For years, smartphone makers have been caught up in a megapixel spec race to prove that their camera is better than the next guy's. But we've finally come to a point where even the lower-end camera phones are packing more megapixels than they need, so it's getting harder to differentiate camera hardware.

This is my first article on here, it's based off of a project that I'm working on at school which is on three ways to bypass windows user password's. If all goes as planned and you all would like I'll work on part two and part three and post them as soon as I can. I do have to give credit to Puppy Monkey Baby and The Defalt, both of whom are my classmates at college and have helped me with writing this article.

If you read my previous post, "How to Hack into a Mac Without the Password", you know that it is very easy to break into someone's Mac if you have physical access to the computer. Now the question that lies is, how do we protect ourselves from this happening to us? Well, here is a way that guarantees that no one will be able to change your password through OS X Recovery.

Chicken breasts have gotten a bad rap. Dry, flavorless, boring... poor white meat gets no love, and dark meat gets all of the credit for being sinfully flavorful and delicious. But the truth is, even though chicken breasts are lower in fat and calories, they can also be incredibly versatile and full of flavor... if they're prepared correctly. You're probably familiar with poaching, which is a technique that gently cooks more delicate meats such as chicken or fish fully submerged in a liquid b...

I'm back. School's an ass. On my quest for knowledge, which started approximately 3 years ago, I can upon an interesting little artifact. It is called the Arduino.

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - at my blog, here - https://techkernel.org/2015/12/11/embed-metasploit-payload-in-apk-easily/

Android has a brand new mobile payments system, and it's rolling out to most devices as we speak. Android Pay, as it's called, will replace the existing Google Wallet app as an update, and it brings some awesome new functionality such as tokenization and the ability to tap-and-pay by simply unlocking your phone.

Like a strong-tasting cup of joe, but want more caffeine out of it? Start double brewing your coffee. To paraphrase a big fan of the double brew process on Reddit, it'll make you feel like you can throw an orange at 60 percent the speed of light. It's that strong. Really.

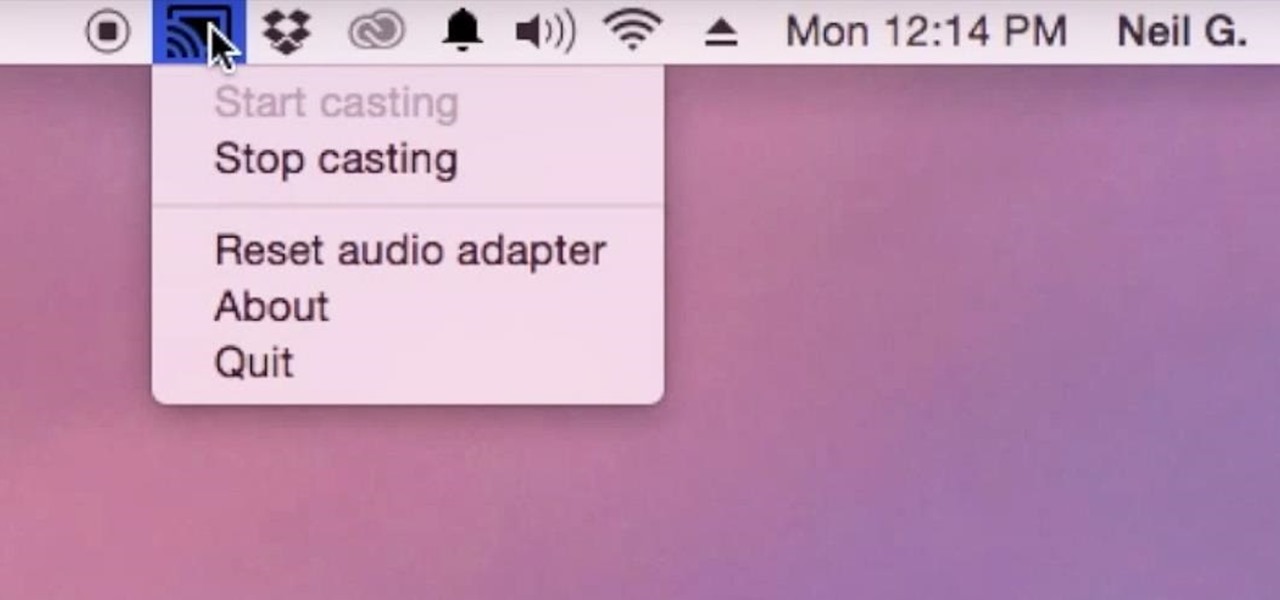
Although I know it will never happen due to Apple and Google's tempestuous relationship, I sometimes wish I could cast iTunes or Apple Music from my Mac to Google's Chromecast. When you don't have speakers to blast your music, the television is a great alternative to amplify your music.

To be twentysomething is an awkward time for entertaining. As we graduate college and begin to work in “the real world,” there is a yearning to transition from keg parties into dinner soirées. However, though the desire is there, often the bank account is not. Here are some ways to do in the kitchen what twentysomethings do best: fake it until you make it. (In other words, host a fabulous dinner party for four and still be able to make rent this month!)

With the amount of time we spend glued to our smartphones, they could be considered a second job (if only we got paid). I spend a large part of my day scrolling through Reddit, Facebook, Instagram, and countless other apps, and burn through hours and hours without even noticing.

The Galaxy S6 might just be the best Android phone on the market right now. From a hardware standpoint, Samsung truly knocked this one out of the park with its finely-crafted build quality and amazing screen.

After several weeks of testing out the public beta, Apple has finally released iOS 8.3 to the general public. The latest iteration of iOS for iPad, iPhone, and iPod touch serves mostly as an update to fix many of the bugs that plagued earlier versions, but there are still a couple of awesome new features included in the new build.

While honey is one of the most popular ingredients on kitchen shelves the world over, honeybee pollen is still a relatively rare find in most households. It's not hard to guess why: eating pollen just sounds weird... it would probably sell a lot better if it had a more appetizing name, like honey. Furthermore, it looks unlike any other common ingredient, and the smell can be off-putting to some. But it's good, it's healthy, and it's altogether pretty awesome!

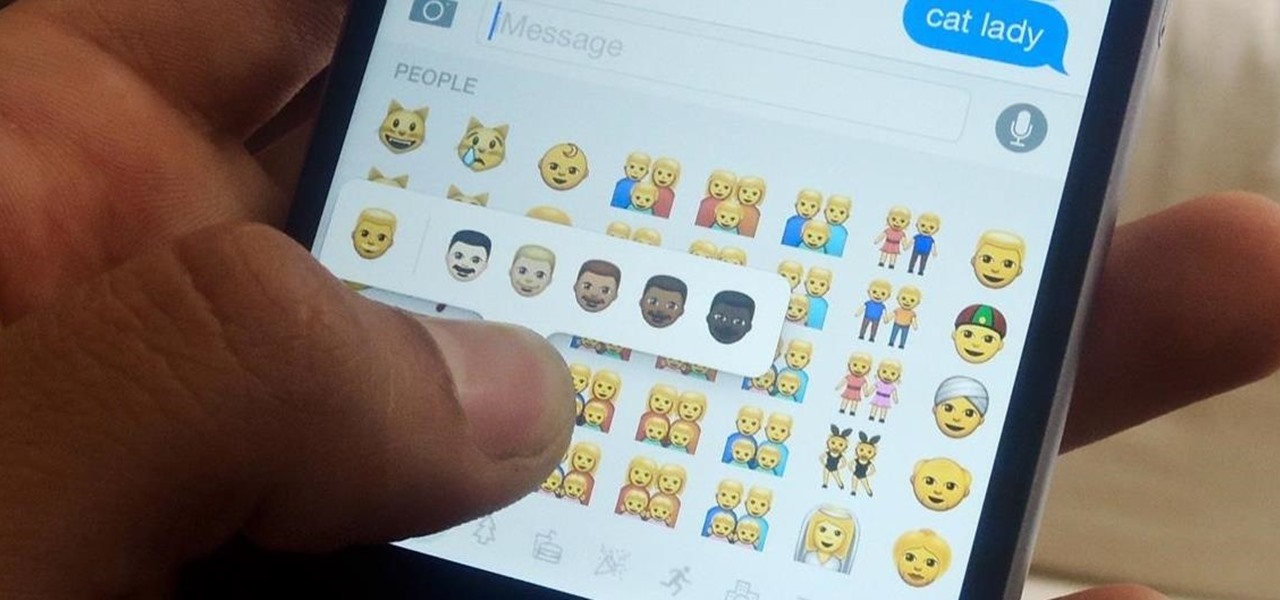
If you are anything like me, you have a knack for taking silly selfies of yourself, i.e., taking scotch tape and wrapping it around your face to make yourself look like the blob, or perhaps you like taking selfies of yourself in weird or unusual situations doing weird and unusual things.

The only mail I like getting comes in the form of an Amazon package, but when I go to my mailbox, it always ends up being a pile of credit card offers and catalogs I could never see myself ordering from. Those pieces of junk mail usually end up in the trash, which is horrible when you think about all the trees that had to get cut down in order to produce them.

Shopping: you either love it or hate it. With a tight budget, shopping can become a huge headache for even the biggest shopaholic. We've all been there, and we've all given in to our impulses and bought something we probably shouldn't have. Yet strolling through the mall doesn't have to require a strong will to keep your credit card from entering a downward spiral. You just need to keep your hands to yourself.

Most of you already know that a zero-day exploit is an exploit that has not yet been revealed to the software vendor or the public. As a result, the vulnerability that enables the exploit hasn't been patched. This means that someone with a zero-day exploit can hack into any system that has that particular configuration or software, giving them free reign to steal information, identities, credit card info, and spy on victims.

First, I want to give credit to the author where I first found how to do this: Astr0baby's Blog. This article was dated, so I took the script on his page and reworked it to make it work today. (I also included the way to make it hide the cmd line popup.) Requirements

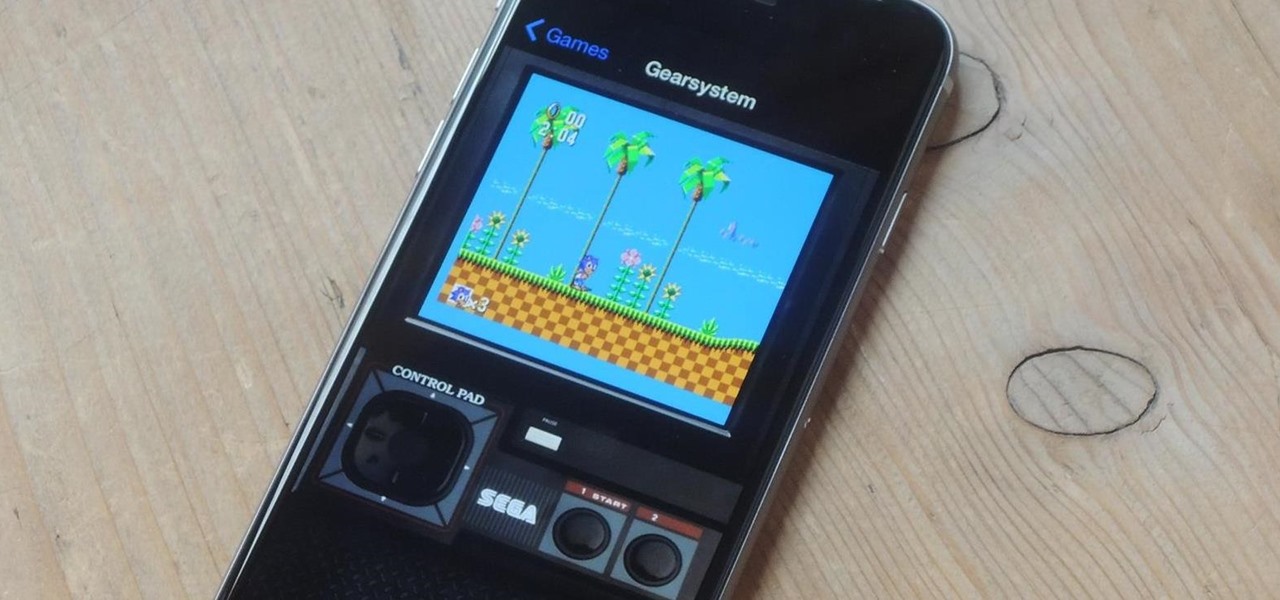
The Master System, more popularly referred to as the Sega Master System, or SMS for short, is a video game console that was released in the mid-1980's as a direct competitor to the original Nintendo (NES).

Yes, I know. Nexus owners aren't exactly the biggest Apple fans out there. That "Pure Android" experience was one of the main reasons we bought our Nexus devices. But give the other side some credit—the iPhone's operating system has come along way, and is still the champ when it comes to aesthetic design (at least until Material Design dethrones it this fall).

Merely fidgeting and shivering can burn calories, but now you can add trembling in fear to the list too. Just pop in a good horror movie and turn down the lights to burn off up to 200 calories. What would you rather do? Walk for over 30 minutes or watch a 90-minute scarefest?

Instagram is not only a great platform to easily share some of your favorite moments with friends and family, it's a useful service for peering outside of your physical location. While you share a picture of your dog in Los Angeles, you can almost instantly view and like a picture someone posted of their breakfast in Tokyo.

There's more to earning someone's trust than simply shaking their hand, especially if you're not particularly trustworthy. Your body language doesn't reveal your thoughts, it reveals your intentions, and sometimes intentions are better left unrevealed. Psychopaths, take note...

Hey, coffee drinkers—your morning cup of joe is killing your metabolism.

Erudite. Barbiturate. Cacophony. Denouement. Okay, that last word is technically French, but words like these make the average person sweat, and it turns out that the key to learning how to pronounce them once and for all just might be getting them wrong.

How many times have you heard someone utter the phrase, "Now, let's break into groups"? From classroom discussions to workplace think tanks, gathering into groups to generate ideas is common practice. These forced get-togethers are intended to encourage creativity and unique thought, but they can actually do the opposite. More often than not, group brainstorming is annoying rather than encouraging, and these group sessions can actually be detrimental to your productivity. Getting together har...

The best sangria I ever had in my life was made by a Spanish friend for my birthday party. The ingredients included a giant box of Franzia red, one bottle of Bombay Sapphire Blue, one cup of sugar, a liter of 7-Up, and some cinnamon sticks. She put everything but the 7-Up in a giant zinc bucket from Home Depot and insisted that it had to sit overnight so the flavors could blend (and so the Franzia wouldn't taste so, well, Franzia-ish).

To flip, or not to flip, that is the real question. When you're nervously standing over the stove or grill, what do you do with that steak before you?

A few days ago I finally finished my 2 week journey into trying to get OpenVas to work properly. You all may have noticed that you can't just click the setup openvas in kali and have it working properly.

Welcome back, my greenhorn hackers! Although we have focused primarily on technical hacks here, social engineering can sometimes be especially effective. This one requires a bit of technical skill, but not too much. In addition, it's limited by how specific a target you can choose—but it will work.

I have a theory that chocolate chip cookies are the gateway drug to cooking. The recipe is easy, no special equipment is required, and at the end, you get warm, fresh-from-the-oven cookies that are simply irresistible. It's how I got hooked on baking and cooking, and anecdotal evidence (i.e. me asking my other kitchen-obsessed friends and a few culinary students) supports me.

A perfectly cooked roast potato is a study in contrasts: the outside should be crisp, crunchy, and salty, while the inside is tender and fluffy. Too often, however, roast potatoes come out overcooked, greasy, and tough.

Sometimes you've got a head of lettuce that you want to eat but it lacks a certain youth. In other words, it's wilted and browning at the edges. Other times, you get to the grocery store near the end of day and the only lettuce or greens available look a little on the sad side. Never fear. You're not doomed to a meal of fast food or mouthfuls of soggy salad. You can easily revive those leaves and have something crisp, green, and delicious for your next meal, so don't dump it in the trash.

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.

On the new Moto X smartphone, the only thing you have to do to activate the virtual assistant is say "Okay, Google Now." That's it. You don't have to press a button or tap on the display at all. It's always ready for your voice commands via its "Active Listening" feature, making it a truly hands-free experience.

I've never understood gift cards. Aside from being severely restricted as to where you can use them, they're also a strange gift, especially if you don't shop at that particular store. Some even have expiration dates and service fees.

"Ahoy-hoy." If telephone titan Alexander Graham Bell had his way, we'd all be answering phones like Mr. Burns. Thankfully, frienemy Thomas Edison had enough sense to realize we weren't always on the briny. He preferred "hello" as our standard telephone greeting, which he is credited with coining in 1877. Fellow American pioneer Davy Crockett actually used it as a greeting first in 1833 (as compared to an exclamation)—but in print, not over the phone.

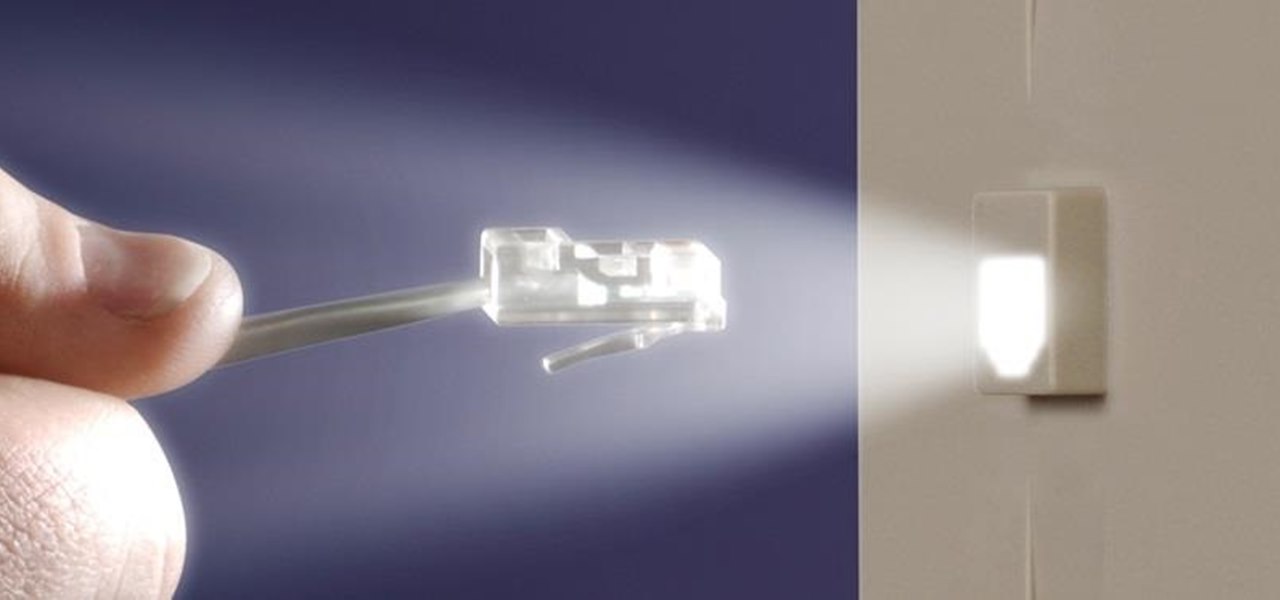
Today's project will show how you can convert your laptop, smartphone, or tablet computer into a makeshift projector—just in time for March Madness! It's super cheap to build, and can add a little bit of creative fun to your next sports party.

Craigslist is probably the greatest site ever created, and I'm just talking about it's classified section, both awesome and amazingly creepy. Seriously, spend 20 minutes scrolling through the personals and you'll never want to take your eyes off the screen. But I digress—Craigslist is also one of the most convenient places to buy and sell pretty much anything you can think of. I've used it to buy my bed, my old bike (which was stolen!), and my couch. And while Craigslist is great in many ways...