
How To: Use the security features on an HP Compaq 2710p PC
The HP 2710p business notebook has a number of innovative security tools to make sure your data stays where you want it.


The HP 2710p business notebook has a number of innovative security tools to make sure your data stays where you want it.

Earthworm Jim is a classic SEGA video game from the early nineties that made its way to almost every conceivable gaming console known to man. Now, the Xbox 360 gets it chance. The remake is entitled Earthworm Jim HD, and has been available on the Xbox Live Arcade (XBLA) since June 9th, 2010.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

Coinbase is the primary go-to for many users when it comes to investing in Bitcoin (BTC), Ethereum (ETH), Litecoin (LTC), Ripple (XRP), and more, due to its user-friendly interface. But before you join them, know that the ease of use comes with a price. Coinbase charges fees for each transaction, and your bank might even add charges on top of that. Plus, there is some fine print to be aware of.
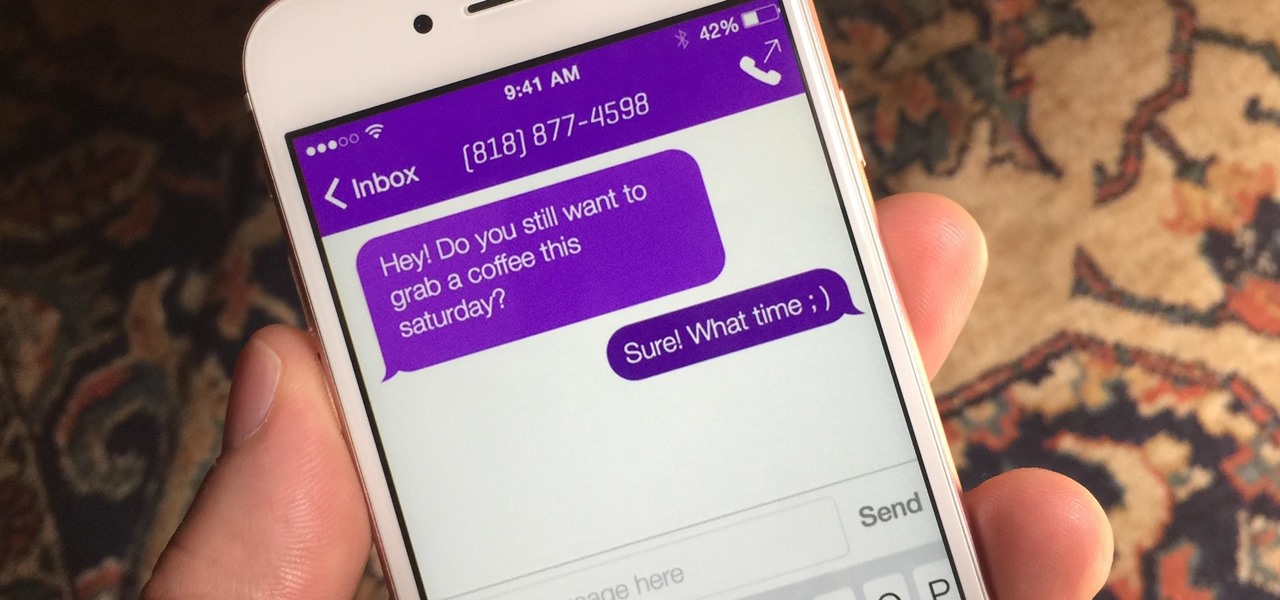
Throwaway phones aren't just for seedy criminals and spies—they can be useful for many everyday situations.
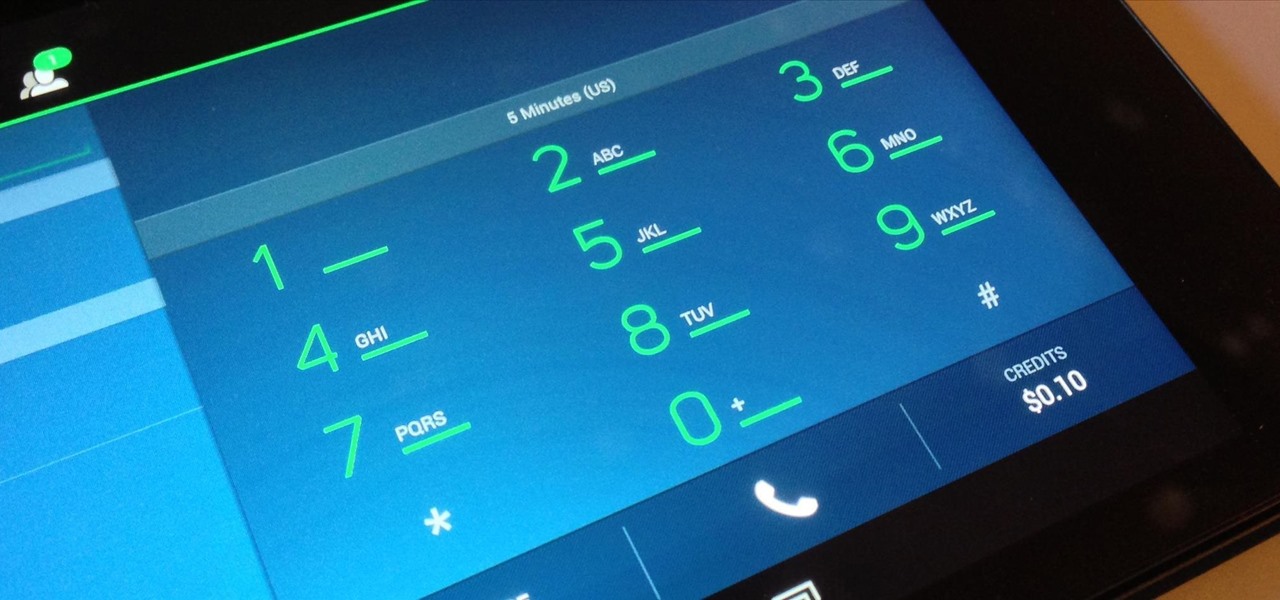
Your Nexus 7 may be a tablet, but it can also be used as a phone, thanks to the continued upswing of VoIP applications, which send voice and media messages over the Internet—not over a cellular network.

Gather your hoop and supplies. Wrap the suede evenly around the entire ring. Wrap it either eight or sixteen times, depending upon your preference. Glue the ends to the hoop. Secure them with a clothespin until the glue dries. Make the web. Tie the nylon string to the suede. Make eight knots evenly dispersed around the ring. Keep the thread taunt between knots. Make a second row. Place each knot "between" the knots of the previous row. Continue in this manner until a small hole remains in the...

Shaun Alexander was an amazingly productive NFL running back. In this video, he takes some time to explain for young running backs how to hold the ball properly, protecting it from the defense and potential fumbles. Proper finger positioning and placing the body between opponents and the ball are both crucial elements.

In this video, Karlyn M. Campbell, an Information Technology student, goes through how to set up and secure a wireless network on a laptop. For a wireless network you will need your computer, a wireless router and its CD, and a USB wire. First the video goes through how to set up the router by using its installation CD. This video uses a Belkin router, and so shows the steps the Belkin installation CD takes the user through. The CD also lets the user decide which security settings he or she w...

If you're new to DreamCoder for MySQL, one of the first things you may want to know how to accomplish is to connect to a remote MySQL database securely via SSH tunneling. Happily, this tutorial will walk you, step by step, through the process. To learn how to establish a secure connection between a given MySQL database and the DreamCoder for MySQL, take a look!

Babies have no way of communication other than crying. = Touch is one of a baby's most highly developed senses at birth. Holding, caressing and cuddling your infant is crucial to helping her feel safe and secure. There are a number of tips demonstrated in this instructional video to help calm a crying baby. Watch this video child care tutorial and learn how to comfort a baby.

This video demonstrates how to install or replace a dead bolt in your door. Having a dead bolt lock gives you a added sense of security, because it is more secure than just the lock on the door handle.

This video is designed to help deaf people, or those with hearing impairments, learn how to do basic first aid. Specifically, this video deals with sever bleeding and how to stop it, and is taught in sign language.

You can edit videos in Windows Movie Maker. Movie Maker allows you to make videos. What you will want to do first is open pictures or a video that you will want to use. Select however many images or videos you want to use. Create a title and credits for this video. You can select whatever type of font and font color that you want to use. The next step you will want to do is add Audio. You can do this by looking under Tasks on the far left side of the page and add whatever audio from your hard...
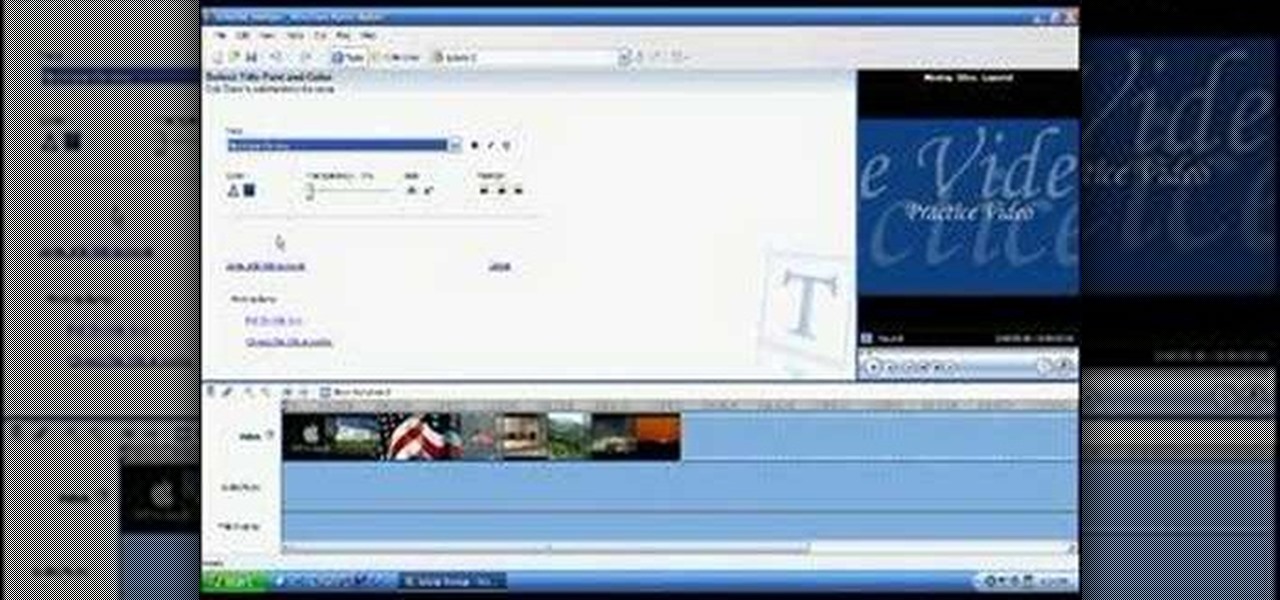
Follow along as we are shown how to make a movie in Windows Movie Maker. -To begin, open up Windows Movie Maker, if you do not have this you can download it at http://www.microsoft.com

In this video from Lowe's we learn how to use a gas smoker. This tip comes from Lowe's. You can cook with a smoker anytime of year. He is using a gas smoker. Keep this away from siding. The fire source heats the moist wood chips, which release the smoke that flavors the food. You need tongs and a meat thermometer for sure. Before you cook for the first time, season the smoker by smoking some wood chips without food in it. He is cooking a pork shoulder which he uses a dry rub, wraps in plastic...

Place 2 Tbsp. oil in a wok or large frying pan over medium to high heat. Add garlic, galangal (or ginger), shallots, and chili. Stir-fry until fragrant (about 1 minute). Stir-frying Tip: Add a little water to the wok/pan when it gets too dry instead of more oil.

These videos show you how to use baking strips to make a better cake. Use caution when using baking strips, and watch your oven carefully.

As a Boy Scout, when the First Class rank is attained, a scout has learned all the basic camping and outdoors skills of a scout. He can fend for himself in the wild, lead others on a hike or campout, set up a camp site, plan and properly prepare meals, and provide first aid for most situations he may encounter. A First Class scout is prepared.

This dance tutorial teaches you how to do swing dance routines from great classic films. The moves in this tutorial are based on the 1929 film short "After Seben." Footage is of Shorty George Snowden and his partner, sometimes credited as Pauline Morse, at other times identified as Big Bea. The music is by Chick Webb and his orchestra.

Everyone gets cut every once in a while, but sometimes those cuts can be more serious than expected. It could turn into severe bleeding, and there's a certain way to deal with this type of bleeding in a victim. How would you treat someone who was bleeding severely?
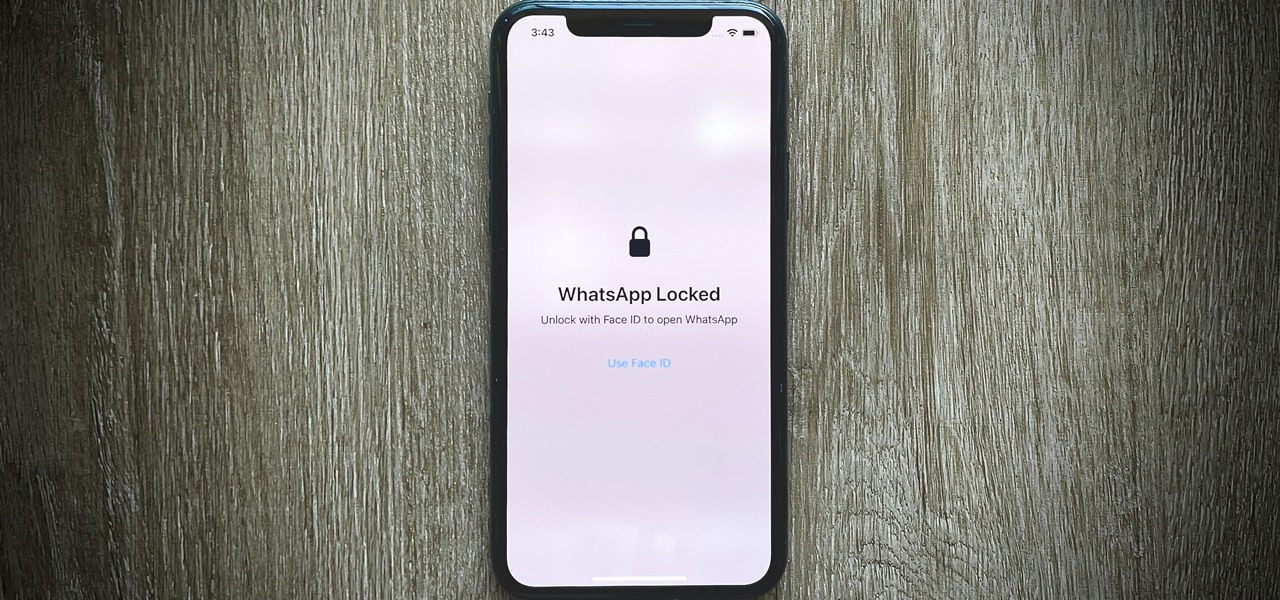
End-to-end encryption makes WhatsApp chats private and secure. However, if someone has access to your iPhone, they can easily open the app and browse through all of your personal conversations. Luckily, there's an easy way to block any would-be intruders at the gates — just lock the app behind Face ID or Touch ID.

With millions of people working from home as a result of the coronavirus outbreak, hacking is on the rise. Nefarious black hats are taking advantage of the fact that workers have been forced to abandon their secure office networks in favor of home wireless connections. And white hats are spending even more time at home trying to be the next great ethical hacker.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.
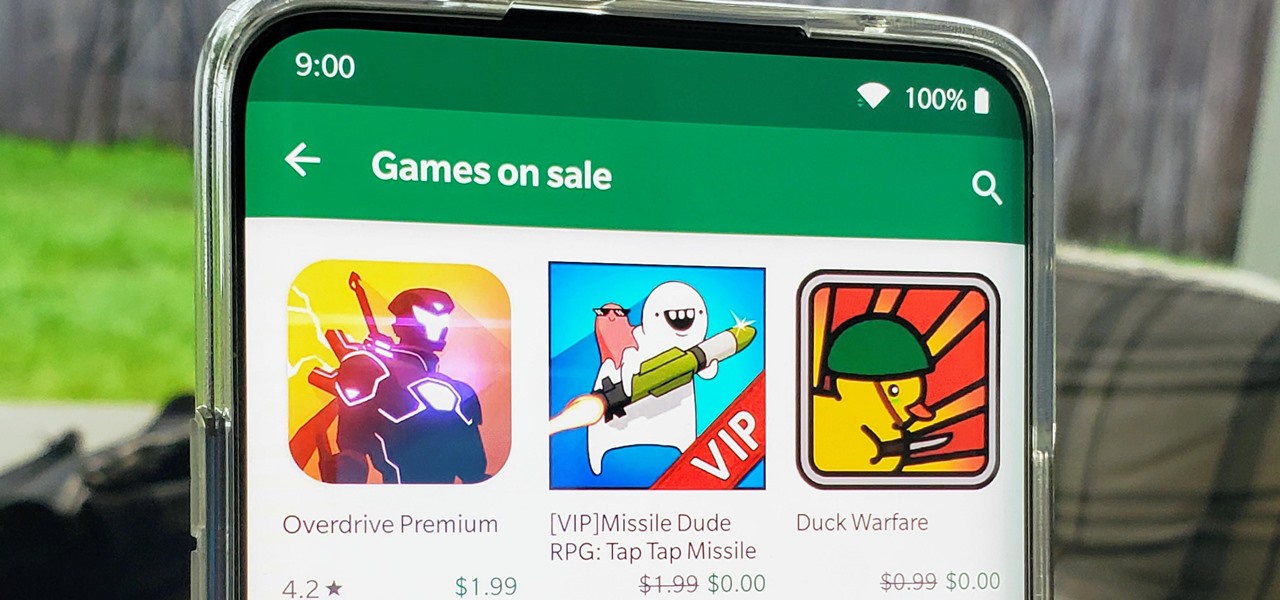
I think we all like the idea of getting paid games for free with minimal effort. Typically, though, anything claiming to help you do that is either illegal or a scam. But there are actually quite a few no-fuss methods that can get you paid games without going too far out of your way. From checking notifications to discovering hidden offers, you might have something waiting for you.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.
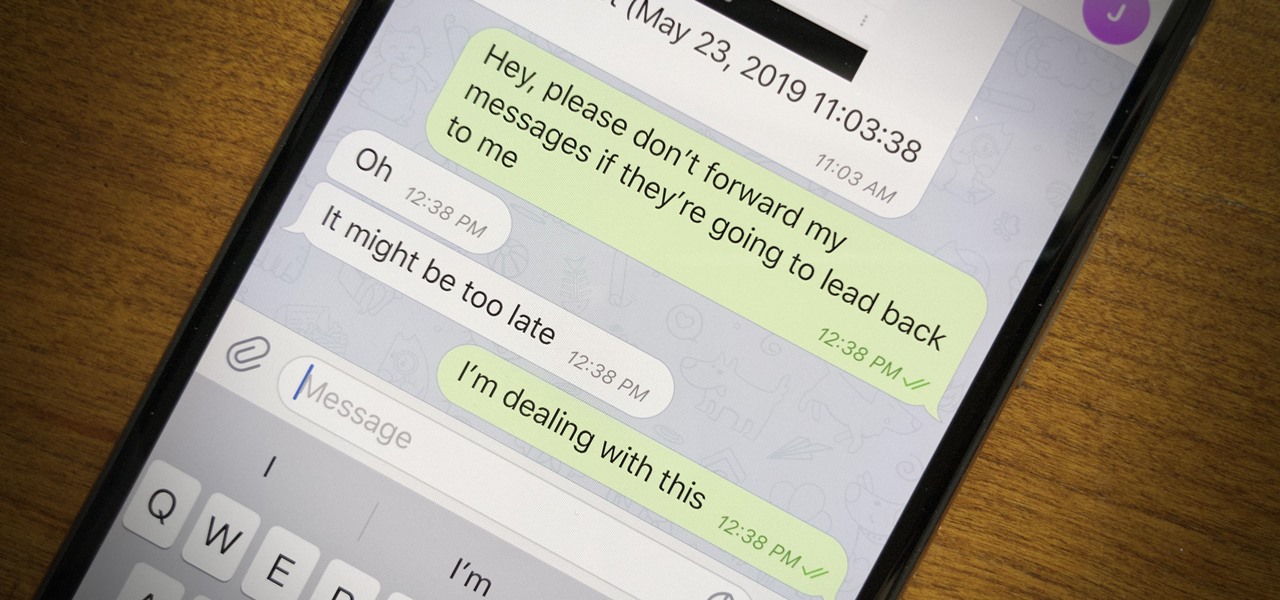
Forwarding messages is a helpful Telegram feature that makes it easy to share funny and entertaining content with other contacts. However, for the privacy-centric, forwarding poses an issue, as messages of yours that are delivered elsewhere carry a tag back to your account. Luckily, you can make your messages anonymous, so anyone receiving messages of yours that are forwarded won't be able to see you originally sent the message.

By far the most significant development for AR in the coming months and years — the development that will drive AR adoption — will be our reliance upon the AR cloud.
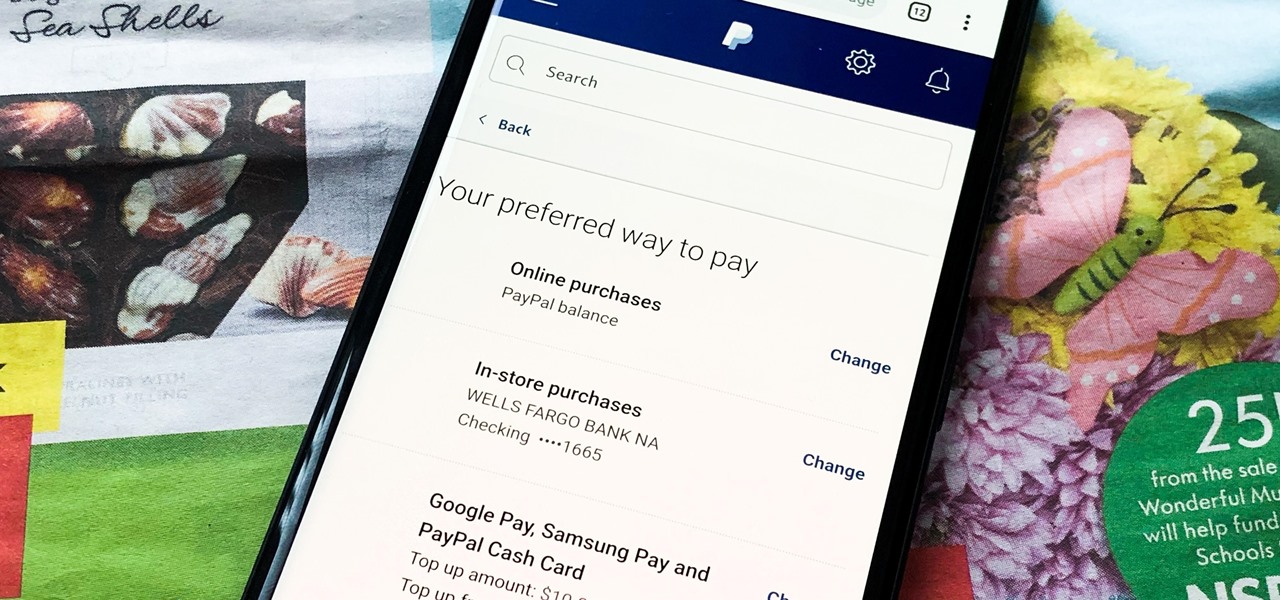
Making a purchase through PayPal is great because you have the option to pay using your account balance, a bank account, debit card, credit card, rewards balance, or even PayPal's own credit product. You need to pick one to be your preferred payment method for each in-stores and online but, unfortunately, changing these preferences can get a bit tricky on your iPhone or Android phone.

When your iPhone goes missing, it's serious business. Depending on your usage, your whole life might be connected to your iPhone, not the least of which includes debit cards, credit cards, and Apple Pay Cash stored in Apple Pay. While it's nearly impossible for someone to use your money with Apple Pay, it's still a good idea to disable it until you find your iPhone, just in case.

Back in July, Google rolled out a new design for the web version of Gmail. The rollout included new features alongside the visual changes, one of which being Confidential Mode. This new privacy-centric feature has now finally arrived on the mobile app version of the service, and here's what you need to know.

After a district judge approved the $85 billion merger between AT&T and Time Warner, we knew AT&T would be quick to reap the rewards of capturing Time Warner's media properties. Today, we get our first look at this with two cellular plans from AT&T. What makes these plans unique is they include a new cord-cutting service called WatchTV.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

In this series, we are going to get you to the edge of building your own cloud-based, cross-platform augmented reality app for iPhone, Android, HoloLens, and Meta 2, among other devices. Once we get the necessary software installed, we will walk through the process of setting up an Azure account and creating blob storage.

Chances are, you just point, shoot, and share photos and videos on your iPhone without a second thought about how your privacy is affected. It's fairly easy to do so since the Camera and Photos apps that Apple provides seem so innocent. But there are a few things you need to know when it comes to shooting media, sharing it, and even deleting it.

When traversing the web, you'll regularly come across websites that require you to create an account. With the majority of these accounts, protection is limited to a simple password. Despite this, many people are still using weak passwords such "123456." For these reasons, you really need a password manager, and our research has shown that LastPass is still your best bet.

While iOS 11.3 doesn't have as many new features as iOS 11.2, there's still a lot to love about Apple's latest update for iPad, iPhone, and iPod touch, even if some of the best features we were expecting didn't make the cut.

Now that Apple Pay Cash has rolled out to compatible devices in the US, you're likely to give Apple's new person-to-person payment system a try since it's right there in the iMessage app drawer in Messages. However, just like with Venmo, Square Cash, and other mobile payment processors, there are some hidden fees, limits, and other fine print you need to be aware of.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.