The food TV chefs prepare make our mouths water. From one scrumptious creation to another, they fly through preparation without frustration or error. They make us think we can do the same with similar ease and delectable, picture-perfect results. Some of us have noticed, though, that these TV chefs don't always adhere to the same safe food handling guidelines we've been taught to follow.

Cats give us so much—companionship, loyalty, love... and now the bird flu. Several weeks ago, a veterinarian from the Animal Care Centers of New York City's Manhattan shelter caught H7N2 from a sick cat. According to a press release from the NYC Health Department on December 22, "The illness was mild, short-lived, and has resolved." This isn't the first time cats have passed infections on to humans, but it is the first time they passed on the bird flu—avian flu H7N2, to be exact.

Months before London-based Jonathan Moon would turn 30, he started musing over how to celebrate. While he had rung in past birthdays at home, he wanted to do something out of the ordinary as a farewell kiss to his twenties. A short ski vacation with friends felt like the perfect idea.

Even when no one is in your kitchen, it is crowded. The refrigerator, sink, and counters are all covered with microbes that are just hanging around. They are inadvertent remnants from the raw chicken you used in that recipe last night, brewing a bacterial cocktail in your Nespresso machine, or just growing their merry little colonies on your leftovers.

The Meta 2 developer kit has finally begun shipping! Gary Garcia, the senior director of customer success at Meta, just sent out an email that they are shipping out to the first round of preorder customers. Waves will be building from there, up to far higher manufacturing rates near the end of Q1 of 2017.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

If you've ever played the game of Would You Rather, you've probably been given the ultimatum between eating insects or doing something else that sounds absurd, like licking a cactus. I'm advising you to always choose the insects, and here's why:

The international, Exynos-powered Galaxy S7 and S7 edge have had a working root method ever since a few days after release. But the North American variants—those using Qualcomm's Snapdragon 820 processor—have locked bootloaders, and have proven to be almost unrootable up until now.

Swipe keyboards such as GBoard, SwiftKey, TouchPal, and Swype are handy for quick one-thumbed typing on an iPhone, but Microsoft upped the game with its experimental Word Flow Keyboard. In short, the keyboard fans out to occupy the natural range of your thumb, where you can type or rely on predictive swiping.

This year's Nexus devices are already two of the best bang-for-your-buck smartphones on the market, but with a new sale price from several retailers across the net, they might just be an unbeatable deal.

Using a technology we like to call "Hive Computing," several Android apps allow you to contribute idle processing power to help further scientific research. This basically means that when you're not using your phone or tablet, it can join forces with other idle devices to form a supercomputer that scientists can use to potentially make a world-changing breakthrough.

Coverage for the 88th Academy Awards, aka the Oscars, will air live this Sunday, February 28th at 4 p.m. PT (7 p.m. ET). The ceremony itself, hosted by Chris Rock, is set to begin at 5:30 p.m. PT (8:30 p.m. ET).

When performing something such as a mass mailer attack on a company, sending executables usually isn't the best option. That's why, in this tutorial, I'll be teaching you how to code a VBA script macro into a Word document in order to compromise a system. Combined with a little social engineering, this can be a very effective technique.

Greetings to all geeks, hackers, nerds, and explorers of Null Byte. Welcome to my brand new tutorial, "Using BASH for Computer Forensics". This tutorial will give you a look at how the computer programming language, Bash, can be used to find out details on apple devices for later use.

When an album sells a million copies, it gets certified as platinum and cements itself as one of its generation's biggest hits. When an album sells 10 million copies, it reaches diamond status and transcends generational gaps. But when an album sells well over 40 million copies, there's only one thing you can call it—Michael Jackson's Thriller.

Though you can use the Social Engineering Toolkit to clone websites, this way is much more customisable.

Well, this is my first article so if it sucks tell me...lol!! Story Time

As you're probably well aware by now, the Apple Watch isn't just for sending text messages and checking Instagram—you can also use it as your wallet. With Apple Pay compatibility, you can use your Watch to make purchases at any retailer that accepts the payment service.

A group ironically called the "Guardians of Peace" hacked into Sony Pictures' computer systems and released a mountain of internal information such as medical records, leaked scripts, work complaints, and even celebrity aliases.

Google's music offerings have been on a roll lately. First they announced a new music video streaming service called YouTube Music Key, offering ad-free playback with background listening. Then they stated that the new offering would be rolled in with their Google Play Music service, with members allowed to exclusively test the Music Key beta, which just went live. And if all that wasn't enough, they're also offering free music to boot!

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

Now that you've updated your iPad, iPhone, or iPod touch to iOS 8, there's a lot of cool new things to explore. If you felt a little overwhelmed from all of the detailed information available in our Coolest Hidden Features of iOS 8 post, then I've got a simple breakdown of all of the new features available with quick links to their walkthroughs and pictures, if available. Watch the short video roundup, or skip below for the list.

The new iPhone 6 and 6 Plus have bigger displays, and that means more overall screen real estate, something that the new Safari app has taken into account by letting you access desktop versions of mobile websites. Even if you're sporting an older device, you'll still be able to request the desktop version of a site online in the browser.

Each day, we read about another security breach somewhere in our digital world. It has become so commonplace that we hardly react anymore. Target, J.P. Morgan, iCloud, Home Depot, and the list goes on and on.

Researchers at the University of California, Riverside and the University of Michigan announced recently that they have developed a hack that works 92% of the time on Google's Gmail system on Android, as well as with the H&R Block app.

T-Mobile continues to make waves in the U.S. wireless market behind CEO John Legere's UnCarrier program. At the latest installment in a series of industry-challenging announcements, Uncarrier 5.0 unveiled Test Drive. The new program is set to allow would-be customers to try out the "latest generation" iPhone for seven days on T-Mobile's network without any financial commitments.

Remember the feeling you had the moment you removed your shiny new Nexus device from its packaging and booted it up for the first time? You swiped through the app drawer at lightning speed and thought to yourself, "This is the last Android phone I will ever need, they just aren't going to get any better than this."

I love making stock. It's thrifty because you get extra use out of poultry bones and vegetable peelings, plus having homemade stock on hand makes so many things taste better, from soup to stews to pasta sauces. If you deglaze a pan, homemade turkey stock, booze of some kind, and butter will create an eye-rollingly good sauce in mere moments. One task I do not love? Figuring out how to skim the damn fat off the stock (or soup) after I've made it. It's necessary to skim the fat as you boil down...

Sometimes, ceiling fans just don't cut it. They spin meekly, barely generating any air flow to cool down your sweltering room. Or, when turned up high, they can wobble wildly, shaking and vibrating as if the ceiling is about to come crashing down. If this sounds like your ceiling fan, chances are the solution is a simple as flipping a switch.

Remember those horrible, soul-crushing studies from a few years back linking grilled meats with cancer? Unfortunately, they're still true, but scientists have recently found that an unexpected ingredient can curb some of the harmful effects of high-temperature cooking.

Unless you've been living under a rock with no internet connection, it's safe to say that you've heard of the Heartbleed flaw that allows practically anyone with the right knowledge to steal your personal information, such as passwords, credit card numbers, and e-mail addresses using OpenSSL.

If you're a Febreze fanatic, you're well aware that the "odor eliminator" can be pretty pricey, and that's reason enough to stop buying it.

A new coat of paint is an easy, cheap way to make your home look instantly better, but dealing with paint fumes for days afterward isn't so fun, especially if you have kids or pets.

It's so nice to be able to reuse old glass jars for food storage. Occasionally, though, even the sturdiest container has to be recycled because it retains the smell of its previous contents. Usually the culprit was garlic, garlic-based, or something pickled, and you're certainly not going to store your fresh herbs or fruit in that. There is, however, a quick and easy way to get that old stink out of your jar and make it usable again. You just need two things...

Welcome back, my hacker apprentices! To enter the upper echelons of hackerdom, you MUST develop scripting skills. It's all great and well to use other hacker's tools, but to get and maintain the upper hand, you must develop your own unique tools, and you can only do that by developing your scripting skills.

Doritos Locos Tacos were the brilliant concoction of a man named Todd Mills who never worked for Taco Bell, and never made any money from his creation. He originally pitched the idea to Frito-Lay, and when they said no, he took matters into his own hands by creating a Facebook page.

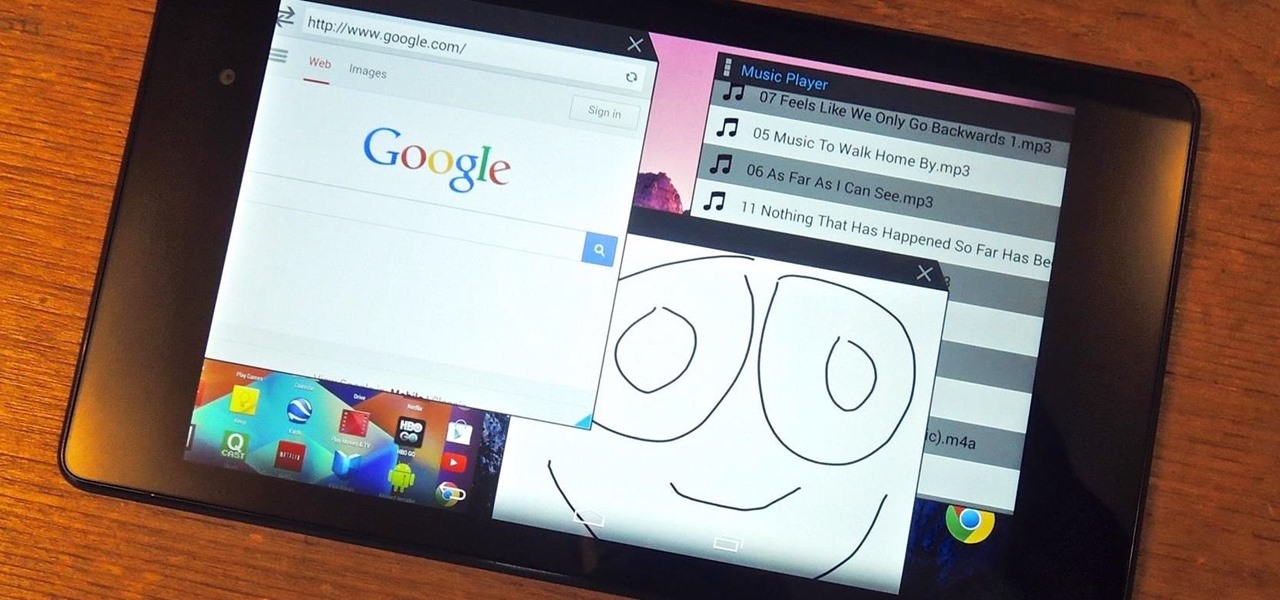
Recently, I offered a guide detailing how to run two separate windows on a Nexus 7 tablets for better multitasking. While extremely useful, that mod was limited to only two windows, and you also needed root access to use it.

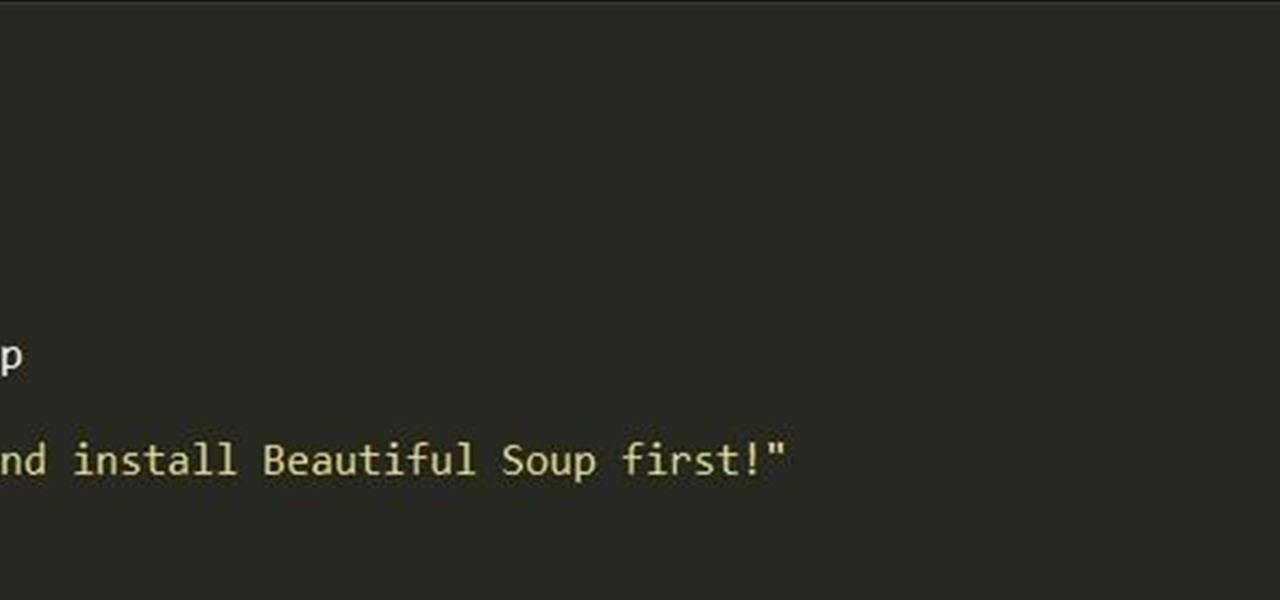
Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

Streaming apps like Netflix, Hulu and Amazon Instant Video have been available on game consoles for a while, but if you're in a country where they're blocked, it can be hard to find a way around. There are apps and extensions like Hola Unblocker and Media Hint and that to bypass location restrictions on your computer, but what about your Xbox?

There are several ways to get around location restrictions on subscription sites like Netflix and Hulu using apps, extensions and proxies, but they tend to only work on laptops and computers. Users who want to access content from mobile devices and gaming consoles are usually out of luck.