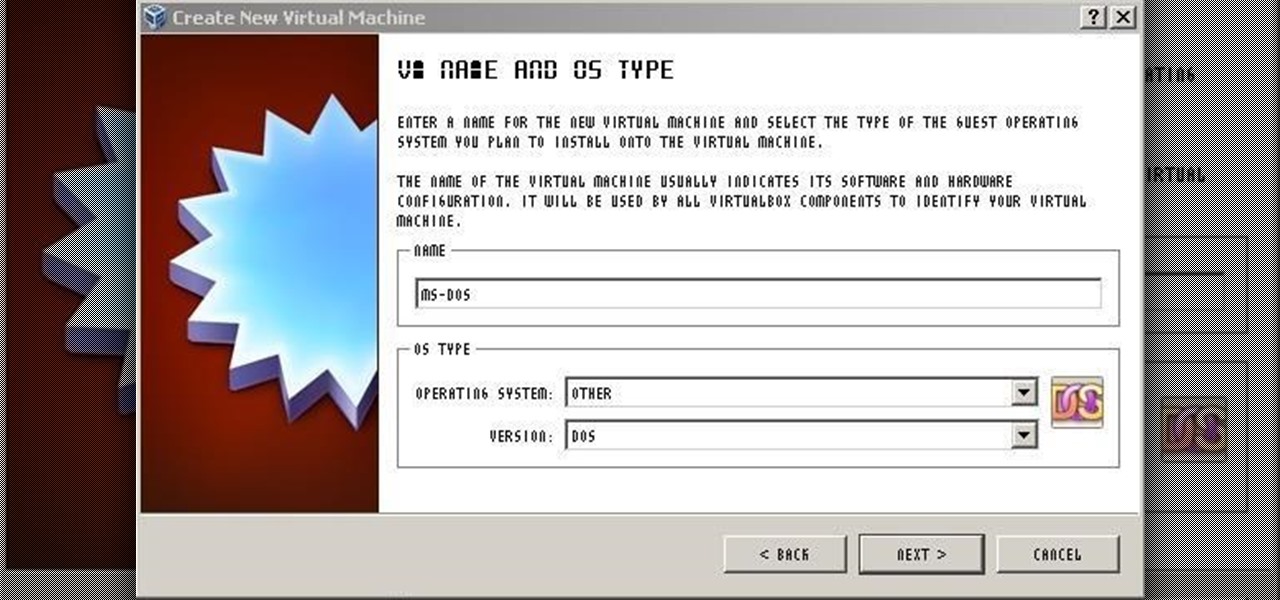
For those needing to replace old controller hardware on cutting mills, those into native retro gaming, or for those who want to see what all the fuss was about in the 1980's, or for those who just want a play with old but great technology, this tutorial shows you step-by-step processing getting the breakthrough desktop operating system running on the latest greatest hardware.

SCRABBLE. To some it's just a game, but to me it's life or death. Well, not really, but it feels that way anyway. On a normal weekend, a game becomes much like Jon Thomas' "friendly game of death Scrabble."