
Halloween Food Hacks: Make an Icy-Cold, Bloody Hand
We at Food Hacks Daily freakin' love Halloween—it's the perfect time for weird and creepy food. The gruesomer, the better.


We at Food Hacks Daily freakin' love Halloween—it's the perfect time for weird and creepy food. The gruesomer, the better.

Few companies have maintained such intense secrecy, in the face of such extreme hype, as Magic Leap, but the closer their mysterious Mixed Reality product comes to mass production, the harder it becomes to hide the details. Hopefully we'll find out way more details soon, as a Magic Leap job posting for a supply chain manager hint that they're readying for release in the next couple years.
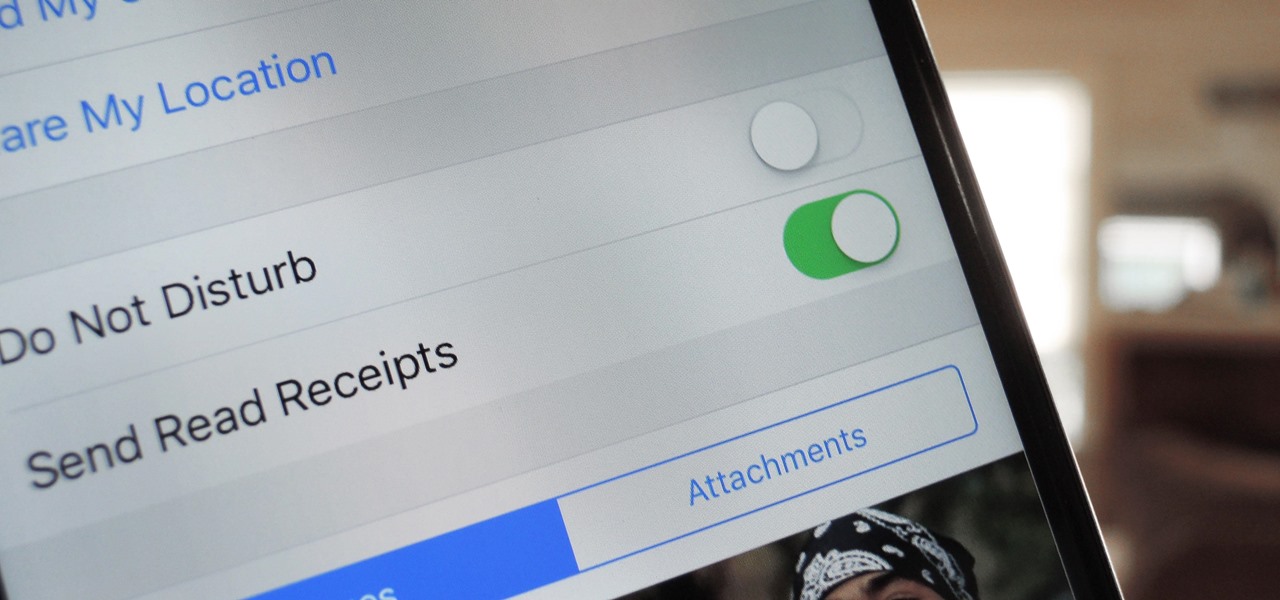
With iOS 9.3.5, as well as all of the versions prior to that, you had two choices when it came to "Read Receipts" for iMessage — either on for everybody or off for everybody. So if you weren't comfortable with one or two of your contacts knowing whether or not you've read their messages, you had to keep the feature disabled and miss out on Read Receipts for people you're a bit closer to.

Hola my fellow hackers! I promised you the tutorials on setting up RAT's and Botnets, but before jumping into those, i want you to know about the precautionary measures and detection of RATs which might be on the system without your prior knowledge. Of course the Anti-virus do most of the job but there are some RATs which slips past the Anti-viruses (This is where Hacker's skill come into play).

Aside from being able to change the wallpaper and add shortcuts, the Galaxy S4's lock screen doesn't offer much in the department of personalization. The lock screen is efficient and practical, but it's also a little bland.

Animal masks are always a popular option for Halloween, not just because you can pair them with practically any outfit, but because they never go out of date. They've been a staple of Halloween costumes starting from the 1900's, but possibly even prior to that. George Takei, of Star Trek popularity, even left a hilarious comment on Accoutrements' Horse Head Mask Amazon page, making puns left and right about the animal mask—a testament to how trendy these faux mammalian skins really are.

Let's just say it's been a pretty bad year for spies and government agencies and an even worse one for the privacy of U.S. citizens. Edward Snowden blew the lid off the NSA's spy program, and the FBI was recently discovered to have the ability to access your webcam any time they want—without triggering the "camera on" light. Yeah, that means those Justin Bieber lip sync videos you recorded weren't just for your private collection.
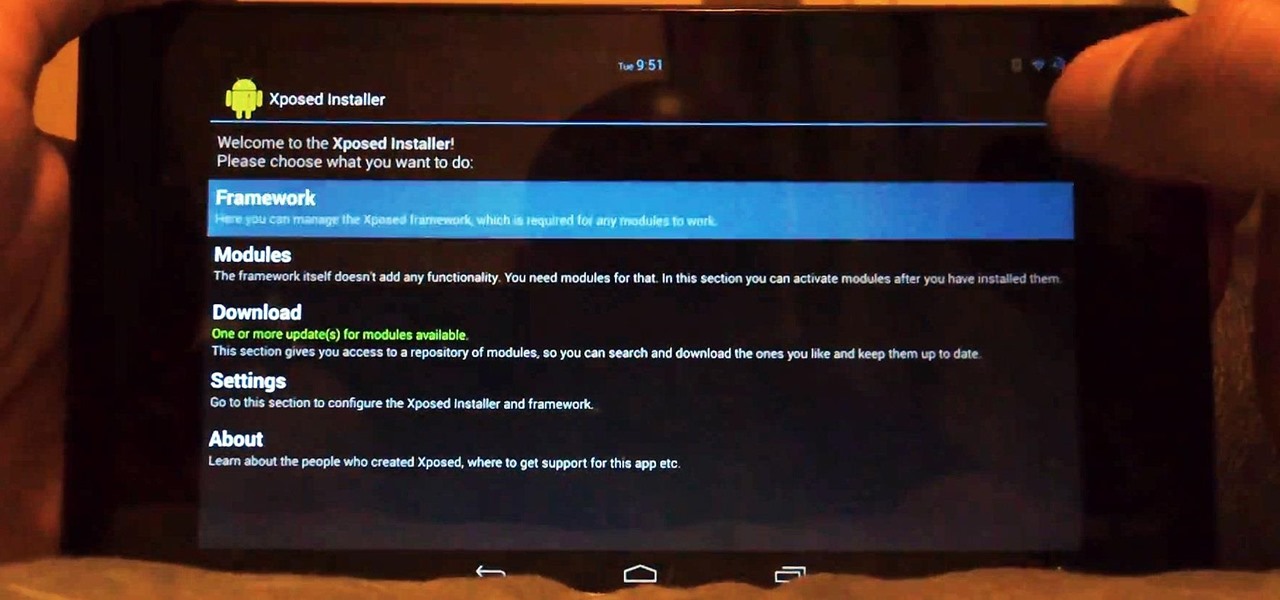
Customization of our Android devices, outside of what Google and mobile carriers allow us to do, used to mandate that our devices were rooted and running a custom ROM.

How can you tell if the pair of Ray-Ban Wayfarer sunglasses that you are about to buy online are not a fake? Follow these 9 simple steps to verify the authenticity of your purchase. Always ask the seller to use the youVerify app prior to purchase. It's Smarter Selling & Safer Shopping.

One of the best ways to reduce stress is to see a therapist. Interviewing a therapist can be tricky, but picking the right therapist for you is crucial. Get advice on reducing and managing stress in this stress management how-to video.

We all love the relaxing quality and lovely smell a burning candle adds to a room but it is frustrating when candles burn through too quickly. By taking into consideration the placement and properly prepping the candle you’ll give it a longer life.

Windows 10 passwords stored as NTLM hashes can be dumped and exfiltrated to an attacker's system in seconds. The hashes can be very easily brute-forced and cracked to reveal the passwords in plaintext using a combination of tools, including Mimikatz, ProcDump, John the Ripper, and Hashcat.

We've all seen the login pages that allow you to log in to third-party accounts using your credentials from Facebook, Google, or Twitter. It saves you the trouble of creating another account and remembering more passwords — but it can also become a privacy and security issue, which is why Apple created the "Sign in with Apple" feature for iOS 13.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.
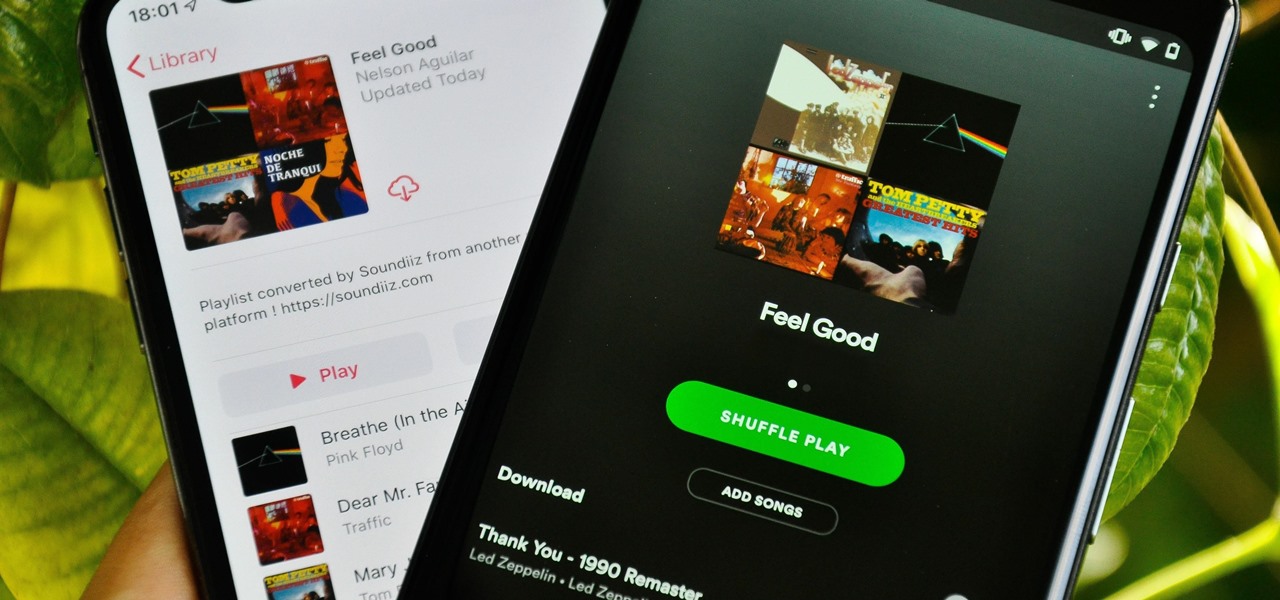
Music streaming services make it difficult to transfer your favorite songs and artists from one service to another and for a valid reason: they don't want you to leave. But when it comes to switching, playlists are a big concern, because who wants to do it all over again? Luckily, if you're moving from Spotify to Apple Music, you can use a third-party app to take playlists with you.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on.

Teresa Richardson from the crochet-mania blog will be teaching us how to crochet a left handed seed stitch scarf. In her video, she is going to be guiding us through the process of crocheting single and double seed stitches as well as providing us with step by step instructions on how to make the scarf. Teresa designed this tutorial with beginners in mind, so newcomers are more than welcome to utilize and learn from it as well. Be sure to have a crochet needle and some yarn handy prior to wat...

Learn how to understand the Difference between Chinese ink and watercolor with Chinese paintings. There are several differences between ink and watercolor art. Learn how to spot these variations with this video tutorial from Blue Heron Arts. This tutorial shows the differences between Chinese and Western culture paintings, which is largely rooted in the use of rice paper in Chinese artwork as well as the stretching of the paper prior to painting. Additionally, different types of paints are us...

This video gives instructions on how to cite sources when giving a speech. When giving a speech, you want to appear persuasive and credible to the audience. In order to do this, you must cite the sources of your speech's content. Prior to giving your speech, research materials relevant to your topic. In the course of giving the speech, mention where you got your data. In this case, the speech is about Emotional Intelligence in the Workplace. While making your first main point, mention that "a...

Playing popular songs on the guitar is not as difficult as it seems. With this tutorial you can learn how to play "Roll Out the Barrel" by Milburn on the acoustic guitar. This lesson is geared towards intermediate guitarists because it assumes prior knowledge of guitar playing. Marty Schwartz covers the finger picking as well as the chord structure for "Roll Out the Barrel." Watch this how to video and you will be able to sing and play "Roll Out the Barrel" by Milburn.

Playing popular songs on the guitar is not as difficult as it seems. With this tutorial you can learn how to play "SOS" by the Jonas Brothers on the acoustic guitar. This lesson is geared towards intermediate guitarists because it assumes prior knowledge of guitar playing. Marty Schwartz covers the finger picking as well as the chord structure for "SOS." Watch this how to video and you will be able to sing and play "SOS" by the Jonas Brothers.

Want to learn how to play guitar like Brit Daniel from Spoon? In this how to video you can learn how to play "Paper Tiger" by Spoon on the guitar. "Paper Tiger" uses the capo in the 5th fret in standard tuning and the chords are Am, Em, F, C. This lesson is geared towards intermediate to advanced guitarists because it assumes some prior knowledge of guitar playing. With this how to video you will be able to sing and play "Paper Tiger" by Spoon on the guitar.

Want to learn how to play Lifehouse on the guitar? With this tutorial you can learn how to play "You and Me" by Lifehouse on the acoustic guitar. This version is a simplified version of the song and is not exactly how Lifehouse plays it. This lesson is geared towards intermediate guitarists because it assumes prior knowledge of guitar playing. Watch this how to video and you will be able to sing and play the guitar along to "You and Me" by Lifehouse.

Want to learn how to play Matt Wertz on the guitar? With this tutorial you can learn how to play "5:19" by Matt Wertz on the acoustic guitar. This version is a simplified version of the song and is not exactly how Matt Wertz play it. This lesson is geared towards intermediate guitarists because it assumes prior knowledge of guitar playing. Watch this how to video and you will be able to sing and play the guitar along to "5:19" by Matt Wertz.

Want to learn how to play Howie Day on the guitar? With this tutorial you can learn how to play "Collide" by Howie Day on the acoustic guitar. This version is a simplified version of the song and is not exactly how Howie Day plays it. This lesson is geared towards intermediate guitarists because it assumes prior knowledge of guitar playing. Watch this how to video and you will be able to sing and play the guitar along to "Collide" by Howie Day.

Want to learn how to play Nickleback on the guitar? With this tutorial you can learn how to play "How You Remind Me" by Nickleback on the acoustic guitar. This version is a simplified version of the song and is not exactly how Nickleback plays it. This lesson is geared towards intermediate guitarists because it assumes prior knowledge of guitar playing. Watch this how to video and you will be able to sing and play the guitar along to "How You Remind Me" by Nickleback.

Want to learn how to play Bryan Adams on the guitar? With this tutorial you can learn how to play "Summer of 69" by Rascal Flatts on the electric guitar. This version is a simplified version of the song and is not exactly how Rascal Flatts play it. This lesson is geared towards intermediate guitarists because it assumes prior knowledge of guitar playing. Watch this how to video and you will be able to sing and play guitar along with "Summer of 69" by Bryan Adams.

Want to learn how to play Buckcherry on the guitar? With this tutorial you can learn how to play "Sorry" by Buckcherry on the acoustic guitar. This version is a simplified version of the song and is not exactly how Buckcherry plays it. This lesson is geared towards intermediate guitarists because it assumes prior knowledge of guitar playing. Watch this how to video and you will be able to sing and play guitar along to "Sorry" by Buckcherry.

Want to learn how to play Jason Mraz on the guitar? With this tutorial you can learn how to play "I'm Yours" by Jason Mraz on the acoustic guitar. The capo is on the 4th fret in standard tuning. This version is a simplified version of the song and is not exactly how Jason Mraz plays it. This lesson is geared towards intermediate guitarists because it assumes prior knowledge of guitar playing. Watch this how to video and you will be able to sing and play along to "I'm Yours" by Jason Mraz.

Want to learn how to play "Superman" on the guitar? With this tutorial you can learn how to play "Superman" by Joe Brooks on the acoustic guitar. The capo is placed on the 10th fret in standard tuning. This version is a simplified version of the song and is not exactly how Joe Brooks plays it. This lesson is geared towards intermediate guitarists because it assumes prior knowledge of guitar playing. Watch this how to video and you will be able to sing and play guitar along to "Superman" by Jo...

Want to learn how to play Matchbox Twenty on the guitar? With this tutorial you can learn how to play "Unwell" by Matchbox Twenty on the acoustic guitar. This version is a simplified version of the song and is not exactly how Matchbox Twenty plays it. This lesson is geared towards intermediate guitarists because it assumes prior knowledge of guitar playing. Watch this how to video and you will be able to sing and play along to "Unwell" by Matchbox Twenty.

Want to learn how to play Staind on the guitar? With this tutorial you can learn how to play "Everything Changes" by Staind on the acoustic guitar. This version is a simplified version of the song and is not exactly how Staind plays it. This lesson is geared towards intermediate guitarists because it assumes prior knowledge of guitar playing. Watch this how to video and you will be able to sing and play along to "Everything Changes" by Staind.

Want to learn how to play 2face Idibia on the guitar? With this tutorial you can learn how to play "African Queen" by 2face Idibia on the acoustic guitar. This version is a simplified version of the song and is not exactly how 2face Idibia plays it. This lesson is geared towards intermediate guitarists because it assumes prior knowledge of guitar playing. Watch this how to video and you will be able to sing and play along to "African Queen" by 2face Idibia.

Learning to play your favorite songs on your guitar is not only a wonderful way of passing the time–and impressing those whom you'd like to impress–, it can do wonders for your technique. In this song tutorial from Siggi Mertens' series of beginning guitar lessons, you'll learn how to play "Song of Joy." While this video tutorial is geared towards beginners, it assumes at least some prior knowledge of guitar playing and its jargon. Take a look to get started playing "Song of Joy"!

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

The idea of a world without passwords used to be a pipe dream. But as we inch closer to making that a reality, we have services now that securely store all of our passwords under a single master password. It's a convenient way to keep our accounts safe and sound without having to remember all of their credentials. And there's no reason to be afraid — I'll explain why.

Imagine a scenario where you're nowhere near your iPhone, but it's on loud, and you really need to silence it. An alarm may be blaring, notifications could be spitting out sounds left and right, and calls may be ringing. Things can get annoying real quick for whoever's around it. Plus, all that attention makes it easy for someone to find and possibly steal your iPhone. Luckily, you can quiet it down.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

Can you be too lazy for video games? That's how I feel sometimes. I want to play the latest PlayStation has to offer, but I can't be bothered to get out of bed. As if Sony read the minds of lethargic gamers everywhere, the company has released an amazing thing — PS4 Remote Play allows you to play your PS4 on your iPhone, no TV required. The best part? It's 100% free.