When your iPhone goes missing, it's serious business. Depending on your usage, your whole life might be connected to your iPhone, not the least of which includes debit cards, credit cards, and Apple Pay Cash stored in Apple Pay. While it's nearly impossible for someone to use your money with Apple Pay, it's still a good idea to disable it until you find your iPhone, just in case.

If you store important, sensitive information on your iPhone in Notes, you'll want to be more careful. When Notes syncs across your iPad and Mac via iCloud — devices that family members or coworkers may share — you run the risk of having your notes read, edited, and deleted by other people. Such a catastrophe is easily avoided.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

I've seen my fair share of heartbreaks when it comes to used phones. As a repair tech, I often had to try and help out customers who bought used handsets which turned out to be useless, either because it was stolen or not working on their carrier's network. More often than not, there was very little I could do. To help you from being stuck in the same situation, here are some tips to prevent you from getting scammed out of your hard earned money when buying a used handset.

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

Volleyball has numerous unique rules. For example, volleyball is one of the only sports that does not allow throwing or catching the ball. Learn the rules of volleyball in this video tutorial.

The underhand serve is a passive and slower volleyball serve designed to only get the ball over the net and, as you will see in this sports video, is very easy to return. Learn how to serve underhand in this volleyball video tutorial.

Advanced defensive techniques are important in getting to balls that are hit into difficult positions. Whether the ball is hit low, to the side or high, the volleyball player must be prepared. Learn how to do advanced defensive techniques in this volleyball video tutorial.

The volleyball attack can excite the crowd and devastate the opposing team. The approach, jump and landing are the basic aspects of a successful volleyball attack. Learn how to attack in this volleyball video tutorial.

The jump serve is an aggressive overhand volleyball serve designed to score quickly and, as you will see in this sports video, is very difficult to return. Learn how to jump serve in this volleyball video tutorial.

Serve receiving in volleyball depends upon a proper beginning posture and correct footwork. Learn how to receive serves in this volleyball video tutorial.

The setter in volleyball is one of the most important positions because they set up the spike which, in many cases, ends in a point if the set is done right. Watch these setting tips in this sports video tutorial.

The volleyball middle hitter attacks from both in front of the setter and sliding behind the setter. Learn how to be a middle hitter in this volleyball video tutorial.

Perfect body position allows the volleyball player to execute effective techniques on both offense and defense. Learn how to get into perfect body position in this volleyball video tutorial.

The overhand serve can be placed with great accuracy and power and, as you will see in this sports video, is difficult to return. Learn how to serve overhand in this volleyball video tutorial.

The volleyball defensive priority is to contact the ball in the body's midline. Maintaining perfect body position is essential to good volleyball defense. Learn how to play defense in this volleyball video tutorial.

Tennis is a great summer sport, which makes having a great forehand essential for any tennis player. Learn how to improve your forehand swing in this tennis video.

Tennis is a great summer sport, and a great backhand is essential to being a good tennis player. Learn how to improve your backhand swing in this video tennis tutorial.

Playing popular songs on the guitar is not as difficult as it seems. With this tutorial you can learn how to play "Lithium" by Evanescence on the acoustic guitar. This lesson is geared towards intermediate guitarists because it assumes prior knowledge of guitar playing. Marty Schwartz covers the finger picking as well as the chord structure for "Lithium." Watch this how to video and you will be able to sing and play "Lithium" by Evanescence.

Want to learn how to play Red Jumpsuit Apparatus on the guitar? With this tutorial you can learn how to play "Your Guardian Angel" by Red Jumpsuit Apparatus on the acoustic guitar. This version is a simplified version of the song and is not exactly how Red Jumpsuit Apparatus plays it. This lesson is geared towards intermediate guitarists because it assumes prior knowledge of guitar playing. Watch this how to video and you will be able to sing and play along to "Your Guardian Angel" by Red Jum...

Want to learn how to play Nickleback on the guitar? With this tutorial you can learn how to play "Hero" by Nickleback on the acoustic guitar. This version is a simplified version of the song and is not exactly how Nickleback play it. This lesson is geared towards intermediate guitarists because it assumes prior knowledge of guitar playing. Watch this how to video and you will be able to sing and play along to "Hero" by Nickleback.

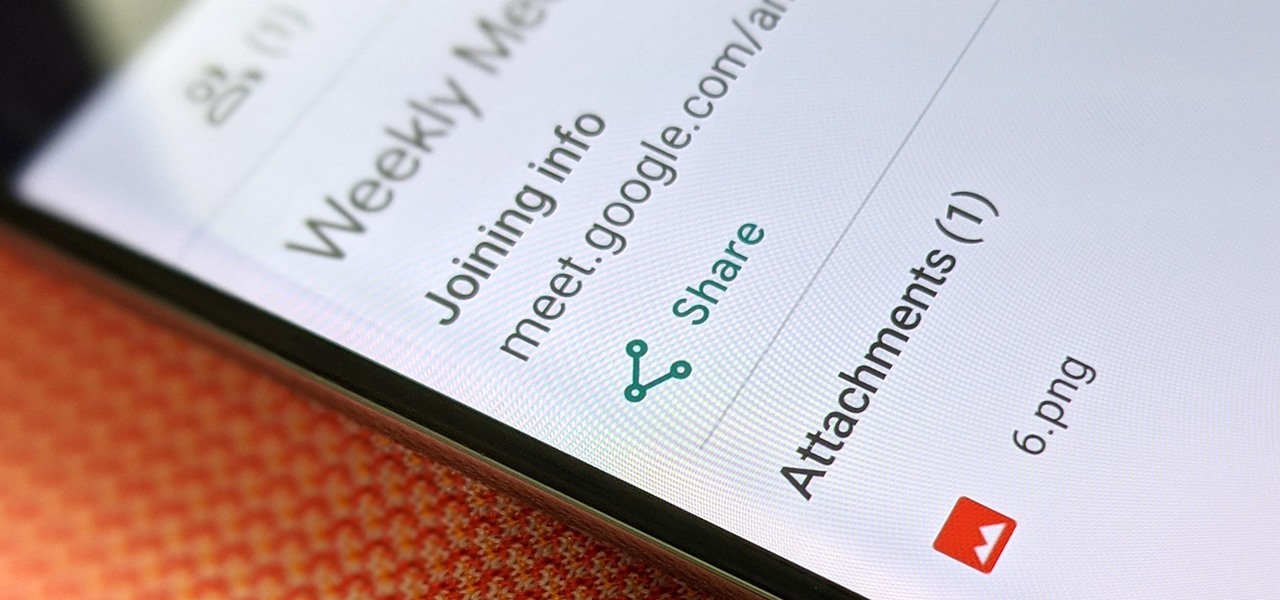
Google Meet might not have virtual backgrounds like Zoom, but it hits all of the other basics, from hosting many multiples of video participants to sharing your screen, that you'd expect from a robust video conferencing platform.

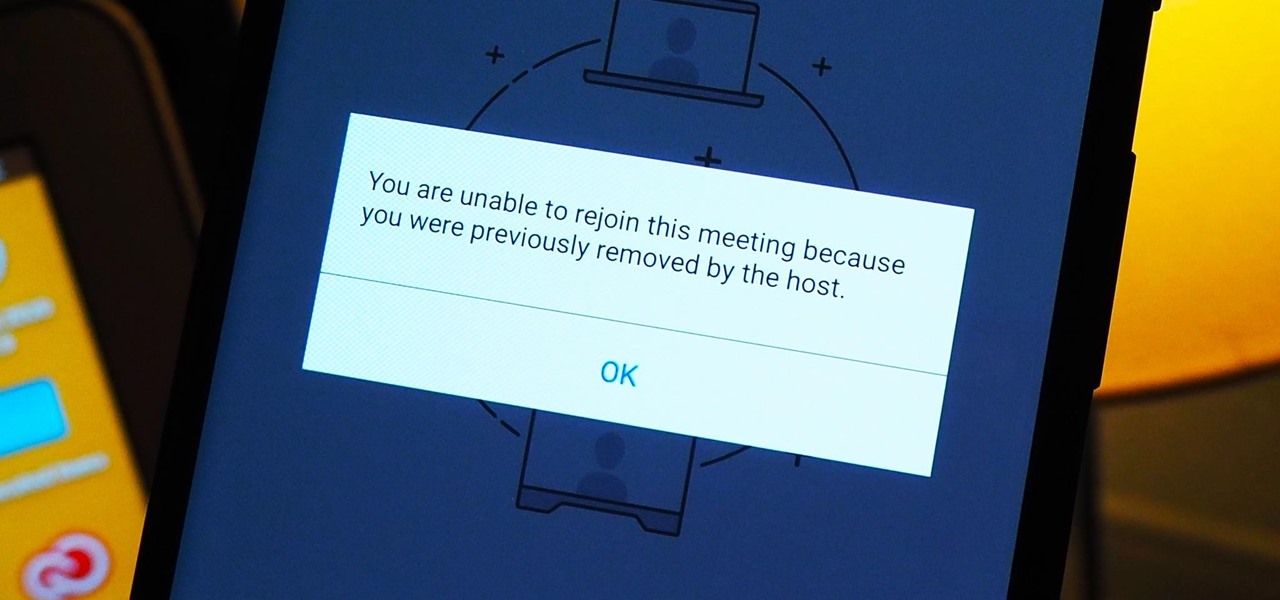
As more and more people use the video conferencing service Zoom, the chances of trolling behavior and attacks only increase. But it's not just "Zoombombers" you need to worry about. A heated discussion between family, friends, or colleagues could turn sideways real quick, and sometimes the best course of action is to remove the participant from the group video meeting altogether.

We're living in uncertain times. The sudden outbreak of the novel coronavirus and subsequent self-isolation of roughly half the world's population has led to a massive reorganization of the economy, countless layoffs, compromised security networks, and a variety of other significant disruptions that will forever alter the landscape of our daily lives.

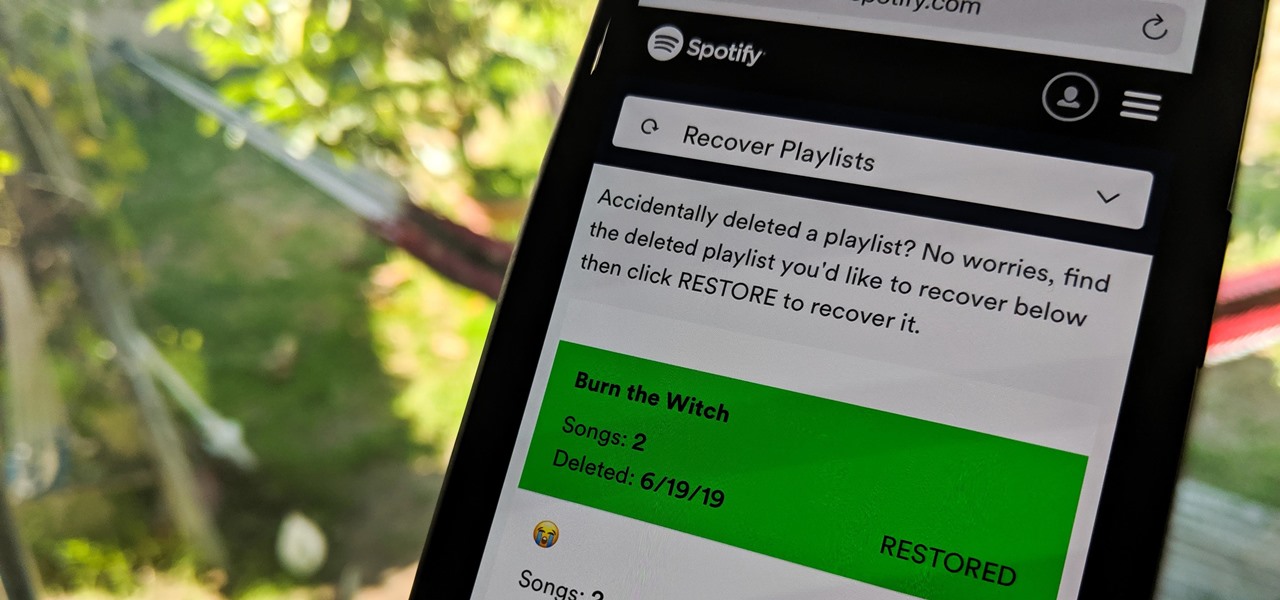
Absentmindedly or accidentally deleting your favorite Spotify playlist — which you spent hours or even days meticulously crafting — may seem devastating because there's no obvious way to bring it back. However, there is a hidden setting in the popular streaming service that can help you recover deleted playlists — you just need to know where to look.

The last third season episode of Rick and Morty aired Oct. 1, 2017. Over a year and a half later, we finally have confirmation that everyone's favorite morally ambiguous, universe-traveling duo will make their return in November. While six months is still quite a wait, you can make it go faster by catching up on some classic episodes.

When setting up a Raspberry Pi, it's easy to overlook changing the default password. Like many IoT devices, the Raspberry Pi's default Raspbian operating system installs with a widely-known default password, leaving the device vulnerable to remote access. Using a tool called rpi-hunter, hackers can discover, access, and drop custom payloads on any weak Pi connected to the same network.

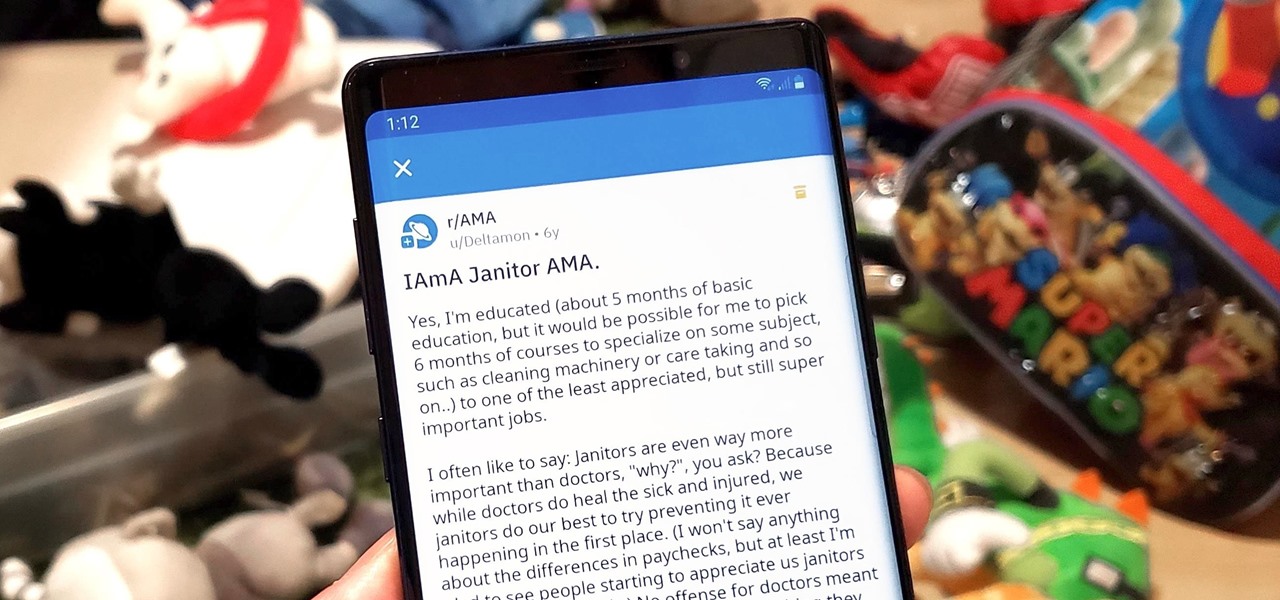
Short for Ask Me Anything, AMA threads are one of Reddit's signature features. They enable you to directly interact with a whole range of interesting personalities, from common folk with amazing life experiences to influential celebrities that help shape politics and culture.

Thanks to leaks that let us try out the latest Android Pie beta on the Galaxy S9, we already have a good idea of what the update has in store for Samsung's flagships moving forward. As we've come to expect, Android 9.0 brings a slew of notable updates, such as the addition of a system-wide dark theme and an all-new TouchWiz replacement called "One UI."

These days, it seems new phones get announced every other week. We've grown accustomed to glossing over the specs, looking at some press renders, then moving on to check out the next phone. If you had done this in September 2008, you might have overlooked what would become one of the most important phones of all time.

Attention all Redditors: Between June 14 and June 18, Reddit experienced a data breach. The popular website claims it discovered the breach on June 19 and has since made the necessary moves to contain and eliminate the threat. Unfortunately, there isn't much they can do about the data was that accessed and stolen — your user data.

MLB.TV is a great service that lets you watch most Major League Baseball games in North America, as long as you're a subscriber, of course. While I personally love it, blackouts can ruin the ability to watch my favorite teams. Fortunately, MLB At Bat Android users have an easy way to bypass blackout restrictions — and with no root required.

Coinbase sets itself apart from other wallet apps by making cryptocurrency transactions incredibly convenient. You can easily withdraw cash from the app and deposit it into your bank account within days — and now, if you want to cut the time from days to mere minutes, Coinbase has you covered as well.

There's a new macOS vulnerability that hackers within physical reach of your computer can use to gain root access to your system and accounts. Just by using "root" as the username and a blank password on a privilege escalation prompt, someone can install malware on your computer, access hidden files, reset your passwords, and more. Root access gives them the ability to do anything they want.

It looks like there is a fatal flaw in the current macOS High Sierra 10.13.1, even straight from the login menu when you first start up the computer. This severe vulnerability lets hackers — or anyone with malicious intentions — do anything they want as root users as long as they have physical access to the computer.

In a classic case of one step forward, two steps back, Apple has eliminated the ability to use multiple iCloud accounts for FaceTime and Messages in iOS 11, meaning the primary Apple ID on the account is the only one allowed. As inconvenient as this omission is, there's still a way to use alternate iCloud accounts on your iPhone with a little hackery.

Though not quite as agile as the world famous plump plumber Mario, Toad, the lovable fungus, is still one of the most fun characters to use while playing Super Mario Run. Thankfully, he is also by far the easiest character to unlock in the game, requiring no special tasks to complete.