Many operators use elevators to control access to particular floors, whether it be the penthouse at a hotel or a server room in an office building. However, the law requires them all to have a fire service mode, which gives emergency access to restricted floors, and a hacker can use that to bypass security altogether.

Apple first included a dual-lens camera onto its iPhone 7 Plus back in late-2016, yet not many developers besides Apple have harnessed the depth data that "Portrait" mode photos provide. A relatively new app is changing that, though, by using that depth information to let you add realistic-looking light sources to your photos.

Google Lens is a fantastic addition to Google Photos for Android and iOS that allows your smartphone to identify a number of things in your pictures, like landmarks and contact info. Using this power, you can even find out how to buy almost any product you've taken a photo of — you don't even need the barcode.

Chrome is the browser of choice for millions of iPhone and Android users, largely thanks to its user-friendly interface and native Google support. But with concerns over sharing private information with massive companies growing, many people are starting to want a little less Google integration in Chrome.

Google collects an enormous amount of personal data. While some of this data is used for targeted ads, others tidbits of info such as our location are used to improve our mobile experience. While it is natural for us to distrust Google's intentions, by allowing their data collection, we can add new functionality to our favorite apps.

Since making waves at Mobile World Congress 2018, Android Go devices have slowly trickled their way onto US shores. Only one device was officially announced for the US at MWC, but several OEMs have extended availability to the US in the months since, and it looks like we just received another.

The first question people ask me when they come to my apartment is usually "What's your Wi-Fi password?" While I'm happy to give my friends free access to the internet, it's hard to walk each person through my secure password. Luckily, there's a way to create a QR code that will let people easily connect to a Wi-Fi network.

MoviePass may be popular with filmgoers on a budget, but it might not be with those of you who are concerned about your privacy, since MoviePass may be logging your location data even when you don't expect the app to do so.

UPDATE: The P20 and its variants are officially available now. However, there's no official North American variant. You can purchase the international version of the P20 Pro or P20 Lite on Amazon, but be aware that it may not work perfectly on US carriers.

For the unaware, RED is a company that specializes in high-end cameras and other recording devices. RED's cameras are used to shoot some of Hollywood's biggest films and TV shows. Their modular designs make them ideal for the user who does a lot of mixing and matching — and has a wallet to back their work up (their WEAPON 8K VV starts at $79,500).

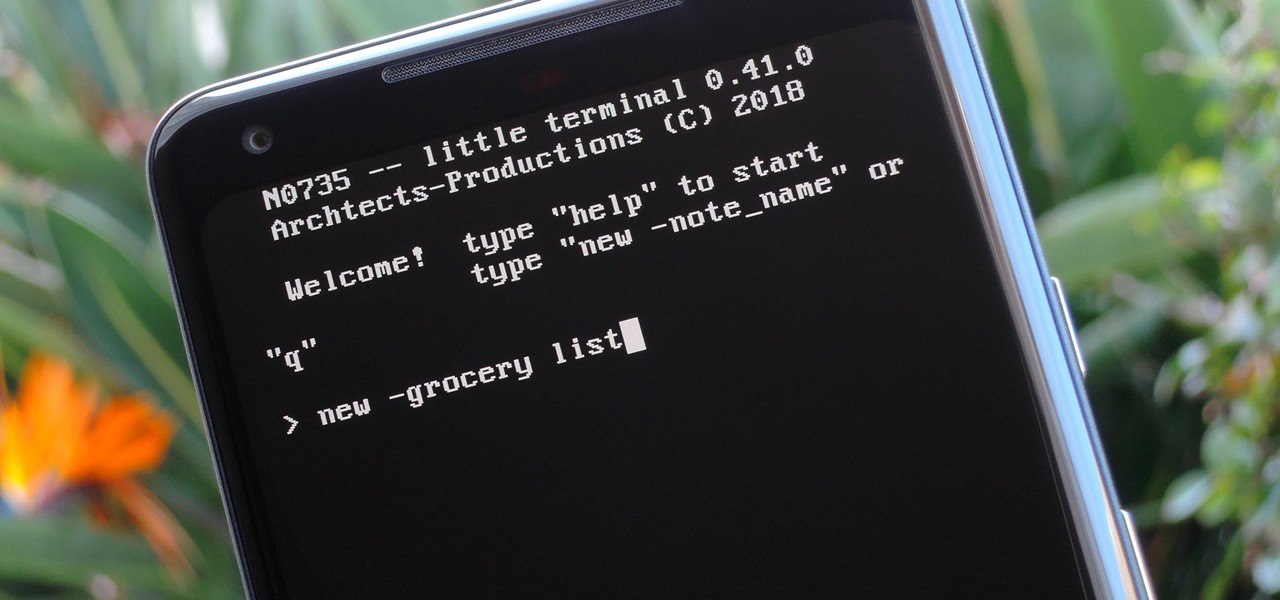
Deep down inside, Android is really just a fork of Linux, the popular open source desktop OS. You can see traces of its roots everywhere, and this lineage still holds a certain appeal with many Android fans. If you're in that boat, you'll love the newest notes app we just found.

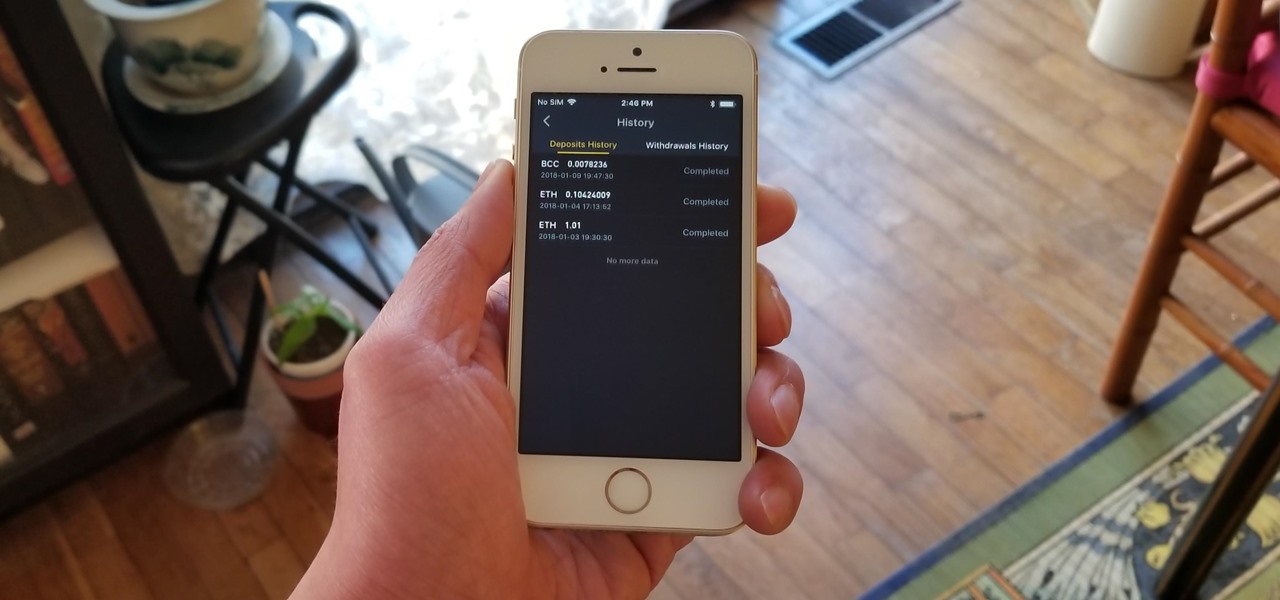
As cryptocurrencies gain mainstream acceptance, it's not far-fetched to think that we'll one day be able to buy alt coins like Ripple (XRP) and Stellar (XLM) using debit cards and bank accounts. Until then, we'll have to rely on using bitcoins and ethereum to buy digital coins. Thankfully, depositing and withdrawing cryptocurrencies with Binance is relatively hassle-free.

Market boxes are an integral part of the player experience in Animal Crossing: Pocket Camp, but using them effectively can be a tricky task. The item-trading tool between human friends is the locale for both junk and diamond-in-the-rough deals, and it can greatly increase the number of bells you earn if you play your cards right.

Connecting to your headless Raspberry Pi on the go typically requires a network connection or carrying around bulky peripheral hardware like a screen and keyboard. With the help of an old-school connecting standard, though, you can log into your Pi from any computer using a simple cable. If you don't have a power source, you can also power your Linux distro over the cable at the same time.

Unscheduled pit stops go hand in hand with road trips, no matter how well-planned they are. In the past, making a stop due to low fuel or an emergency bathroom break may have snowballed into massive delays when you went off course on your own, but thanks to a feature in Apple Maps, you can do this in the most efficient manner possible.

The next frontier for AR hardware is the consumer headset, and tech companies of varying size and tenure are working hard to strike the right mix between comfort, cool factor, and cost. How these companies handle the hype and flow of information vary wildly.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

So after being teased last Christmas with an email promising that the Meta 2 was shipping, nearly a year later, we finally have one of the units that we ordered. Without a moment's hesitation, I tore the package open, set the device up, and started working with it.

When it comes to Hi-Fi music streaming services, Jay-Z's Tidal is one of your only choices. But as you can imagine, true High Fidelity audio requires faster download speeds than your average music service. So the question becomes, how do you listen to Hi-Fi tracks on Tidal when a speedy internet connection isn't available? Offline music is the answer.

Now that the the iPhone 8 and iPhone 8 Plus have been revealed, we've been eager to see how the new devices will stack up against top-of-the-line Android phones like the Galaxy S8 and S8+. We can't compare real-world usage right now since the new iPhone models haven't been released yet, but we can see how they stack up on paper to get an idea of which one is the better buy.

A PirateBox creates a network that allows users to communicate wirelessly, connecting smartphones and laptops even when surrounding infrastructure has been disabled on purpose or destroyed in a disaster. Using a Raspberry Pi, we will make a wireless offline server that hosts files and a chat room as an educational database, a discreet local chat room, or a dead-drop file server.

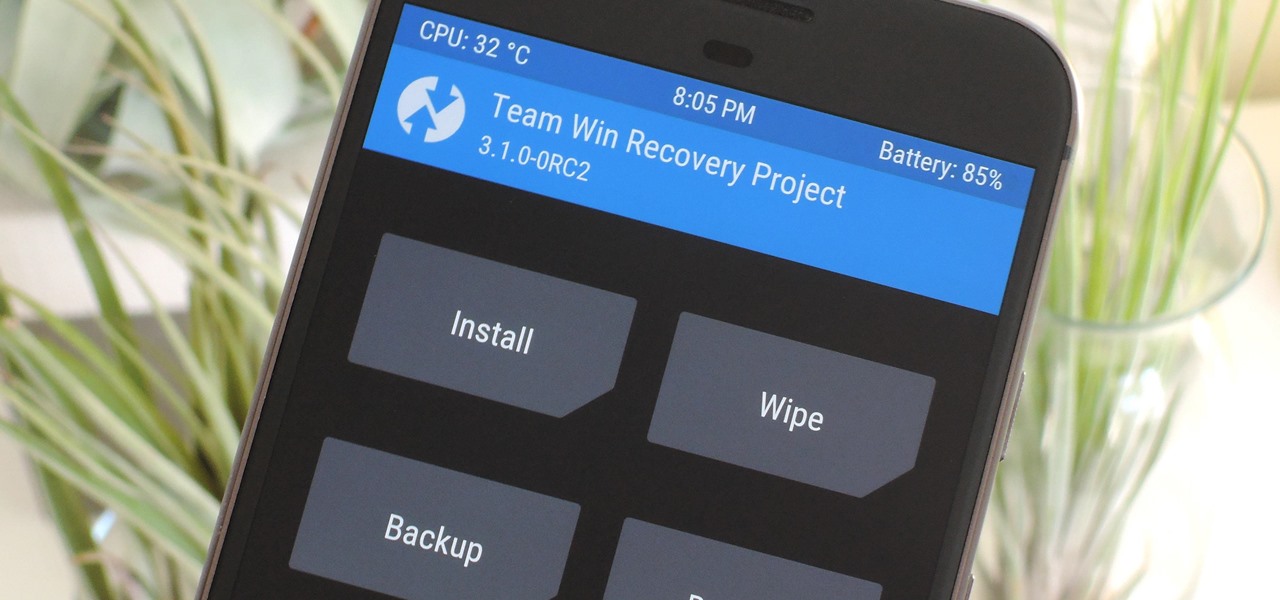
When it comes to modding Android, root gets all the glory, but a good custom recovery is really the only thing you need. Not only does it allow you to back up your entire phone, install flashable ZIPs, and load custom ROMs like LineageOS, but a custom recovery will even let you root your device. For years now, the only custom recovery worth mentioning has been Team Win's TWRP.

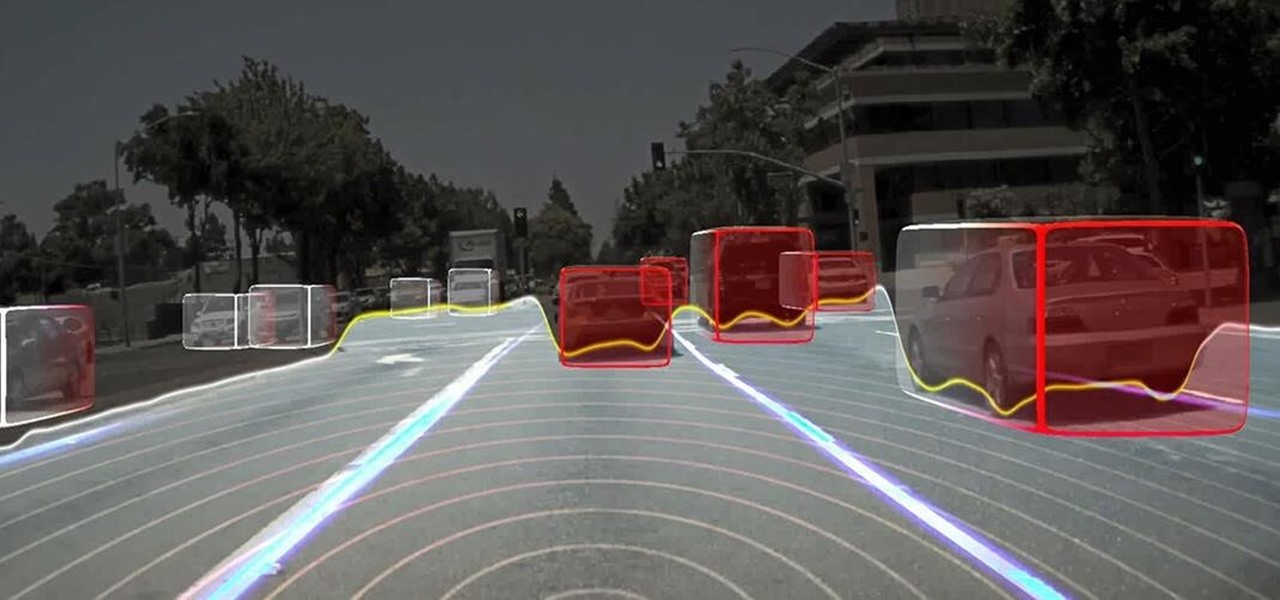
Long before Nvidia figured out how to embed neural networks in its graphics processor units (GPUs) for driverless vehicles, it and other chipmakers were already making the same kinds of devices for 3D games and other apps.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

Since its debut 9 years ago, the iOS App Store has always had roughly the same functionality: Featured apps, categories, top charts, a search function, and a place to update your apps. But starting with iOS 11, that's all changing — drastically.

At the moment, it would be safe to say that demand for devices running Tango, Google's augmented reality smartphone platform, is relatively low among consumers. Kaon Interactive, a B2B software company who has built more than 5,000 interactive applications for use at trade shows, remote sales demonstrations, and other customer engagements, is betting that there is a market for the devices in sales and marketing.

Typing on a mobile device has come a long way since the days of flip phones. Today, there are awesome keyboard apps like Gboard, which integrates Google search features and makes typing a breeze. But the whole experience still stands to improve if you take some time to learn a few useful tips.

New statements from Apple make it clear that they do not believe a hacker, or group of hackers, breached any of their systems. This comes after a recent report from Motherboard that a hacker gang called the "Turkish Crime Family" is threatening to remotely wipe up to 559 million iPhones by April 7.

The LG V30 has finally been announced and was rumored to be released sometime in September, but September has come and is almost gone, while LG fans have been waiting anxiously. The V series offers a more robust media experience when compared to LG's other flagship, the LG G6. Since the phone has been announced, we do have all of the details for the third flagship in LG's V series, and believe me, it's sounds like it'll be worth the wait.

We live in a computer world full of file formats. Whether we are talking about images, videos, or text documents, there are dozens of file types for each, and there are new ones added every year to applications. Keeping in mind that many of these formats were created before the internet was widely available (at least, in infant form), the primary reason for this glut of often complex choices is competition.

Last week it was announced that Waymo, the former Google Self-Driving Car project, had graduated from Alphabet's X innovation center. This graduation had been in the cards for many months with senior members of the project team and X hinting that it would be soon.

Google's new Project Fi cellular carrier has been making waves across the mobile industry, so we decided to put it to the test against T-Mobile, one of the more established networks. For the actual testing, we slapped a SIM card from each carrier into two identical Pixel XL phones, which offer full compatibility with both networks.

The new Google Assistant is only officially available on three platforms—newer Android phones (Pixels and those running Marshmallow and Nougat), the Google Allo app, and Google Home. However, most of the Assistant's basic functionality is also bundled into the Google app for Android and iOS, which used to go by the name Google Now, but is now referred to only as Screen Search or your Google app's Feed.

The hatred is almost universal—by now, even late night TV hosts are bashing Apple's move to ditch the headphone jack in the iPhone 7. It's not like the disdain is baseless, either, because there are plenty of problems that come along with removing the iPhone's only analog sound output.

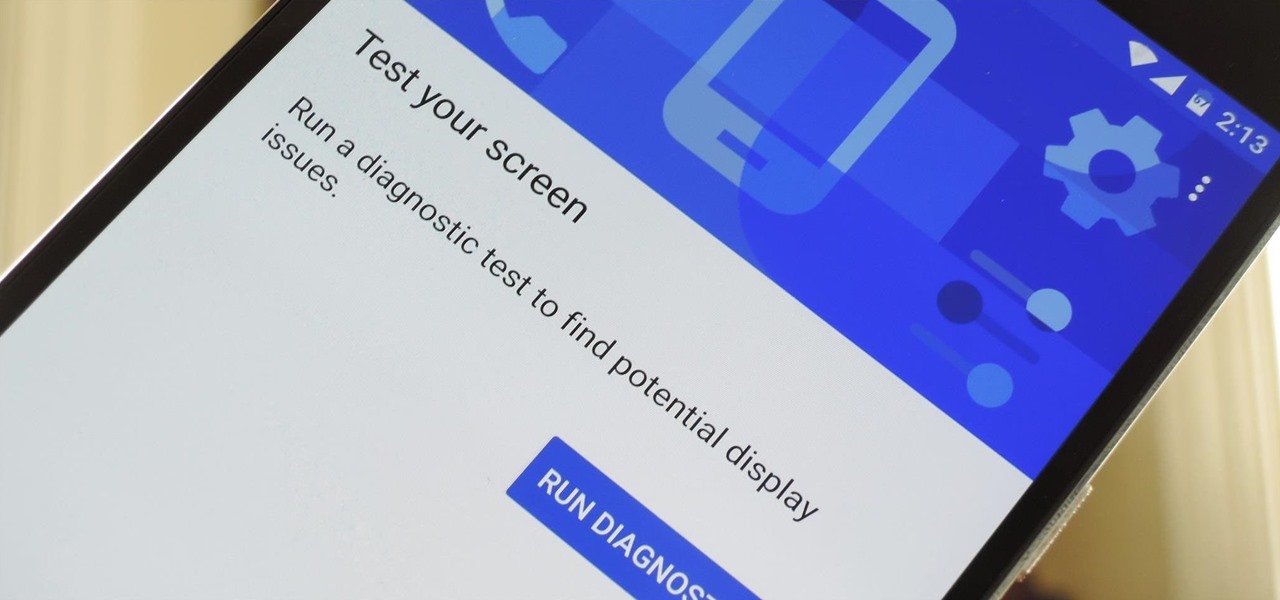
Google has a lesser-known Android app called Device Assist that might just be one of the most useful programs the company has ever published. It offers interactive guides and general tech support for Android, plus it can diagnose your device and help you fix any issues it finds.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

Fewer and fewer Android phones are being released with SD card slots, so it's always a struggle to make sure you have enough free storage space for your photos, videos, and music. Things like app data and cache slowly build up as you use your device, which means your available storage number gradually decreases over time.

If you're experiencing issues with an app or custom ROM and would like to report your problem to the developer, there's no better way to do it than by capturing a logcat. Android keeps track of all the commands that have been executed by various apps and services, which means that when something goes wrong, the error is clearly shown in this so-called logcat.

First of all, I would like to apologize for a week long absents for the tutorials of this newly series, Raspberry Pi. But obviously I'm back and I present all you guys a article on turning your Raspberry Pi into a hacking platform. I'm gonna use the platform Kali Linux for the Raspberry Pi. I should note that I'm not gonna go into detail on how to install Kali Linux since OTW already has done a tutorial on how to turn your Raspberry Pi into a Hacking Pi. The point of this particular tutorial ...