The check just arrived; now what? Whether you sipped tap water all night or ordered a rare bottle of wine, we have an answer. Learn how to avoid over paying. Follow proper bill splitting etiquette with this how to video.

So you've been given the slip -- the pink slip. Take a deep breath, and do the following. You Will Need

It's the coolest pool party game ever named after a 13th-century explorer. Marco Polo is a perfect way to cool down and have fun.

How to make fake pee! Does it look real? Prank your friends with fake pee. Squirt in your toilet or elsewhere.. get creative. Gross!

Ceramic beer steins are a creative and festive way to practice your pottery skills. Learn how to create your very own beer stein in this free ceramics video series.

Making pottery bowls with clay is a fun and creative art project that can be done with a potter's wheel and a few basic tools. Learn how to make a clay pottery salsa bowl in this free pottery lesson video from a ceramics artist and sculptor.

Clay pottery is a fun and creative art form that can be done with slabs of clay and not only on a spinning wheel. This free video clip series will show you several tips on how to construct matching clay plates and open a world of design ideas for you.

Arthritis is a common problem among older dogs and large dog breeds. Learn how to treat arthritis in wrist joints using dog acupressure with tips from a veterinary technician in this free dog care video series.

In this great video clip series our expert, Karen Weisman, shows us a few great centerpiece ideas that are easy to make without costing an arm and a leg. All you need are a few melons, some extra fruit and a little bit of time and you will have a delightful centerpiece that accents the rest of the table and the food that is on it. She shows you how to make complex pieces like a peacock and a wishing well but also throws in some simpler ideas like a swan. Take these ideas, run with them and ma...

Anyone looking to have a complete set of design tools at their fingertips needs to look no further than Adobe's Creative Cloud. This suite of applications is the go-to platform for creative software and is, in many ways, a must-know in fields like graphic design, video editing, and photography.

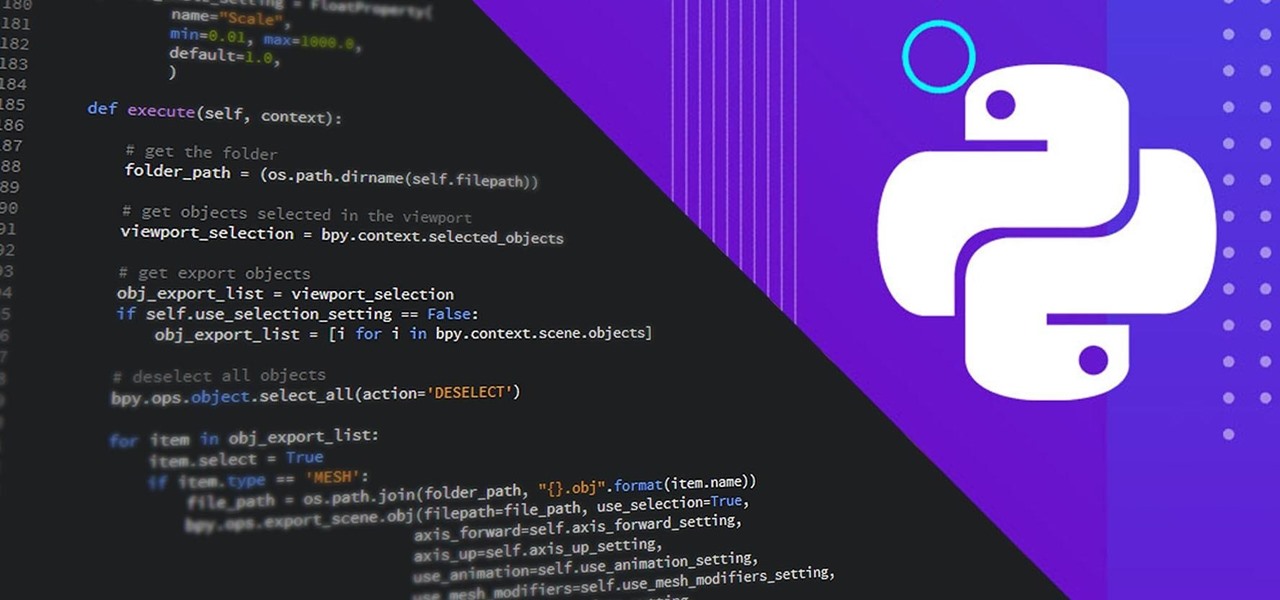
It can seem as though there's a virtually endless number of essential programming languages to choose from these days. And complicating matters even further for aspiring or even established programmers, developers, and hackers is the fact that most languages are a bit esoteric and suited for only a certain number of relatively finite tasks.

When you look at the top corner of your phone, what do you see? Upon upgrading to Android 11 or iOS 14, you'll see either "5G," "5G+," or "5G E" if you're connected to the right network. But what exactly do these symbols mean? They indicate not only if you're using 5G, but also what type you're connected to.

As we settle into our new normal, this extra time provides a perfect opportunity to learn new skills. Speaking a foreign language is a great way to expand your cultural boundaries while also training your brain. Not only will you pass the time more effectively, but you'll also be doing something positive for your health.

Castlevania ranks up there with Super Mario as one of the most memorable video games ever, and a new iteration of the side-scrolling action RPG has been soft-launched in Canada ahead of a worldwide release. If you want to try out the game on your iPhone before everyone else, there's a simple hack to try.

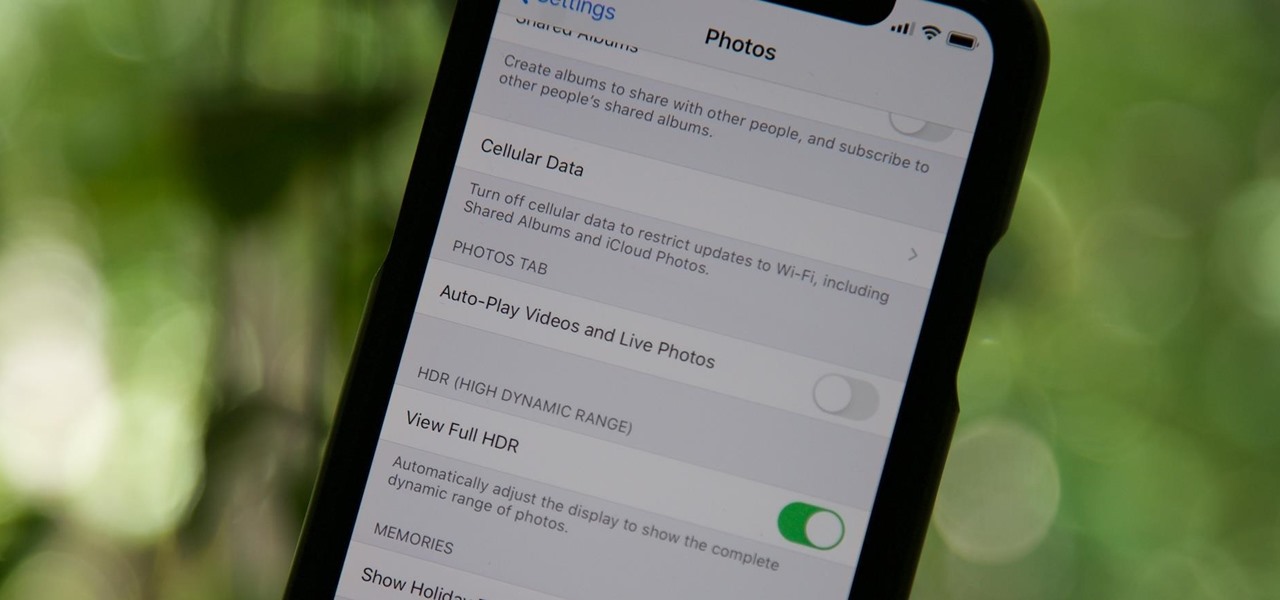
By default, videos in the Photos app auto-play in several instances on iOS 13, making it a great way to get a quick, extended glimpse when you're browsing. But this isn't always ideal — especially when you're flipping through private or embarrassing videos and other eyes are on your screen. Fortunately, Apple has an easy way to disable this feature.

Big-box retailer Target has been on a bit of an augmented reality advertising shopping spree via Snapchat lately.

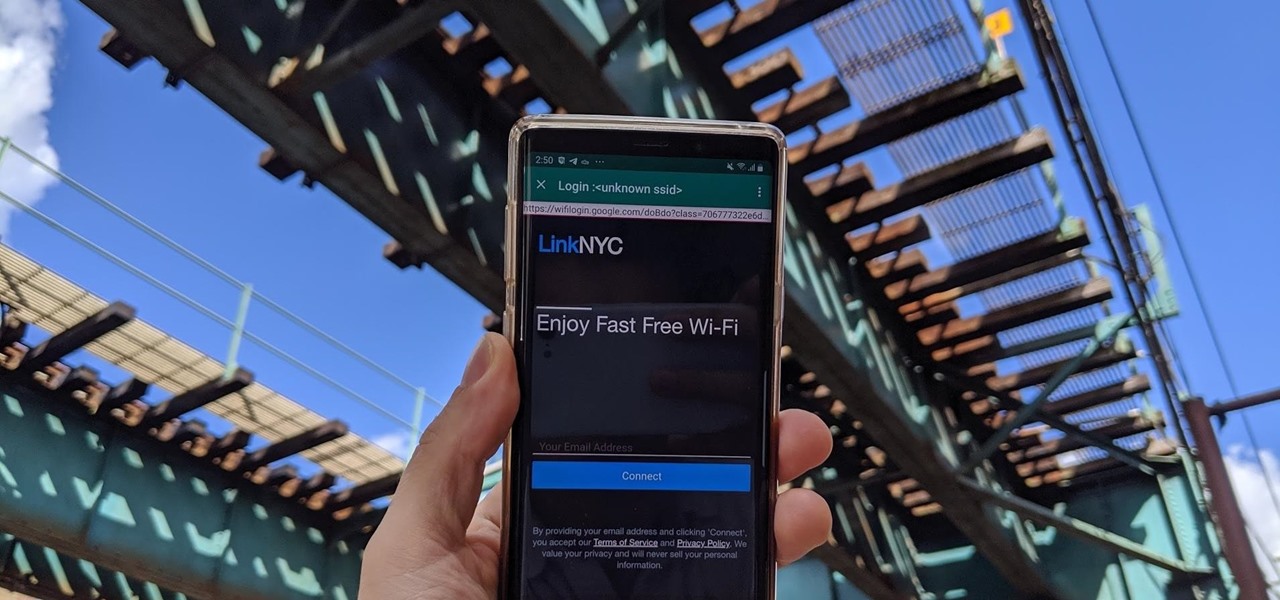
Public Wi-Fi networks that have a captive portal sign-in screen can sometimes be broken on Android. This seems to happen randomly and on some devices more than others. You'll get the "Sign into Wi-Fi network" notification, but it just doesn't work. If that's happening to you, you'll be glad to know an app can help fix the issue.

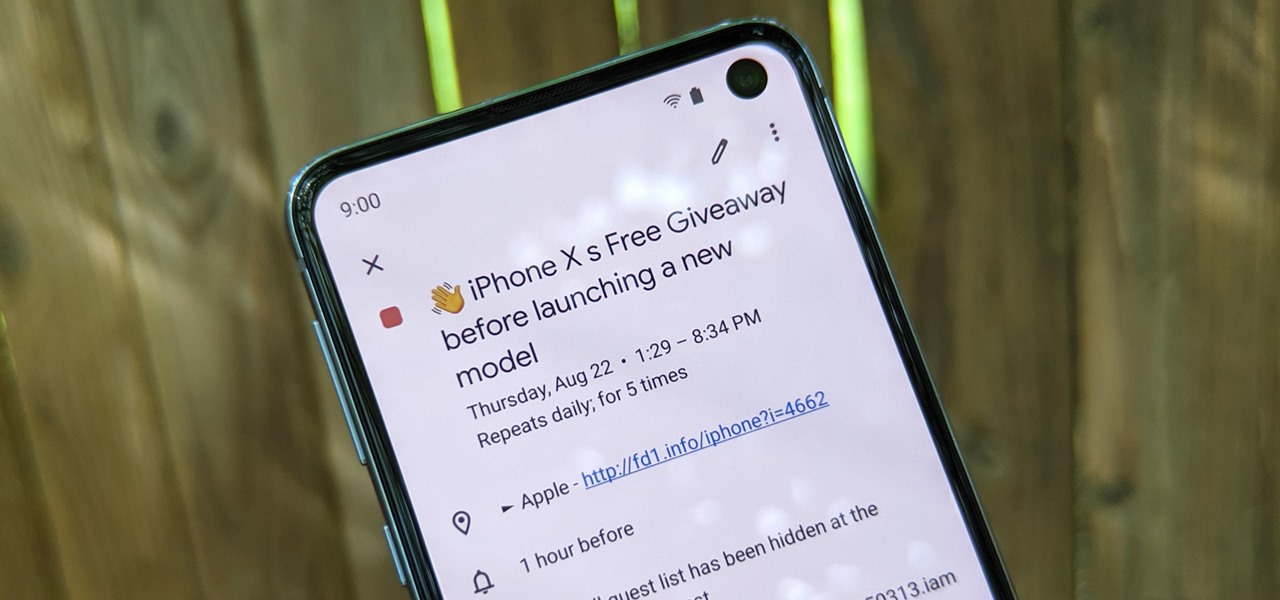
There have been hundreds of reports of Google Calendar users receiving notifications for events they didn't create. These "events" are actually spam ads and potential phishing threats. If this has happened to you, you're not alone — but luckily, there's a way to put an end to it.

Increasingly, cutting-edge platforms like blockchain technology and augmented reality are overlapping, forging new digital frontiers that promise to change the way we interact with the virtual and the real world.

One of the first steps in attacking a web application is enumerating hidden directories and files. Doing so can often yield valuable information that makes it easier to execute a precise attack, leaving less room for errors and wasted time. There are many tools available to do this, but not all of them are created equally. Gobuster, a directory scanner written in Go, is definitely worth exploring.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

It's been proven that hackers can manipulate your screen with fake taps through specific exploits, so they can potentially hit the "Grant" button when you get a superuser request. This is the last thing you'd want to happen since the malicious app from that point forward has full system privileges. Luckily, using a fingerprint to lock your superuser requests can prevent this.

Your Skype contact list might contain a sea of names that make it tough to find a specific person you're trying to reach. The same goes for your loved ones and colleagues, especially if you have a common name like Jennifer or John. Knowing that, you might want to change your Skype display name to set yourself apart.

After showing off a prototype of the Grordbattle multiplayer first-person shooter at the Game Developer Conference, Magic Leap has added a new Shared World feature in version 0.95.0 of the Lumin OS update released this week.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

Picture this: You finally get that awesome angle, the perfect selfie. You can't wait to post it on your Instagram, except there's one problem — it looks a little flat and the colors just seem off. Maybe it's the lights? Or maybe your new smartphone camera isn't as good as you thought? How are your friends getting those beautiful photos they've been posting on social media?

Snapchat made augmented reality selfie effects famous, with Facebook copying the feature across its mobile apps. Of course, others have followed, but their face tracking apps often pale in comparison to the original.

We are in the midst of a mini-boom for communications tools designed for augmented reality headsets, with the introduction of Avatar Chat and Mimesys for Magic Leap One and Spatial for the HoloLens within the last few months.

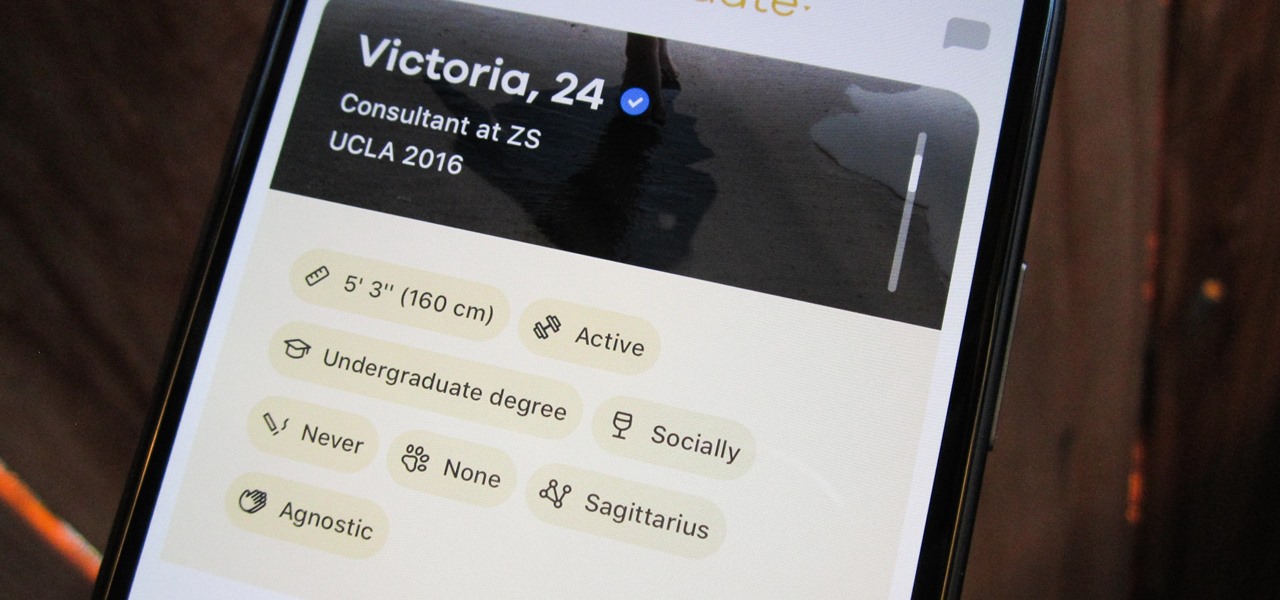
Despite Tinder's tremendous popularity, Bumble has carved out a billion-dollar business by focusing on women (they message first), simplicity (ice breakers less wordy than OkCupid), and relationships past romance (friends and prospective jobs). Now they're diving into customization, with filters that allow you to pore over prospective matches by height, religion, education, politics, and more.

So, you accidentally sent a voice message to someone in an Instagram DM. Maybe it contains an unflattering conversation about the recipient. Maybe it's a record of something embarrassing you said. Whatever your message contains, it's out there, on someone else's smartphone. You might think you're out of luck, and that your life is over. If you act quick, however, it won't be.

While Unity is already the leading 3D engine for augmented reality content in terms of volume, the announcement of Project MARS, a new augmented reality authoring tool, at Unite Berlin in June promised to expand AR development to a whole new audience of designers and other non-coders this fall.

On Sunday, Apple CEO Tim Cook (the number one person on our NR30 list) made a rare television appearance to talk about and show off his current obsession: augmented reality.

Despite the relatively small size of Magic Leap's first annual L.E.A.P. conference, there was a lot to see and experience. Apparently missed by many was one of the best experiences I had at the event: Wingnut AR's unreleased Pest Control game.

It turns out that Dr. Grordbort's Invaders is not the only Magic Leap demo to become a reality for the Magic Leap One.

Amazon Web Services is calling up an age-old tactic of the tech industry — the hackathon — to drum up excitement and encourage the development of apps built on the Amazon Sumerian AR/VR platform.

Having a dropped call can be incredibly frustrating, especially when you look down and see that your iPhone has full reception. While there's any number of issues that can cause this, one common and often overlooked issue is your iPhone failing to switch cell towers as appropriately needed.

In recent years, medical professionals have demonstrated how the HoloLens can assist in surgeries, ranging from collarbone repairs to spinal surgeries to cosmetic procedures. Now, the largest children's hospital in the United Kingdom is also ready to deploy the technology.

Will smartphone batteries ever last as long as we need them to? Perhaps not. That's why we rely on external batteries to help us stay connected for hours, even days, longer than usual. But in 2018, you don't want to use just any external battery. Modern Android phones have fast charging — so should your portable charger.

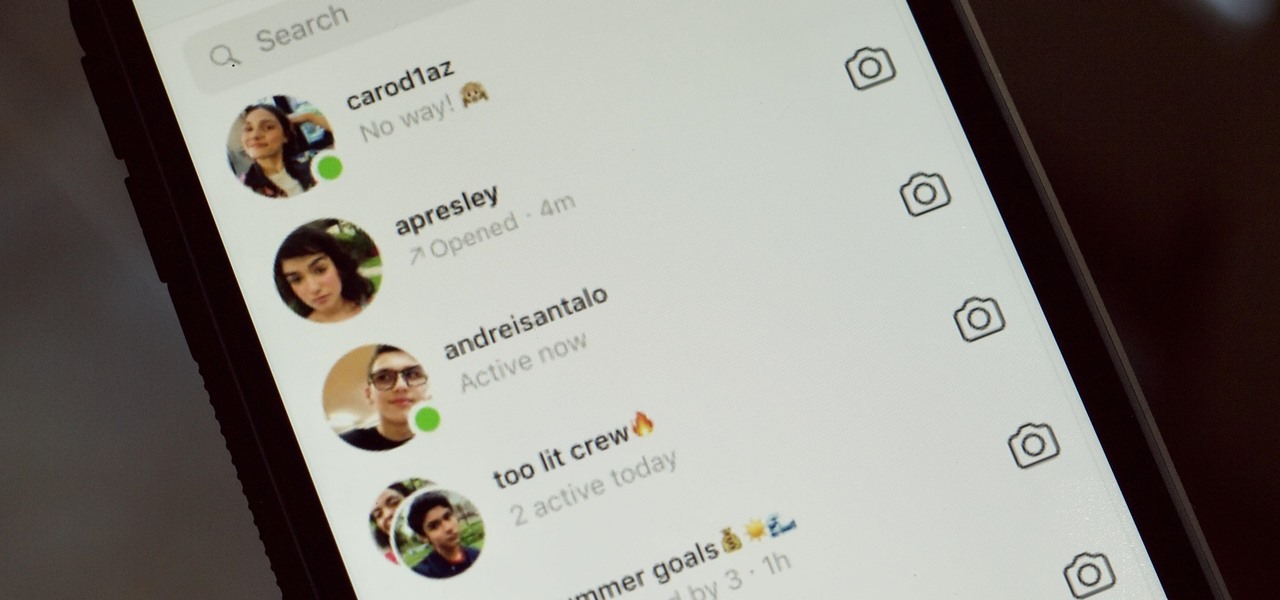
While it might be more common to chat with friends on apps like Twitter, Messenger, or WhatsApp, direct messages on Instagram are becoming more and more sophisticated. Case in point, the app is rolling out a new feature to users that shows a "green dot" next to friends who are online. Luckily, you don't have to let your followers know when you're browsing photos if you don't want to.

Data breaches are all too common now, and the latest one you need to know about involves Timehop, a mobile app that makes it easy to reminisce over old photos. The breach, which took place on July 4, was revealed on Sunday, July 8. At the time, Timehop disclosed that 21 million users had been affected by the breach, but it now appears that all users were impacted in some way.