
TypoGuy Explaining Anonymity: Secure Browsing Habits
to stay secure, you dont just need Tor, and a VPN. You need good browsing habits. What are Browsing Habits You Ask?


to stay secure, you dont just need Tor, and a VPN. You need good browsing habits. What are Browsing Habits You Ask?

When it comes to security, there are usually only a handful of things that you want protected from prying eyes on your iPhone—private photos, scandalous videos, and important text, such as credit card and social security numbers.

Welcome back, my rookie hackers! In my ongoing attempts to familiarize aspiring hackers with Linux (nearly all hacking is done with Linux, and here's why every hacker should know and use it), I want to address a rather obscure, but powerful process. There is one super process that is called inetd or xinetd or rlinetd. I know, I know... that's confusing, but bear with me.

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.
The internet is forever. When you put something out there, it can easily be re-shared, floating from server to server indefinitely with no way of taking it back. It's a scary thought when you consider that a young adult's grandchildren will one day have access to their drunken party pics.

This is a extremely easy to follow tutorial which will allow you to learn to how to build a sugar cane farm.

With all of the personal data that's stored on our smartphones, it's of vital importance that we have some sort of lock screen security enabled. One of the Galaxy S5's killer features is obviously the fingerprint scanner. It makes the process of dealing with a secure lock screen a bit easier than typing in a password or PIN.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.

Ever since the FBI took down the Silk Road and Dread Pirate Roberts last month, many questions have been raised about whether Tor still provides anonymity or not, and if it's now broken. I'll try to address that question here today succinctly from multiple angles, keeping it as simple and plain-language as possible. The Closing of Silk Road

Today's project will show how you can convert your laptop, smartphone, or tablet computer into a makeshift projector—just in time for March Madness! It's super cheap to build, and can add a little bit of creative fun to your next sports party.

Creative Commons is awesome—really. If an image, video, or audio file is tagged with a CC license, that means you can use it as long as you give appropriate credit to the owner. For bloggers with no money for pricey stock media, it's a godsend. When you license your own media under CC, you can choose how you want it to be used by others and whether or not it can be used commercially.

This video will show you how to disable secure virtual memory in Mac OS X. From the top left of your screen click on the apple icon. Click on system preferences from the pull down menu. Click on the security icon. Click on the image of the closed lock from the bottom left of the window so that you can change make changes.

Now we'll learn how to secure PDFs so that we can safely send them out to clients for review and be assured that they can only access the content the way we want them to. Turn off things like printing and content extraction. Password protect your PDFs so that they can't even be opened without a password.

This is a tutorial on how to secure your wireless network. This tutorial shows you how to setup a WEP encryption key for your wireless network.
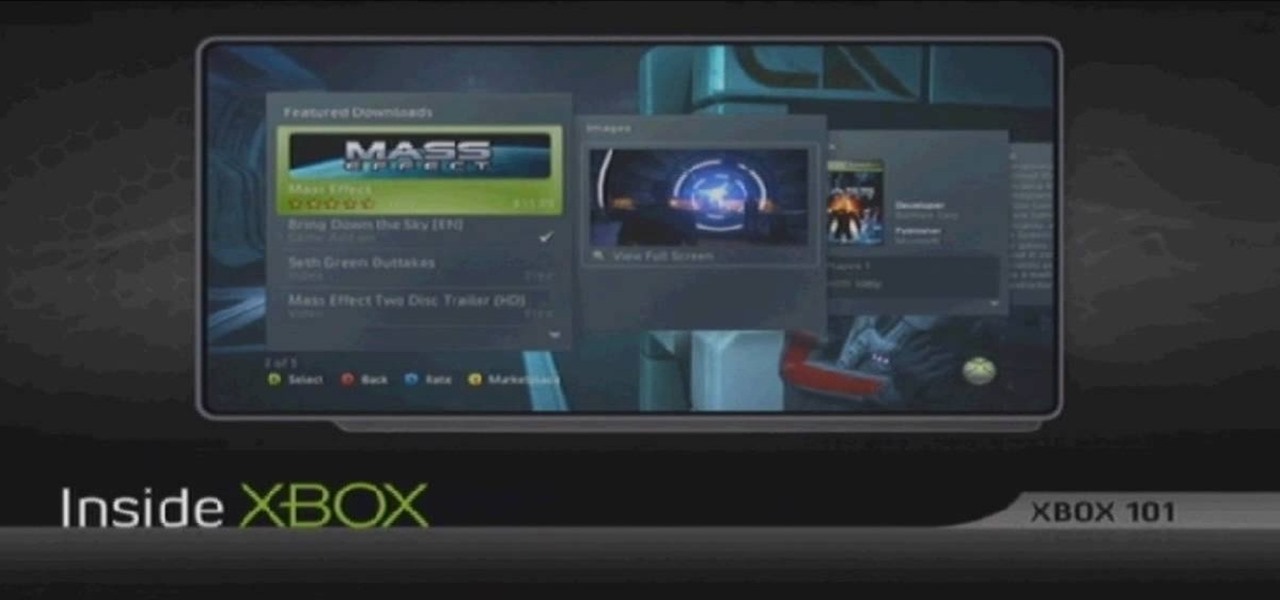
In this tutorial, we learn how to get Games on Demand on Xbox LIVE (Xbox 101). You will find all the newest games as well as classics and downloading is easy. It's the same process as downloading the demos. Just head to the marketplace and select from the title choice. You have the option to charge the title to your credit card or using points to purchase it. Each game is several gigabytes in size, so give it lots of time to download. To familiarize yourself with games, go to the website for ...
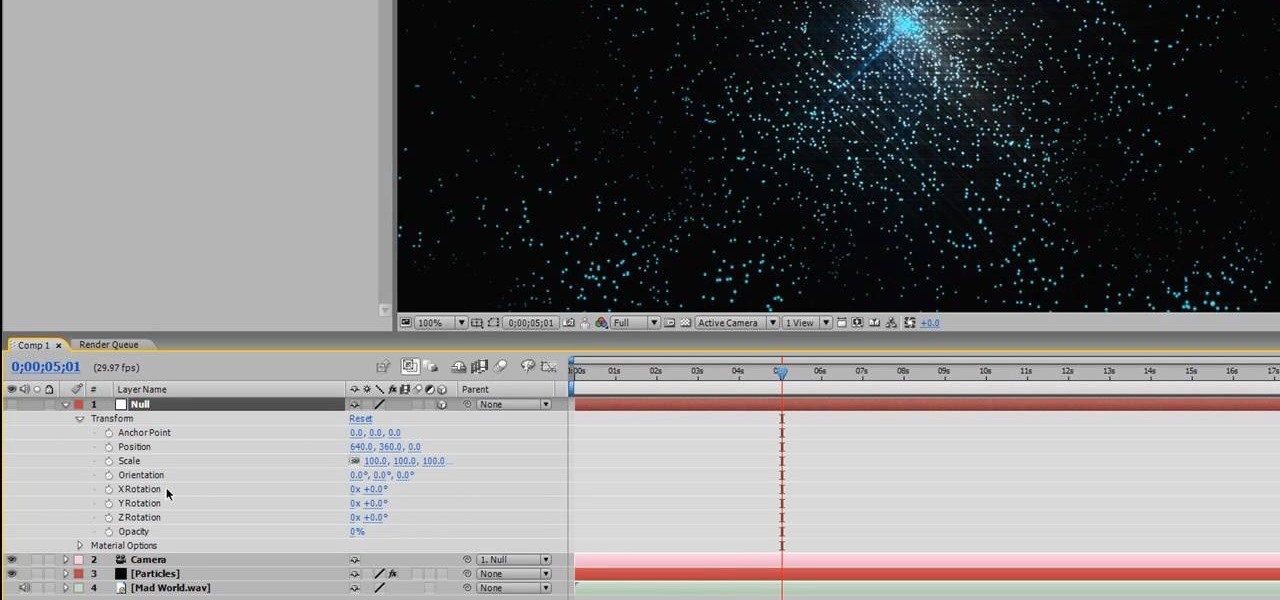
Very few effects can be considered standard in After Effects, many are unique creations made by combining After Effects many tools. This video will show you how to create one such effect, an audio particle spray that will looks very cool in either titles or ending credits for a film. It is pretty easy to make and looks very, very cool.

This video provides detailed instructions on how to hack into the game credits of 'Shopping Cart Hero 2'. The first step in this process is to complete the first level of the game in order to gain in-game funds. The instructor then shows how to use a cheat engine when buying an item in-game to change values within the game to whatever you choose allowing the player to have unlimited funds and buy everything they want within the game. This means that the shopping cart can easily receive every ...

Don't have the cash to spend on a brand new leather wallet? Why not make one out of duct tape? All you need is a pair of scissors and a roll of duct tape (specifically the "thinner" "cheaper" kind, as DuctTapeStuff explains makes for an easy-folding wallet). By following these easy folding instructions, you'll have yourself your very own unique duct tape wallet complete with bill fold, credit card slots, coin pouch and more.

This tutorial will show you how I created my own original Terminator costume from scratch and a modest budget. All the materials used are easy to find items sold at your local Hallowe'en or theatrical costume store.

Rubber bands are an ordinary, everyday, common household item, right? Their hidden in your desk, wrapped around your bills, holding your pencils together at the office, but what else can you do with rubber bands? What are some extraordinary uses? Woman's Day Magazine tells you how you can repurpose those rubber bands!

In this tutorial, we learn how to wear a full formal kilt outfit with accessories. You will need: socks, garters, shoes, kilt, sporran, kilt pin, jacket, vest, and knife. First, put your socks on, then wear the garter around the sock, folding the top of the sock over the top of the garter. After this, put your shoes on, by lacing them up to the top of the socks. Next, open your kilt and wrap it around your wait. The strap should go through the buckle, then through the hole in the strap. Secur...
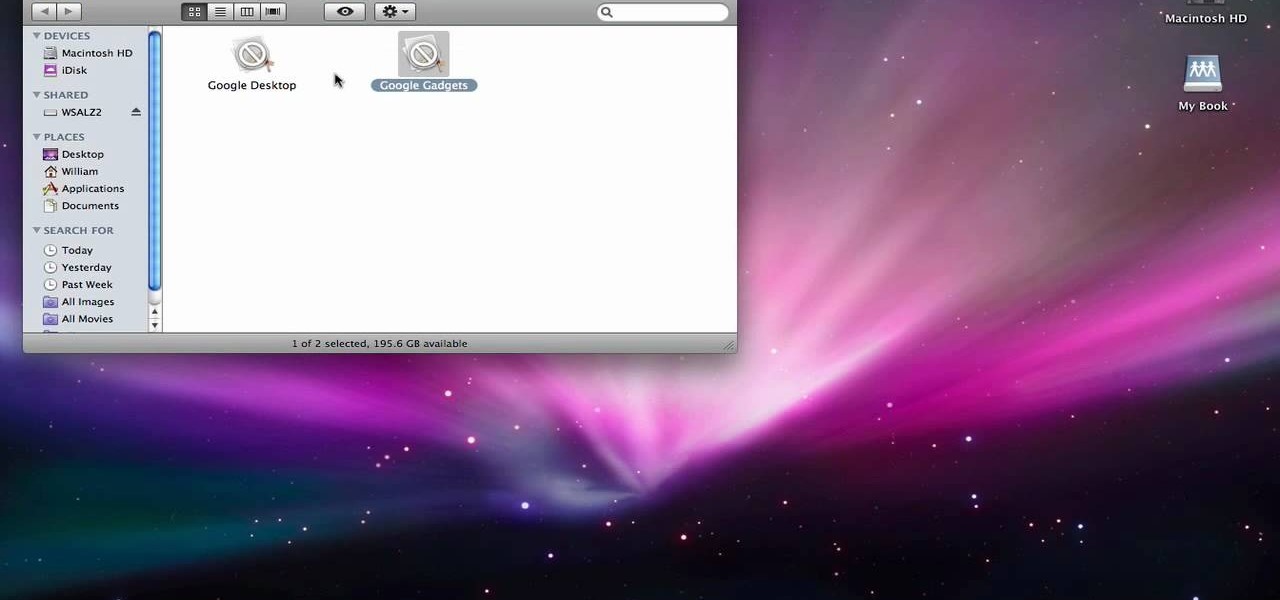
In order to completely delete items from Mac OS X. Download Google desktop. This will search your computer and the web and your computer. Go to Applications. Right click on Google Desktop. Go to Show Package Contents. Drag contents into the trash. Next, go to Google Gadgets. Click and drag it to the trash as well.

Learn how to put up a tarp for shade and protection from the rain in this video. First, find two trees with a nice flat spot in between them. Throw a rope up over a limb at least fifteen feet or so high. Now, tie the rope off to itself or to a smaller limb. Next, secure the rope on the other tree and leave the slack on the ground. Next, put the tarp over the rope evenly and anchor one end with a wire tie, small rope or bungee. Now you hoist the tarp up using one end of the rope and pull it to...

This video shows how to style your hair based on the Final Fantasy video game character Yuna. First you will need to spray your hair with a root gel spray, which is a spray that gives your hair texture. Then blow-dry your hair upside down.

Leah for May Arts Ribbon shows how to make a flower loop bow. The following items are needed for it: Needle and thread, scissors, May Art Ribbons and a ruler. Buttons or flowers may also be needed to put on top of your bow as per your selection.

You'll need five baked eight inch square cakes, five - seven cups of white icing, five sugar cones, a little glitter, a little bit of pink icing, a pastry bag, silver non parils, gummy balls, candies, pink and red icing, mini canned hearts, red sprinkles, colored paper and tape and 5 toothpicks. Cut one cake into fourths and stack them one by one on top of a stack of the other four cakes, secured by white icing. Poke a hole in the tops of each of the cones, then sprinkle each one with edible ...

This is a video on how to weave in ends on kniting. First take two ends at a time, tie the new color and a half not around the current working color, and tie them. The thread the end onto the yarn needle, and go througha few of the yarn stitches. Next give it a little pull to make sure nothings coming loose. Go up to the next yarn ends, and do the same thing. What you have to make sure you do is weave the yarn through light colors. Also make sure the knots are secure, and are not going to com...
In order to make a Silicone Ring Mold you should first get a small plastic container. This will be your mold box. First, you should cut the bottom out of the container. Next, use double sided tape to stick the ring down to the base of this. Next, secure the mold walls to the base. Now, mix the silicone mix in a separate mixing cup. Make sure you mix this thoroughly until the color is uniform. Now pour the silicone into the mold in a fine stream on the side of the ring, this will help prevent ...

How to make a great green apple martini. First we start with the tools of the trade, you will need a glass, champagne or martini glass will do, next a set of tumblers, a speed pour-er, and a martini strainer. Now that all of those are laid out we need to chill the glass down, so take the larger tumbler and fill it 3/4 full of ice. Add the ice to the glass and set aside. While the glass is chilling out, we need to get our liquor out and ready to mix, these are the liquors needed:

In this how-to video, you will learn how to make a small jug with a handle using a wheel. Place the clay onto the wheel and start spinning it. Grasp it with your hands as it spins and make a vertical shape. Use your thumbs to make the interior bowl shape. Now, use your hands to make the clay more vertical. Keep doing this until you get the desired height. Now, insert your hand into the interior to widen the shape. Make the top more narrow with your fingers. Make the edge stick out as well wit...

This video demonstrates how to create an origami ninja star. Prepare a square shaped piece of paper. Lay it down on a table or on a flat surface. Fold the paper right across the middle in a vertical orientation. Fold it once more in the same manner as the first fold, now creating a more slender vertically standing rectangle. Fold the upper portion of the origami diagonally forming a small triangle on top of the rectangle. Do the same on the bottom portion of the origami. Fold the upper portio...

This video demonstrates how to make a balloon light saber. For this project, you will need the following: long balloons.

Learn how to ‘Paint onto your T-Shirt’ by watching this video. Materials required for this include the following:•Marabu Textil Plus Start Kit – 6 colors included with paint brush•Marabu Metallic Outliner Paints•Crocodile clips•Masking tape•Pencil•Design printed from the computer•Tracing paper•A large cardboard wrapped in cling film•A dark colored T- ShirtBegin by placing a tracing paper over the design and secure it to the table using masking tape. Next, use a pencil to trace the design on t...

For the fairy sized princess tiara you will need 32 gauge silver wire, silver ball beads, seed beads (your choice of color) and 4 mm crystal beads. Start with about 6" of the wire. String a seed bead to the center of the wire- and twist one or two times to secure it in place. Then bring both ends of the wire together- and clip so that they are even. Next string a 4 mm crystal bead over both pieces of wire and press snugly next to the first seed bead already strung. Then add a silver ball bead...

Whatever your reasons for doing it, if you are trying to hack passwords, it helps to have the right software for getting the job done. With the Cain and Abel program, you will be well on your way to hacking even the toughest personal passwords.

This video presents how to connect to your iPod Touch or iPhone using SSH (Secure Shell) without using Wi-Fi connection.

To install the new toilet you will need a putty knife, hacksaw, tape measure, adjustable wrench, level, sponge, and replacement wax seal. Before you begin removing the old toilet, turn off and disconnect the water supply to the toilet. Then flush the toilet to get the water out of it. Use a sponge to remove any remaining water in the bowl or tank.

This wrap is intended to support and stabilize the ankle joint. Supplies needed include a 1 - ½'' – 2'' adhesive tape, pre-wrap, and heel and lace pads. Apply heel and lace pads at high friction areas, including the distal aspect of the Achilles tendon, and the dorsal aspect of the ankle joint. Apply under-wrap to secure them in place. It is critical that the foot remains at a ninety degree angle for this portion of the procedure. Apply an adhesive tape anchor strip at the lower leg, approxim...

In this video you learn to make a PVC rocket that can travel hundreds of meters high. You start off by cutting your PVC pipe 62 mm long. Next dilute some kitty litter in a bowl to make it damp to compress. This makes a plug. Plug the pipe with 1 cm of liter. Then you add the rocket fuel. Be careful not to mix! Compress until it is time to plug the other end with kitty litter. Next you drill a hole in the center of the pipe with a 5mm bit. Tape the pipe to a stick about 40 cm long. You then cu...

Richpin demonstrates how to remove the inner tie rod end on an automobile. First, get the car up in the air and support it by jack stands. Remove the wheel assembly.