If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.

In a move sure to stir up even more speculation about the future of Snap Inc., the company's vice president of content, Nick Bell, is leaving the company after five years.

With the iPhone X, Apple introduced a brand new way for iOS users to interact with their iPhones. Gestures took the spotlight, as they very apparently replaced functions you would normally execute on the Home button. But swipes aren't everything for the new iPhone XS, XS Max, and XR. Don't believe us? Just take a look at the Side button.

While most kids his age are busy playing Fortnite, 11-year-old Yumo Soerianto is developing augmented reality games. Kids like Soerianto are the future of the augmented reality field — they'll likely be coming into their own as professional developers right as AR technologies become lightweight and powerful enough to be contained in a pair of sunglasses.

Right on the heels of the iOS 11.4.1 beta 3 release, Apple pushed out iOS 12 beta 2 to registered developers on Tuesday, June 19. Public beta testers received the same version, labeled as iOS 12 public beta 1, six days later on Monday, June 25. Last year, the iOS 11 public beta opened up just five days after the release of iOS 11 developer beta 2, so iOS 12 is pretty much right on track in that regard.

With each year that we anxiously await Apple's next big version of iOS, there comes the sad reality that the eldest iPhones will not continue to receive support. That's not the case with iOS 12, however, as the software is compatible with all iPhones currently running iOS 11, going back as far as the iPhone 5S.

While there are at least five cool things coming in iOS 11.4, they may not be enough to get you to install the iOS 11.4 beta on your iPhone. Since its initial beta release at the start of April, there have been plenty of known issues and user-reported bugs to deal with. While bugs are to be expected with a beta, you may want to read these before installing this one on your iPhone.

One of the best gifts that someone with an iPhone can receive is a paid app, hot new movie, bestselling album, gift card, or anything else in iTunes, Books, or the App Store that costs money. Even if it's a small $0.99 game that you heard a friend talking about, a gesture like this can go a long way. Gifting apps and media is now easier than ever, even if you don't have an iOS device yourself.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

When you don't want somebody you're calling to know the real phone number associated with your iPhone, whether it's for privacy reasons, to avoid being called back, or to prevent being ignored, there are multiple things you can do to block it on their caller ID.

Investors aren't keen to throw money at a new technology sector without at least some hope of a significant return on their investment in the future. That's why a recent run of activity within the augmented reality business space has stoked some new optimism among the financial community.

Apple didn't invent the concept of photos with videos embedded (that credit goes to HTC and their Zoe feature), but they sure did popularize this functionality when they came out with Live Photos. If you're jealous of iPhone users, you certainly don't need to be — there are several great ways to recreate Live Photos on Android.

Now that the holiday season has officially kicked off, Office Depot has updated its popular Elf Yourself app with a few new augmented reality options.

While Black Friday shoppers found countless deals on all kinds of smartphones, one device was overtly left out of the price cuts — the iPhone X. Walmart was the only store to offer a promotion on the newest Apple device, and even then, it was difficult to find. Cyber Week appears to have repeated recent history, with only one store offering a special on the iPhone X, but it's not Walmart this time.

Since the iPhone X has no Home button, the Side button has some heavy lifting to do. So not only is the Side button responsible for all of its usual duties, like sleeping and waking the device, it has to do everything the Home button did too. That's a lot of work for one button, but we've got everything figured out for you.

While Meta Company has agreed to a settlement in its lawsuit against a former employee and his company, they find the tables have now turned on them in the form of patent infringement allegations from another entity.

If you are an NYC commuter like me, then I'm sure you know how bad the city's transportation has gotten.

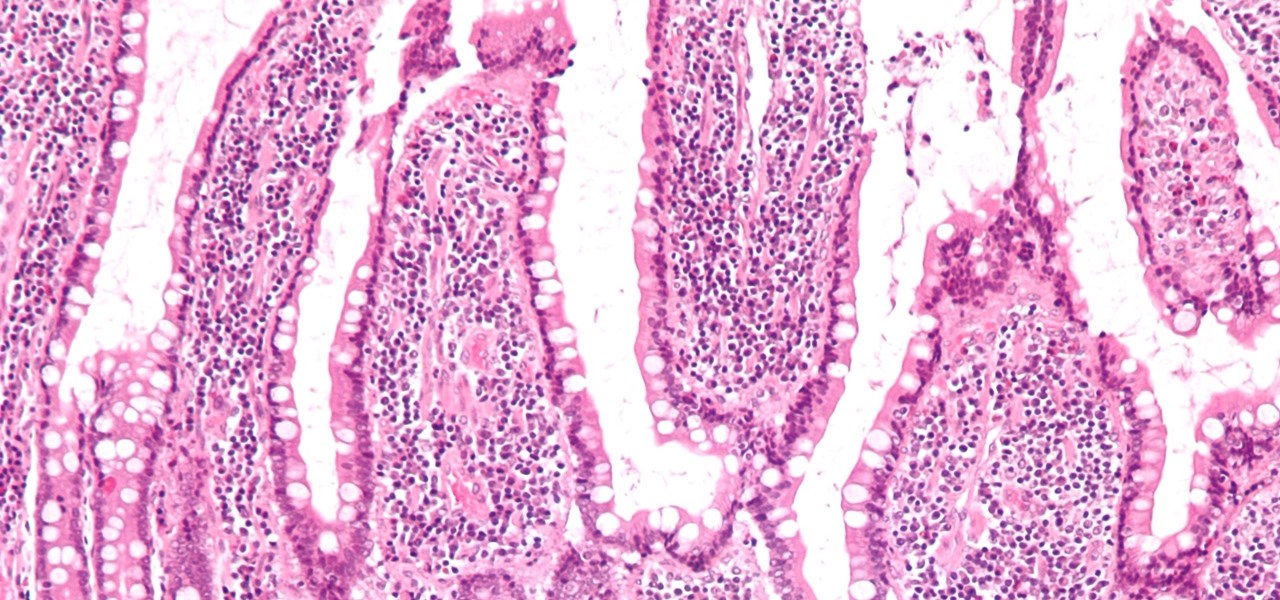
If the all the fingerlike projections in our gut were flattened out, its surface area would be 100 times bigger than our skin's. It's so large that the actions of just a small part of it can impact our health. A new research study has found that enterochromaffin cells in the intestinal lining alert the nervous system to signs of trouble in the gut — trouble that ranges from bacterial products to inflammatory food molecules.

Have you ever wanted to control a swarm of robots? Well, now you can! Robotics researchers at New York University (NYU) have created an app which controls 'bots from your smartphone, using augmented reality. This AR app would certainly come in handy when you want to make a coffee from the comfort of your couch, but let's not get ahead of ourselves!

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

Super Mario Run was released for iOS on December 15, 2016. Even though it debuted as a "free" app, almost all of the playable content was hidden behind a ridiculous $10 unlocking package. Despite coming with such a hefty price tag and receiving a two-star rating on the day of its release for iOS, Android users are still very much interested in giving this game a whirl.

This is my first article on here, it's based off of a project that I'm working on at school which is on three ways to bypass windows user password's. If all goes as planned and you all would like I'll work on part two and part three and post them as soon as I can. I do have to give credit to Puppy Monkey Baby and The Defalt, both of whom are my classmates at college and have helped me with writing this article.

Chicken breasts have gotten a bad rap. Dry, flavorless, boring... poor white meat gets no love, and dark meat gets all of the credit for being sinfully flavorful and delicious. But the truth is, even though chicken breasts are lower in fat and calories, they can also be incredibly versatile and full of flavor... if they're prepared correctly. You're probably familiar with poaching, which is a technique that gently cooks more delicate meats such as chicken or fish fully submerged in a liquid b...

I'm back. School's an ass. On my quest for knowledge, which started approximately 3 years ago, I can upon an interesting little artifact. It is called the Arduino.

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - at my blog, here - https://techkernel.org/2015/12/11/embed-metasploit-payload-in-apk-easily/

Like a strong-tasting cup of joe, but want more caffeine out of it? Start double brewing your coffee. To paraphrase a big fan of the double brew process on Reddit, it'll make you feel like you can throw an orange at 60 percent the speed of light. It's that strong. Really.

Although I know it will never happen due to Apple and Google's tempestuous relationship, I sometimes wish I could cast iTunes or Apple Music from my Mac to Google's Chromecast. When you don't have speakers to blast your music, the television is a great alternative to amplify your music.

To be twentysomething is an awkward time for entertaining. As we graduate college and begin to work in “the real world,” there is a yearning to transition from keg parties into dinner soirées. However, though the desire is there, often the bank account is not. Here are some ways to do in the kitchen what twentysomethings do best: fake it until you make it. (In other words, host a fabulous dinner party for four and still be able to make rent this month!)

With the amount of time we spend glued to our smartphones, they could be considered a second job (if only we got paid). I spend a large part of my day scrolling through Reddit, Facebook, Instagram, and countless other apps, and burn through hours and hours without even noticing.

The Galaxy S6 might just be the best Android phone on the market right now. From a hardware standpoint, Samsung truly knocked this one out of the park with its finely-crafted build quality and amazing screen.

After several weeks of testing out the public beta, Apple has finally released iOS 8.3 to the general public. The latest iteration of iOS for iPad, iPhone, and iPod touch serves mostly as an update to fix many of the bugs that plagued earlier versions, but there are still a couple of awesome new features included in the new build.

While honey is one of the most popular ingredients on kitchen shelves the world over, honeybee pollen is still a relatively rare find in most households. It's not hard to guess why: eating pollen just sounds weird... it would probably sell a lot better if it had a more appetizing name, like honey. Furthermore, it looks unlike any other common ingredient, and the smell can be off-putting to some. But it's good, it's healthy, and it's altogether pretty awesome!

If you are anything like me, you have a knack for taking silly selfies of yourself, i.e., taking scotch tape and wrapping it around your face to make yourself look like the blob, or perhaps you like taking selfies of yourself in weird or unusual situations doing weird and unusual things.

The only mail I like getting comes in the form of an Amazon package, but when I go to my mailbox, it always ends up being a pile of credit card offers and catalogs I could never see myself ordering from. Those pieces of junk mail usually end up in the trash, which is horrible when you think about all the trees that had to get cut down in order to produce them.

Most of you already know that a zero-day exploit is an exploit that has not yet been revealed to the software vendor or the public. As a result, the vulnerability that enables the exploit hasn't been patched. This means that someone with a zero-day exploit can hack into any system that has that particular configuration or software, giving them free reign to steal information, identities, credit card info, and spy on victims.

First, I want to give credit to the author where I first found how to do this: Astr0baby's Blog. This article was dated, so I took the script on his page and reworked it to make it work today. (I also included the way to make it hide the cmd line popup.) Requirements

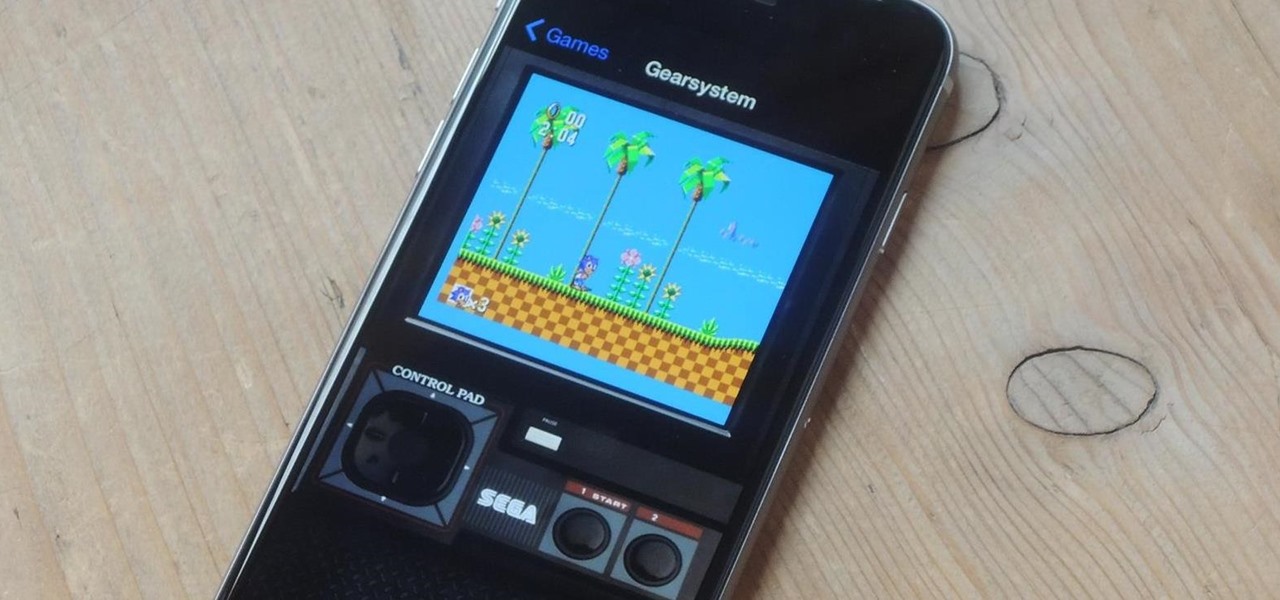
The Master System, more popularly referred to as the Sega Master System, or SMS for short, is a video game console that was released in the mid-1980's as a direct competitor to the original Nintendo (NES).

Yes, I know. Nexus owners aren't exactly the biggest Apple fans out there. That "Pure Android" experience was one of the main reasons we bought our Nexus devices. But give the other side some credit—the iPhone's operating system has come along way, and is still the champ when it comes to aesthetic design (at least until Material Design dethrones it this fall).

Merely fidgeting and shivering can burn calories, but now you can add trembling in fear to the list too. Just pop in a good horror movie and turn down the lights to burn off up to 200 calories. What would you rather do? Walk for over 30 minutes or watch a 90-minute scarefest?

Instagram is not only a great platform to easily share some of your favorite moments with friends and family, it's a useful service for peering outside of your physical location. While you share a picture of your dog in Los Angeles, you can almost instantly view and like a picture someone posted of their breakfast in Tokyo.