It may be surprising, but those cardboard toilet paper tubes are dead useful for so many things besides just keeping the circular shape of your TP roll. As shown before, you can make car dash mounts for your mobile phone, but that's just one of the many beneficial uses from a seemingly junk cardboard tube. You probably go through quite a bit of bathroom tissue over the course of a year, especially if you're using it for facial tissues, too. So, the next time you throw away that lonely little ...

Mason jars are a DIYer's best friend, nearly on par with duct tape and paper clips. Why? Because you can use mason jars for so many things besides just canning and drinking, and I'm not talking about other obvious uses like basic storage containers or miniature terrariums. I'm talking about MacGyver-style ingenuity. With a little creativity, the uses for those jars are practically endless.

Thanks to everyone who submitted ideas in last month's Mad Science contest. The question called for your best idea for using Sugru, a temporarily malleable silicone modeling clay that self cures for a soft-touch permanent bond. It's a marvelous product for at-home quick fixes and for even making some cool DIY bumpers and grips for your electronics. William scoured through all of the comments and chose the two winners he felt best deserved a pack of Sugru.

WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the communities.

Today I would like to share a few data about painting on silk with all the creative readers. The knowledge comes in handy if you want to give a homemade gift or even try to sell a few of your masterpieces.

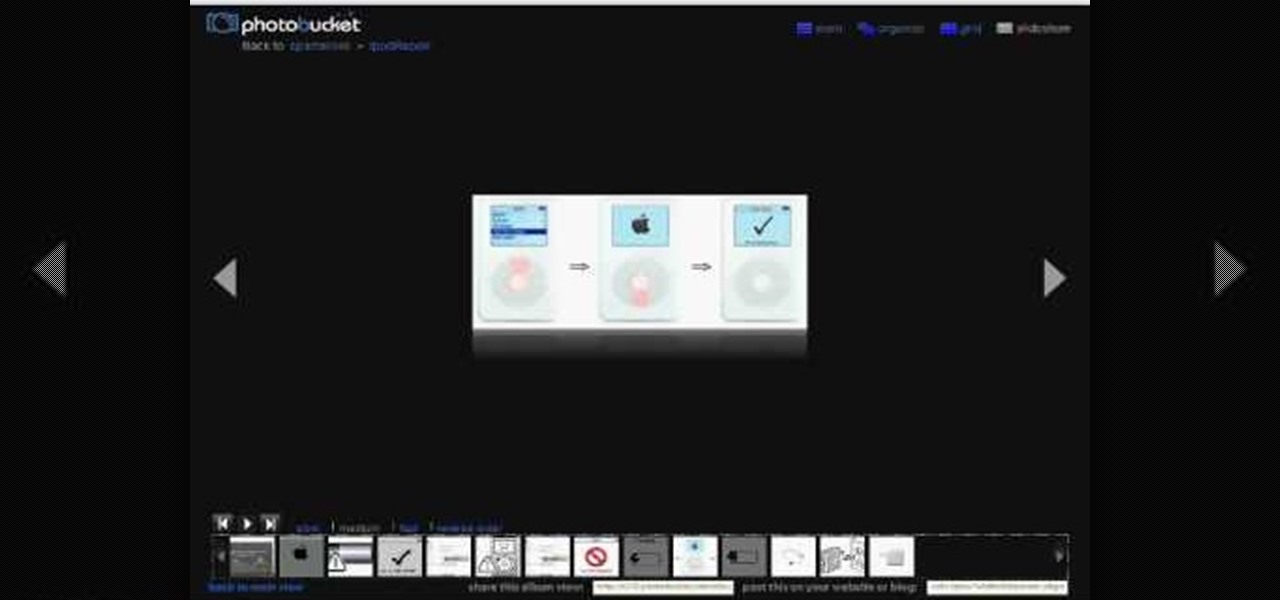
Have a tweaking Zen Vision M? Your battery might need replaced, so do it yourself instead of paying someone else to do it! You don't need to pay an expensive professional when you only need to pay for the battery. This step-by-step video demonstration will show you the procedure for replacing the battery in your Creative Zen Vision:M Portable Media Player. You can use the replacement battery found in the video, or any other replacement battery, the results are the same.

Does your car idle high and make an obnoxious racket every time you are stopped at a light, drawing dispproving looks from your fellow motorists? If you are into home car maintenance, you may be able to diagnose the cause of this problem yourself. This video illustrates how to test for one common problem that leads to a high idle, a faulty throttle position sensor, the contacts on which have been worn down by the throttle. You will need an analog multimeter to test the ohm load from the senso...

The great thing about having long hair, is the ability to do almost anything to it. You can flatten it, cut it short, place it in a ponytail and of course curl it. There are so many ways to curl hair, but one of the most easiest and common ways is by using a curling iron and some basic hair products such as hair spray, a comb, and of course, patience. Sit back and find out how to curl short hair easily in this tutorial. Enjoy!

In this tutorial video, hosted by harrymedan, you will learn how to fix a broken or nonfunctional select button on your iPod, as well as the common causes of the select button no longer working. According to the host this problem is usually caused by the battery in the iPod itself. He suggests opening up the back of the iPod and replacing the old battery, which is usually swollen from being charged so many times, and puts pressure on the select button causing it to become inoperable. If you a...

When you are tested for drugs, the drugs can be found in your hair and blood. There are three types of tests: hair test, blood test and urine test. The urine test, being the cheapest, is the most common drug test. Some ways to beat this unwanted drug screening is by drinking x-amount of water, this dilutes the drug within your system. The second method is to inform them that you are a user, or that you attend frequent rock concerts. (This method isn't recommended because of the outrageous amo...

Use a motor to make a fan and a speaker. People often take for granted the common items and devices they use in everyday life. Looks can be deceiving. It's not what things appear to be, it's what they can become.

It's time for some golf! What's an 18-year-old know about distance? Justin James can belt it 400 yards and more, and with his power tip, you too can tack on a few extra yards. Well, maybe not 400 yards, but you get the idea. See how to get more power out of your golf drive.

This truck repair video shows you how to remove the bed from a Chevrolet C1500 W/T truck. This needs to be done to fix certain problems, in this case the fuel lines. Whatever reason you need to remove the bed from your Chevy, this video shows you how to do it properly.

PEX, or cross-linked polyethylene, is a common alternative to copper piping. If you're looking to save time on your project (or have an aversion to soldering), PEX might be for you. In this tutorial, you'll learn what PEX is and how to decide what type of PEX is best for your application.

Learn what common time or 4/4 time is and how you can use it with this how to video. This music theory tutorial will help you understand the concept of time signatures and counting rhythm.

Dr. Ari Goldsmith discusses the diagnosis of swimmers ear and a few common treatments.

A Look into Internet Marketing including common pitfalls to avoid and how to build a userbase. Part 1 of 2 - How to Get into Internet Marketing.

The Mad Hatter from Tim Burton's Alice in Wonderland not only makes a great costume but a great project. The hour-glass shaped hat, the striped pants, the fingerless gloves, and the Hatter's signature scarf are the most important components in this costume. If you're fairly skilled with costuming already, this shouldn't take more than four or so hours.

Okay, so you've decided to take the plunge, and participate in our Love. Earn program with a how-to article. But, for whatever reason, your article keeps getting rejected by WonderHowTo, and you're wondering, well, where's the love?

First off, don't be frustrated. YOU CAN DO IT! Contrary to the message in the image above, it's NOT over. It's just beginning. And when it comes to solving the New York Times crossword puzzle, the old cliche does apply: practice makes perfect.

Calendars are usually pretty drab, lacking creativity and focusing on the basics… year, month, day, and holidays. Besides a usually visually striking picture for each month, these store-bought calendars are nothing to look at, but they can be with a little modification!

Peeling some fruits can be quite a nuisance. And some fruits are even impossible to peel, hence the watermelon. Mangos are something of the sort, you dont really 'peel' them persay but more of an extraction. Mangos are quite delicious but peeling can sometimes come with a little trouble. This video tutorial will demonstrate exactly how to peel a tropical mango with a creative approach. This is a great way to peel and cut a mango especially if you are making a salad, some juice, or anything in...

Get a crash course on HScript Expressions, Variables, and Attributes in Houdini 10. If you don't even know what this means, then you probably need to check this video tutorial series out. Understanding how to massage data in Houdini is key to giving yourself the creative edge and allowing you to unleash mind-blowing visual effects. This 18-part video series covers a variety of simple yet essential weapons in your arsenal including Global, Standard and Custom Variables to Math and String Modif...

Google Poly, a repository of 3D objects for use in AR and VR experiences, is the latest Google offering to fall victim to the company's habit of axing products and services, regardless of popularity.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

Smartphones have put an end to camcorders. If you want to capture memorable moments in high quality, look no further than that technological marvel in your pocket. Recent Galaxy phones are shining examples of how far we've come — but the more capable a camera gets, the more complicated things can be.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're concerned, you can take steps right now to beef up your passcode and prevent outsiders from gaining access to your device.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.

The world is full of vulnerable computers. As you learn how to interact with them, it will be both tempting and necessary to test out these newfound skills on a real target. To help you get to that goal, we have a deliberately vulnerable Raspberry Pi image designed for practicing and taking your hacking skills to the next level.

Microbial cells can improve the functionality of clothes in creative and useful ways, including cooling us down during a workout or making clothing glow for better visibility.

You may not have heard of visceral leishmaniasis, onchocerciasis, or lymphatic filariasis, and there is a reason for that. These diseases, part of a group of infections called neglected tropical diseases (NTDs), impact more than a billion people on the planet in countries other than ours. Despite the consolation that these often grotesque illnesses are "out of sight, out of mind," some of these infections are quietly taking their toll in some southern communities of the US.

In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.

If you live with pets, you know where their tongue has been, yet you let them kiss and lick you all they want without even thinking twice about it. I've heard people say that a dog's mouth is very clean, and that their saliva, delivered by licking, can help heal wounds, but is that really true?