Want to learn how to play Chuck Wicks on the guitar? With this tutorial you can learn how to play "Stealing Cinderella" by Chuck Wicks on the acoustic guitar. The capo is on the 1st fret used in standard tuning. This version is a simplified version of the song and is not exactly how Chuck Wicks play it. This lesson is geared towards intermediate guitarists because it assumes prior knowledge of guitar playing. Watch this how to video and you will be able to sing and play along to "Stealing Cin...

Want to learn how to play Rascal Flatts on the guitar? With this two part tutorial you can learn how to play the intro to "Bless the Broken Road" by Rascal Flatts on the acoustic guitar. This version is a simplified version of the song and is not exactly how Rascal Flatts play it. This lesson is geared towards intermediate guitarists because it assumes prior knowledge of guitar playing. Watch this how to video and you will be able to sing and play along to "Bless the Broken Road" by Rascal Fl...

Want to learn how to play Rascal Flatts on the guitar? With this tutorial you can learn how to play "What Hurts the Most" by Rascal Flatts on the acoustic guitar. The capo is on the 1st fret used in standard tuning. This version is a simplified version of the song and is not exactly how Rascal Flatts play it. This lesson is geared towards intermediate guitarists because it assumes prior knowledge of guitar playing. Watch this how to video and you will be able to sing and play along to ""What ...

Check out this instructional video that shows how to set up a prop static ghost for Halloween.

Welcome back everyone. I apologize for the lack of training articles, but I've been rater busy lately. I've recently picked up a second job and my college courses are now back in session, so I'm a bit strapped for time.

I'm no coupon-cutter (I just don't have the patience for it, sadly), but I do love buying things in bulk to save a buck or two. And one of the staples on my bulk-buy list is chicken; I cook with chicken so often that trying to save money on it is a no-brainer.

Hackers have stolen over 225,000 Apple user's account information from countries all over the world—including the United States, China, and France—in what many are reporting to be the biggest known Apple hack in history.

A recently discovered bug in iOS 8's Mail app by Jan Soucek can allow the maliciously-minded to quite easily phish your iCloud password without you ever thinking something has gone awry. Using a bug that allows remote HTML content to be loaded in place of the original email content, unsuspecting victims would be prompted for iCloud credentials in a popup that resembles the native one found on iOS.

Sideloading apps on Android is incredibly easy—you just have to enable "Unknown sources" in your device's Security settings, then you're free to run an APK installer file to get the app installed.

Thanks to a couple of photoshopped images that made rounds across Twitter last year, iPhone users were duped into thinking that iOS 8 included a security feature that would lock individual apps. Of course, none of it ended up being true, but we covered other features and apps that could accomplish roughly the same thing.

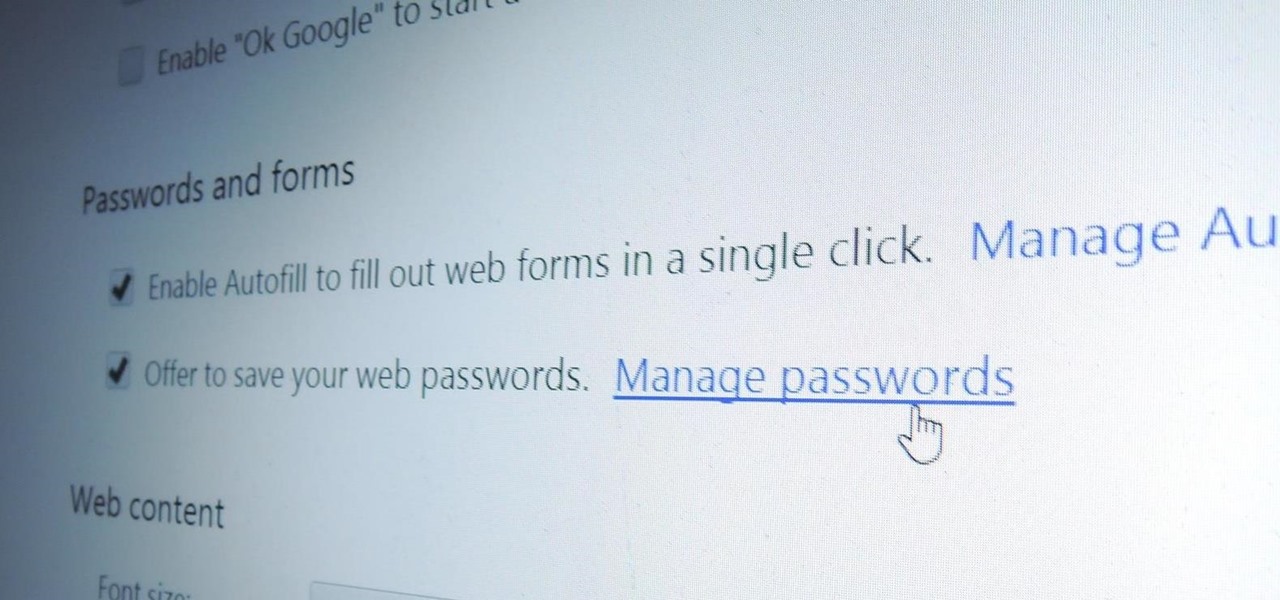
Chrome, Firefox, and Safari all provide built-in features that allow you to save your username and password for your favorite sites, making the process for entering your credentials a breeze when you revisit them.

The folks behind StumbleUpon have created a video service that is just as awesome at introducing you to new content as their website service is.

The following video will demonstrate a simple process by which hard-boiled eggs can be scrambled prior to cooking, creating a deliciously blended center once finished.

XSS Shell is a cross-site scripting backdoor into the victim's browser which enables an attacker to issue commands and receive responses. During a normal XSS attack an attacker only has one chance to control a victim's browser; however, the XSS Shell keeps the connection between the attacker and the victim open to allow the attacker to continuously manipulate the victim's browser. XSS Shell works by setting up an XSS Channel, an AJAX application embedded into the victim's browser, that can ob...

The arrival of Magic Leap One is tantalizingly close and, although the company has been saving the last details for launch day, a few of the more important details were found this week hiding deep in the code on Magic Leap's website.

ER showed the world what goes on inside the emergency room, and in every episode, we experienced a common but very important procedure— intubation. But ER never made it seems easy; it showed just how hard it is for medical students to successfully intubate a patient due to fear and naivety. And for real-life doctors and medical practitioners, learning the art of airway management is just as difficult.

The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.

Most alarms just make noise to wake you up, and it can be a bit jarring coming off of a deep sleep to suddenly being woken up by a blaring sound. On the flip side, if you're a heavy sleeper, this might not even be enough stimuli to snap you out of your 8-hour coma.

One of the hardest things a man can go through in life is a trip to the hospital, especially when he knows he's going to need a catheter. It's every man's worst fear. But for a nurse, it's necessary knowledge. Learning the male urinary catheterization procedure hands-on is difficult due to the urgency involved in patient care, so this video aims to prepare nurses so they can learn and stay fluent with the proper urinary catheterization technique of a male patient.

In many situations, learning proper medical procedures is difficult due to the urgency involved in patient care, so this video aims to prepare nurses so they can learn and stay fluent with the proper urinary catheterization of a female patient.

The Tree of Life Rejuvenation Center has created this instructional video on how to make a diabetic friendly millet breakfast cereal. You will need almonds, cinnamon, shredded coconut, and hemp seed. You can make your own milk out of the almonds, coconut, or hemp or you can purchase almond milk. Place one cup of millet of two cups of water in a pot and heat it up on the stove. It will take about 15 minutes for the millet to cook. To make the almond milk, soak the almonds for 24 hours prior. P...

Starting with Android 9 and 10, Google made privacy and security the main priorities for Android updates. Both versions brought numerous changes to help erase the notion that Android isn't safe, but Android 11 might even have them beat.

There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.

Unless you're completely new to Instagram, it's likely that you've linked your account with a third-party service at some point and forgotten about it. Those services still have access to data such as your media and profile information, so it's important that you not only know how to find these "authorized" apps, but that you know how to revoke their permissions.

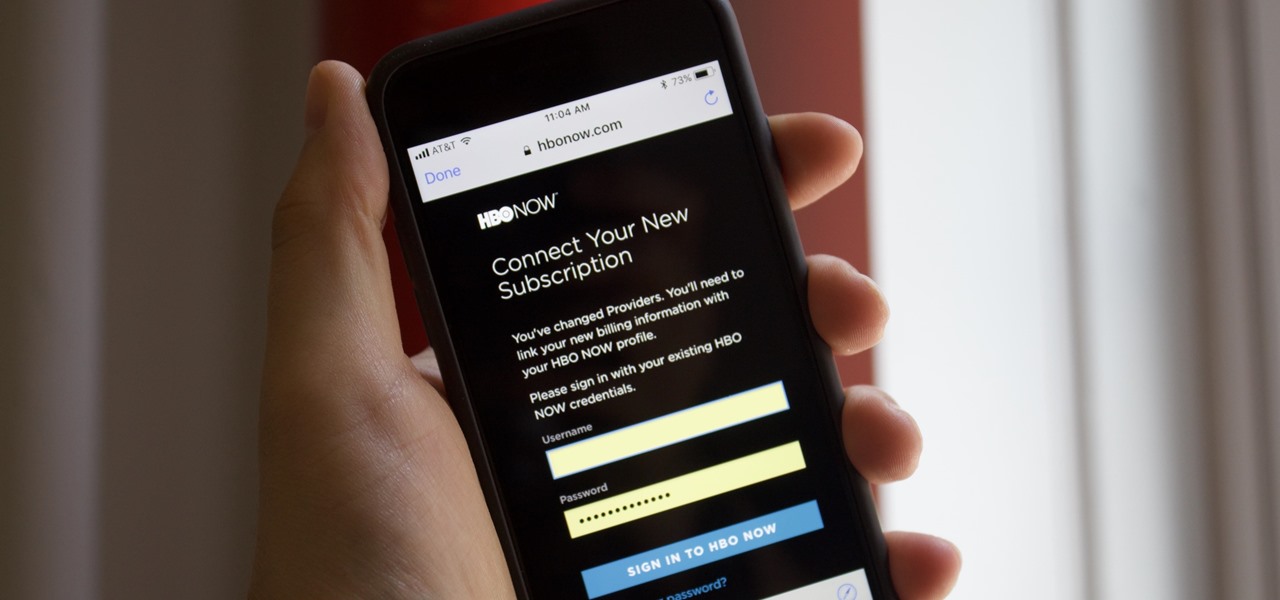
Media subscriptions are all the rage these days. Between Netflix, Apple Music, HBO Now, and countless more, your TV, movie, and music options have never been better. Unfortunately, all these choices weigh heavily on your wallet. So, when there's an opportunity to snag not just Spotify but Hulu and Showtime as well, all for just a tad bit over five dollars a month, how could you turn that down?

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

GitHub is an extremely popular site that allows developers to store source code and interact with other users about their projects. Anyone can download public, open-source files on GitHub manually or with Git, and anyone can fork off someone's project to expand or improve it into its own project. It's a really great site for programmers, developers, and even inspiring hackers.

Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

An annotated bibliography is very important when writing a scholastic paper or essay. In this tutorial, learn how to create an annotated bibliography, step by step.

Love basketball? Then you probably love Kobe Bryant… everybody loves Kobe. Watch this tutorial to learn how to draw Kobe Bryant. Make sure to pause the video after each step and look at the screen every few seconds while you are drawing.

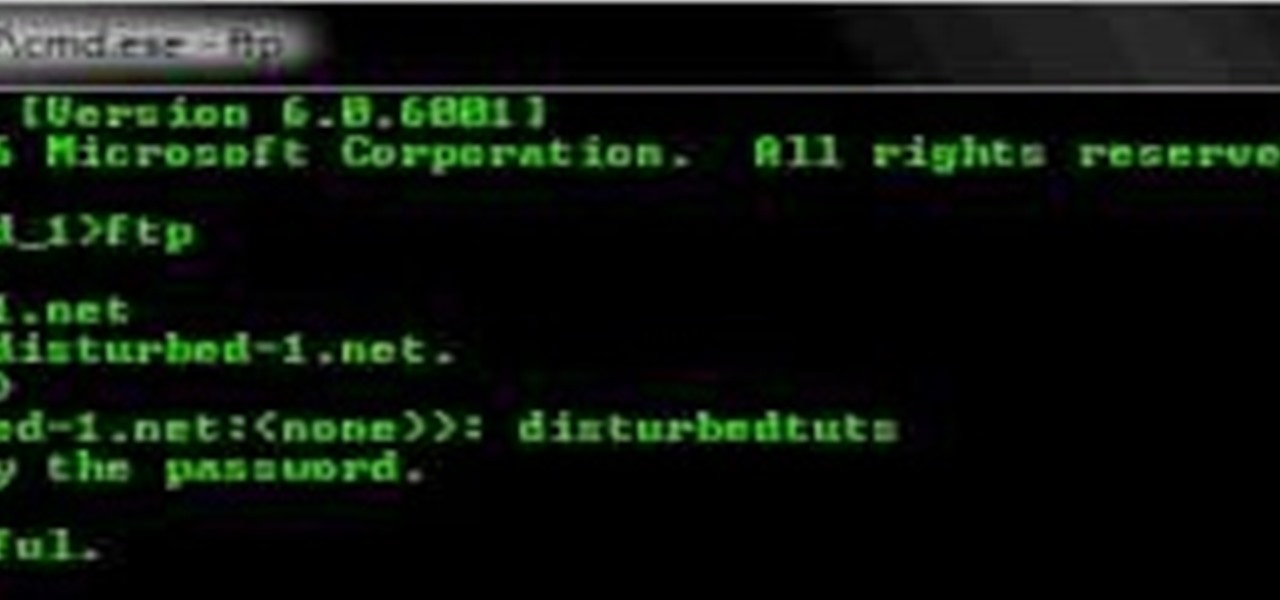
You can connect to an SSH server or connect to an FTP server from you windows computer. Open the run dialogue in your windows and type in cmd. Press OK to open the command prompt. Type in ftp command and press enter. This brings up the ftp prompt. Type o to connect to a server. Next type in the server name you want to connect to. Now you will need the authentication credentials to connect to the server. First enter the user name and then the password. Up on successful log in it shows the same...

Dropping out of high school doesn’t have to mean the end of your educational career. You can earn a General Education Development diploma, also known as a GED. In this video, learn about the process needed, step-by-step, to get your GED.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.

When you have a personal Instagram account but also manage other profiles — like ones for work, your entrepreneurial startup, an alter ego, or your famous pet, to name just a few examples — how do you manage them all from the same device?

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

Update: HBO discontinued this service. Your best bet for transferring your data from one account to another is to save a record of your watch list. That way, you can add your titles back manually with your new account.

Now that we've learned about keeping all our data safe with encryption, it's time to continue progressing through getting your Mac set up for hacking.