Smelly foods are what make my culinary world "go 'round," so to speak. I grew up with fish sauce, learned to cook with and love fermented beans and veggies, and am one of the biggest garlic advocates I know... other than my husband, who thankfully shares the same smelly food sensibilities. (Let's put it this way: anyone that can stomach stinky tofu can handle anything I could possibly cook up.)

In recent weeks, some people have been shunned from the Null Byte community because they expressed "black hat" aspirations. This is because Null Byte is the "white hat" hacker training/playground. Although most of us think we know what that means, it does beg the question; "Who and what is a white hat hacker?"
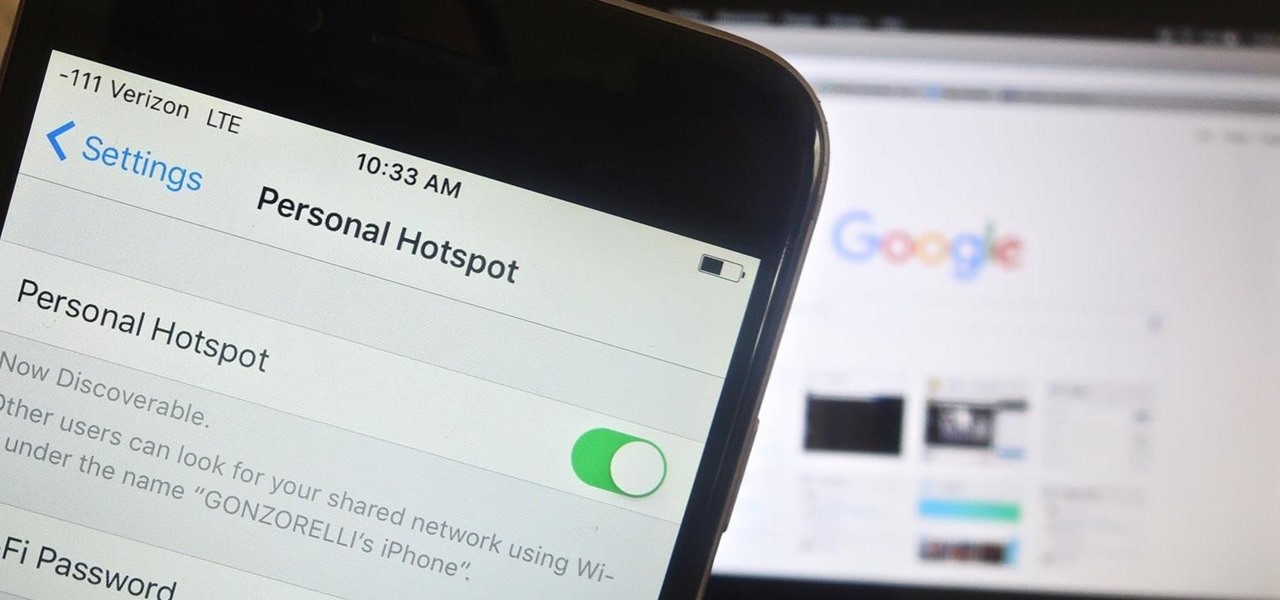
When you're in a bind and need an internet connection for your laptop, look no further than your iPhone. Using the Personal Hotspot feature in iOS, you can share your iPhone's internet connection with other devices by way of Wi-Fi, Bluetooth, or even USB.
Hello everyone! I'm glad to post my first tutorial and hope you will appreciate it.

Frosting, for many, is the best part of the cake. There's not much to dislike about it, after all—there's a type of frosting for every person. Whipped frostings for those who like it light, dense buttercream for indulgent sugar fans, cream cheese frosting for the tangy crowd... and so on. But I'll bet you've never made or tried frosting made with Jell-O packages before! Infusing your frosting with the sweetness and bright color of Jell-O changes both its taste and appearance, and using Jell-O...

Boxed brownie mixes advertise their convenience compared to homemade brownies—with only a few ingredients, they promise a moist, chocolatey crumb. However, these "instant" mixes still require fresh ingredients and a baking time that matches that of homemade brownies. When you're craving a chocolate fix but you're coming up short on eggs, oil, and time, don't despair: you can still make brownies using a can of soda. Two Different Methods, One Soda Required

For reasons unknown, Microsoft decided to change the way the Guest account feature in the new Windows 10 operating system works. In previous versions, the Guest account feature allowed you to set up a limited account for other users so they don't have access to your important documents and settings. Now, the process requires assigning an email to a new account and configuring share settings.
It's been a while, since I have just started High School. I have put a hiatus to my pentesting for a few weeks, and now, I am making a return. I have taken time to read about code, (even did a research article analysis on how humans can write "beautiful" code and something like that) and pentesting, but never made a full return. I will be occasionally coming back for a while.

Butter is one of the most versatile ingredients in the world: its variety of uses range from brightening a morning piece of toast to finishing a beautiful rib-eye steak with decadent flair.

Piracy, it can be argued, is the scourge of the internet. But when it comes to music, sometimes it's best to give a listen to a track or album before deciding to spend your hard-earned money on fully supporting it.

Downloading YouTube videos for offline use to watch later has always been a problematic endeavor. Dedicated third-party apps don't last long in the App Store, web-based converters aren't very functional on mobile, and rogue apps outside the App Store are tricky to sideload and open up the possibility of vulnerabilities. But that doesn't mean you still don't have a few good options.

Developing GUI apps in python is really cool. I ask those who understand the language to help convert some of the command-line or console programs or apps ( I mean programs that are useful to a hacker ) to GUI. I know GUI makes us lazy and not wanna learn but we should all know its fast. Today's tutorial is on p2p chat app I developed last week and decided to share it with the community since its kinda cool.

The peanut butter and jelly sandwich has officially left the building. When you eat this every other day in elementary school, you've sort of reached your limit. The thing is, peanut butter itself is delicious and quite versatile if used in the right way. Let's explore this kitchen cabinet staple and showcase it via the three dinner courses.

There are certain ingredients that chefs regularly use to elevate their food beyond the status of what us mere mortals can create. Shallots are one. Good, real Parmesan cheese is another. And the rind of that real Parmesan cheese just so happens to be one of the culinary world's biggest kept secrets.

We're all familiar with the sinking feeling that happens when you cruise through a recipe, only to arrive at an instruction that calls for a tool you don't have. Some of the best food hacks (and my personal favorites) exist to combat that problem. Why spend money on a kitchen tool—or worse, avoid a recipe altogether—when you could find a new way to achieve the same result?

If you're a Mac user with an Android phone, some apps on your computer aren't very useful, such as Messages, which is meant to work and sync with iOS devices. But now, thanks to MDRS, LLC, using the Messages app on your Mac with an Android phone is now possible and easily achievable. Plus, we've got 50 promo codes to give away for a free year of service!

Here at Food Hacks, we're very fond of finding ways to regrow food. That means taking things like carrot tops and leftover bits from garlic, onions, chives, and other herbs and aromatics to create mini reusable herb gardens.

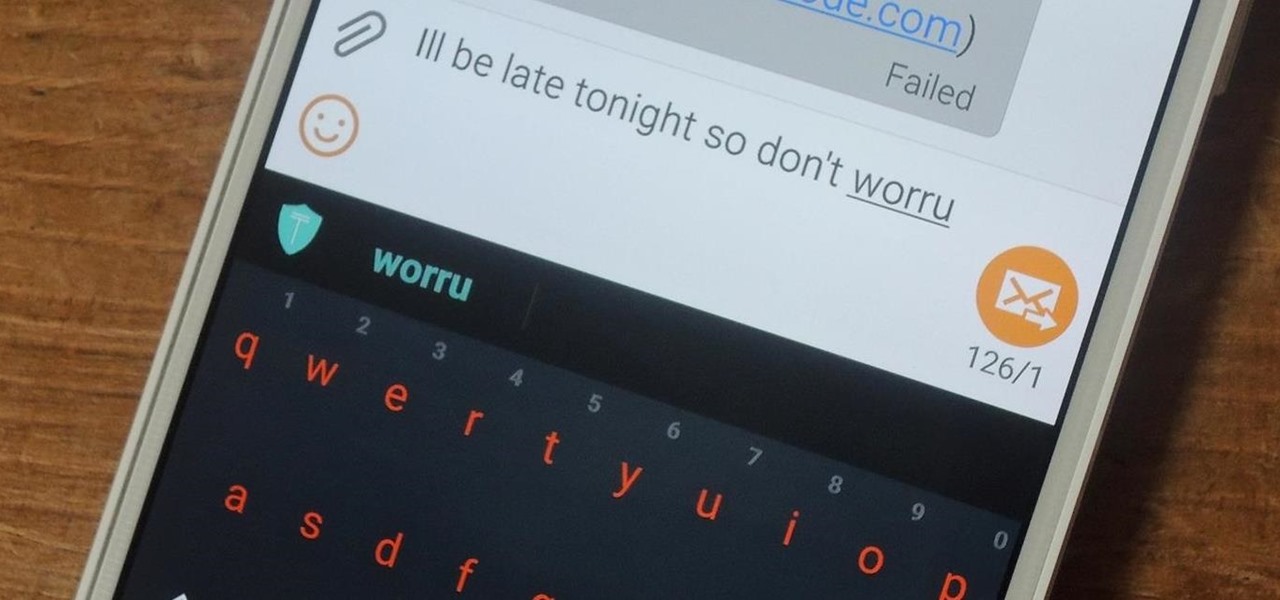
My reliance on autocorrect has made me a horrible speller. I take it for granted that it'll catch all my mistakes, but it only ends up making matters worse (especially when it inadvertently makes correct words wrong). So instead of relying on autocorrect to fix typos, why not try to completely prevent mistakes from happening in the first place?

There are a lot of frustrations when you're dealing with cramped living quarters, but you can do a lot of good cooking in your tiny kitchen if you make the most of your space. These storage hacks will make it easy to cook delicious meals, no matter how limited your square footage.

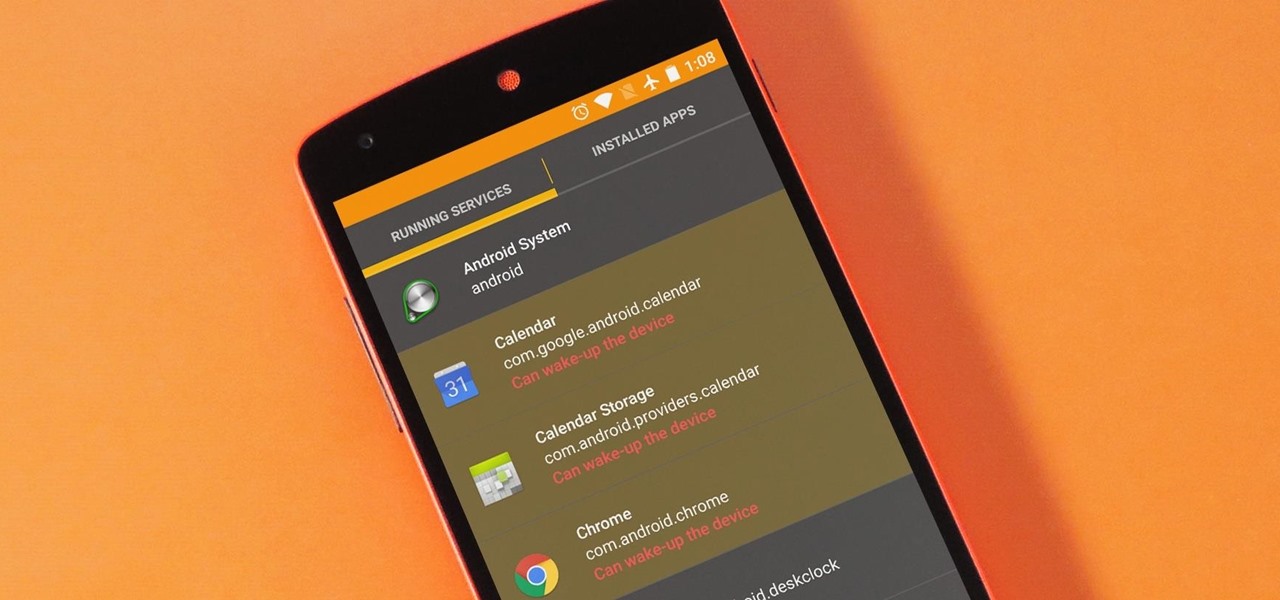
The vast majority of Android apps use background services to sync data, check for location updates, and perform various silent tasks. These background services can start up whenever they'd like, and they continue to run in the background even when you're not actively using the app that they originated from.

These cake eggs are a gorgeous treat that also makes a delicious April Fool's Day prank. Getting a fairly humdrum breakfast of boiled eggs and fruit and discovering that it's cake instead is an eggcellent surprise, isn't it? If you want to make these for Easter instead, then they're an Instagram-worthy dessert to grace your brunch spread. This might be the only dessert that is appropriate for both April Fool's Day and Easter.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

As touchscreen phones continue to evolve, the need for physical buttons seems less and less pronounced. While hard keys may seem like an endangered component on mobile devices, save for the Samsung Galaxy line, it'd be difficult to fathom a world where volume keys are absent.

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

Today, I want to share a tutorial on one of the most useful but old methods which you could use to hack websites, that is using the Dot net nuke (DNN) vulnerability . I know some of you already know about this method.

With the sheer amount of photos, videos, and miscellaneous files we place on our computers, proper organization becomes necessary. Not only so that we can quickly get to a file when it's needed, but also to declutter folders and keep them from looking like random file dumps.

Finding the right theme can be a pain. Some are too gaudy or simple, while others look like they were thrown together as a joke. So why not try your hand at making your own?

The lack of Xposed support on Android Lollipop has left modules like GEL Settings incompatible with my Google Play Edition HTC One, so I've had to find a new launcher to meet all of my needs. While I can safely say I will never find the perfect launcher for me, Blinq comes pretty damn close.

From parents and other family members to friends and peers, personalities are built by environment. Though people are important in the development of our own individual personality, there are other, different influences, including what you choose to read. The books you take the time to enjoy can make you nicer and more understanding, or leave you overall unchanged.

Decisions are rarely easy to make, and there are countless ways to mull your options over. You can sleep on it, pluck flower petals, make a list of pros and cons, or even follow the advice of a psychic. Yet to make the best decision possible, you might want to consider holding off until a certain time of the day—or even until you feel specific emotions. The state you find yourself in has significant impact on each decision you make.

It's a shame that one of the world's tastiest foods can be such a pain to prep. Most cooks are familiar with this conundrum: chopping or crushing garlic releases a pungent liquid that causes bits of garlic to stick your knife and hands, creating a messy affair. So what is going on here? The common assumption is that the garlic is releasing some kind of oil, but the truth is that this liquid rinses away easily in water. Yet one of the basic precepts of chemistry is that oil and water don't mix.

One of the biggest under-the-hood changes in Android 5.0 is a new, robust Camera API. When Lollipop makes its official debut, this API will allow developers to hook into your phone's camera sensor like never before.

Can you tell when someone is shooting you a fake smile? Even though fake smiles are easy enough to see through, we all still do it, attempting to show others just how happy we are when we're really feeling less than fantastic. Unfortunately, every smile we fake makes us a tiny bit more miserable.

"Cooking" with liquid nitrogen seems like one of those activities that should be strictly limited to pros who are appearing on Top Chef, but it's the only way you'd ever be able to make Dippin' Dots at home. If that isn't enough of a reason for you to get some LN2 for your kitchen, check out this dose of pretty:

We've already shown you how to free up internal space on your iPhone, and now it's time to tackle another problematic storage issue—your iCloud account.

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

Welcome back, my budding hackers. So many of you are interested in hacking Wi-Fi that I have decided to revisit my Wi-Fi Hacking series with some updated and more in-depth material. I strongly suggest that you look at some of my earlier posts, such as "Getting Started with Terms and Technologies" and "Getting Started with the Aircrack-ng Suite of Wi-Fi Hacking Tools," before continuing here. If you're ready, you can also check out our updated 2017 buying guide here.

The bootloaders on the AT&T and Verizon Wireless variants of the Samsung Galaxy Note 3 still cannot be unlocked, despite the $1,400+ bounty that arose late last year. Nine months later and still nothing. But just because we can't "unlock" the bootloader doesn't mean we can't get around it.

One of Android's strengths when compared to other mobile operating systems is its ability to set third-party apps as the default handler of certain file types. Instead of being stuck with pre-installed system apps when it comes to opening files and links, you're free to choose a better-fitting alternative.

Certain files contain sensitive data that you don't want being shared with just anybody. Even still, it would be nice to be able to send such a file to a certain confidante without fear of it falling into the wrong hands.