Amazon Web Services is calling up an age-old tactic of the tech industry — the hackathon — to drum up excitement and encourage the development of apps built on the Amazon Sumerian AR/VR platform.

Attention all Redditors: Between June 14 and June 18, Reddit experienced a data breach. The popular website claims it discovered the breach on June 19 and has since made the necessary moves to contain and eliminate the threat. Unfortunately, there isn't much they can do about the data was that accessed and stolen — your user data.

Project Fi, Google's MVNO, is running a new promotion on the latest and greatest from LG. From July 16 until the 29th, whenever you order and activate the LG G7 ThinQ or LG V35 ThinQ, you will receive a $300 service credit. When you do the numbers, that equals a minimum of three free months of service.

While privacy and security are cornerstones of Apple's ecosystem, your iPhone isn't bulletproof. Creating a strong passcode will protect you from most threats, but there exist tools that can break through even the toughest passcodes via the Lightning port. Luckily, Apple has implemented a new security feature to disable your Lightning port and keep your data safe and secure.
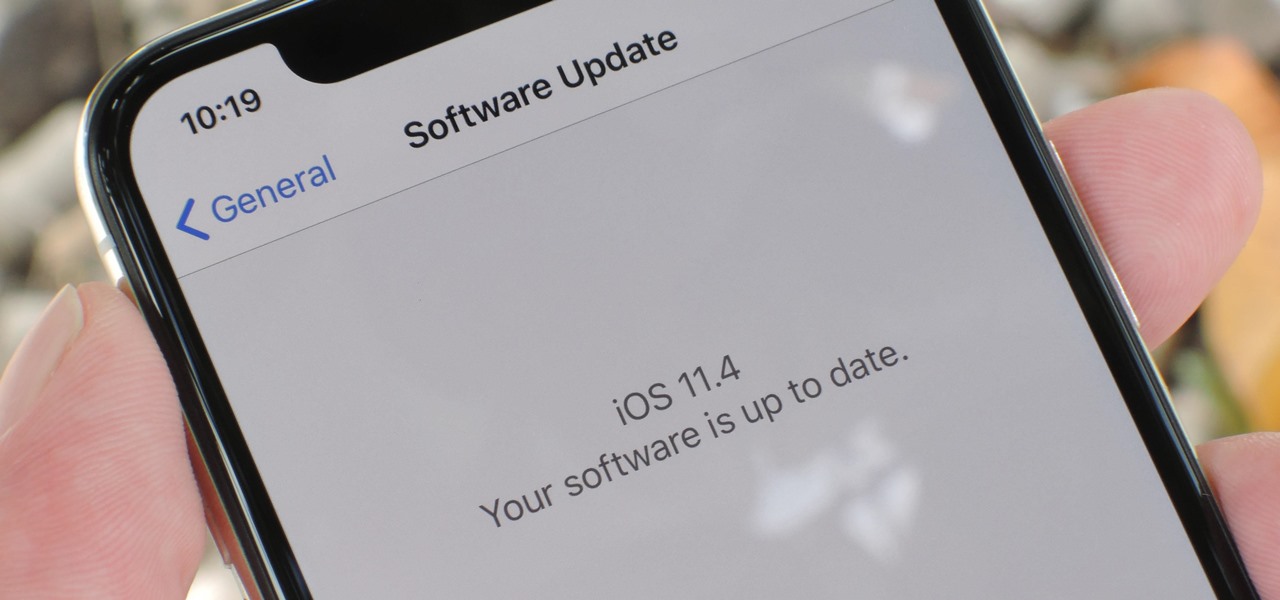
Talk about rapid-fire. Apple released the sixth beta for iOS 11.4 on Thursday, May 17. The update comes just three days after the release of iOS 11.4 beta 5, indicating that Apple is readily approaching the official release of the software. Apple has not issued an official iOS update since 11.3.1, which found its way to users over three weeks ago.
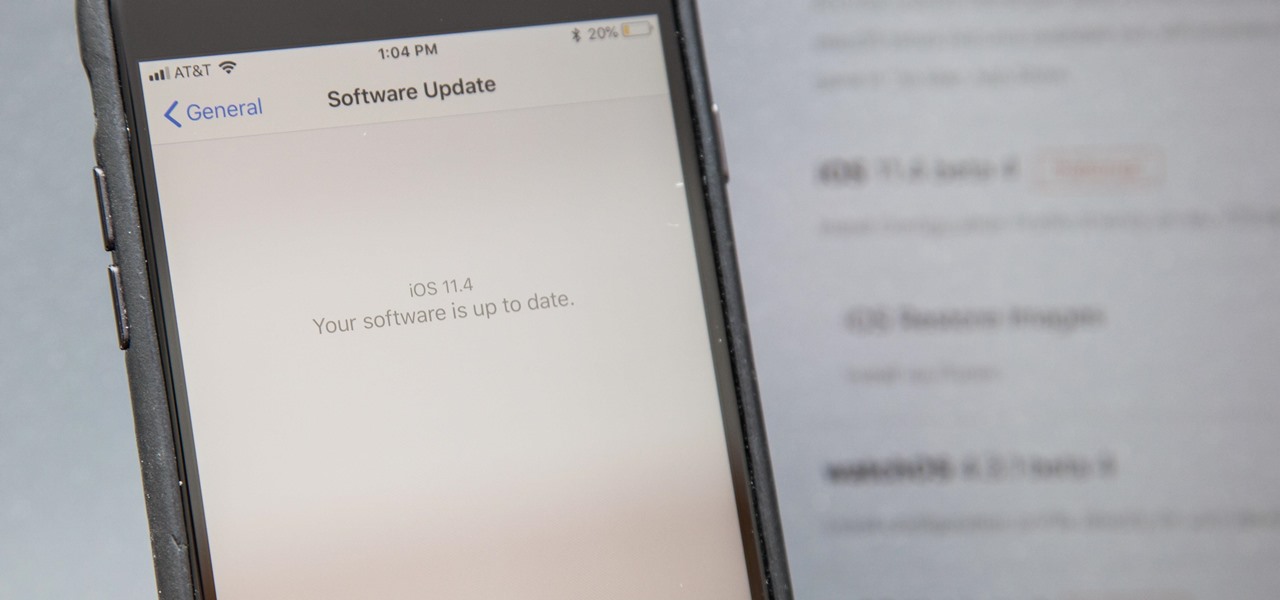
Apple released the fourth developer beta for iOS 11.4 on Monday, May 7, followed the next day with the public beta release. This update arrives just six days after the company seeded beta 3 to users, which fixed an 11.3 issue with 3D Touch, among other various bugs.

With April coming to a close, there's a fresh group of augmented reality Snapchat lenses you should try out while they're still hot. We've got a prank lens, gamer-oriented ones for Fortnite and Fallout, and ones for the memesters out there.

Apple has introduced a special edition iPhone 8 and 8 Plus to bring attention to the ongoing worldwide battle against AIDS. As the second iPhones to carry the (PRODUCT)RED name, these rare iPhones may quickly sell out when preorders open up on Tuesday, April 10, at 5:30 a.m. (PDT), so we'll go over some tips to help you secure a red iPhone before it's gone.

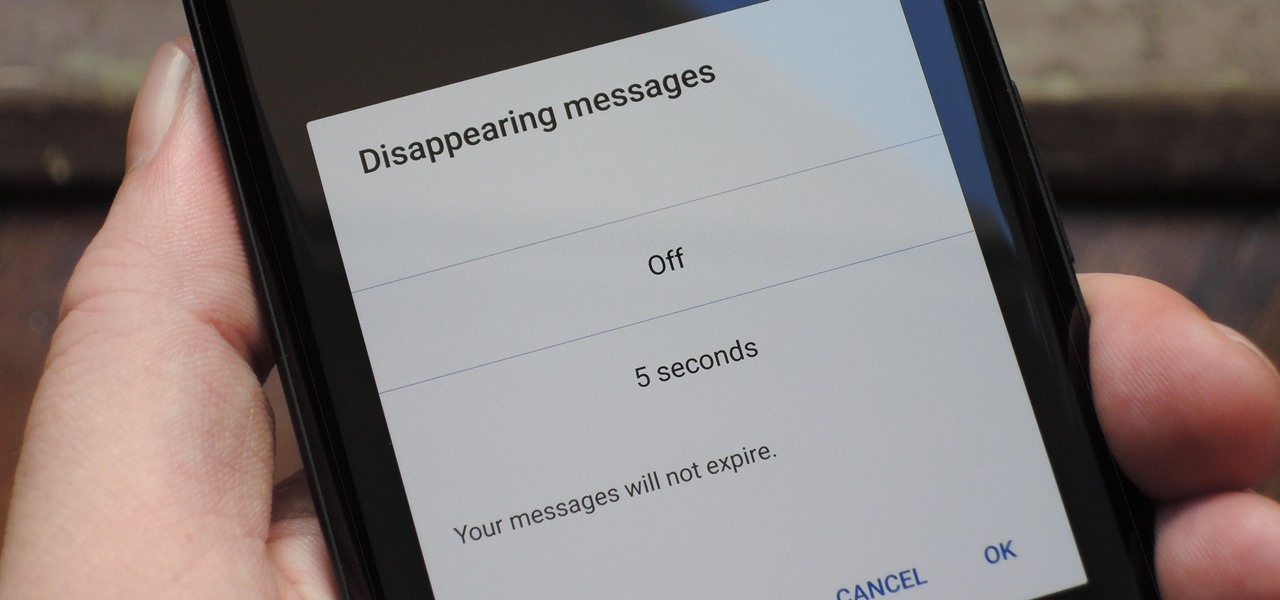
With Signal's class-leading end-to-end encryption, you can be sure your messages will remain secure as they travel to the recipient. However, once the message arrives, its privacy is completely dependent on the receiver, who could share it anywhere if they wanted. To patch this vulnerability, Signal added disappearing messaging.

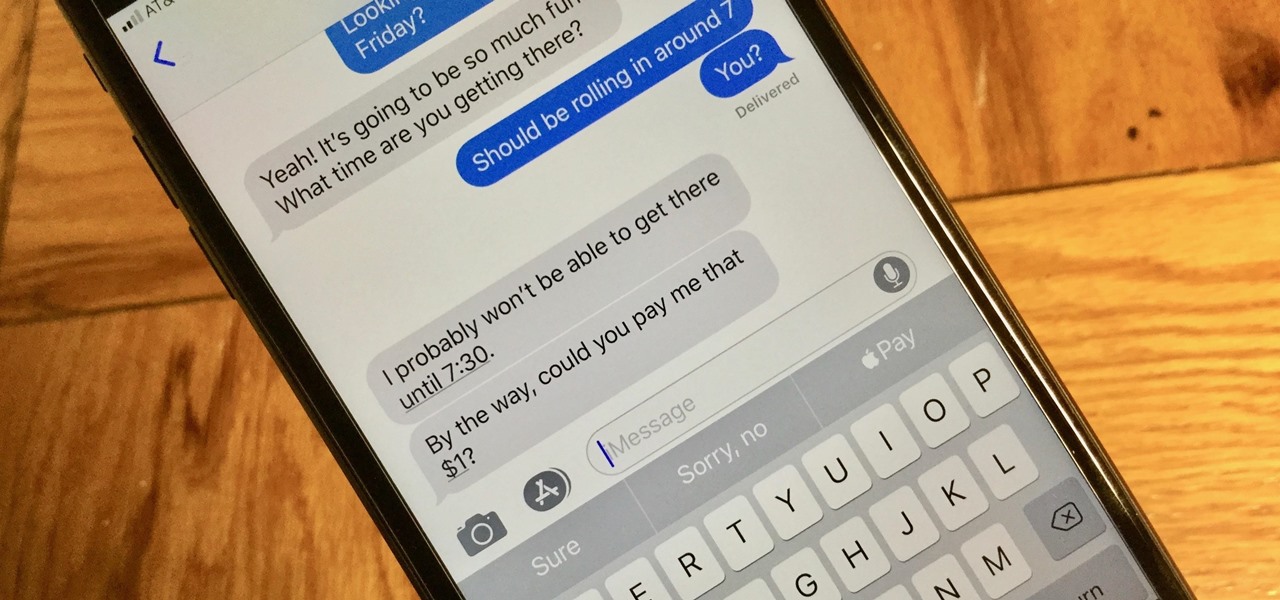
With Apple Pay Cash, you can easily and securely pay your contacts directly in your iPhone's Messages app. While you can always use the normal method of paying someone with Apple Pay Cash, there's actually a faster way, as long as your contact asks you for money in an iMessage.

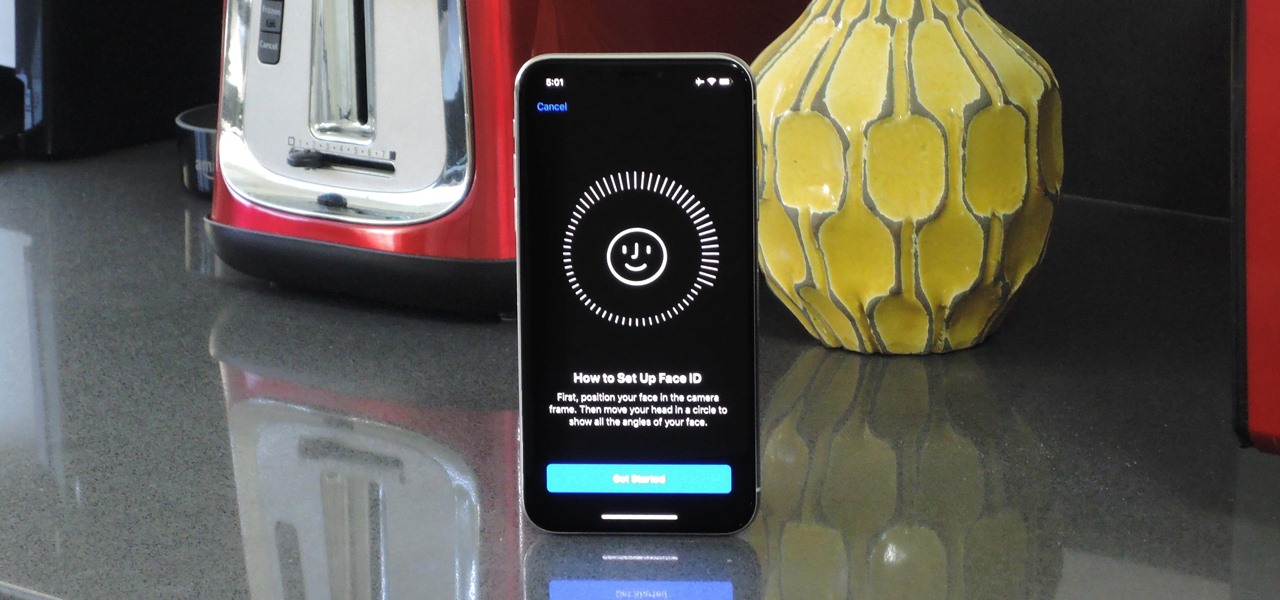
The cutting-edge iPhone X, XS, XS Max, and XR have one-upped their Android competitors when it comes to facial recognition. Apple packed these flagships with an array of front-facing sensors to complement its selfie camera, which allows the new device to more accurately analyze faces, which you need for Face ID, Touch ID's replacement.

As more companies begin adopting augmented reality in the workplace, providers like Vuzix reap the benefits.

Toyota is testing blockchain and distributed ledger technology (BC/DL) for data sharing for driverless cars and other applications. This could eventually reassure buyers of its upcoming high-end cars by making sure their sensitive data is secure.

This week in Market Reality, we see two companies capitalizing on technologies that contribute to augmented reality platforms. In addition, industry mainstays Vuzix and DAQRI have business news of their own to report.

The Pixel is now rumored to be the next phone up in line to be getting a curved display. ET News just reported that Google is in talks to invest $875 million (KRW 1 trillion) in LG Display to give their next-generation Pixel 2 smartphone some curves around the edges.

The ride-sharing company Lyft has managed to secure $500 million in funding, which will certainly help its ongoing competition with Uber. According to recent reports, the cab firm is currently valued somewhere between $6.9 billion and $7.5 billion, but this still pales in comparison to Uber's estimated $70 billion valuation.

Upskill, an enterprise software developer for industrial augmented reality applications, recently received an influx of funding and a major vote of confidence from two of their top customers.

No one is safe anymore, it seems. Google's Project Zero has just uncovered how easy it is for attackers to target your phone's Wi-Fi chip, which is essentially a mini processor for Wi-Fi that detects and processes networks.

You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication between your browser and a website are unencrypted, which means it can be eavesdropped on.

Starting with version 6.0 Marshmallow, Android now supports fingerprint scanners natively. This change has effectively opened the floodgates, and now almost every flagship Android device includes a fingerprint scanner out of the box.

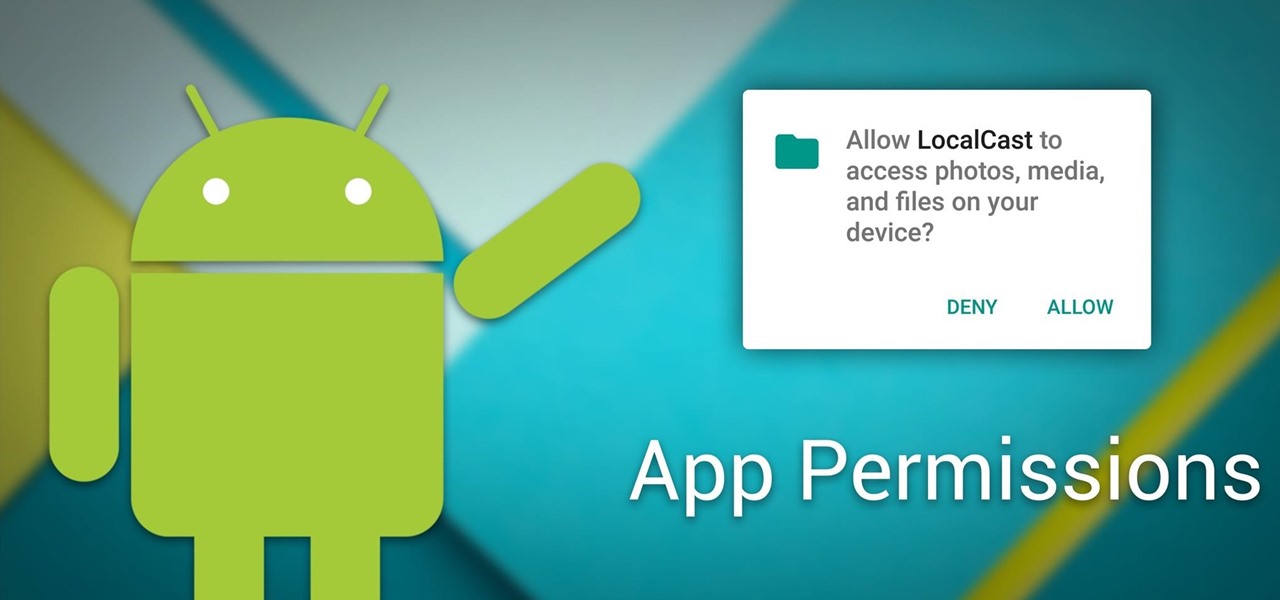
Android 6.0 Marshmallow added a new permissions system that can make your digital life much more secure. Unlike previous versions, apps now have to ask for your consent before they can access certain data, which puts you firmly in the driver's seat.

If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a problem—how exactly are we supposed to remember all of these complicated passwords?

School internet filters serve a valid purpose—they keep students from wandering off into the deep corners of the web while still allowing at least some internet access. But a lot of these restrictions are completely ridiculous, to the point where some school districts block access to the educational material in National Geographic or forbid searching terms like "China," "Iran," or "Russia"—because, you know, breasts and commies.

Kim Kardashian and Kanye West have fittingly named their second child "Saint," but I'm sure you don't care about that—and neither do I. Unfortunately, regardless of our pop culture interests, we're forced to know these types of stupid facts because the internet is so densely populated with Kardashian-related content that it's impossible to avoid. It's enough to make you puke.

Want the next level security? Well then take a read here because this is some next level stuff. Heard of It?

Roughly four years ago, Adobe decided to abandon development of the mobile version of their popular Flash Player browser plugin. Their excuse at the time was that this move would enable them to focus more on HTML5 development for mobile devices and allow them to put more effort into maintaining the fluidity and security of their desktop Flash plugin.

Welcome back, curious hackers! In today's tutorial, we will be diving deep into the manipulation of Google Operators, commonly referred to as "Google Dorks" in order to access Surveillance Cameras and other control panels.

Computer system authentication is critical to keeping systems safe from unwanted users, intruders, and abusers. Basically, authentication is the process of the potential user proving they are an authorized user.

Keeping your online data and identity private is an uphill battle, but with the anonymity network Tor, you have a pretty decent line of defense from prying eyes.

Welcome back, my novice hackers! As most of you know by now, a notorious commercial, legal hacking group named "Hacking Team" was recently hacked. As part of the hack, thousands of emails and other material on their servers was divulged. Among the material released were three zero-day exploits. In this tutorial, we will walk through the steps to load one of them, which has become known as the CVE-2015-5119 exploit.

The traditional six yards is undoubtedly among the most gorgeous outfits a woman can adorn. Here we tell you how you can wear it with a new twist for a modern look.

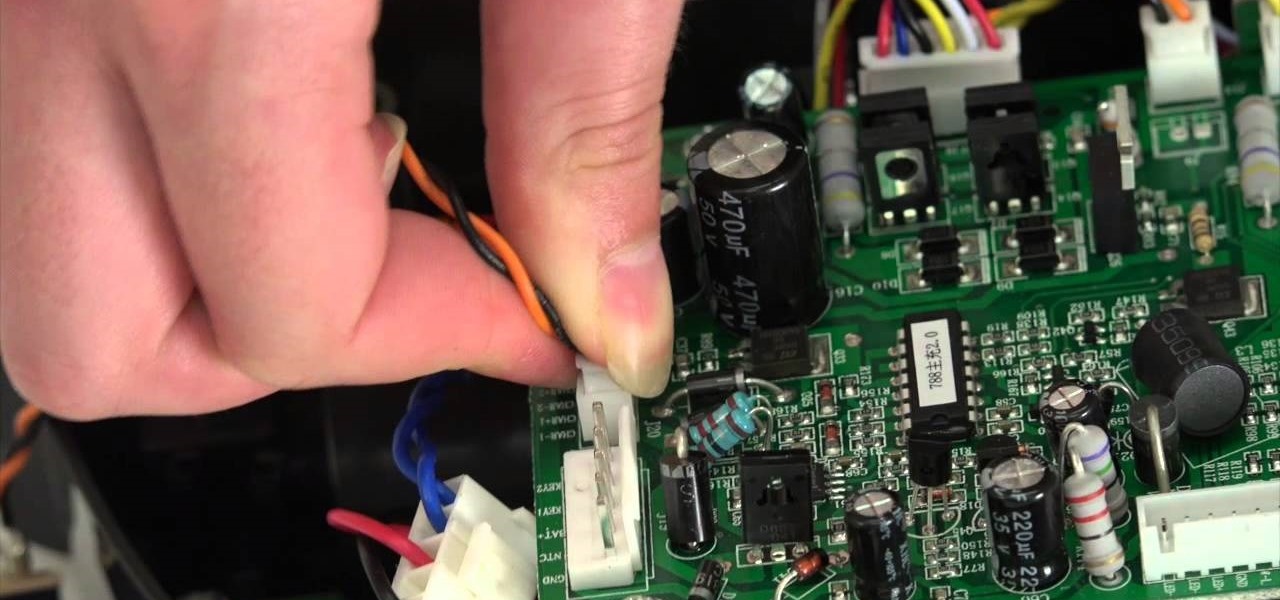
The guide will walk you through a power switch replacement on a bObsweep Standard or Pethair. It includes:

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Smartphone users often wish for a privacy, where no one is able to poke his/her nose in their personal stuff. Unfortunately, none of the smartphones have been able to guard their privacy in this fashion. Smartphones usually come up with none or almost negligible built-in security to serve your purpose.

In the weeks before Apple officially released iOS 8, consumers were abuzz over rumors that a new feature would password-protect your photos and text messages from prying eyes. Unfortunately, this ended up being untrue, though we did cover some alternatives to protecting your important information using some built-in features and a third-party app. Now, there's a new iOS app that can do it all.

With all of the different websites we use in our day-to-day lives, keeping track of our numerous login credentials can start to become a hassle. This has created a market for password managers that aim to centralize these account credentials and generally streamline the process of logging into our favorite sites.

People who know that I am a professional hacker often ask me what they can do to make their computers and personal information safe from people like me. The answer, of course, is that nothing will make you completely safe, but there are a number of measures any computer user can take to reduce the chances of being a victim of a hacker.

As great as the Internet is, it is not without its dangers. Hackers at any time may be breaking into your online accounts and compromising your sensitive information. Last year, hackers broke into Facebook, Gmail, and Twitter and made off with 2 million stolen passwords.

It's a modern day nightmare to accidentally reveal too much information on Facebook. I've inadvertently told the world my location more times than I can laugh off, and my friends haven't fared too well either. Just take a look at the requested app permissions next time you're about to click install and you'll quickly realize how much that app can reveal about you.

Apple's new iOS 8 has a ton of new features, and so does their revamped Safari app, only some of the features aren't quite as obvious as others. In this guide, I'll show you my 5 favorite Safari secrets in iOS 8 for your iPad, iPhone, or iPod touch.