Some of the best images I've seen were shared via Snapchat, but once they're expired, they're gone forever, with no way to view them again unless I want to take a screenshot. But that will, of course, alert the sender.

Welcome back, my novice hackers! In this third installment of my Hacking Web Apps series, we will look at the authentication of web applications. Remember, there are many ways to hack web applications (as I pointed out in my first article), and cracking authentication is just one method.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

Some people are of extremely secretive nature. They do not like sharing their personal events in their lives with anyone. Thus people around that person wont be able to figure out details on their life's personal matters. It is not like they want to hide some mysterious secrets from the world, but it is just their nature that they do not want others to know much about them or are too shy to share their feelings with others. Being secretive is neither good nor bad, it is just how they are.

Smartphone users often wish for a privacy, where no one is able to poke his/her nose in their personal stuff. Unfortunately, none of the smartphones have been able to guard their privacy in this fashion. Smartphones usually come up with none or almost negligible built-in security to serve your purpose.

If you are anything like me, you have a knack for taking silly selfies of yourself, i.e., taking scotch tape and wrapping it around your face to make yourself look like the blob, or perhaps you like taking selfies of yourself in weird or unusual situations doing weird and unusual things.

Android Lollipop still doesn't have a simple way to add a custom lock screen wallpaper, so when I came across Corgi For Feedly from developer Stan Dmitriev, I had to check it out. What sets Corgi apart from other lock screen replacements is that it connects directly to your Feedly account to display top stories from your favorite RSS feeds as your background.

When Google Play Music launched a few years ago, I ditched iTunes and began using the service as my one and only source for listening to my personal music library. While All Access is great, I still prefer the radio feature on Spotify, so I still use that to discover new music.

With all of the different websites we use in our day-to-day lives, keeping track of our numerous login credentials can start to become a hassle. This has created a market for password managers that aim to centralize these account credentials and generally streamline the process of logging into our favorite sites.

When Google released Android 4.2, a new feature was introduced for tablets that allowed for multiple accounts to be used on a single device. In order to create a unique experience for each user, apps and personal data were kept separate, and switching between users became as simple as tapping your profile photo from the lock screen.

Instagram is not only a great platform to easily share some of your favorite moments with friends and family, it's a useful service for peering outside of your physical location. While you share a picture of your dog in Los Angeles, you can almost instantly view and like a picture someone posted of their breakfast in Tokyo.

Welcome back, my hacker novitiates! Many of you have probably heard of a man-in-the-middle attack and wondered how difficult an attack like that would be. For those of you who've never heard of one, it's simply where we, the hacker, place ourselves between the victim and the server and send and receive all the communication between the two.

It can be extremely frustrating when you've forgotten the pattern you use to lock your smartphone, and even more so if someone has managed to prank you by changing it. Luckily, there's an easy fix if you know the username and password for the Gmail account you used to set up the lock.

The one man Sam Fisher trusts, Victor Coste, has some information for him. To find out the intelligence, Sam has agreed to meet in person. Find out what the important intel is in this walkthrough for the Washington Monument (Mission 5), and where that lead Sam next.

Take a trip into the past as Sam Fisher gets captured by terrorists in the Iraq War. Instead of playing as Sam, you'll be playing the part of Victor Coste — the only man Sam trusts. Find out how Coste saved Fisher's life in this walkthrough for the Diwaniya, Iraq (Mission 4). What happens that day in Diwaniyah? Find out.

Joanna Schlip is a professional make-up artist who focuses on how to deal with puffy eyes. Prevention is always better than cure and making sure that you get enough sleep, staying well hydrated, treating any existing allergies, avoiding known allergens are just a few ways you can avoid your eyelids from getting puffy. In today's fast paced day and age where we don't have time to call up a loved one, let alone get eight full hours of sleep a night, there is precious little one can do to avoid ...

In this six-part video tutorial, learn how to create an access database. The following six parts go over the following:

Prepare yourself for more info than you need for winning The Saboteur for the Xbox 360. See everything involving the second mission in the Prologue: Better Days. Sean will flashback to 3 months prior to the opening mission. After the cutscene introduces some new characters, hop into the truck with Jules. Follow the GPS through the country side while avoiding running into other cars on the road. You'll eventually reach the German border. Pull up to the gate and a Nazi will inspect your papers ...

In the latest software updates for iPhone and iPad, there's an even easier way to view all your saved Wi-Fi networks and credentials and share them with family, friends, and others who need access.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

Tuesday has long been considered the best day to save money on a plane ticket. Airlines typically announce new deals on Monday, so by Tuesday, all other airlines have matched their competitor's lowest fares. It's a tip that I learned at a young age from my father and was solidified by countless others who swore by it. Well, it turns out that we were all wrong.

YOUTUBE Logan Salter presents a video demonstrating a method to create "Crocodile Tear" Makeup. The entire video is demonstrated through visual action, with typed titles in green appearing on the screen prior to each new step, and electronica music played throughout. Logan begins by applying moisturizer, demonstrated visually in the video by applying moisturizer to his facial area and moves at an increasingly faster rate through steps visually demonstrating how to apply various powders and br...

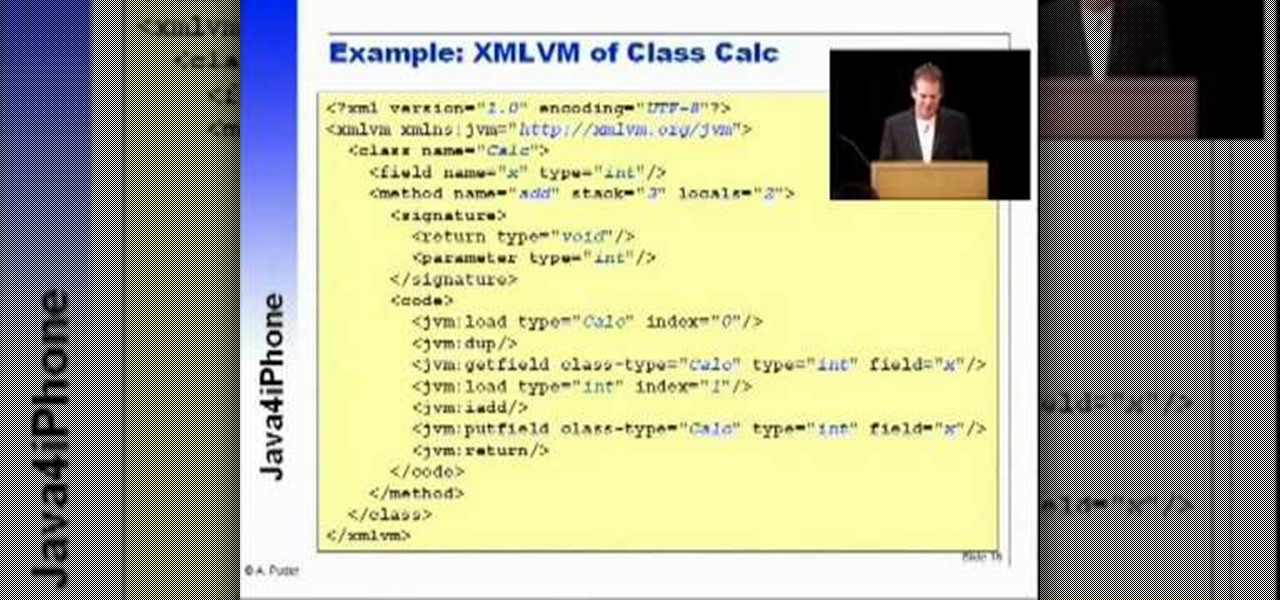
Arno Puder, a master of the XML coding field, gives a great rundown of Apple's new proprietary Java coding. This is especially helpful for Cocoa implementation

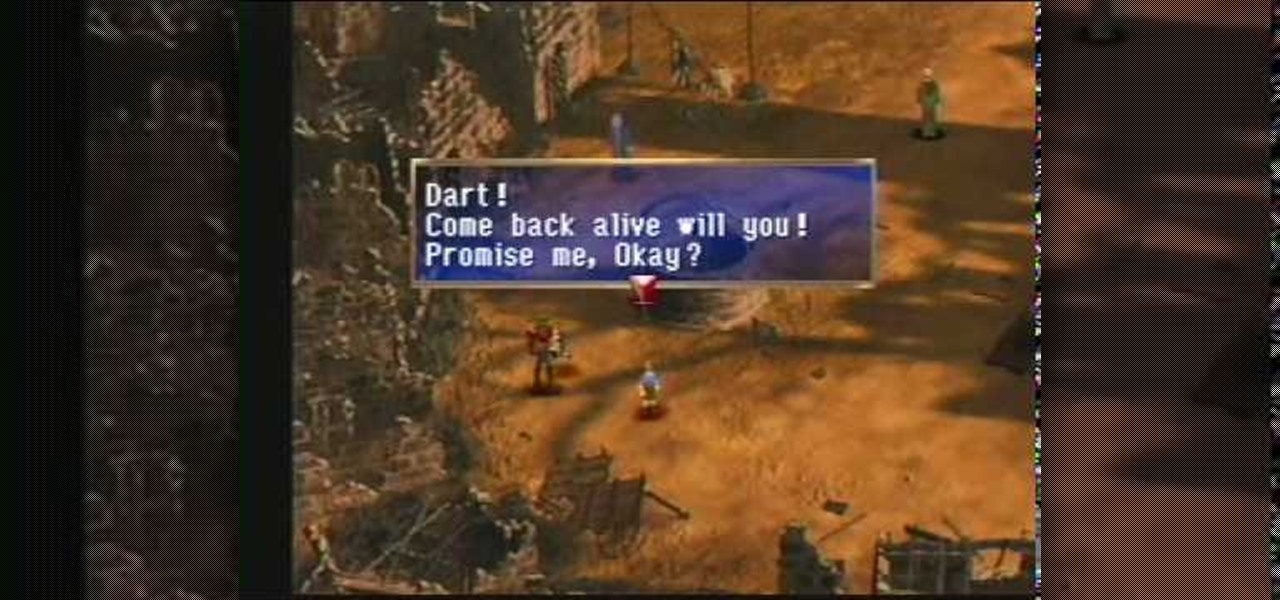
Dart and his friends are almost done. They just need to defeat Faust and return to the Law City Zenebatos in this part of The Legend of Dragoon for PlayStation. This video walkthrough takes you from where Dart and company fight and defeat Magician Faust in Flanvel Tower, they leave Flanvel and Kashua Glacier and back to the Law City Zenebatos to where they are exploring the city and rewriting laws so they can move about easier.

Start your battle with the Magician Faust in this section of The Legend of Dragoon for PlayStation. This video walkthrough takes you from where Dart and company fight and defeat Belzac and Kanzas, they head to Deningrad to buy/sell some stuff, through the Kashua Glacier to the Flanvel Tower, and they explore the Tower to where they are fighting Magician Faust.

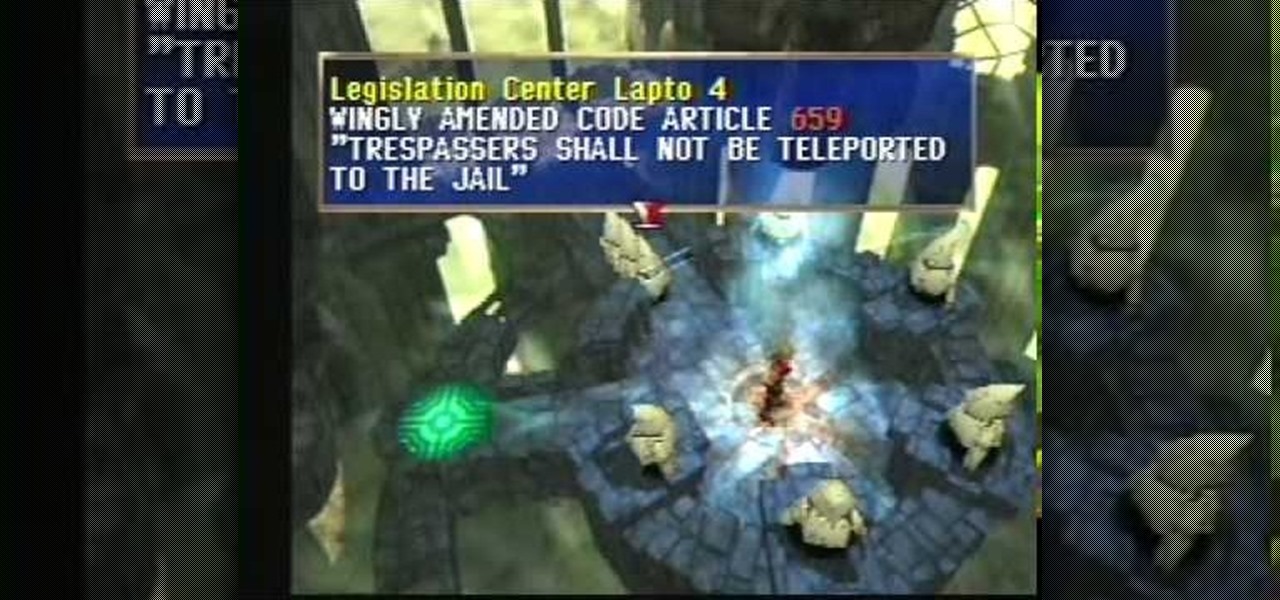
You'll find yourself in Kadessa and Deningrad in this installment of The Legend of Dragoon for PlayStation. This video walkthrough takes you from where Dart and company are exploring Kadessa, they fight and defeat the Grand Jewel for possession over the Dragon Block Staff, the party leaves Kadessa just as the Divine Dragon is launching an attack upon Deningrad, the Winglies try to teleport the party to Deningrad but they are too late to stop the attack, the party rush to the castle and make s...

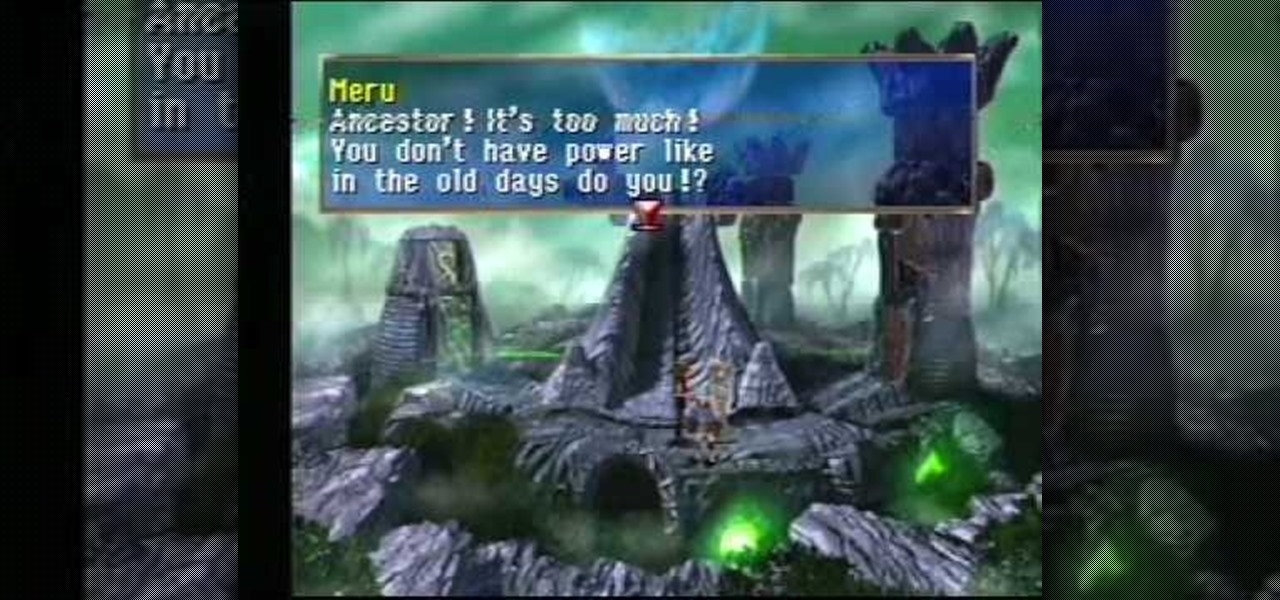
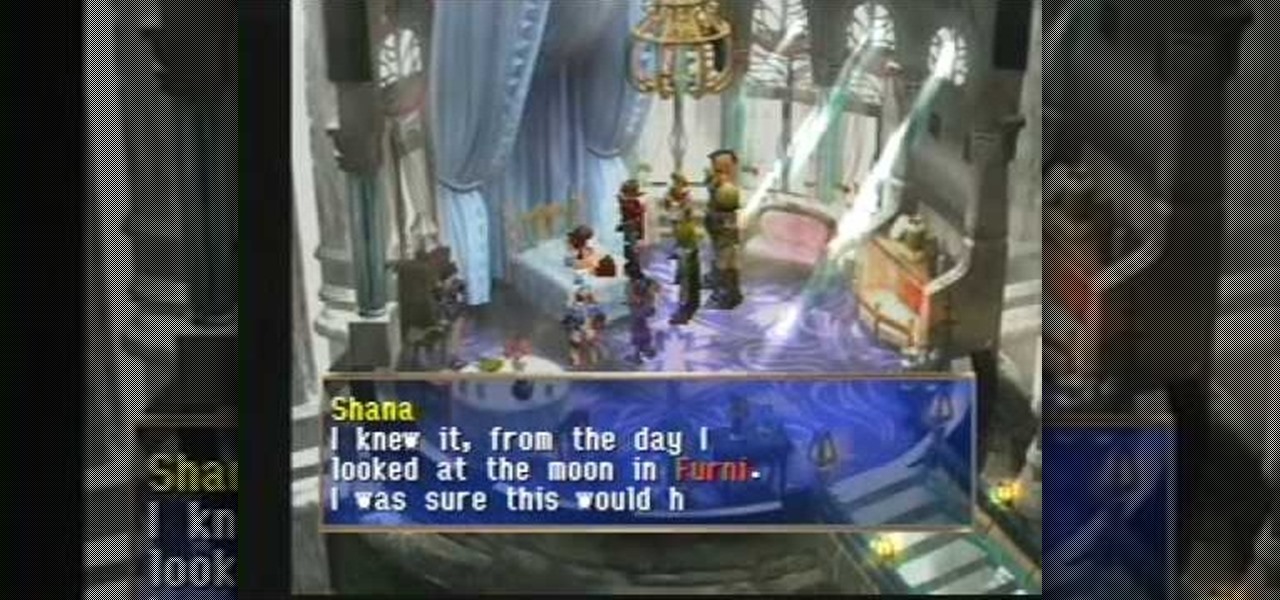
There's a lot going on here. In this level of The Legend of Dragoon for PlayStation, you'll see Queen Theresa, Sister Miranda, Shana, Winglies, and Neet. This video walkthrough takes you from where Dart and company make a visit to the Crystal Palace, Queen Theresa gets the party to agree to stop the Divine Dragon, Shana's Dragoon Spirit leaves her for First Sacred Sister Miranda, Shana collapses and is forced to stay behind, the party leaves and goes through the Evergreen Forest, they make a ...

In Hellena Prison, save the King from his execution… save the day in this level of The Legend of Dragoon for PlayStation. This video walkthrough takes you from where Dart and company are racing to the top of Hellena Prison to save King Albert from execution, they fight and defeat Fruegel, Lloyd steals the Moon Gem from Albert, Lavitz turns Dragoon in an attempt to help King Albert and gets slain, King Albert joins the party, they all go talk in Seles to where they travel to and explore the Bl...

Cooling sprays are a safe, easy, and effective way to relieve the discomfort of hot flashes associated with menopause. Watch this video to learn how to make a hot flash cooling spray.

Prepare this easy vegan meal that serves six. The quinoa and black beans takes 15 minutes to prep and 35 minutes to cook.

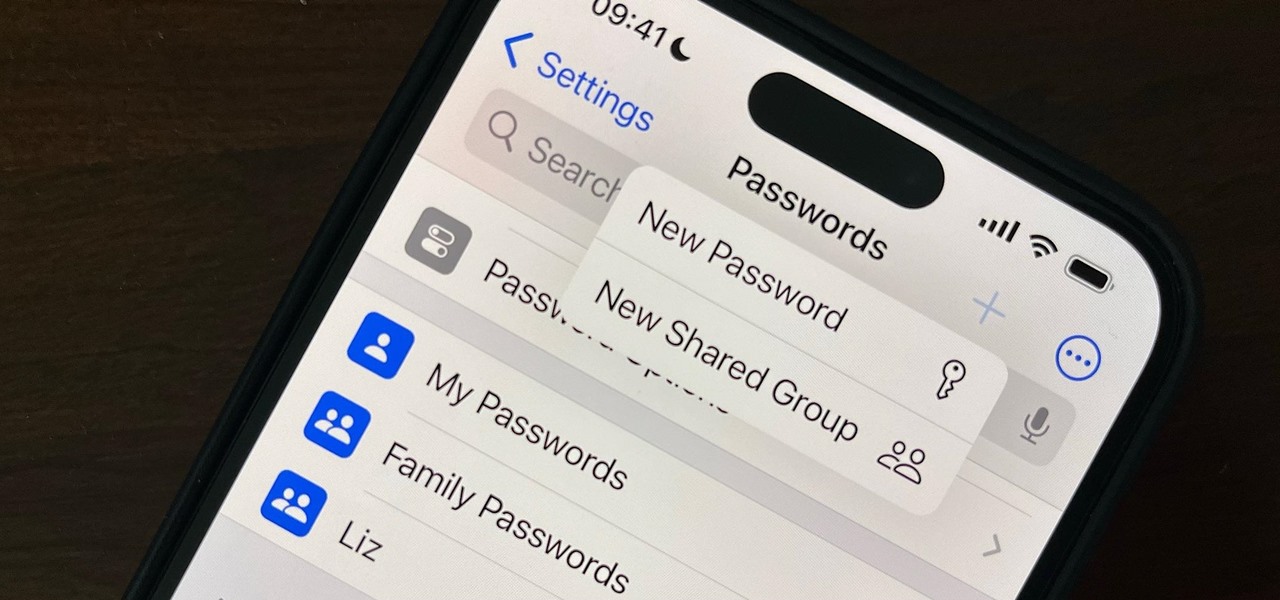
Previously, you'd have to use a third-party password manager on your iPhone, iPad, or Mac to securely share passwords with other people or groups outside of AirDrop range. And while apps like 1Password, Bitwarden, and Dashlane let you store passkeys, only 1Password has added support for passkey sharing so far. Now, Apple itself makes sharing passwords and passkeys much, much simpler.

More and more tech-savvy leaders are flocking to the lucrative and exciting world of project management thanks to the high-pay, analytical environment, and nearly unparalleled flexibility. But this means that competition for the best positions in this dynamic field is fierce. If you want to stand out from the crowd, you're going to need to have more than a few base-level certifications on your résumé.

There are countless ways in which a talented and trained programmer and tech pro can earn a lucrative living in an increasingly data-driven age — from writing and creating apps and games to working for a cybersecurity firm or even the federal government.

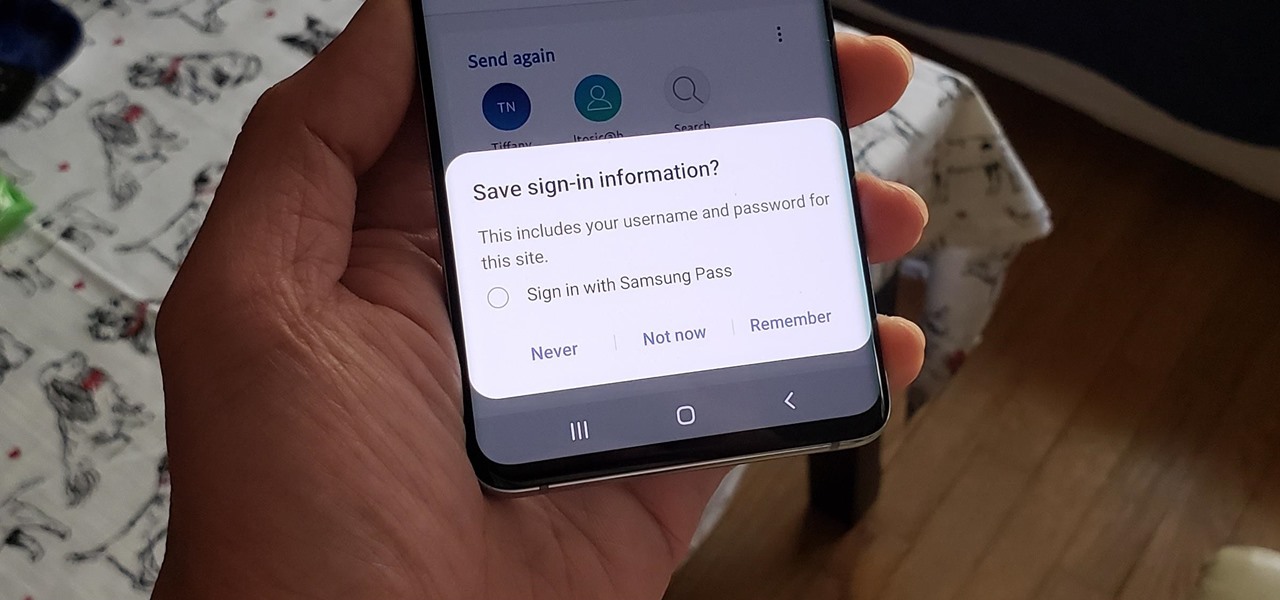
If you use Google Chrome on your computer, you've undoubtedly saved a ton of passwords since the browser always prompts you to. But Samsung uses their own password service on their phones by default, so you'll have to change a setting if you want to use your Chrome passwords to log into apps and sites on your Galaxy.

Your friends are ditching Snapchat for Instagram. After the social network turned camera company announced it lost $13.30 per user in its first quarter as a publicly traded company, well, it doesn't look too good for the platform's future, y'all.

Welcome hackers. Hackacademic.RTB1 is vulnerable machine for training our skills.This machine can be download from free from here. There is many tutorial how to hack these machine but i did always be my self.

Hello Everyone! I wanted to share a free and open source note taking tool that I've been using for quite some time now.

Apple announced the release of their newest Mac OS X version at this year's Worldwide Developer's Conference, and it's called "El Capitan." Like the majestic rock formation it's named after (located within Yosemite National Park), El Capitan promises to emphasize and expand on some of the great features we used on 10.10 Yosemite.

In an attempt to remain a mobile-exclusive app, Instagram doesn't let users upload photos or videos from their computer. On the Instagram web app, you can pretty much only like and comment on items in your feed, but what about all of those photos on your computer that scream #tbt?

Whether it's for handling your business's social media account or just for personal reasons, like trolling an ex-girlfriend's page (not that I've ever done that) or posting on behalf of your pup, there are instances where having two different Facebook accounts on one device is simply easier than switching back and forth.