In the event of an emergency where you can't answer for yourself, trained professionals can view your Medical ID on your iPhone to learn about your medical situation, granted that you have created one. But that's not all your Medical ID can do. With a new feature, iOS can share your Medical ID data automatically with first responders when you place an emergency call.

A long-standing request for the iPhone has been a way to quickly browse and connect to available Wi-Fi networks and Bluetooth devices without having to dig through the Settings app. With iOS 13, Apple has finally built this essential feature into Control Center, giving you quick access to wireless settings from anywhere, including the lock screen.

Seven days ago, Apple released the first public beta for iOS 12.2. Now, public testers have access to the latest beta update since Apple released 12.2 public beta 2 on Tuesday, Feb. 5. The company released the developer beta one day earlier, which includes bug fixes, new Animoji, and more.
On Monday, Feb. 4, Apple released the second developer beta for iOS 12.2. The update features bug fixes to users running iOS 12.2 beta 1, as well as four new Animoji for Face ID devices. Developers are strongly encouraged to update their iPhones. It's unclear at this time whether the update includes a fix for the Group FaceTime bug discovered last week.

Public beta testers are no longer stuck on iOS 12.1.3. Apple just released the first public beta for iOS 12.2 today, Jan. 28. The company released the first developer beta for the software Thursday, Jan. 24, which includes new features for HealthKit and News, as well as a slew of hints for upcoming developments.

One day after the official release of iOS 12.1.3, Apple released the first beta for iOS 12.2 to developers. The software appears to be the first in some time to be a major update. Apple's last beta cycles included 12.1.2 and 12.1.3, incremental updates to iOS 12.1. Now, we've entered a new version of iOS 12 entirely, hopeful for new features.

Shopping wasn't always this easy. Now, in a matter of minutes, you can order your groceries for the week, send your cracked phone in for repairs, get your holiday shopping done, and have everything delivered to your front door in just a few days — without ever having to leave your home. Online shopping is convenient, comfortable, and a blessing ... right? Well, it can also be a headache.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

Project Fi, Google's MVNO, is running a new promotion on the latest and greatest from LG. From July 16 until the 29th, whenever you order and activate the LG G7 ThinQ or LG V35 ThinQ, you will receive a $300 service credit. When you do the numbers, that equals a minimum of three free months of service.

Marvel has solidified itself as the dominant superhero franchise with the release of Avengers: Infinity War, and it's now dipping its toes into the world of mobile card-based strategy games with the soft launch of Marvel Battle Lines in select countries ahead of a worldwide release. If you'd like to install this game right now and get a head start on your fellow gamers stateside, there's a workaround.

With April coming to a close, there's a fresh group of augmented reality Snapchat lenses you should try out while they're still hot. We've got a prank lens, gamer-oriented ones for Fortnite and Fallout, and ones for the memesters out there.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

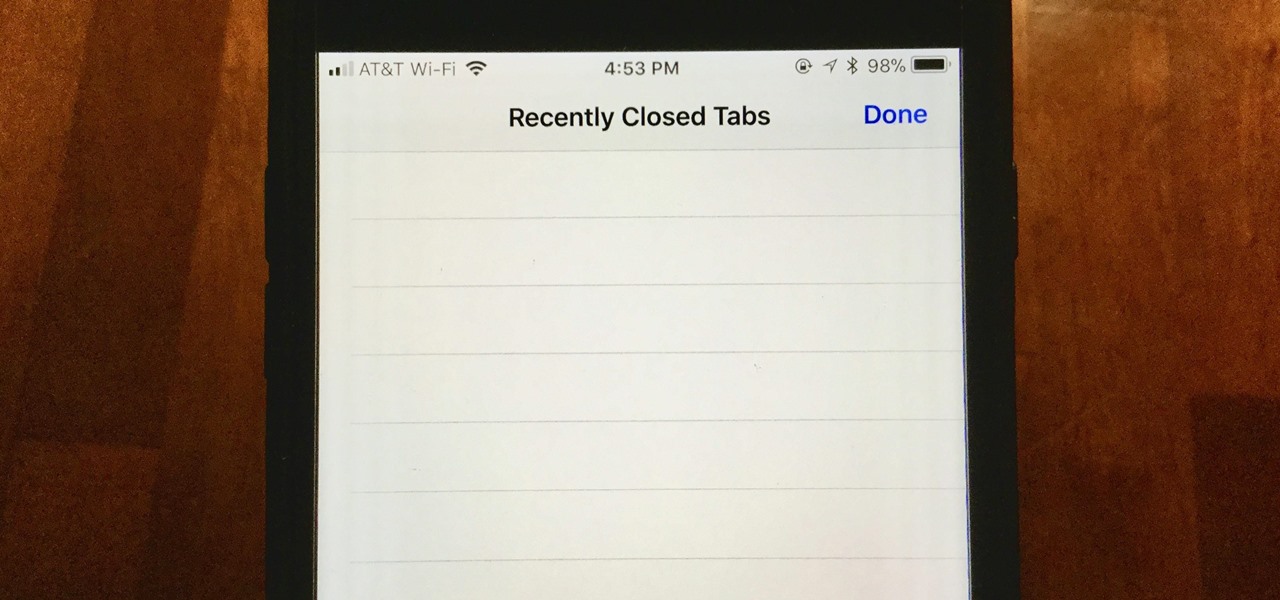
When you accidentally close out of an important tab on your iPhone, Safari's "Recently Closed Tabs" list really comes in handy. However, when it comes time to clear the list, things get a bit complicated. There's no "Delete" or "Erase" button on this page, but don't let that fool you — there are three easy ways to clear your recently closed tabs list.

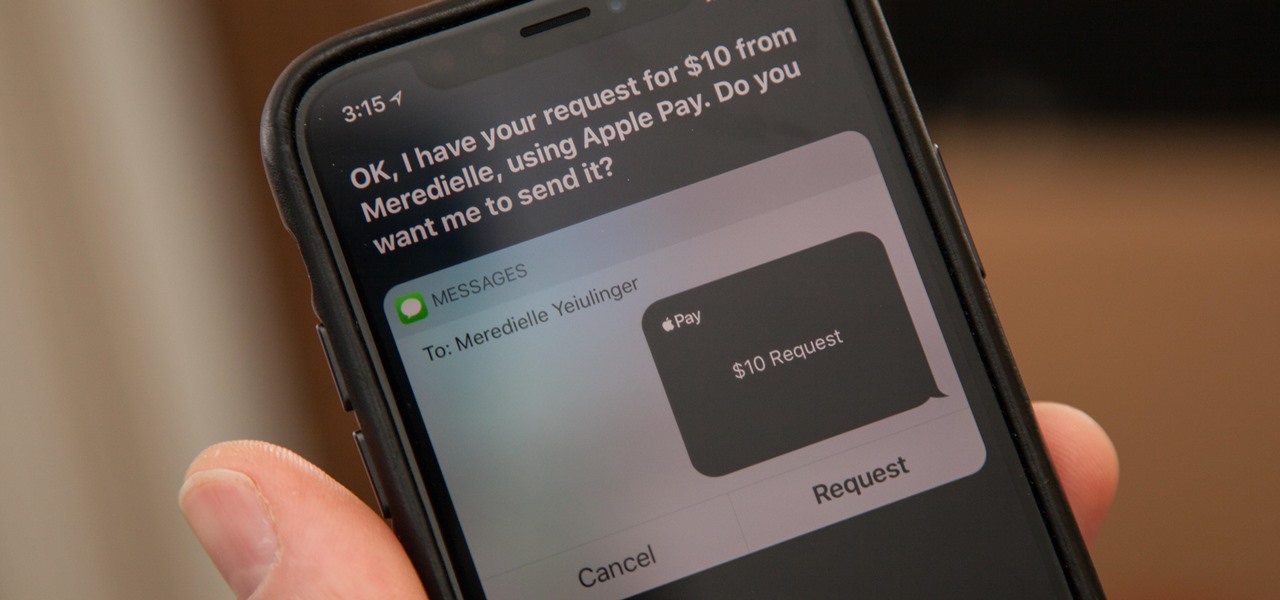
You might be proficient at sending your family and friends money using Apple Pay Cash on your iPhone, but what about when you need some digital currency in your wallet to buy in-app purchases or to get back the money you spent on someone's lunch? Requesting some Apple Pay Cash can be done a few different ways, none of which are hard.

Surveillance is always a useful tool in a hacker's arsenal, whether deployed offensively or defensively. Watching targets yourself isn't always practical, and traditional surveillance camera systems can be costly, lacking in capabilities, or both. Today, we will use motionEyeOS running on a Raspberry Pi Zero to create a small, concealable Wi-Fi connected spy camera that is both affordable and easily concealed.

Aircraft equipped with ADS-B are constantly shouting their location into the radio void, along with other useful unauthenticated and unencrypted data. In this guide, we will make an ADS-B receiver using a Raspberry Pi with a software-defined radio (SDR) dongle, which we can use to track aircraft anywhere in real time.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

Buying a smartphone used is an excellent way to save money, but those savings come with a risk that your seller isn't as forthcoming as they claim. You don't want to end up buying a stolen smartphone because it might not work correctly ... and, you know, it's wrong. Luckily, there's an easy way to check if the phone you're about to buy is legit.

Samsung's new personal assistant, Bixby, is making its debut on the Galaxy S8 and S8+. In addition to taking voice commands and performing visual searches, a new Hello Bixby feature predicts what you might want to do next with an integrated home screen feed. All of these features look nice, but if you're not ready to shell out at least $750 for a new phone, you'll be glad to know that Hello Bixby just leaked.

Like previous installments in the Pokémon series, as you progress through Pokémon GO you'll be able to evolve your Pokémon into more-powerful monsters with new and more-damaging attacks. However, unlike older entries in the series, your Pokémon won't simply evolve when they reach a certain level. Instead, you'll have to "feed" them a certain amount of character-specific candy to induce the transformation.

Android's flexible operating system allows for lots of customization, and one of the most common ways to add personal flair to your smartphone is to set your own ringtones and notification sounds.

Most of you probably heard about Rasberry Pi and if you haven't; what is wrong with you? But nothing less a Rasberry Pi is a computer a very small computer. Despite these size limitations, the Rasberry Pi is to not be underestimated. Not only can it do anything like a normal laptop or desktop, but, in my opinion on of the coolest features is that it boots off a Micro SD card. It can do anything that you want, but it's built to be played with. A hacker heaven.

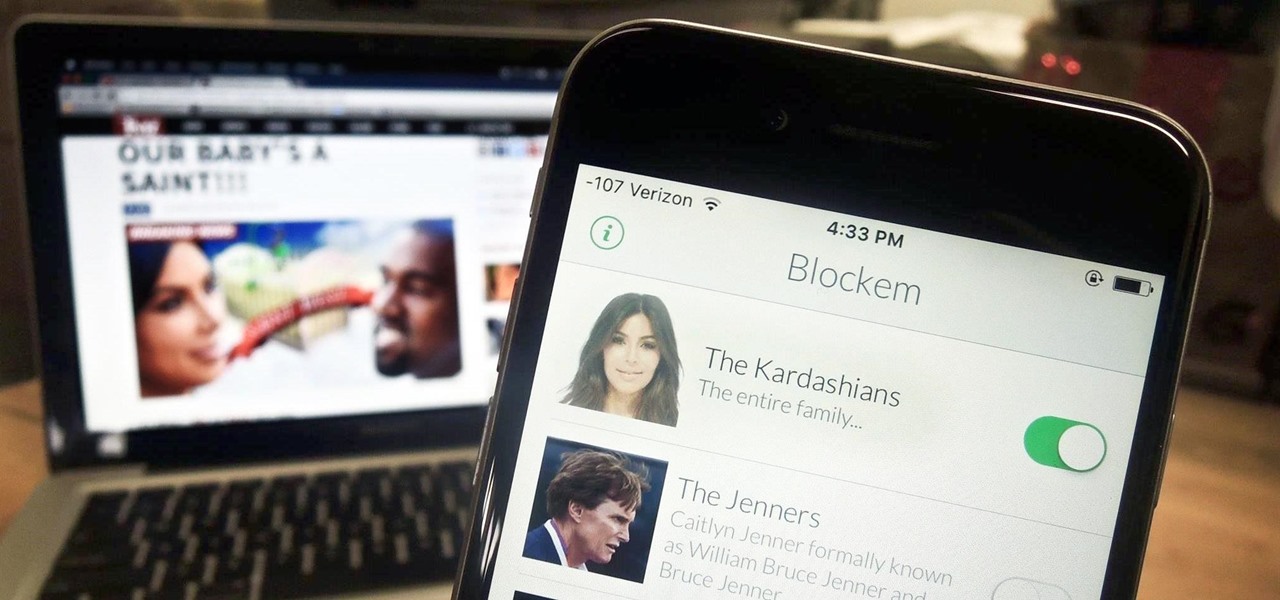
Kim Kardashian and Kanye West have fittingly named their second child "Saint," but I'm sure you don't care about that—and neither do I. Unfortunately, regardless of our pop culture interests, we're forced to know these types of stupid facts because the internet is so densely populated with Kardashian-related content that it's impossible to avoid. It's enough to make you puke.

Computer system authentication is critical to keeping systems safe from unwanted users, intruders, and abusers. Basically, authentication is the process of the potential user proving they are an authorized user.

Keeping data private is vital in the days of smartphones and the free-floating information they carry. Justin wrote a guide on many of the deeply hidden and sometimes concerning privacy settings in iOS 7. Now we're back to cover some of the new (and old) privacy settings in iOS 8 that you need to address right now.

If you have a custom recovery installed on your Nexus 5, you're able to flash custom ROMs and lots of other cool Gadget Hacks. But when it comes time to receive and Over-the-Air (OTA) update directly from Google, having a custom recovery installed can be a fairly big hindrance—and for the upcoming Android L release, you're going to want to alleviate that.

Google Play Music is one of the best cloud music services out there. Without ever paying a dime, you can upload as many as 20,000 songs to Google's servers, then use the app on your smartphone to stream these songs without taking up any of your storage space. And if you're willing to shell out $9.99 a month, you can even play songs from the massive All Access library.

Valentine's Day is a day for love, but it also just happens to be the time when every flower shop in town hikes up their prices. Chocolates are still relatively cheap, but I never understood why you have to give the gift of bigger love handles when something more creative gets the job done at a much cheaper price.

This year, like every year before it, Black Friday sales are starting earlier than ever. A lot of stores will be opening their doors as early as 5pm on Thanksgiving to get a head start on the madness (and it really is madness). As we've discussed in the past, one of the keys to emerging victorious on Black Friday is to plan, plan, plan. So, we've compiled some of the best deals in tech, gadgets and appliances to help you prepare for battle.

Why unlock your Samsung Galaxy S3 to use with a different SIM card? One possible reason is that you love your phone, but not your cellular provider because of the poor service or an unreliable connection. If you purchased a Samsung GS3 with AT&T, T-Mobile, etc. on a contract, it might be locked for a specific amount of time called the contract period.

We've gotten pretty close to a Google Experience before, and even played around with the actual Google Play Edition build. However, the devs over at XDA have a much better solution: actually converting your HTC One into a complete factory-fresh Google Play Edition.

If you have a load of dusty Game Boy Advance games you've been itching to play, load them onto your Samsung Galaxy Note 2 for instant gaming anywhere—anytime!

Learn how to use an online photo website to make creative, homemade and personalized Christmas cards in this Christmas video series.

This video demonstration shows the steps for making a greeting card decorated with a paper skirt. This sweet card can be sent to a friend for a gift or any occasion. Watch this instructional video and learn how to design a thoughtful greeting card and decorate it with a skirt.

Watch this video to learn how to use acetate or transparencies for backgrounds or cards. Part 1 of 2 - How to Make a transparent card.

In this video series, watch as computer expert Gary Zier teaches how to design a graphical business card in Photoshop. Learn how to apply effects and text, how to create masks, and how to resize images in Photoshop. Get tips on how to save a business card as a signature in your email.

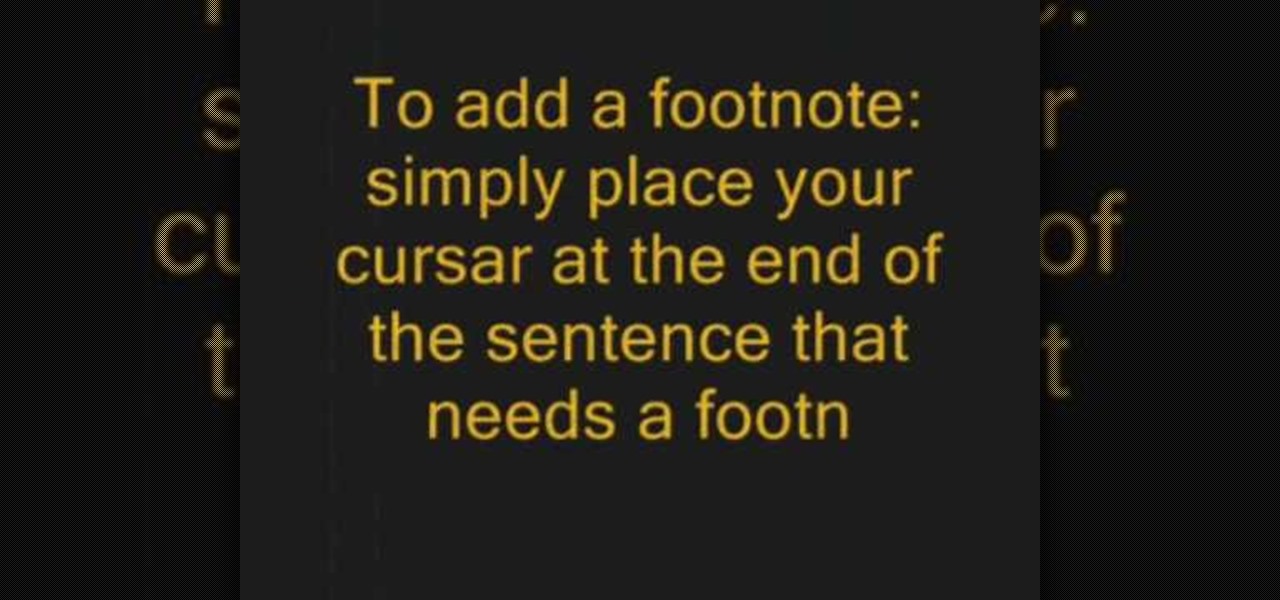
In this tutorial, we learn how to add a footnote to a research paper. To do this, you will need to have all the sources written down where you got the information for the topics that you're writing about. Make sure you give credit to all the places that you go the information, or else you stole it and it's plagiarized. You will need to write down the author's name, title of the source, publication company, city of publication, copy date, and page number. To add the footnote, you will simply w...

In this tutorial, we learn how to score a big buck or elk with Stan Potts. First, take the bottom of it and remove a bottom line from the main beam. Measure the length of all of the sides. If you're going to cut it out, you should be perfectly even with the top. Then, you will do this on the other side for a typical frame. From here, take the greatest inside spread at a perpendicular angle and that will be your spread credit. Add up each side individually and then you will find the difference...

This is it… the last level in Lara Croft and the Guardian of Light. It's called "Xolotl's Stronghold", and it's the last thing you'll see before the credits (hopefully). This Lara Croft / Tomb Raider game is available only from the PlayStation Network or Xbox Live Arcade. If you can't quite make it past the final mission, watch this walkthrough to see how to defeat Xolotl and win the game. For previous levels, check out the other walkthroughs for Lara Croft and the Guardian of Light.

In this video tutorial, viewers learn how to cite sources. The citation style depends on the college major, professor or enrolled class. Citation gives credit to the author, validates claims that you have made, help readers learn about the subject and avoids plagiarism. To cite an article, users will need: the author, publication title, article title, date, volume/issue, page numbers and web address. To cite a book, users will need: the author, title, editor(s), chapter title, date of publica...