Celtx is an application for creating scripts for podcasts, videos, stage plays, screenplays, or any other visual (or audio) media. This podcast shows you how to mark up your script so that you can easily create a scene breakdown sheet in CELTX.
If your cell phone doesn't have internet capabilities, or you're just unwilling to pay the insane price of the web connectivity rates, you can still access Google as long as you can text message. Google responds to text messages with the best match, so it's more ideal for looking up phone numbers, addresses, weather reports, or a word definition. Watch this video cell phone tutorial and learn how to search Google on phone through SMS text messages.

Learn simple repair tips and the tool kit you'll need to keep your snowshoes chugging all winter long with this report from the December 2006 issue of Backpacker Magazine. Associate editor Jason Stevenson covers all the snowshoe snafus--from plastic zip ties to replace stripped rivets to extra webbing to cinch down shredded bindings--in this backpacking tutorial video. Repair your snowshoes and continue your backpacking expedition!
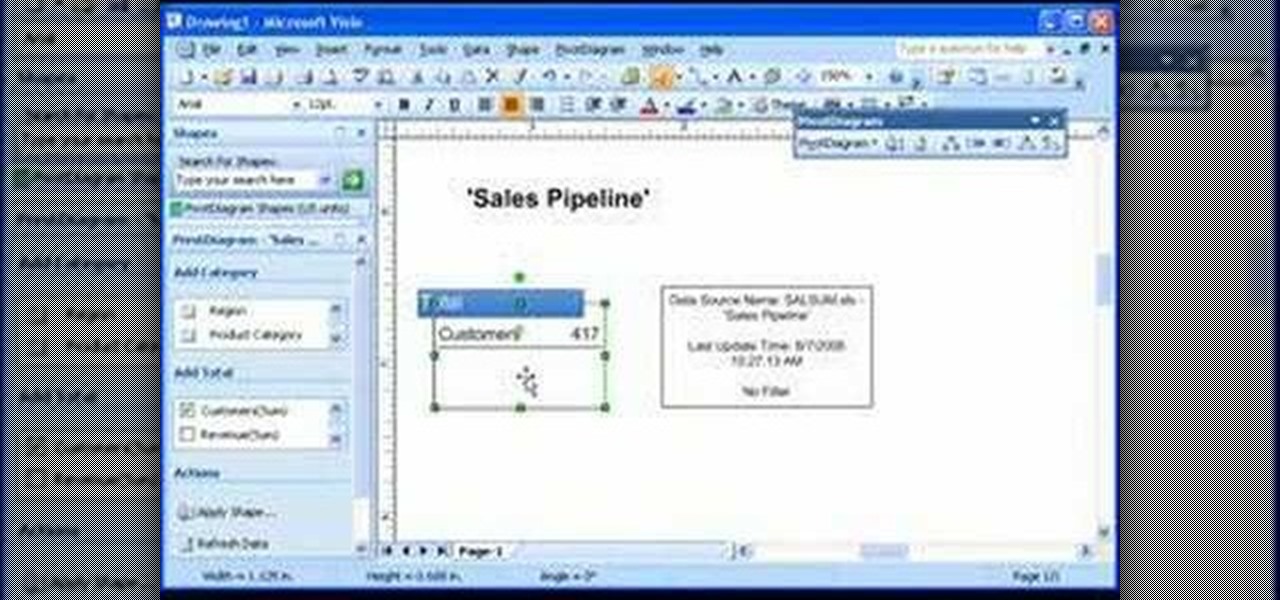
A PivotDiagram is similar to an Excel PivotTable report: It arranges data in a visual way. Check out this tutorial and learn how to look at the same data from different angles to establish and analyze relationships that you might miss in a table or a worksheet.

This how-to video shows how to get out of bog in COD4. This glitch requires old school but not the catapult glitch. This could be done in a actual old school match on Call of Duty 4. Report anyone who is cheating during a game.

Dr. Kiki makes a homemade cantenna, an antenna made out of a can, duh! Moujan reports back from the ultimate DIY event, Maker Faire 2008, and Heather goes beekeeping in the Fringe - all on PopSiren.

AddWeb Website Promoter is an extremely popular program that helps webmasters promote their site on search engines. In this installment, we explore AddWeb's Quick Rank Feature.This feature allows you to run ranking reports that are not tied to profiles. You will want to do this when you want to test out keywords and phrases without committing them to be part of your normal website profile.

Today's word is "weary". This is both a verb and an adjective. As an adjective, it means being tired mentally and physically, or causing fatigue.

If you've ever written up a lab report or done a math project then you've probably either used the equation editor before or would like to learn how to use it, since writing the equation in yourself is a pain (and doesn't really look professional).

DNS spoofing - how to use the hosts file in Windows XP to block unwanted spyware/popups/etc, block programs from reporting to a site, filter/block/redirect websites, and locally create forward lookups (IP to name resolution in network)

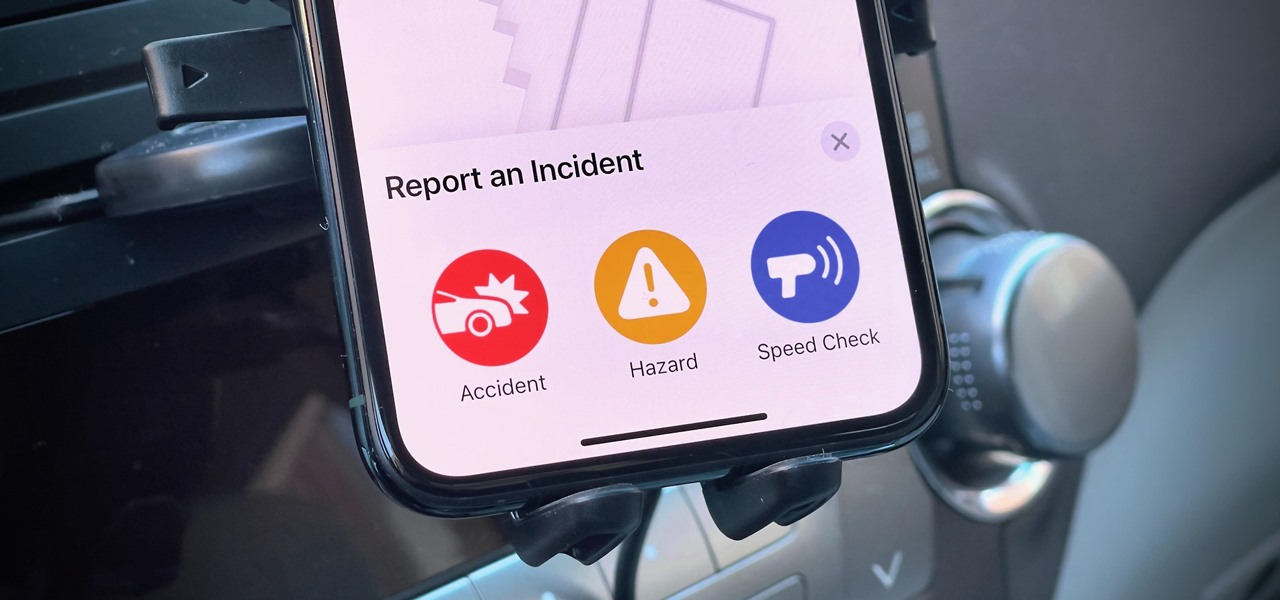
Driving is anything but problem-free. Speed traps, accidents, and other hazards can appear at any time, requiring motorists to be attentive, quick, and prepared for anything. If you see something dangerous on your route that you want to warn others about, there's an easy way to do so in Apple Maps.

Microsoft has unveiled practically every detail of the HoloLens 2 except for when eager developers and enterprise customers can expect to receive the device.

With plans to compete with Niantic and other augmented reality game developers, game developer WarDucks has closed a $3.8 million funding round.

As we predicted earlier this week, the focus has already begun to move from Magic Leap back onto Apple's rumored augmented reality smartglasses. The latest credible whispers come from none other than longtime Apple-focused analyst Ming-Chi Kuo.

Apple continues to build its augmented reality hardware and software team in stealth mode. The latest addition comes via the hiring of a former DAQRI user experience designer and VR app developer.

The Essential Phone was undoubtedly one of the most underrated phones of 2018. It launched with buggy software and camera problems, but the company worked diligently to push out updates. Many Android enthusiasts were anxiously waiting for the Essential 2 release later this summer. Unfortunately, news today from Bloomberg indicates that Essential will not release a phone in 2018.

After the spectacular rise and fall (and rebirth) of Glass, Google is taking another run at augmented reality smartglasses.

While Apple has generally been more bullish on augmented reality as opposed to virtual reality, the latest whispers about its purported AR headset suggests that it may be giving VR another look.

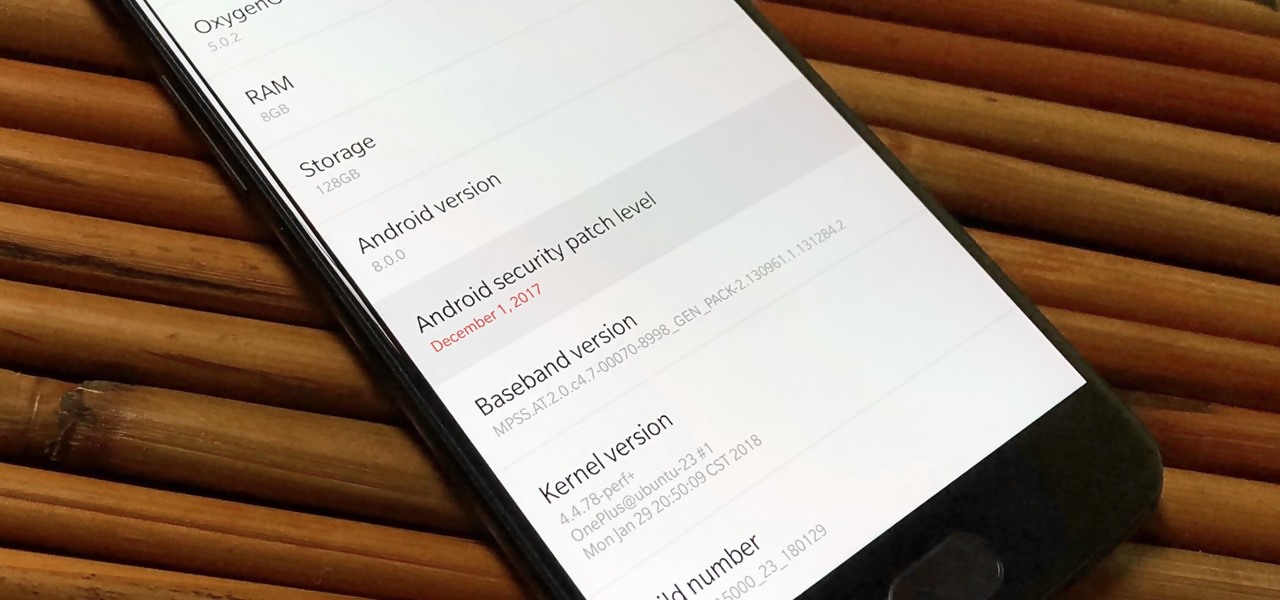
As far as overall security updates are concerned, we all know that iOS reigns supreme over Android. But just how bad do Android devices fare against Apple in general? A recent report will have you second guessing some companies the next time you're in the market for a handset.

Apple CEO Tim Cook told us that augmented reality would change everything, and now we have a better idea of exactly what he meant.

If you're on T-Mobile, you've probably had a rough morning. Reports are coming in saying that the carrier's LTE network is down in cities throughout the country.

For months, consumers have been itching to know whether it will be Samsung or Apple that has the first in-screen fingerprint scanner in their next smartphone. Now, reputable researcher Jiutang Pan has taken to Weibo to report that the answer is neither.

Nope, it's not 2016 again. Samsung is giving it another go at beating its competitor by attempting to unveil their new Galaxy Note 8 before the new iPhone. Because it worked out so well the last time.

On Tuesday, Apple held a public conference call for its Q2 earnings report. During the call, Steve Milunovich from UBS asked Tim Cook about a recent 451 report, and how it reflects a pause in current iPhone sales. Cook's response was more than interesting, to say the least:

Texas has become only the latest state to face an unfortunate outbreak of mumps, but so far seems to be the hardest hit. On April 12, two days before the CDC's report was released, the Texas Department of State Health Services released a health advisory indicating this is the highest instance of mumps reported in 22 years.

A baby with severe Zika-related birth defects was born in San Diego County this week, prompting officials to urge pregnant women to avoid disease hotspots.

A sometimes serious disease spread by fleas is making inroads in Texas, quietly doubling case numbers since 2008, and beginning to encroach on larger metropolitan areas.

The Note7 fireworks bonanza was unprecedented in scope. A recent report suggests that Samsung could lose upwards of $20 billion in lost profit due to this fiasco.

Virtual reality headsets like the Oculus Rift and HTC Vive tether to desktop computers with robust GPUs in order to harness their power. The free-roaming, cordless Microsoft HoloLens forgoes those chains but loses a bit of graphical processing power in the mix. However, a recent report suggests we may get the best of both worlds.

Samsung's next Galaxy Note smartphone is expected to contain some nifty new additions that the company hopes will give it the long desired edge it has been seeking over Apple. One of those features that might make the difference? An iris scanner, which could make it the first major smartphone on the market to have that technology included.

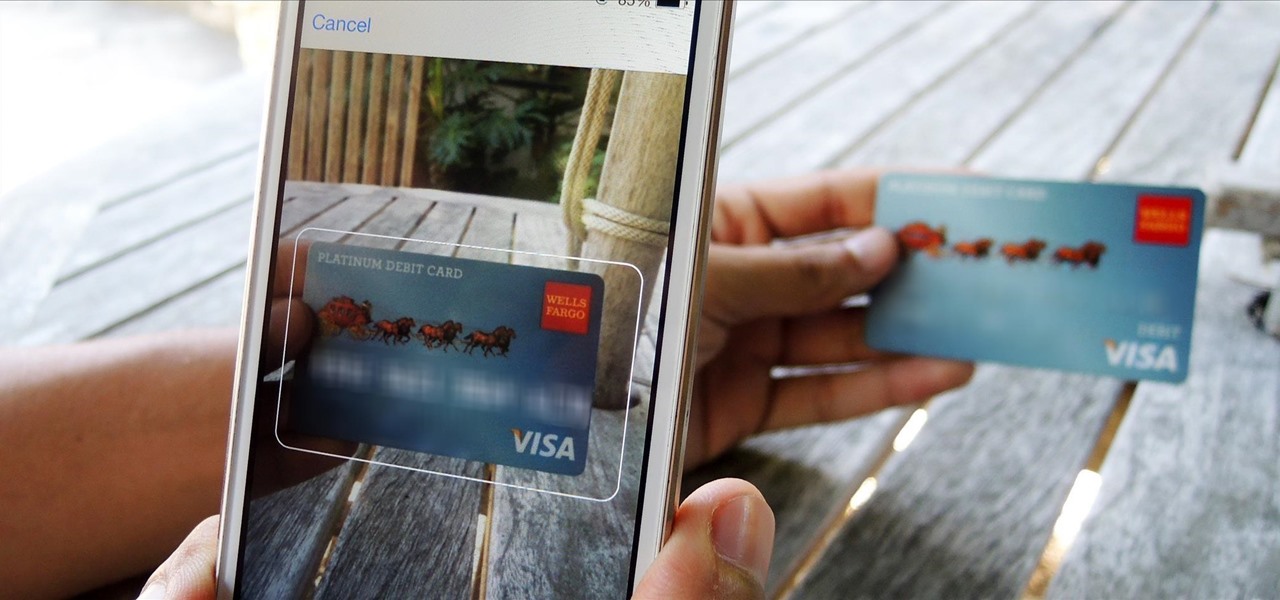
Believe it or not, you can put your money to use very efficiently in a new way: your credit or debit card can serve as a blade in desperate situations. (It might even be handier than dental floss as a brilliant substitution for specialized kitchen tools.) While I wouldn't take bets on it slicing a New York strip steak, there are definitely many other foods it will easily slice through. What Is It Made Of?

In previous posts here, I have pointed out that hackers are in high demand around the world and in nearly every industry. Every military and espionage unit of every country is trying to hire high-quality, experienced hackers as fast as they can to hack their adversaries' computer systems in order to gain a strategic advantage and to spy.

There's a feature that debuted in iOS 7 that lets you to save your credit or debit card information in Safari so that you can auto-fill text boxes when purchasing something online. Unfortunately, you still had to manually fill in your card info the first time, and if you wanted to disable the feature for security concerns, it was entirely useless.

Netflix releases monthly reports on major ISPs relating to how well their service works on each provider. The purpose is to educate the public on their choice of service provider, but since many of us hardly have any choice at all when is comes to an ISP, it backhandedly works to shame them (if they're even capable of feeling shame under all those millions of dollars).

Instagram recently released their new Instagram Direct messaging feature in their Android and iOS apps, which lets users share private photos and videos directly with individuals or groups of up to 15 users. However, there are no restrictions on who you can send private photos or videos to.

In a 10 button Nesquik vending machine or other 10 button vending machines, you can hack to get credited for free drinks.

Security researcher Nadim Kobeissi has discovered that the Windows 8 SmartScreen feature, meant to screen downloads for malicious software, actually reports the data about which applications users are installing to Microsoft. He also says that "the Microsoft server is configured to support SSLv2 which is known to be insecure and susceptible to interception." The two main concerns are the ability of law enforcement to subpoena Microsoft for the information and of hackers to intercept user data...

Video: . » Iran Threatens to Block Tankers in Response to Oil Import Embargo Alex Jones' Infowars: There's a war on for your mind!.

If you want to enter the police station armory in Detroit while playing Deus Ex: Human Revolution, you either need to have enough credits to afford it, or you need a high hacking skill. This video from Game Front will allow you to skip both of those requirements by giving you the password to the armory so you can take all the weapons you want.

Tennis is much more tiring than players of other sports often give it credit for. A match is most often won by the more agile player. If you need to work on your footwork and movement to improve your tennis game, watch this video for drills that will help you do it.