Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

When we talk about driverless technology, the go-to companies are usually Waymo, Uber, or Tesla. However, traditional automakers like Ford and GM are also staking claims to the driverless and advanced driver assistance spaces.

There's now more reasons to make sick workers stay home—a new game theory study suggests adequate hand washing and other illness-aversion tactics aren't as useful as we thought to keep you from getting infected when a virus or bacteria is circulating.

BlackBerry has formally announced the arrival of its flagship, the KeyOne, during Mobile World Congress 2017 in Barcelona. The all-Android KeyOne looks distinctly BlackBerry, with its 4.5" screen and physical QWERTY keyboard. Here's the lowdown on this elegant handset that hearkens back to BlackBerry's heyday, which had previously been known by its code name, the BlackBerry Mercury. Aluminum Unibody with Physical Keyboard

"Necessity, not novelty," is a phrase I use often when it comes to HoloLens development. It would be fair to call it my mantra, or mission statement, as I prototype and explore software creation on this new frontier of mixed reality.

Super Mario Run was released for iOS on December 15, 2016. Even though it debuted as a "free" app, almost all of the playable content was hidden behind a ridiculous $10 unlocking package. Despite coming with such a hefty price tag and receiving a two-star rating on the day of its release for iOS, Android users are still very much interested in giving this game a whirl.

When the "Just another day in the office at Magic Leap" video was released last year, it was called a mind-blowing, stunning, and breathtaking take on mixed reality gaming. It was a great presentation of what the technology could be, but not for a second did I think it was anything other than a concept video, and I'm not the only one who thought that. This was a goal to reach for mixed reality, not the reality.

At an event in Mountain View, CA, and watched by fans via live stream on YouTube, Google announced a slew of new products today. Over the last few weeks, there was no shortage of rumors and leaks about what might be unveiled, but now the secrets are out.

The magic of an ice cold popsicle on a hot summer's day is undeniable, whether you're a child or a kid-at-heart. Neon-colored, store-bought popsicles may have a special place in your memory, but homemade popsicles are pretty hard to beat. Here's how to create delicious frozen treats that will both delight your inner child and tickle your adult taste buds!

The octopus is famous for its bulbous head, enormous eyes, and four pairs of long arms. The stuff of legends and nightmares, octopi have been featured in stories, artwork, and meals galore. But how do you eat this distinctive looking, bilaterally symmetrical sea creature?

This is my first article on here, it's based off of a project that I'm working on at school which is on three ways to bypass windows user password's. If all goes as planned and you all would like I'll work on part two and part three and post them as soon as I can. I do have to give credit to Puppy Monkey Baby and The Defalt, both of whom are my classmates at college and have helped me with writing this article.

Watching the NCAA Men's Division I Basketball Tournament without cable used to be easy. As long as you had an internet connection, CBS and Turner (TBS, TNT, and TruTV), which co-broadcast March Madness, let you watch all 67 games online free of charge.

On the list of problems with Android, manufacturer tinkering ranks near the top. Slow or nonexistent updates, poor performance, excessive bloatware apps—all of these things can be attributed to manufacturer skins like TouchWiz or Sense, and none of them are issues with unmodified, Vanilla Android devices like the Nexus series.

Even though the 88th Academy Awards have come and gone, there's a good chance you still haven't seen all the films that were nominated—or even those that won big.

First of all, I would like to apologize for a week long absents for the tutorials of this newly series, Raspberry Pi. But obviously I'm back and I present all you guys a article on turning your Raspberry Pi into a hacking platform. I'm gonna use the platform Kali Linux for the Raspberry Pi. I should note that I'm not gonna go into detail on how to install Kali Linux since OTW already has done a tutorial on how to turn your Raspberry Pi into a Hacking Pi. The point of this particular tutorial ...

If you read my previous post, "How to Hack into a Mac Without the Password", you know that it is very easy to break into someone's Mac if you have physical access to the computer. Now the question that lies is, how do we protect ourselves from this happening to us? Well, here is a way that guarantees that no one will be able to change your password through OS X Recovery.

Chicken breasts have gotten a bad rap. Dry, flavorless, boring... poor white meat gets no love, and dark meat gets all of the credit for being sinfully flavorful and delicious. But the truth is, even though chicken breasts are lower in fat and calories, they can also be incredibly versatile and full of flavor... if they're prepared correctly. You're probably familiar with poaching, which is a technique that gently cooks more delicate meats such as chicken or fish fully submerged in a liquid b...

I'm back. School's an ass. On my quest for knowledge, which started approximately 3 years ago, I can upon an interesting little artifact. It is called the Arduino.

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - at my blog, here - https://techkernel.org/2015/12/11/embed-metasploit-payload-in-apk-easily/

I think it was 1986 when I first discovered my love for making computers say stupid things out loud. My older brother got a Commodore 64 for his birthday, which came bundled with software that would speak out any term you typed in—and boy, that computer sure made a fool of itself after my five-year-old imagination got a hold of the keyboard.

Android has a brand new mobile payments system, and it's rolling out to most devices as we speak. Android Pay, as it's called, will replace the existing Google Wallet app as an update, and it brings some awesome new functionality such as tokenization and the ability to tap-and-pay by simply unlocking your phone.

Like a strong-tasting cup of joe, but want more caffeine out of it? Start double brewing your coffee. To paraphrase a big fan of the double brew process on Reddit, it'll make you feel like you can throw an orange at 60 percent the speed of light. It's that strong. Really.

Google now has an iOS version of Android Wear, so if you own an Android smartwatch (Moto 360, ASUS ZenWatch, Huawei Watch, LG Watch Urbane, Sony SmartWatch, etc.), you can finally connect it with your iPhone.

Newer gaming systems like the PlayStation 4 have a nice, subtle feature that goes a long way towards helping create a more immersive experience. Any time you're on the main menu or home screen, an ambient background music track is playing, which adds an aural appeal to an experience that would otherwise be all about the visuals.

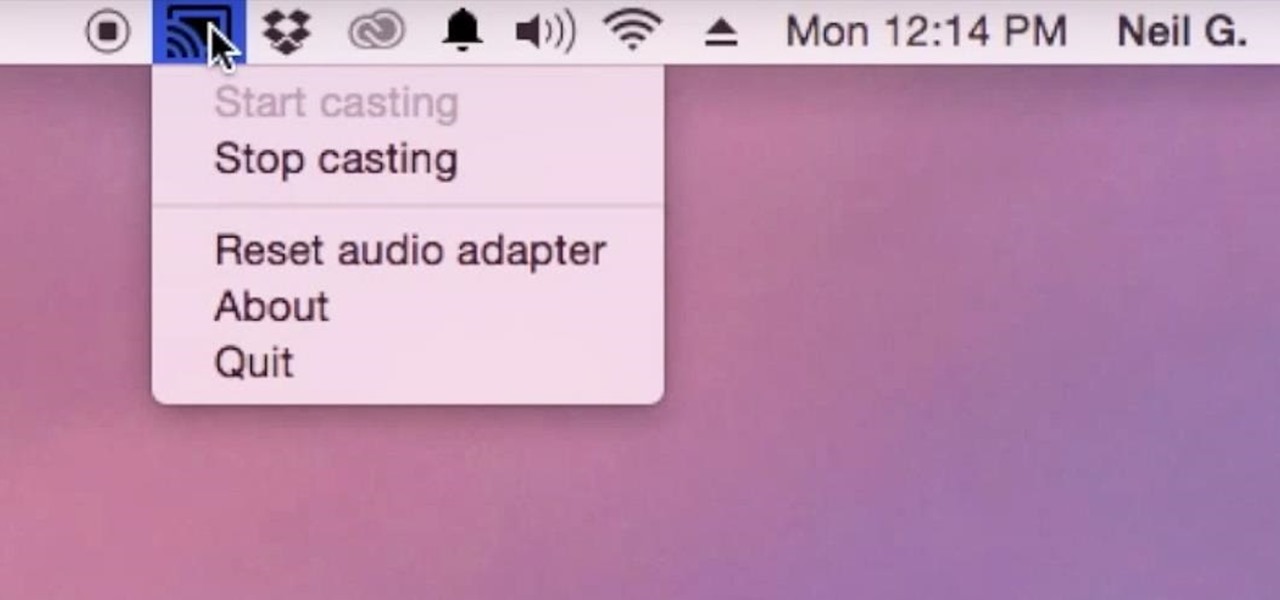
Although I know it will never happen due to Apple and Google's tempestuous relationship, I sometimes wish I could cast iTunes or Apple Music from my Mac to Google's Chromecast. When you don't have speakers to blast your music, the television is a great alternative to amplify your music.

To be twentysomething is an awkward time for entertaining. As we graduate college and begin to work in “the real world,” there is a yearning to transition from keg parties into dinner soirées. However, though the desire is there, often the bank account is not. Here are some ways to do in the kitchen what twentysomethings do best: fake it until you make it. (In other words, host a fabulous dinner party for four and still be able to make rent this month!)

With the amount of time we spend glued to our smartphones, they could be considered a second job (if only we got paid). I spend a large part of my day scrolling through Reddit, Facebook, Instagram, and countless other apps, and burn through hours and hours without even noticing.

The Galaxy S6 might just be the best Android phone on the market right now. From a hardware standpoint, Samsung truly knocked this one out of the park with its finely-crafted build quality and amazing screen.

After several weeks of testing out the public beta, Apple has finally released iOS 8.3 to the general public. The latest iteration of iOS for iPad, iPhone, and iPod touch serves mostly as an update to fix many of the bugs that plagued earlier versions, but there are still a couple of awesome new features included in the new build.

While honey is one of the most popular ingredients on kitchen shelves the world over, honeybee pollen is still a relatively rare find in most households. It's not hard to guess why: eating pollen just sounds weird... it would probably sell a lot better if it had a more appetizing name, like honey. Furthermore, it looks unlike any other common ingredient, and the smell can be off-putting to some. But it's good, it's healthy, and it's altogether pretty awesome!

If you are anything like me, you have a knack for taking silly selfies of yourself, i.e., taking scotch tape and wrapping it around your face to make yourself look like the blob, or perhaps you like taking selfies of yourself in weird or unusual situations doing weird and unusual things.

The only mail I like getting comes in the form of an Amazon package, but when I go to my mailbox, it always ends up being a pile of credit card offers and catalogs I could never see myself ordering from. Those pieces of junk mail usually end up in the trash, which is horrible when you think about all the trees that had to get cut down in order to produce them.

Shopping: you either love it or hate it. With a tight budget, shopping can become a huge headache for even the biggest shopaholic. We've all been there, and we've all given in to our impulses and bought something we probably shouldn't have. Yet strolling through the mall doesn't have to require a strong will to keep your credit card from entering a downward spiral. You just need to keep your hands to yourself.

Most of you already know that a zero-day exploit is an exploit that has not yet been revealed to the software vendor or the public. As a result, the vulnerability that enables the exploit hasn't been patched. This means that someone with a zero-day exploit can hack into any system that has that particular configuration or software, giving them free reign to steal information, identities, credit card info, and spy on victims.

First, I want to give credit to the author where I first found how to do this: Astr0baby's Blog. This article was dated, so I took the script on his page and reworked it to make it work today. (I also included the way to make it hide the cmd line popup.) Requirements

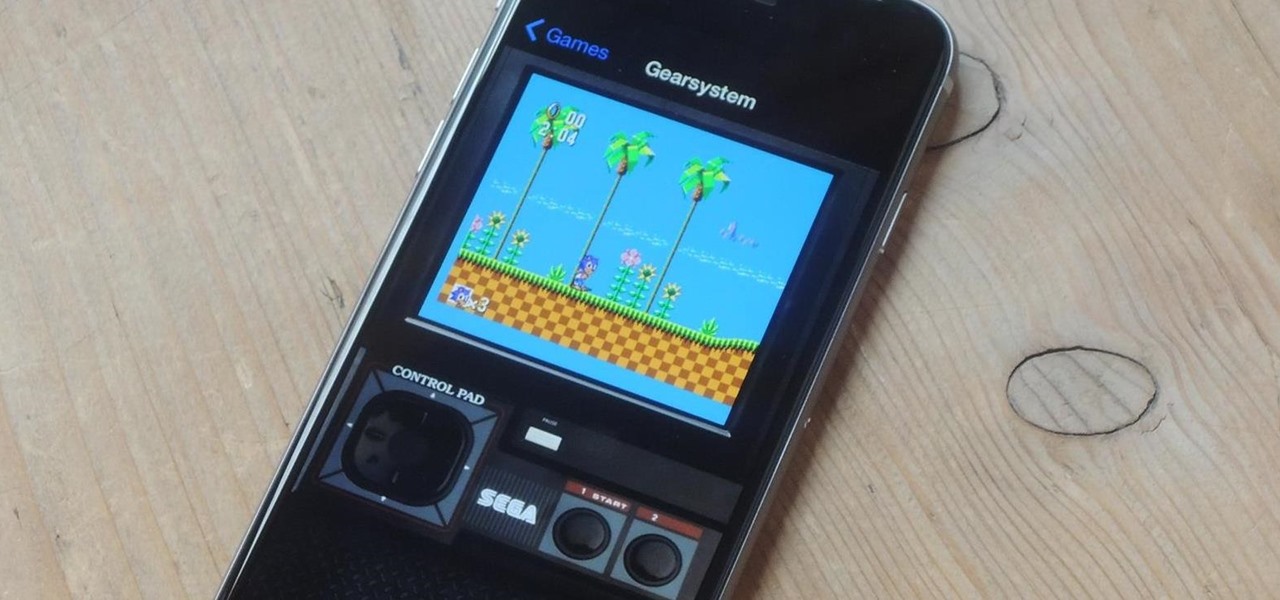
The Master System, more popularly referred to as the Sega Master System, or SMS for short, is a video game console that was released in the mid-1980's as a direct competitor to the original Nintendo (NES).

Keeping data private is vital in the days of smartphones and the free-floating information they carry. Justin wrote a guide on many of the deeply hidden and sometimes concerning privacy settings in iOS 7. Now we're back to cover some of the new (and old) privacy settings in iOS 8 that you need to address right now.

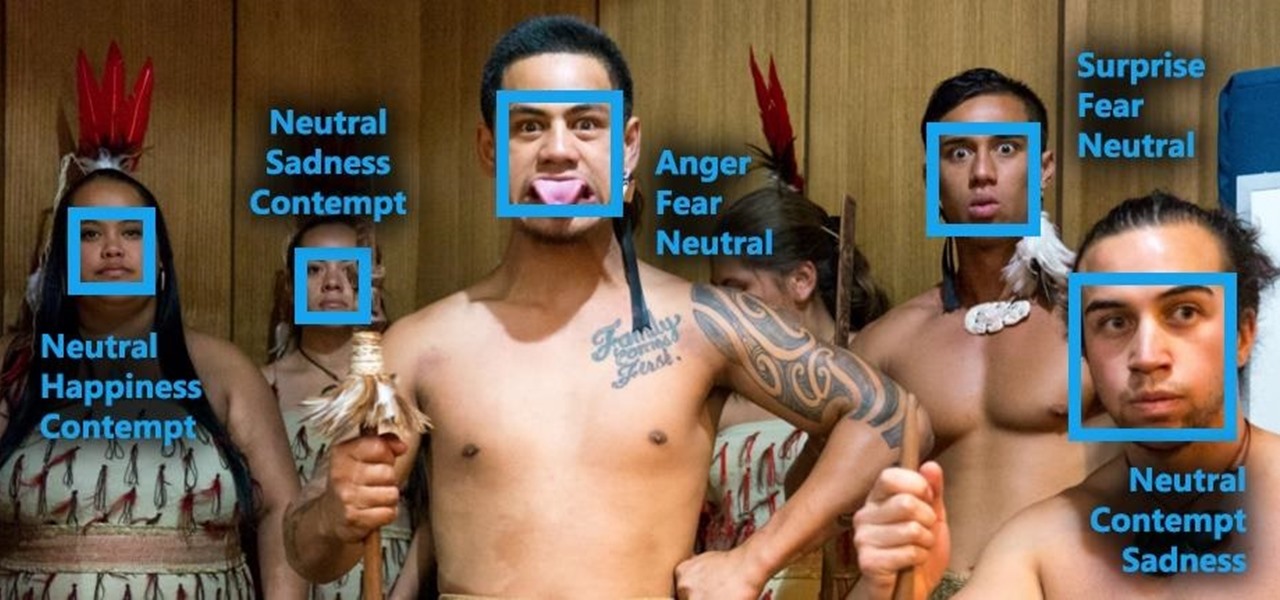
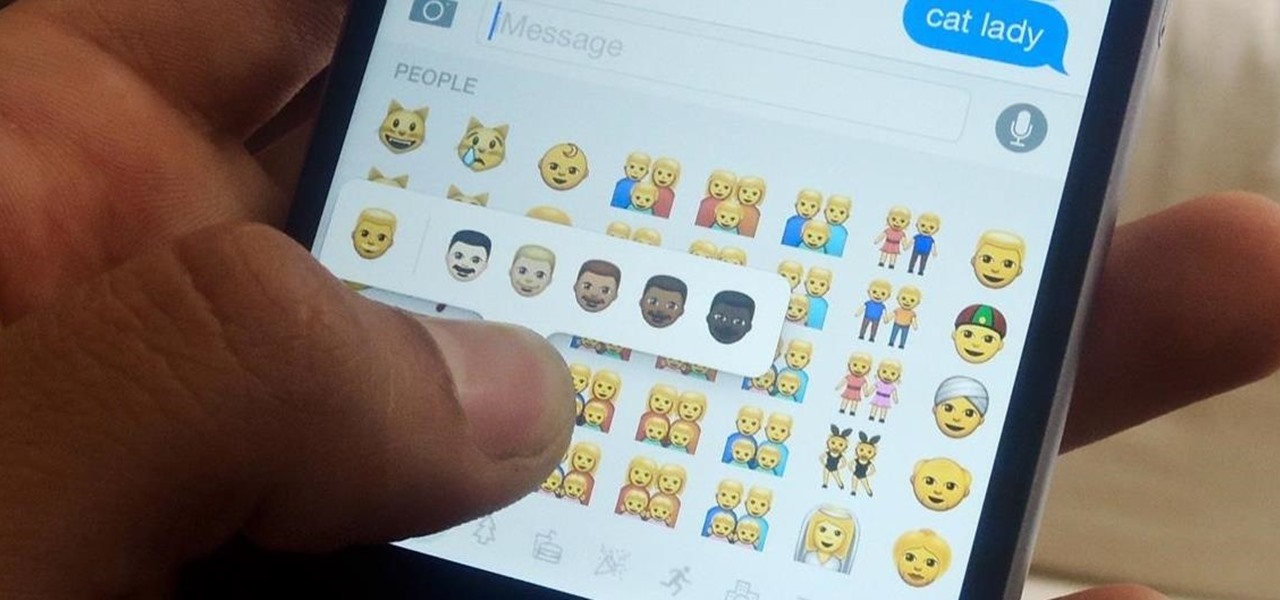
Better sleep, smartphone news, and changes to your favorite forms of entertainment. There's been a lot going on over the last couple of weeks in the world of tech, and we thought we'd show you all of the need-to-know products, updates, and ideas that we think are most important.

Yes, I know. Nexus owners aren't exactly the biggest Apple fans out there. That "Pure Android" experience was one of the main reasons we bought our Nexus devices. But give the other side some credit—the iPhone's operating system has come along way, and is still the champ when it comes to aesthetic design (at least until Material Design dethrones it this fall).