It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

Almost every phone comes with biometric security of some sort these days, but the same can't be said of Windows computers. While fingerprint scanners are becoming increasingly common with laptops and desktops, they're nowhere near ubiquitous. Thankfully, your phone's scanner can be used as a sort-of remote authentication point for your PC.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Watch this video tutorial to learn how to calculate your carbon footprint. A carbon footprint is an equation that estimates just how much you, personally, are contributing to global warming—and all you have to do is plug some info into an online calculator. Figuring out how to make your footprint smaller, of course, is another matter.

Check out this Halloween tutorial video that shows how to make a display graveyard and its border fences.

Create lasting memories by organizing a well-planned family reunion. This video will show you how to organize a family reunion.

This video is on how to install the LED light kit onto your Axon Racing anti-gravity razorback racer hover.

Augmented reality is becoming a slam dunk for sports entertainment, as leagues, their teams, and their broadcast partners have been quick to adopt AR.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

Improved security options in iOS 12 provide you with automatic password suggestions, a way to find and change weak passwords, auto-filling of 2FA codes, and Siri integration. Most of these apply to iCloud Keychain, but Apple hasn't forgotten about users of third-party password managers; In iOS 12, you can use 1Password, LastPass, and others with the AutoFill feature in websites and apps.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

In this first part of my series on getting started with Windows Holographic, we are going to cover everything you need to get set up for developing HoloLens apps. There are many pieces coming together to make one single application, but once you get used to them all, you won't even notice. Now there are different approaches you can take to make applications for HoloLens, but this way is simply the fastest.

This is second post in my series of posts for finding hacked accounts online. Please do read the part 1 of the post at http://null-byte.wonderhowto.com/how-to/find-hacked-accounts-online-part-1-0164611/

SET is great when you have a short space of time at hand, however sometimes you want to know whats actually going on under the hood or have found a site you can't clone with SET.

When it comes to getting your computer and smartphone to work well together, there's no service more robust and capable than AirDroid. For years, it's been the go-to tool for users looking to transfer files between their devices or access contact lists and call logs from their computer.

When a Houston mom got tired of her kids seemingly refusing to return her calls, she decided that she'd take action. Sharon Standifird's vision was to create an app that would somehow force children to get into contact with their parents. Having no experience with app development, Standifird quickly taught herself the ropes and hired an experienced developer to help with coding.

Depending on who you ask, internet connectivity should be a basic human right. With Google recently embarking on a project to provide internet capabilities to remote corners of the world using balloons and satellites while Facebook attempts to do the same with unmanned drones, the concept of free web access is steadily gaining steam.

Welcome back, my hacker novitiates! Recently, I demonstrated a hack where you could redirect traffic intended for one site, such as bankofamerica.com, to your fake website. Of course, to really make this work, you would need to make a replica of the site you were spoofing, or better yet, you could simply simply make a copy of the original site and host it on your own server!

LastPass is a password manager that's been around for some time, and has finally made its way over to Android for use with apps, not just websites.

One of the most frustrating things on the Internet are sites that make you register just to view content. I'm not talking about paywalls—I mean the sites that make you give them personal information to look at free articles or forum threads. Most people are uncomfortable with this because a lot of these sites either spam you themselves, or sell your information to someone else who will.

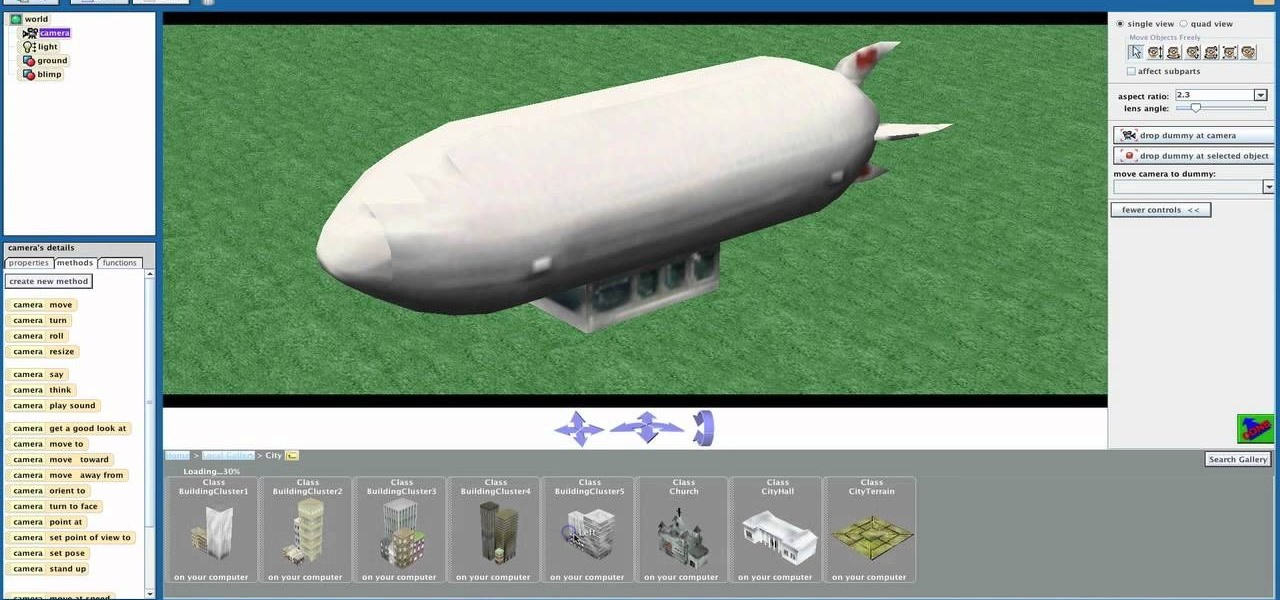
Shaun will teach us how to create a 3D video game compatible with MAC or PC with no prior programming knowledge. First download Alice, a 3D World program that can be turned into a video game. Open Alice, click on "add objects", click on "more controls" and select your choice of aspect ratio such wide screen. Now you can import your own 3D models that Shaun will show you at the end of the tutorial or choose from a wide selection that comes with Alice. In addition, if you click on "home," "web ...

Wash your face and make sure there are no oils or lotions. Use a toner or a makeup primer which you can purchase at drug store. Pull your hair off of your face with a headband. No hair should be near your face, ears or nape of neck. This is the oil undercoat for use with the 'Kabuki Oshiroi' Shiro-Nuri (Doran) face paint. It is softened in the hands and then rubbed over the entire face or other areas to prepare the skin for the white face makeup. This is the stiff wax used to flatten out faci...

Getting a Rapunzel-like mane takes time, but you can speed things up with these valuable tips. You Will Need

Got school spirit? The cheerleading squad's the perfect place for you. Here's how to make the team. Step 1

This video is on my break in method. I use half of the new school break in method and half of the traxxas. My method goes like this:

This video is on how to setup the axon racing anti gravity razorback racer. it involves receiver installation, zeroing your servo with the trims and lifting the horn, programming the esc, installing the lipo, testing the unit, initial turn on.

This video tutorial shows tips on applying Liquid Mask to your RC car body prior to painting. Liquid mask takes the place of masking tape while painting. Watch this video tutorial and learn how to easily prep the body of an RC vehicle before painting.

A side effect of the COVID-19 pandemic is that small businesses are suffering from forced closures and social distancing, but game developer Niantic has a solution.

There are countless ways in which you can turn your love of tech and coding into a full-fledged career — from developing apps and websites as a freelancer to working in the IT departments of small startups or major tech companies. But one of the best ways that you can put your programming skills to good use is to join the increasingly important world of cybersecurity.

Communication is an essential skill for successfully launching products. Whether you're developing the latest and greatest app or trying to get ahead of a large data science project, effective communicators are always in high demand.

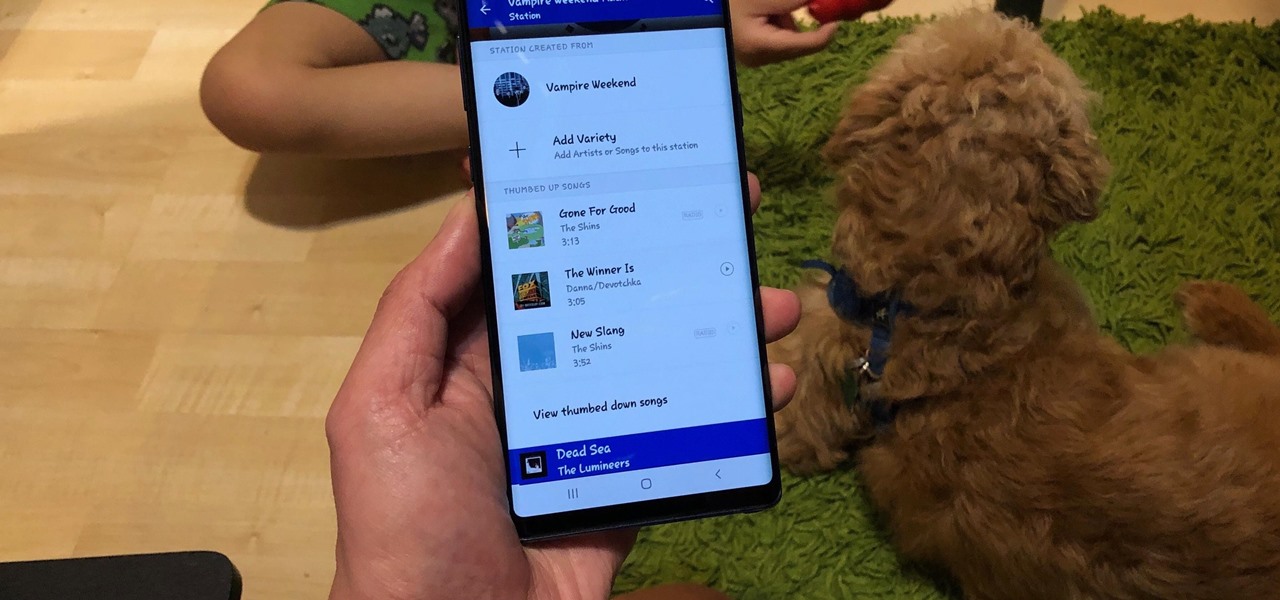
Pandora has a simple rating system that works by hitting either the thumbs-up or thumbs-down icon on a track that's playing on your station. If you choose the former, the song you like along with others similar to it will play with more frequency, while selecting the latter will prevent that song and others like it from playing in your station moving forward.

Augmented reality and drones already go together like turkey and stuffing, but a new iOS app adds some spice to the combination with a new kind of flight path automation.

Augmented reality experiences created in Lens Studio now have a permanent home in the Snapchat app. On Tuesday, Lens Explorer will begin giving users access to a scrollable screen full of a variety of new Lens Studio creations.

Two-factor authentication (2FA) is a great way to add another layer of security to sensitive third-party apps and websites like Venmo. However, before iOS 12, to log into a particular 2FA-secured app or site on your iPhone, you'd have to memorize or copy the SMS code from Messages, then jump back in a timely manner to log in. Apple's latest iOS version streamlines this process.

A newly-filed patent application from Disney Enterprises, Inc. teases more augmented reality lightsaber duels, either for at-home gaming or for the media behemoth's forthcoming Star Wars theme park.

Before starting any drive where you're using Google Maps for directions, it's vital to make sure the app is functioning correctly, specifically, navigation prompts. After initiating turn-by-turn directions on your Android or iPhone, the last thing you want to worry about is Google Maps not audibly telling you where or when to turn, especially in an unfamiliar area.

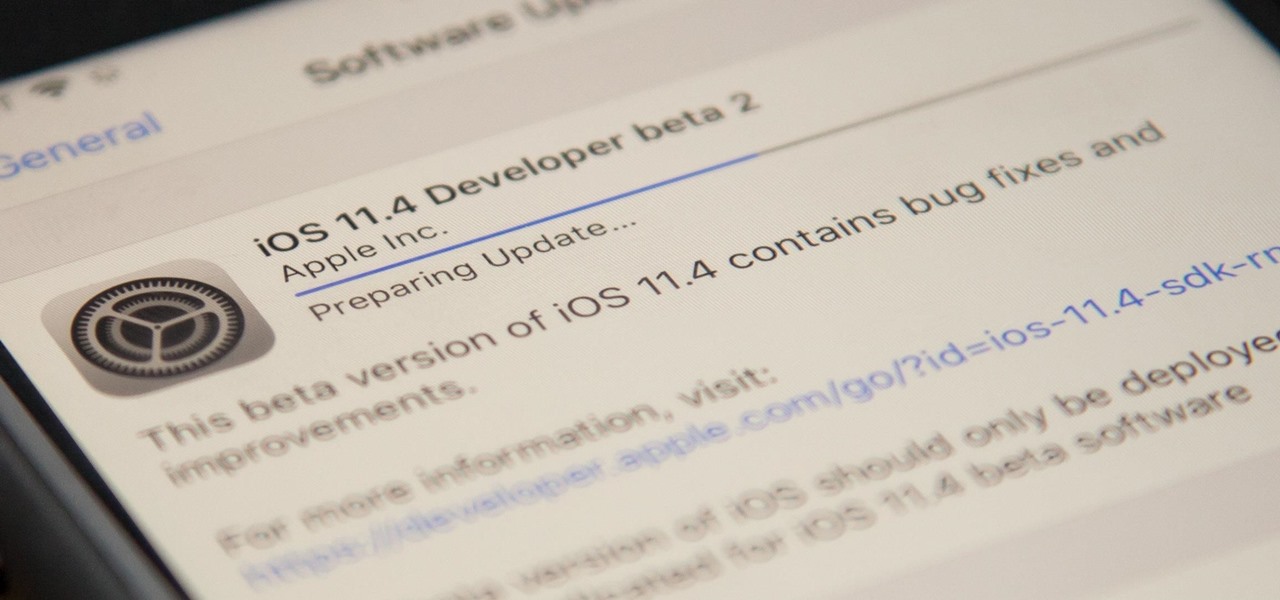
Apple released the second beta for iOS 11.4 on Monday, April 16. Its release comes eighteen days after the company pushed the first 11.4 beta to iPhones, as well as the official build of iOS 11.3. This beta fixes issues with AirPlay, Music, and Keychain, and it also adds a new wallpaper.

It's always a pleasure when your activity syncs across all of your devices. Herein lies another reason to use Samsung Internet — the app natively syncs with your open tabs on desktop Firefox. Anything you do on your computer can be easily accessible from your smartphone.